-
What is spear phishing?
Spear phishing is a phishing attack that targets a specific, named person. It’s a more sophisticated form of the traditional “spray-and-pray” phishing attack. But, just like non-targeted phishing, a spear phishing attack plays on the target’s trust, exploits weak security practices, and can cost a business millions of dollars.
This article will look at the different types of spear phishing, explain how a spear phishing attack works, and explore how common spear phishing is.
Types of spear phishing attacks
Spear phishing attacks vary according to technique, target, and goal. But, here are some types of cyberattacks that involve spear phishing:
- Whaling: A spear phishing attack targeting a company executive
- CEO fraud: A spear phishing attack where the fraudster impersonates a company executive
Here are some cyberattacks that usually involve spear phishing:
Whenever these attacks are targeted at a specific person, they’re considered a spear phishing attack. If the attack isn’t targeted at an individual, we just call it a “phishing attack.”
Struggling to understand the difference? We explain it – in detail – in this article: Phishing vs Spear Phishing: Differences and Defense Strategies.
How does spear phishing work?
Most spear phishing attacks arrive via email. In fact, email is the medium of choice for around 96% of phishing attacks. However, cybercriminals also launch phishing attacks via social media, SMS (“smishing”), and phone or VoIP (“vishing”).
But, let’s stay focused and look at a couple of examples of spear phishing attacks. This will help you understand how this type of cybercrime works.
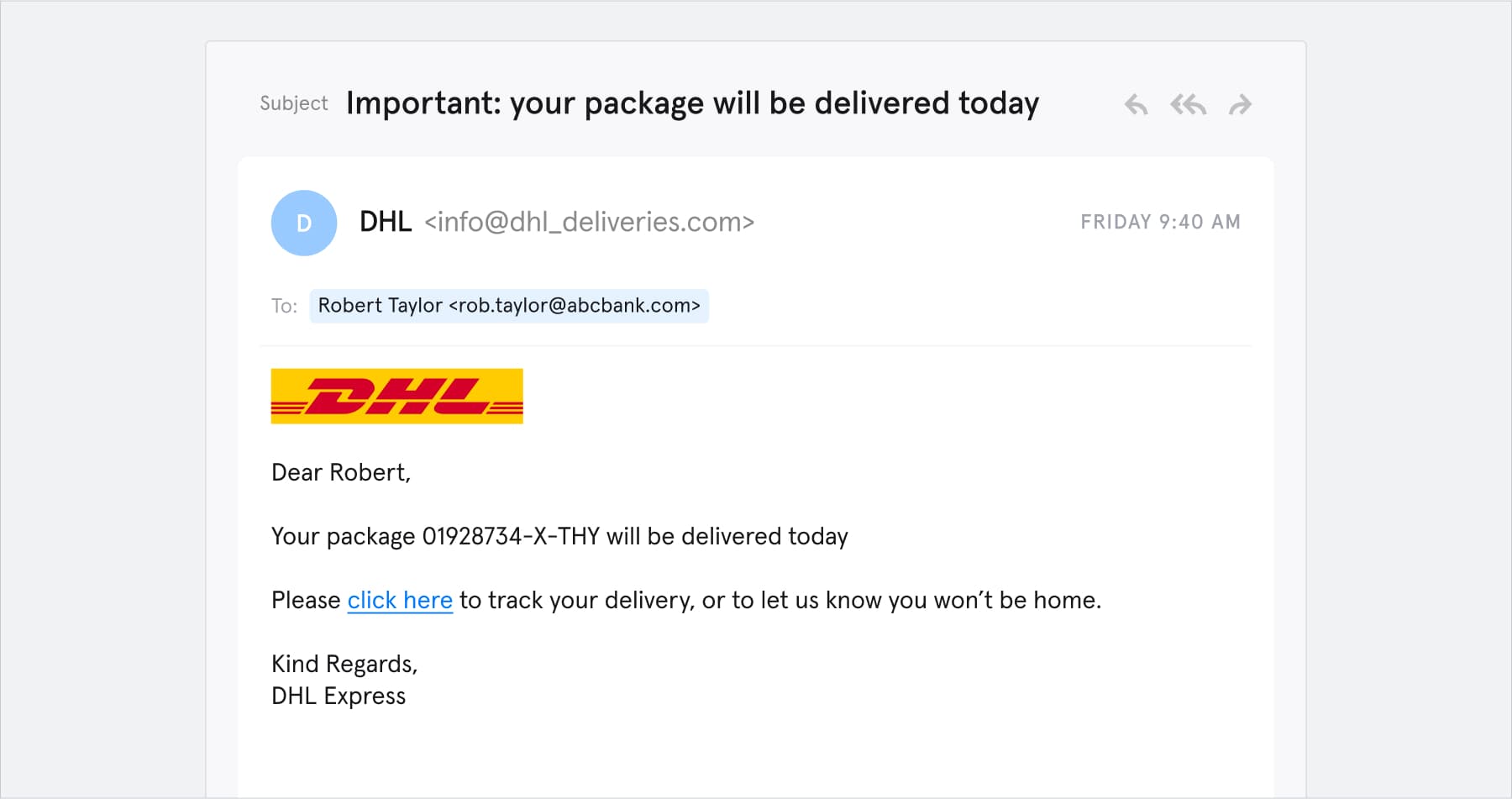
First, the all-too-common “delivery service” spear phishing attack. According to Check Point, shipping company DHL was the second-most impersonated brand in spear phishing attacks throughout Q4, 2020. Here’s how a spear phishing email impersonating DHL might look:
In this example of a spear phishing attack, the attacker is impersonating DHL.
There are a few things to note about this spear phishing email:
- It addresses the target by name. This increases the email’s persuasiveness right off the bat.
- It contains authentic logos and branding. DHL’s real emails look a lot like this.
- The links lead to DHL’s actual website.
But don’t be fooled:
- The sender’s email address is “info@dhl_deliveries.com.” This might look like an authentic DHL address, but it’s a crude impersonation attack.
- The “track your delivery” link leads to a credential phishing website.
The DHL-style scam is a simple but effective form of spear phishing that typically targets individuals. Wondering what other brands are frequently impersonated? Check out this article (+ infographic!): Phishing Statistics (Updated 2021). Spoiler: LinkedIn, Amazon, IKEA, and Google almost made the top 10.
Let’s look at a more sophisticated example of spear phishing that targets a business instead of a consumer:
In this example of a spear phishing attack, the attacker is impersonated the target's colleague.
There are some similarities between this email and the DHL scam:
- Both target specific people
- Both use authentic logos
But these factors make our second example more persuasive:
- The sender’s email address is real. Hackers can use account takeover methods to compromise real email accounts, or they can use email spoofing techniques to trick email clients into displaying bogus information.
- It references “real-world” personal information. Tessian research shows that 90% of people post personal information on social media — this is gold dust for hackers.
- It conveys a sense of urgency and exploits the target’s trust (“counting on you”). People make bad decisions under pressure.
Spear phishing is becoming more refined and advanced all the time, so it’s easy to see why people keep falling for it.
If you want help spotting a potential spear phishing attack, we’ve rounded up four red flags here. If you’re a security or business leader, this is a great resource to share with your employees that complements security awareness training.
How common is spear phishing?
Rates of spear phishing have been climbing consistently over the past decade. Research suggests, in 2019:
- 88% of organizations faced spear phishing attacks
- 65% of US organizations suffered a successful spear phishing attack (55% worldwide)
- 19% of organizations faced more than 50 spear phishing attempts
Note that these statistics refer to the period before the big migration to remote-working in 2020. There’s evidence that, as employees have moved into less secure working environments, cybercrime has increased considerably.
Microsoft’s 2021 New Future of Work report found that:
- 80% of security professionals said security incidents had increased since the start of the pandemic.
- 62% of these said phishing campaigns showed the biggest increase.
So, what’s the upshot of all this? Spear phishing damages people’s privacy, exposes confidential data, and causes major financial losses.
- The FBI reports that financially-motivated Business Email Compromise (BEC), which almost always involves spear phishing, caused direct losses of over $1.8 billion in 2020
- According to Verizon research, spear phishing is a major cause of data breaches. In the long-term, losing control of your customers’ data can be even more costly than losing money. IBM puts the average cost of a data breach at $3.86 million, rising to $8.64 million in the US.
- The biggest known spear phishing scam of all time, targeted at Google and Facebook, resulted in over $100 million in losses over a two-year period
Want to know how to protect your business against this serious type of cybercrime? Read our article on how to prevent phishing to find out.
Evaluating anti-phishing solutions? Learn more about how Tessian Defender detects and prevents the most advanced spear phishing attacks by reading some of our customer stories or booking a demo.