Immediately after the outbreak of COVID-19, there was a surge in opportunistic phishing attacks in which hackers leveraged the pandemic to dupe targets into following links, downloading attachments, or otherwise divulging sensitive information. Wondering what to look out for? We break down 4 emails below, including impersonations of Zoom, HR, and a VPN provider.
Looking for examples of spear phishing attacks that don’t leverage COVID-19? Check out this article instead.
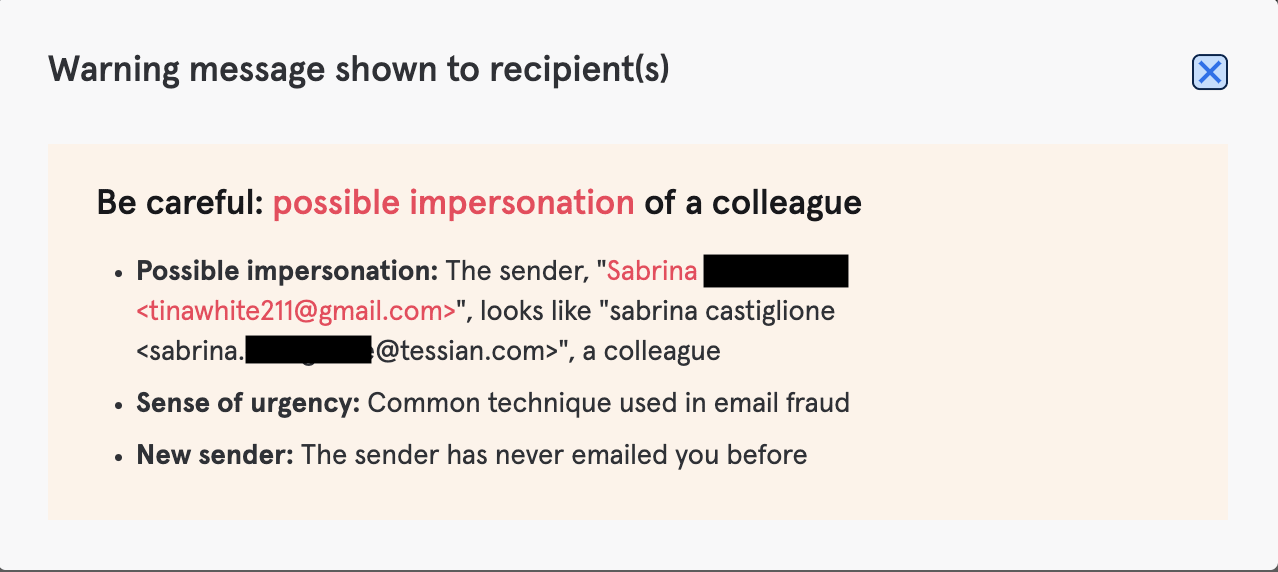
Phishing Email #1: Your CEO is Waiting for You
What’s wrong with this email?
- The Display Name (zoom_meeting@tessian.com) and the email address do not match. The actual sender address is fd29eaab47504bfa8bd773ee581bc7d4@tessian.com.
- The attacker, who sent the email on a Friday afternoon, is hoping that the target will a) be motivated to respond quickly to a meeting request from the CEO and b) be less scrutinizing and security-conscious as it’s the end of the week.
- The target is being encouraged to click on a seemingly legitimate Zoom link, which would likely lead to a malicious site or could deploy malware.
- Upon hovering over the provided link, you’ll find the URL is actually different than the hyperlink would lead you to believe
- The closing of the email is suspicious: “This message is from your company’s IT.”
NB: This phishing email is a direct spoof and was prevented because of DMARC; it was automatically sent to a Spam folder. If you haven’t set your DMARC records correctly, these emails will fly past existing defenses.
Inspect links carefully: here, destination URL and hyperlink do not match
Phishing Email #2: Generic Zoom Spoof
What’s wrong with this email?
- The Display Name (tessian.com ZoomCall) and the email address do not match, but the attacker is hoping the recipient doesn’t look beyond the sender Display Name.
- The conference call time and date in the email subject line seem to have already passed, based on when the attack was received. Note this email was received at 3:22am, so would likely be the first email the recipient reads in the morning.
- The email contains the message “Zoom will only keep this message for 48 hours.” This combined with the subject line adds a sense of urgency and could potentially convince the recipient they’ve missed something important and should quickly try to remedy it.
- The target is being encouraged to click on a seemingly legitimate Zoom link, which would likely lead to a malicious site or could deploy malware.
We’ve been pulling together guidance and resources to help employees and businesses stay safe while working remotely. If you suspect you’ve been targeted by a phishing attack, do not click any links or download attachments. Instead, directly contact the sender via phone or a messaging app to confirm legitimacy of the email and immediately alert your IT or security team.
Phishing Email #3: The Attacker is Capitalizing on Fear Around COVID-19
Display and domain do not match
What’s wrong with this email?
- The Display Name (Information Unit) and the email address do not match at all. (What’s more, ‘Information Unit’ is not a genuine internal group at Tessian.)
- The attacker, who sent the email late-afternoon on a Friday, is no doubt hoping that the target – our marketing team – is less scrutinizing and security-conscious as the week comes to a close, especially when employees across the globe are working from home.
- The target is being encouraged to download an attachment, which opens a fake login page to steal the victim’s credentials.
- The email is rife with spelling and grammar errors as well as formatting inconsistencies and the unconcerned, mechanical language is out-of-character for anyone in management, especially given the content of the email.
- The attacker used complex encoding to try to evade traditional phishing detection tools that would scan for certain keywords in the email’s body. How? By interspacing different invisible characters between other characters so that the content looks like gibberish.
Below is a screenshot of encoding in the email body for reference. Here, you see the characters marked “transparent”; those are the invisible characters.
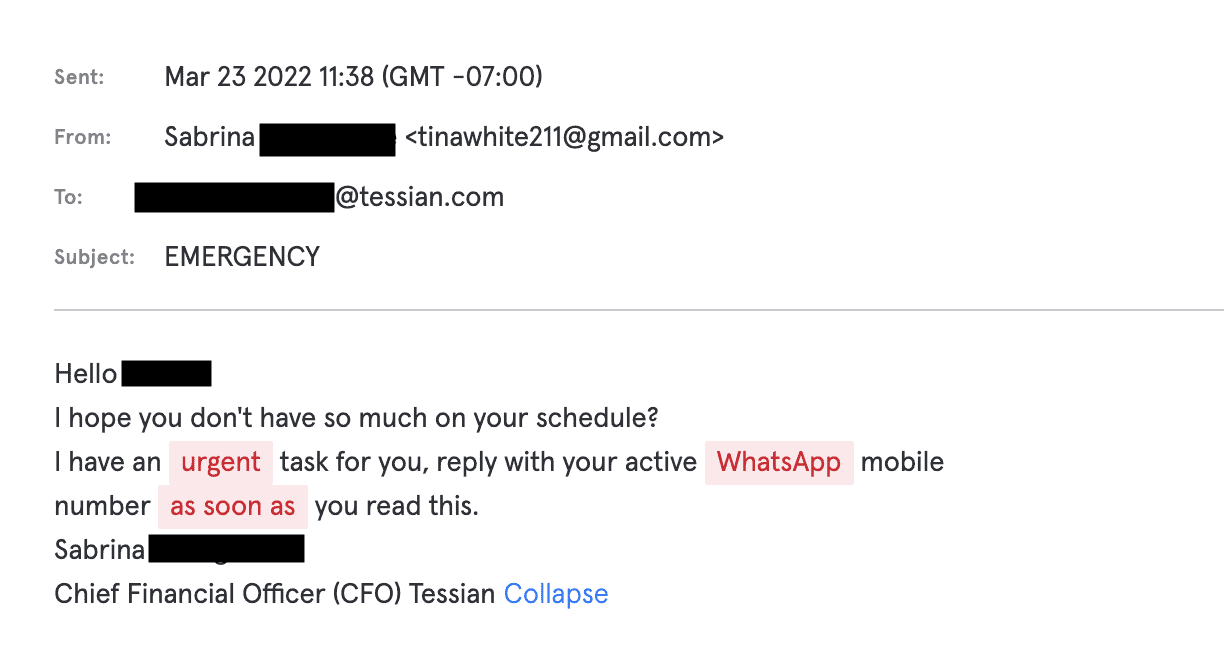
Phishing Email #4: The Attacker Baits the Target With a Remote-Working Tool
What’s wrong with this email?
- The Display Name (Helpdesk_admin@tessian.com) and the email address are in stark contrast.
- This sender’s email address is a direct spoof of the domain (tessian.com).
- The attacker is taking advantage of the fact that many employees around the world are now suddenly working from home and in need of remote-working tools. Therefore, targets are more likely to trust that their employer has, in fact, set them up for remote connection provided by a VPN vendor.
- The way this email is constructed – poor grammar and impersonal – makes it obvious to a Tessian employee that this is not legitimately from our IT manager.
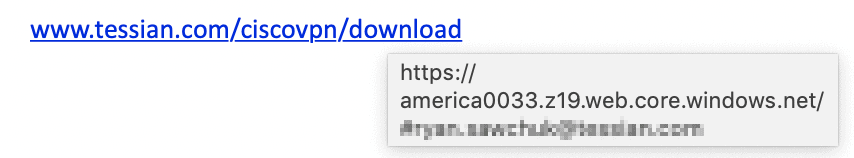
The target is being encouraged to follow a link, which looks inconspicuous. But, upon hovering, you’ll see that the link the target will actually be led to is suspicious.
Important: Because Tessian has DMARC enabled, emails that spoof our domain are automatically sent to “quarantine”. That means the email was never actually received by the target and instead went straight to a spam folder. Unfortunately, though, a lot of companies don’t have DMARC enabled. In fact, nearly 80% of domains have no DMARC policy.
Now that you know what these opportunistic phishing emails look like, what do you do if you’re targeted? That is, after all, what’s really important when it comes to preventing a data breach.
What to Do If You’re Targeted by a Phishing Attack
- If anything seems unusual, do not follow or click links or download attachments. Instead, visit the brand’s website via Google or your preferred search engine, find a support number, and ask them to confirm whether the communication is valid.
- If the email appears to come from someone you know and trust, like a colleague, reach out to the individual directly by phone, Slack, or a separate email thread. Rest assured, it’s better to confirm and proceed confidently than the alternative.
- If you’re an employee who’s been targeted, contact your line manager and/or IT team.
You can download this advice in PDF format (perfect for sharing with others peers and friends!) here.
Want to stay up-to-date on the latest threats, get tips on how to stay safe, and advice for security leaders from security leaders? Sign-up for our weekly blog digest and get new content, straight to your inbox.