Cyber Skills Gap
Learn more about the cybersecurity skills gap and cybersecurity gender gap. Research and interviews with industry leaders and champions of diversity.
- All Categories
- ...
-
 Cyber Skills Gap
Cyber Skills GapIT Departments are Looking for New Jobs: Here’s How to Retain Talent
-
 Cyber Skills Gap
Cyber Skills GapThere Isn’t a Cyber Skills Shortage, You’re Just Not Hiring and Retaining The Right People
-
 Cyber Skills Gap
Cyber Skills GapNew Research: 1 in 3 Employees in IT and Security Teams Are Female
-
 Life at Tessian, Cyber Skills Gap
Life at Tessian, Cyber Skills GapTessian Officially Named a 2021 UK’s Best Workplaces™ for Women
-
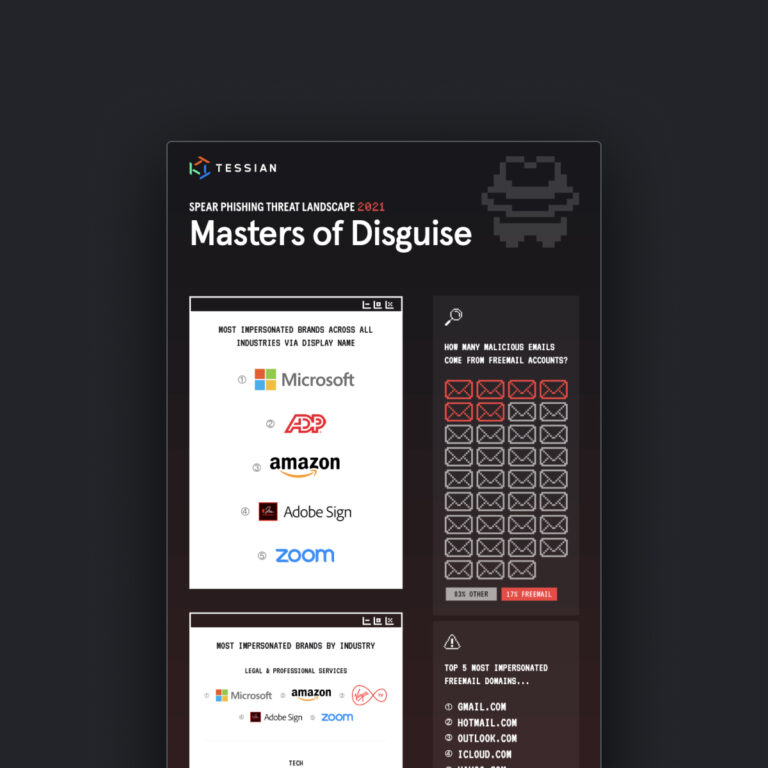 Cyber Skills Gap
Cyber Skills Gap3 Reasons Hackers Could Help Bridge the Cybersecurity Skills Gap
-
Cyber Skills Gap
Key Takeaways from Tessian’s Cybersecurity Skills Gap Webinar
-
 Cyber Skills Gap
Cyber Skills GapIntroducing Tessian’s Opportunity in Cybersecurity Report 2020
-
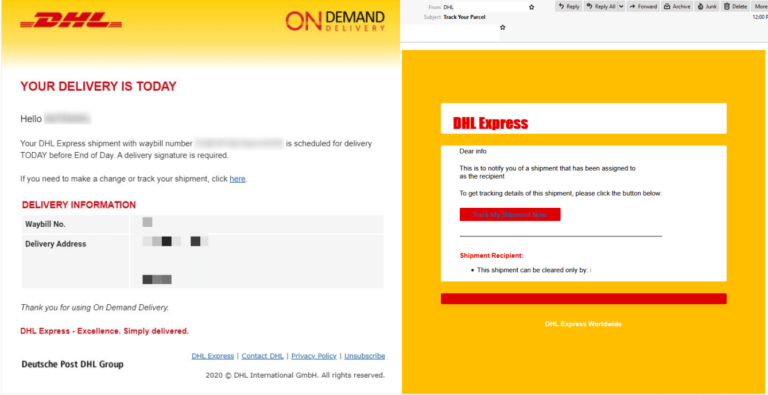 Cyber Skills Gap
Cyber Skills GapOpportunity in Cybersecurity: Q&A With Shamla Naidoo From IBM
-
 Cyber Skills Gap
Cyber Skills GapOpportunity in Cybersecurity: Q&A With Hayley Bly From Nielsen
-
 Cyber Skills Gap
Cyber Skills GapOpportunity in Cybersecurity: Q&A With Hillary Benson From StackRox
-
 Cyber Skills Gap
Cyber Skills GapOpportunity in Cybersecurity: Q&A With Swati Lay From Funding Circle
-
 Cyber Skills Gap
Cyber Skills GapOpportunity in Cybersecurity: Q&A With Amy Johnson From Herbert Smith Freehills
-
 Cyber Skills Gap
Cyber Skills GapOpportunity in Cybersecurity: Q&A With Kim Smathers from Snapdocs
-
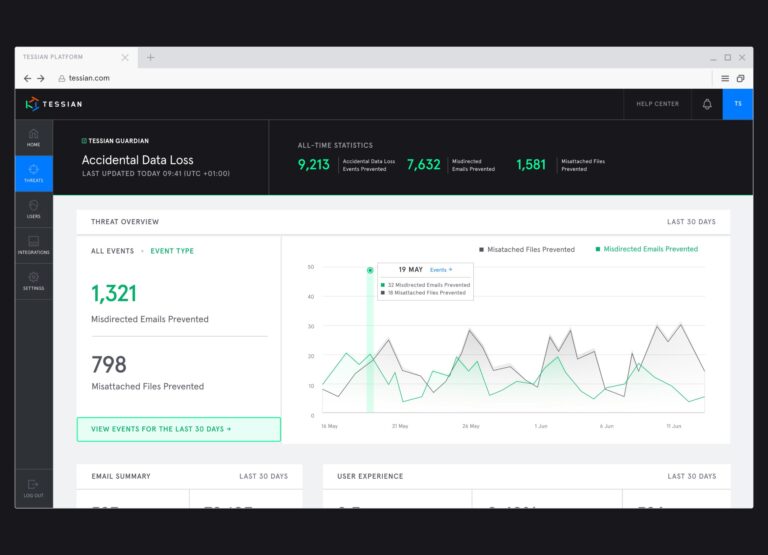 Cyber Skills Gap
Cyber Skills GapOpportunity in Cybersecurity: Q&A With Sara Zahid From Jefferies
-
 Cyber Skills Gap
Cyber Skills GapOpportunity in Cybersecurity: Q&A With Tess Frieswick From Kivu
-
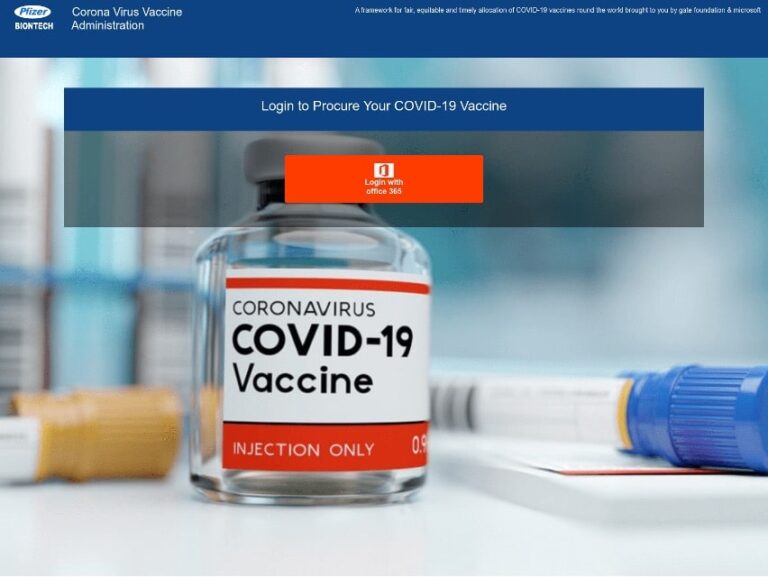 Cyber Skills Gap
Cyber Skills GapOpportunity in Cybersecurity: Q&A With Carolann Shields From KPMG
-
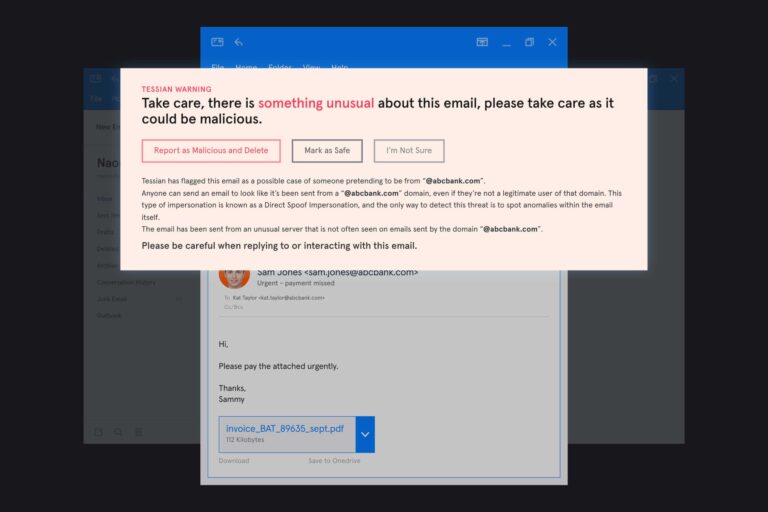 Cyber Skills Gap
Cyber Skills GapOpportunity in Cybersecurity: Q&A With Gisela Rossi From Tessian
-
 Cyber Skills Gap
Cyber Skills GapOpportunity in Cybersecurity: Q&A With Niki Tailor From Tessian
-
 Cyber Skills Gap
Cyber Skills GapOpportunity in Cybersecurity: Q&A With Amber Pham From TransUnion







