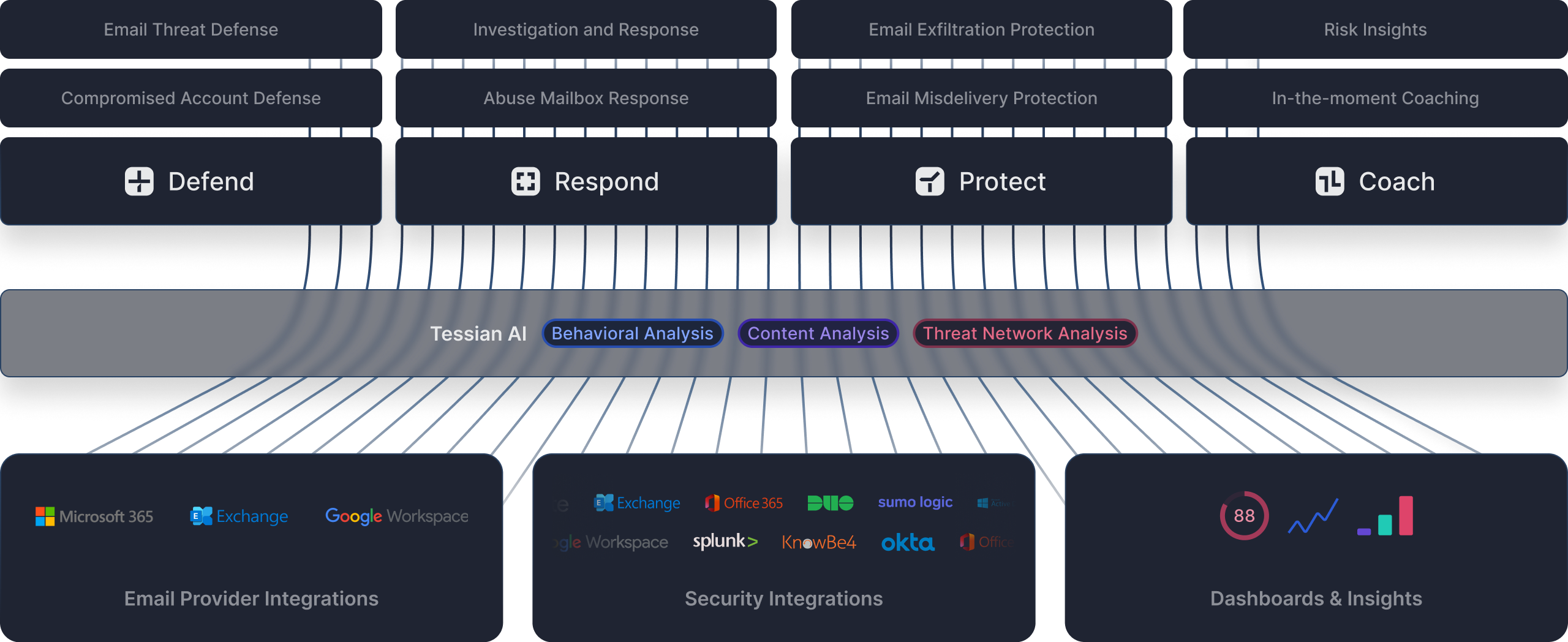
Protect against email misdelivery and exfiltration
-
Email data loss is a critical business risk
-
$20M
or 4% of annual revenue for breaches of GDPR -
40%
of workers emailed the wrong person last year -
72 hours
time to remediate an email exfiltration incident
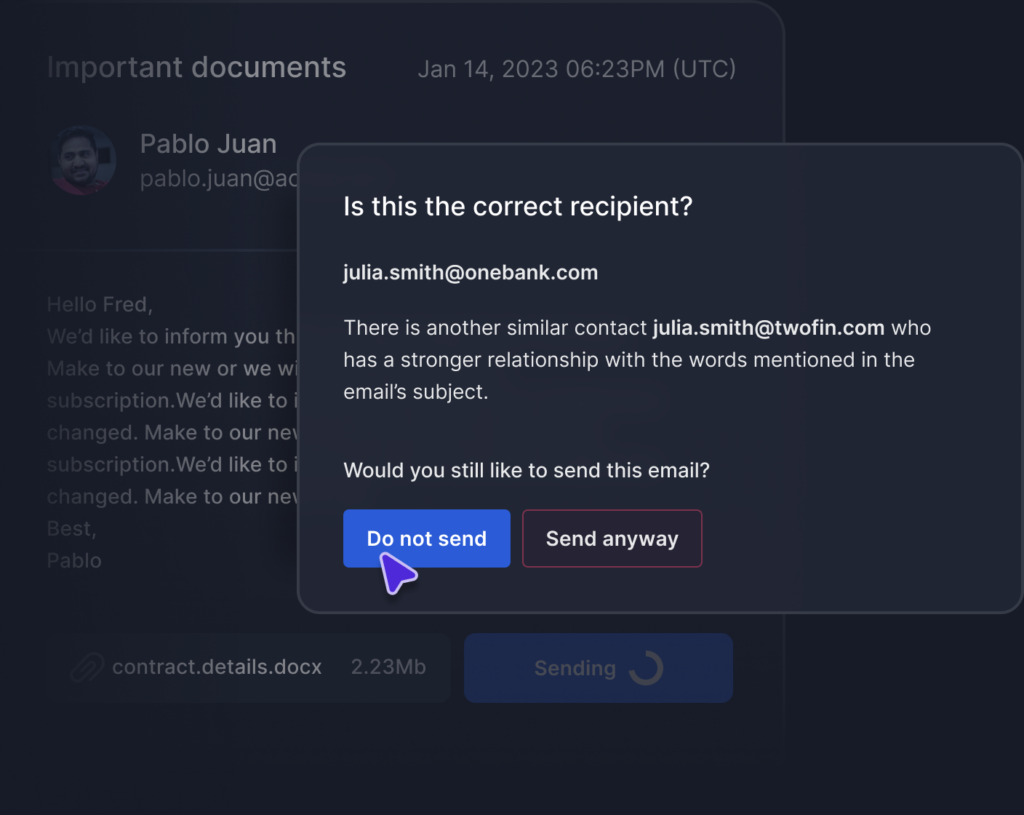
Protect against accidental data loss
Tessian AI uses behavioral and content analysis to warn users of an incorrect recipient before the email is sent.
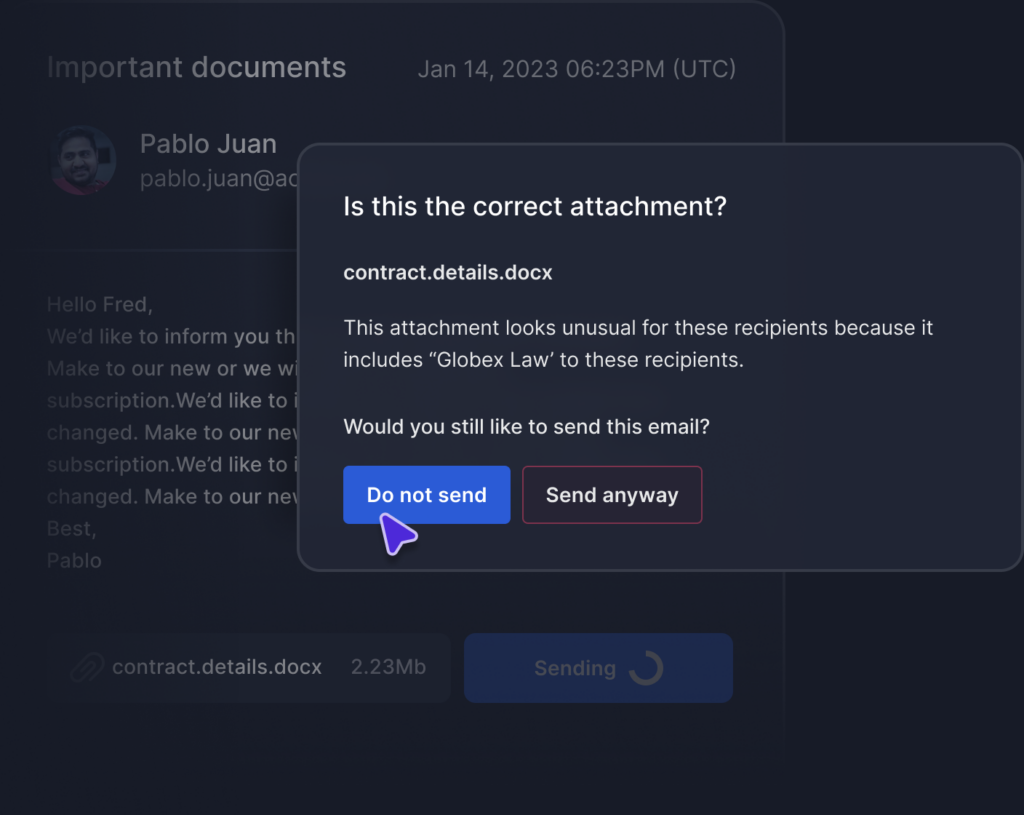
Tessian automatically warns users when the incorrect attachment has been added to an email, helping them remediate in real-time before sensitive information is inadvertently sent to the wrong person.
Eliminate insider risk over email
Automatic detection of legal, financial, HR terms, and sensitive documents while discovering personal email addresses beyond freemail domains.
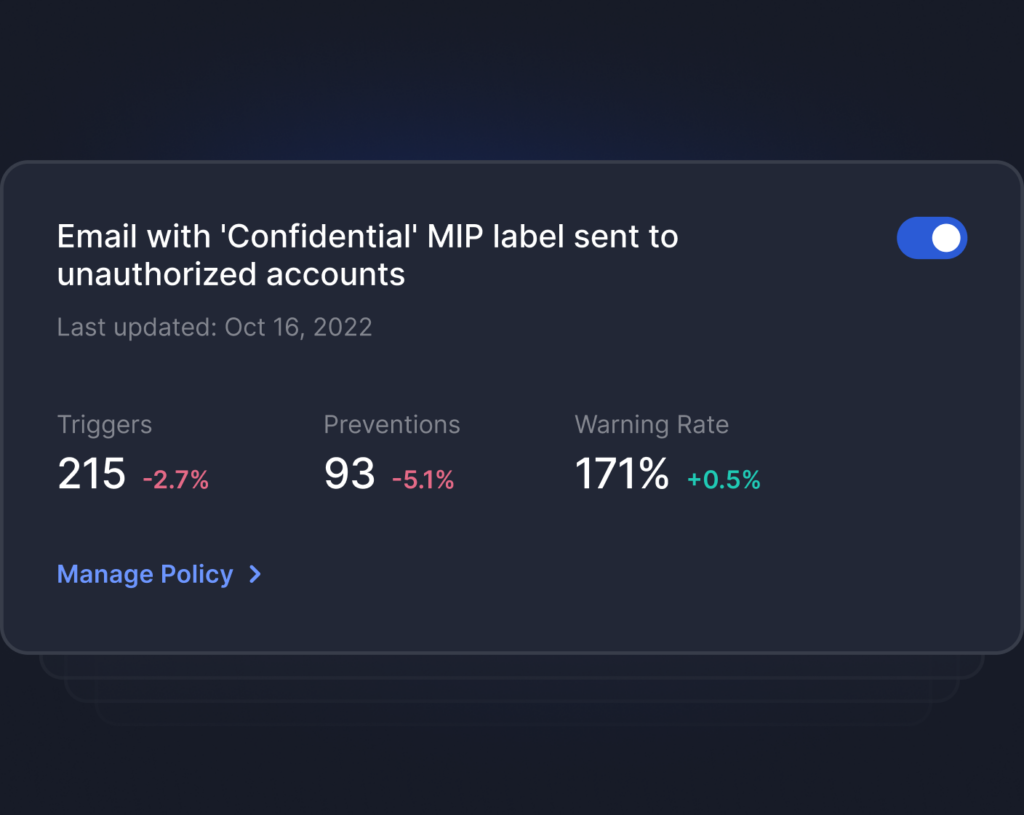
Detect when sensitive or restricted data is being sent to unauthorized or freemail accounts, and block or ask users to justify their actions.
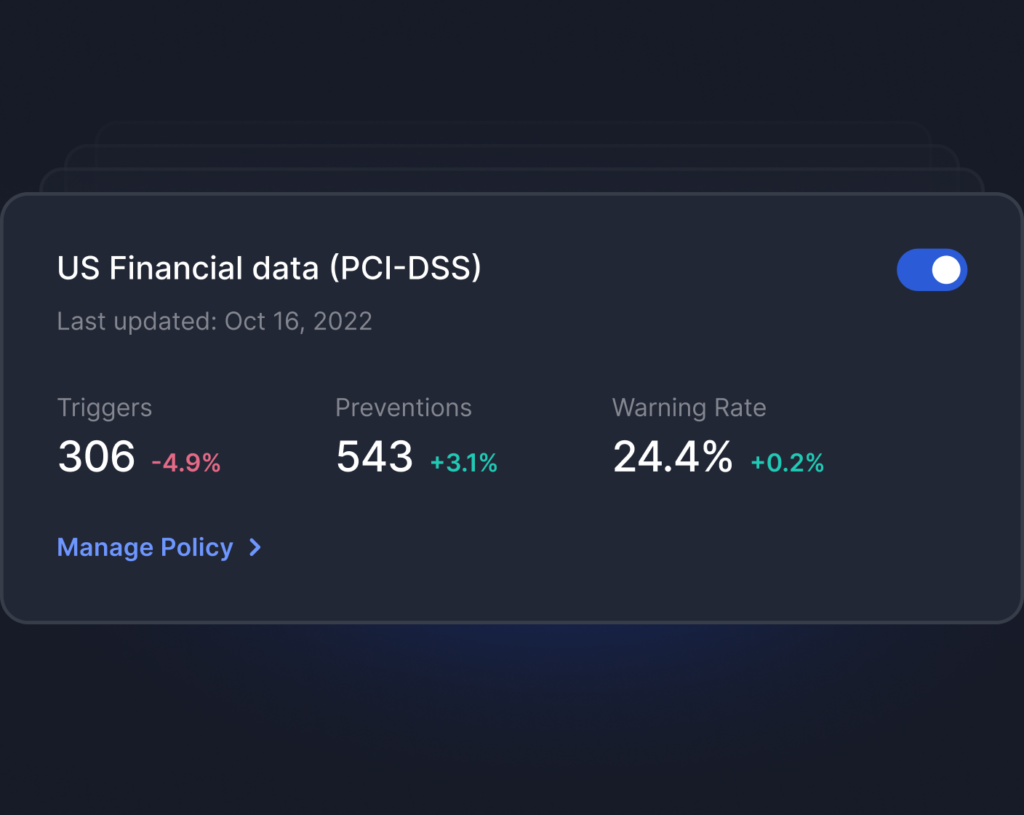
Create intelligent policies that blend machine learning with custom rules to prevent data loss while educating users in a non-intrusive way. The era of warning fatigue is over.
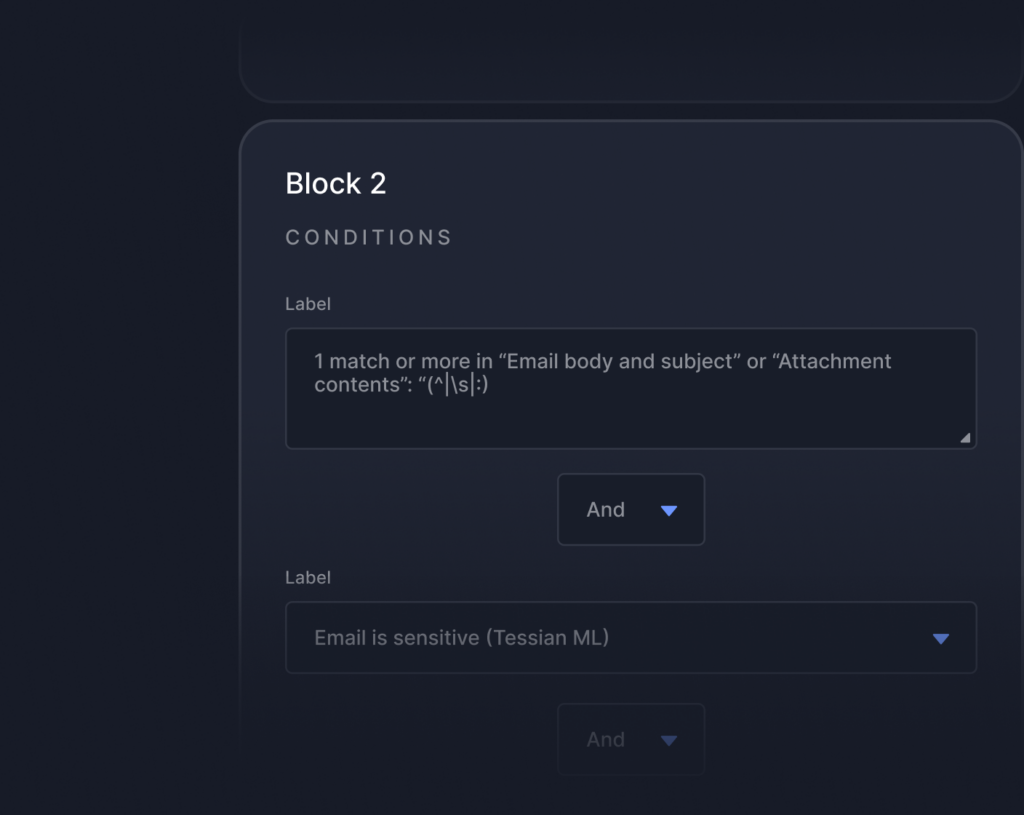
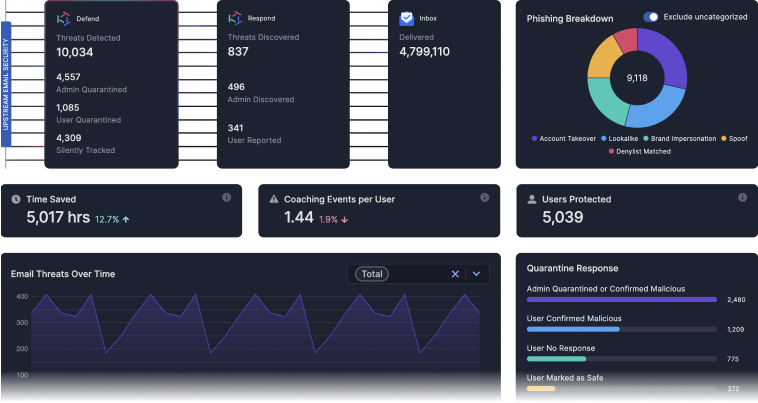
Insights that strengthen your email security
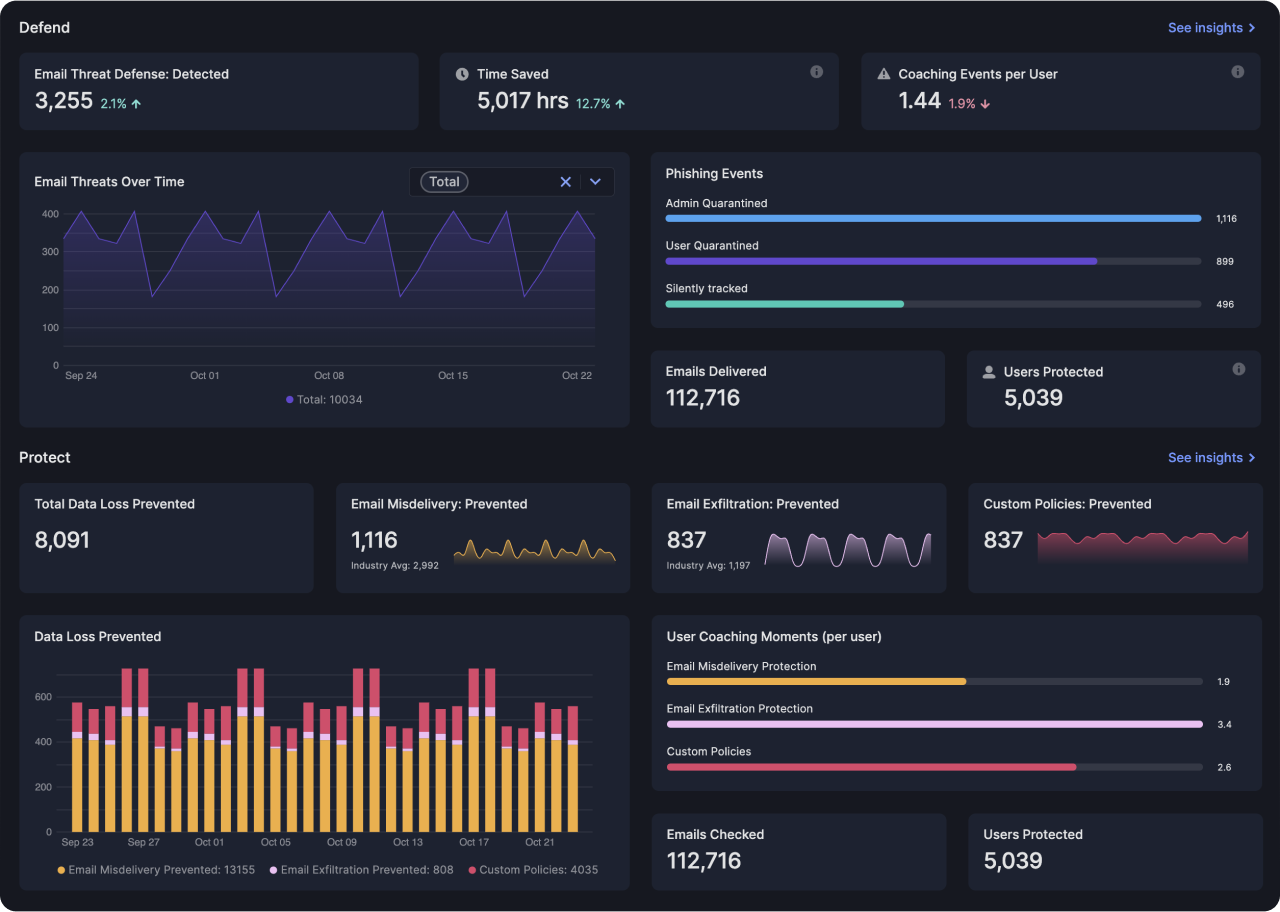
Complete cloud email security, deployed in minutes