Tessian is honored that Gartner has recognized us as a Representative Vendor for Integrated Cloud Email Security (ICES) in the 2023 Market Guide for Email Security. Within the report, Gartner recommends that security and risk management leaders should: “Supplement the native capabilities of your existing cloud email solutions with third-party security solutions to provide phishing protection for collaboration tools and to address both mobile- and BEC-type phishing scenarios.”
According to the report, “The migration to cloud email platforms continues along with a significant increase in the number of phishing attacks.” Further in the report Gartner states, “Impersonation and account takeover attacks via business email compromise (BEC) are increasing and causing direct financial loss, as users place too much in the identities associated with email, which is inherently vulnerable to deception and social engineering.”
The report informs its readers, “email continues to be a significant attack vector for malware and credential theft through phishing. An estimated 40% of ransomware attacks start through email. Cloud adoption continues, with an estimated 70% using cloud email solutions.
Gartner recommends that security and risk management leaders responsible for email security should:
- Supplement the native capabilities of your existing cloud email solutions with third-party security solutions, to provide phishing protection for collaboration tools and to address both mobile- and BEC-type phishing scenarios.
- Use email security solutions that include anti-phishing technology for targeted BEC protection that use AI to detect communication patterns and conversation-style anomalies, as well as computer vision for inspecting suspect URLs. Select products that can provide strong supply chain and AI-driven contact chain analysis for deeper inspection and can detect socially engineered, impersonated, or BEC attacks.
- Prioritize integration of email security solution APIs to enable integration of email events into a broader XDR or security information and event management (SIEM)/security orchestration, analytics and reporting (SOAR) strategy.
While email security has come a long way since its inception around 2000, the greatest external threats facing on-premise mail servers at the time were bulk unsolicited mail and spam. But today, the world has changed. As Gartner refers to in the report, now an estimated 70% of organizations are using cloud email solutions.
This rapid shift to the cloud has opened up a new threat to landscape security. Risk management leaders must uncover and learn how to protect themselves from it. Regarding email, the effectiveness of safeguarding this unsolicited domain has been in the crosshairs for quite some time. Today email is the entry point responsible for over 90% of cyber attacks.
But why is this the case?
The rapid shift in moving to the cloud allowed cyber criminals a huge opportunity; an opportunity grabbed with both hands. Email security, while being in the crosshairs, has been largely untouched for many years. Organizations holding significant investments in their Secure Email Gateway (SEG) protect their internal network from the outside world.
Still, it isn’t as though these solutions deteriorated overnight, but the world around them did. Secure Email Gateways were built to address security concerns in a forgone, cloud-adverse world. They were once the gold standard in email security.
But the rapid shift to the cloud and ever-changing threat landscape exposed this once sturdy and reliant email defense to become vulnerable and ineffective in safeguarding users and data from advanced threats and insider risks.
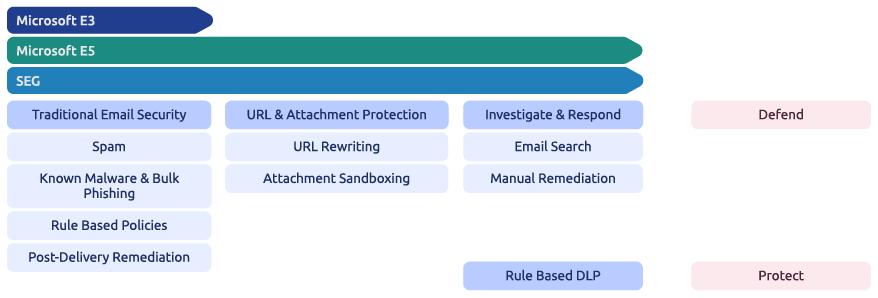
Further to this, Microsoft and Google have pressured this space. Now offering overlapping capabilities of a Secure Email Gateway (SEG) solution within the cloud productivities platforms allowing organizations to streamline their email security approach, simplify their security stack and reduce cost and complexity.
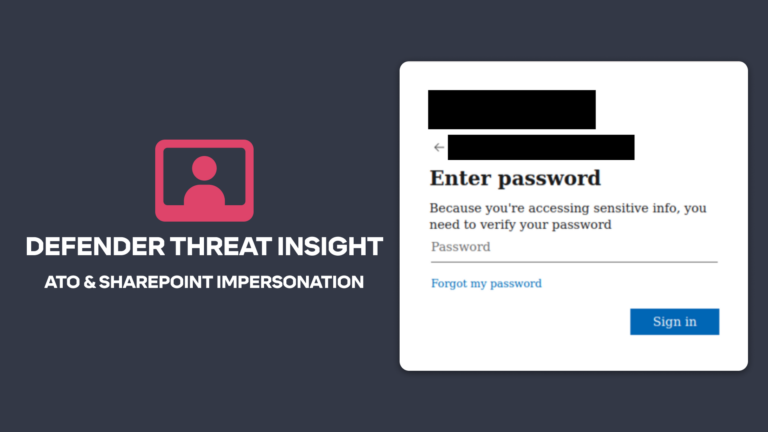
But while this is a positive for security and risk management leaders, Gartner states in the report that “threat actors are also getting more sophisticated, often targeting the end users using fake login pages as a way of harvesting credentials. Sophisticated email threats include compromised websites and weaponized documents used to deploy malware. Many ransomware-as-a-service gangs use email as the initial entry point. Beyond malware, business email compromise and account takeover threats continue to rise, with significant financial losses as a result”.
Combatting this new wave of attacks
Now it is recommended to consolidate overlapping gateway capabilities into Microsoft 365 to help CISOs reduce cost and complexity while cautioning that CISOs should carefully evaluate the native capabilities offered by cloud email systems and ensure that they are adequate to prevent a sophisticated attack. An argument can be made that “complexity” remains at the heart of Microsoft’s licensing model.
Microsoft has numerous packaging options, bundles, and add-ons. Knowing where they differ and overlap is vital to understanding what you have access to today and effectively leveraging native security capabilities to secure your email environment.
Gartner recommends that to combat this new wave of attacks, email security solutions need to use a variety of more-advanced detection techniques, including, but not limited to, Natural Language Processing, Natural Language Understanding, and Social Graph Analysis. Gartner states, “ICES solutions go beyond simply blocking email by adding context-aware banners warning users. This means that the threshold for false positives can be higher and can also reinforce security awareness training. Often, a mechanism for reporting phishing is included, either as part of the email client or as another banner inserted into the email body.”
Microsoft + Tessian = Comprehensive security
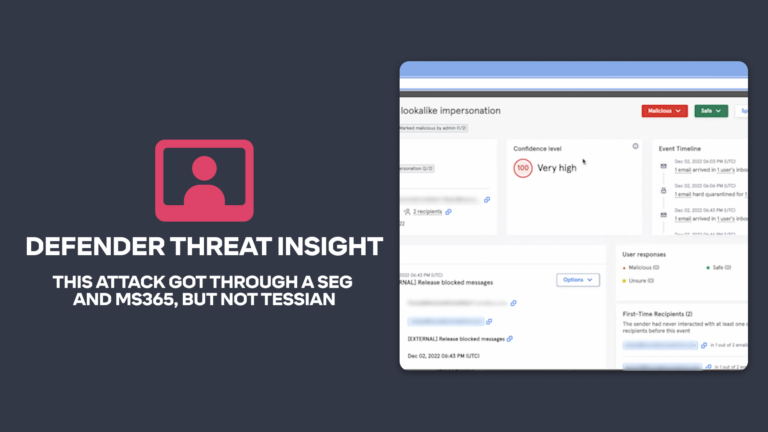
This is where an intelligent cybersecurity solution like Tessian Cloud Email Security Platform comes into play, providing advanced email threat protection and insider risk protection on email. With Tessian, no mail exchange (MX) records need to be changed. Tessian can construct a historical user email pattern map of all email behavior in the organization. The algorithm can then detect and prevent threats that Microsoft or SEGs have failed to detect.
“Tessian stops the threats that you just can’t make a rule for. The platform really has evolved along with our own security stack and with the risk environment. It reinforces our training and complement Microsoft”
Mike Vieira
Cloud and Perimeter Security Capability Lead, Schroders
This dynamic protection improves with each threat that is prevented. Unlike the in-line static nature of SEGs, it ensures 24/7 real-time protection against all attack vectors, including insider threats. That is why the leading enterprises opt to displace their legacy SEG and augment Microsoft’s native security capabilities with Tessian.
Gartner, Market Guide for Email Security, Ravisha Chugh, Peter Firstbrook, Franz Hinner, 13 February 2023
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally, and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
James Alliband
Director of Product Marketing