Data Exfiltration
Negligent Data Exfiltration, occurs when an employee, knowingly or not, breaks internal data privacy policies and sends sensitive information to an undesired email address.
This often occurs when an employee sacrifices security for convenience, for example, to access work on a tablet for their commute or to print work documents on their home network.
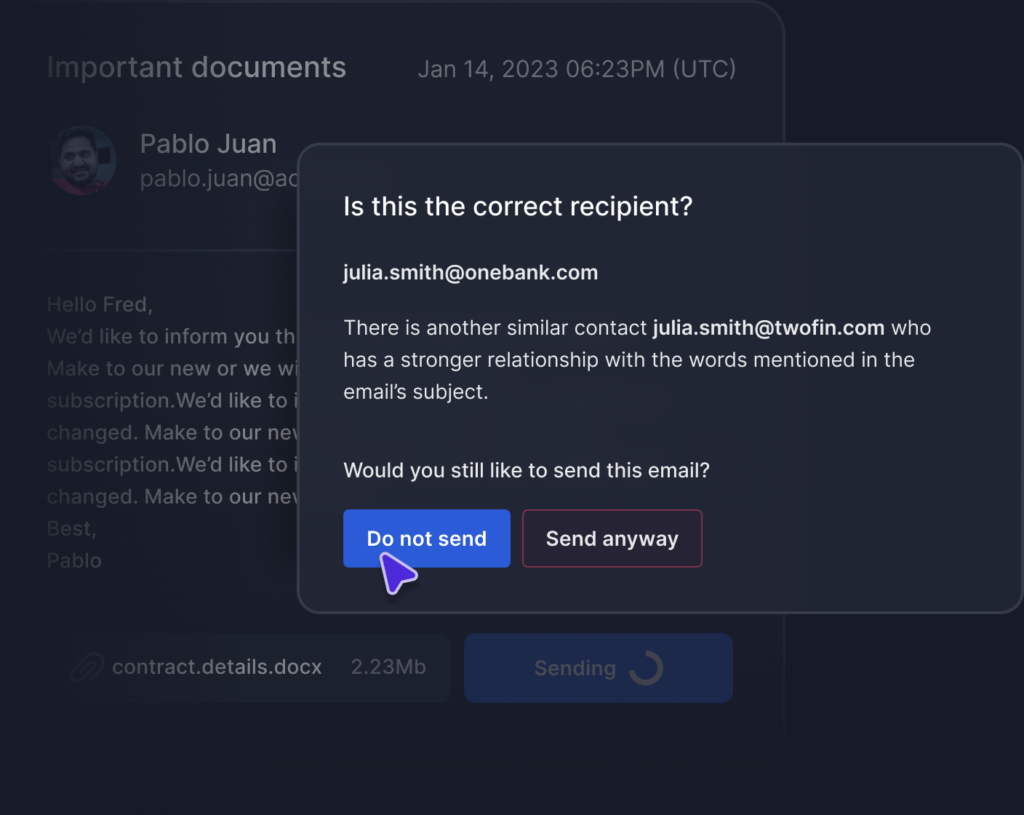
Malicious Data Exfiltration is often caused by a “Malicious Insider” or “Bad Leaver”, and occurs when confidential company information is stolen with the intent of personal or financial gain.
This often occurs when an employee is participating in Insider Trading, or is leaving the company and looking to take information and/or clients with them to their new organization.
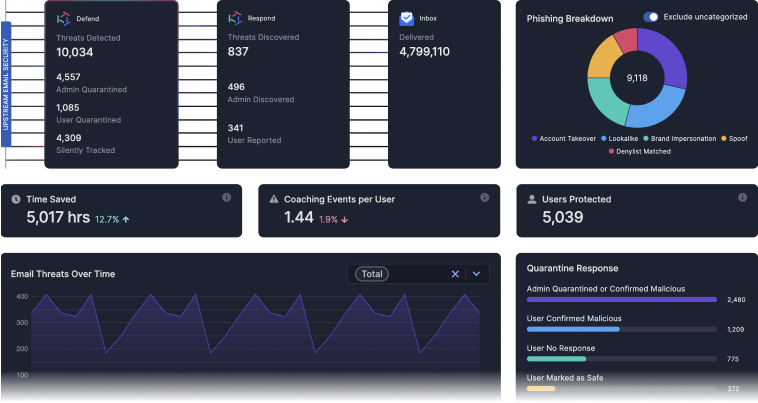
Tessian AI Explained
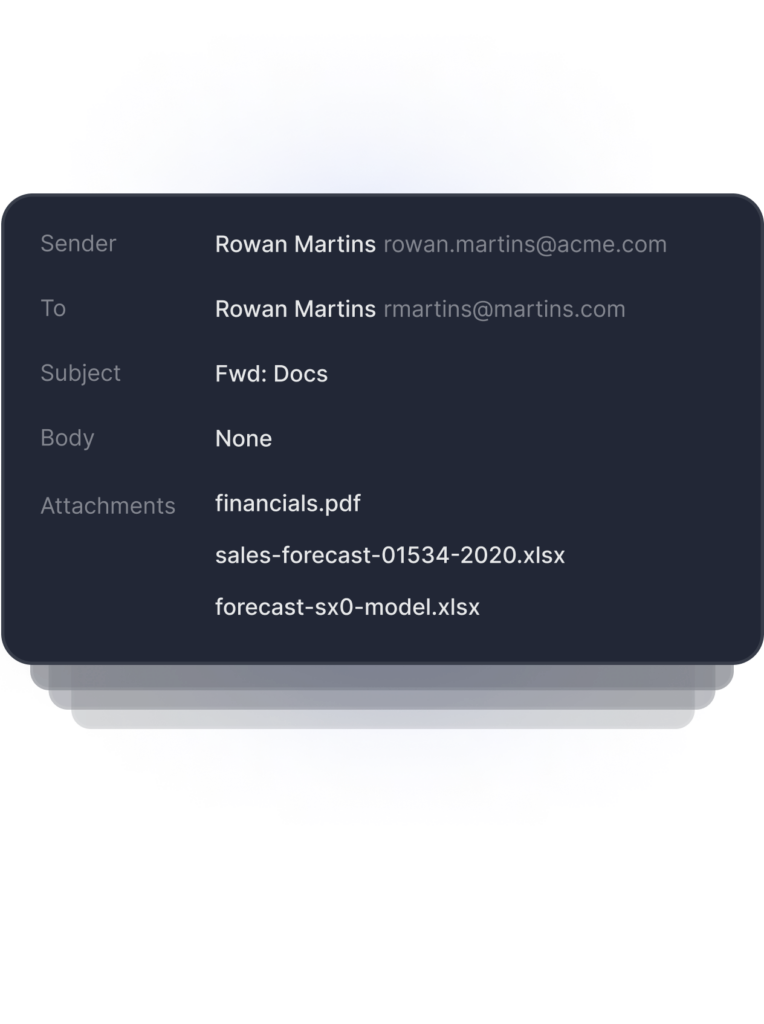
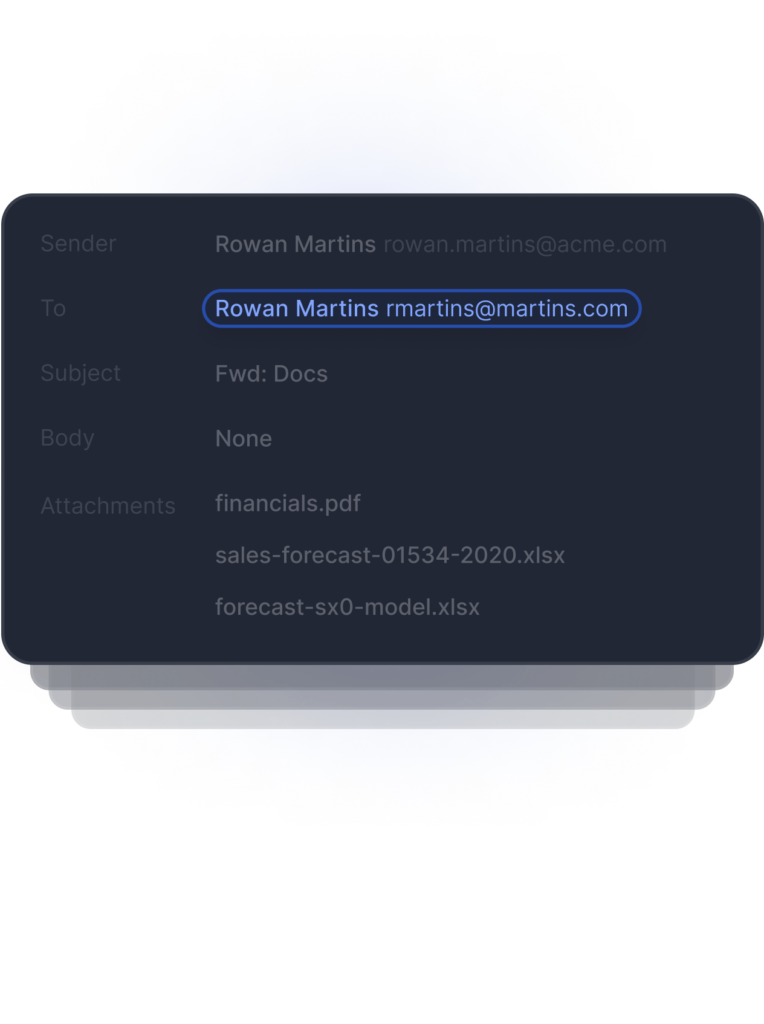
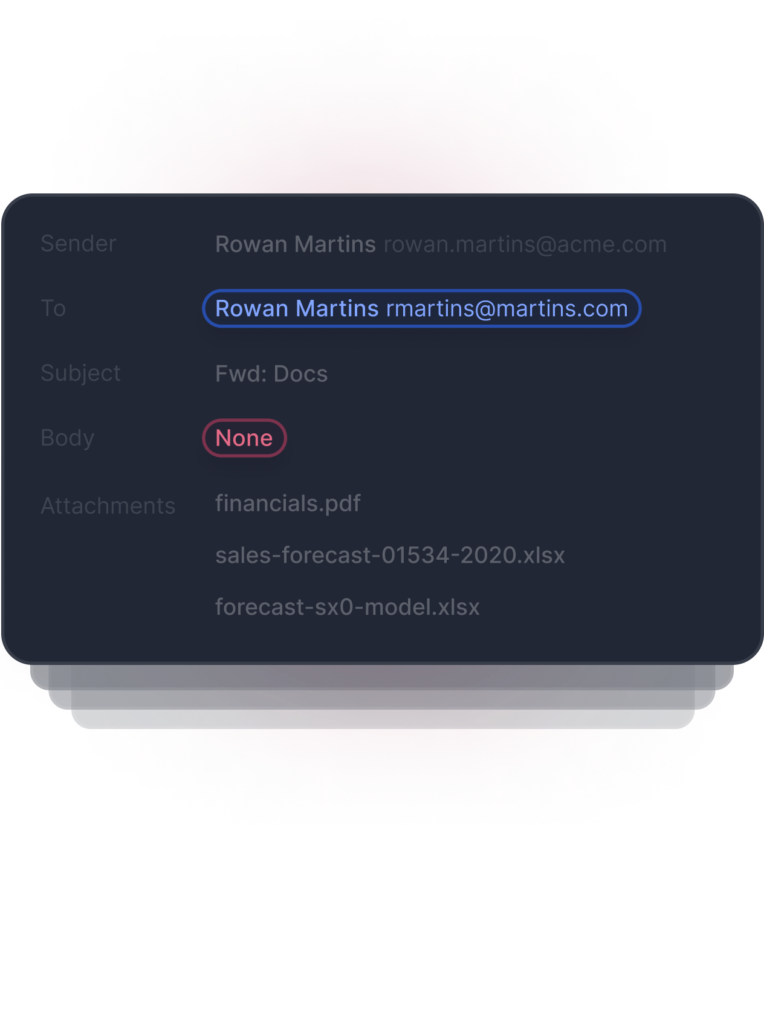
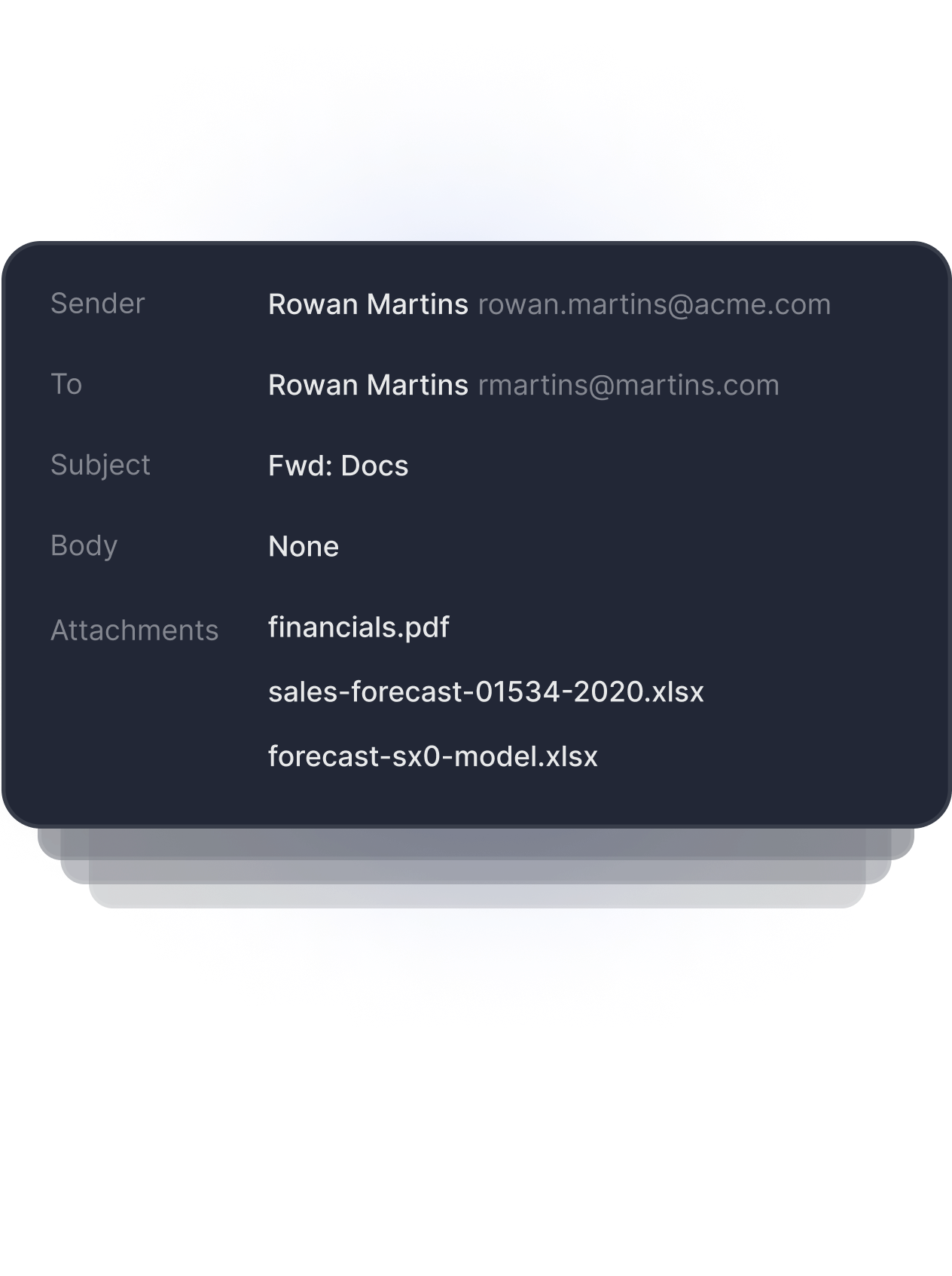
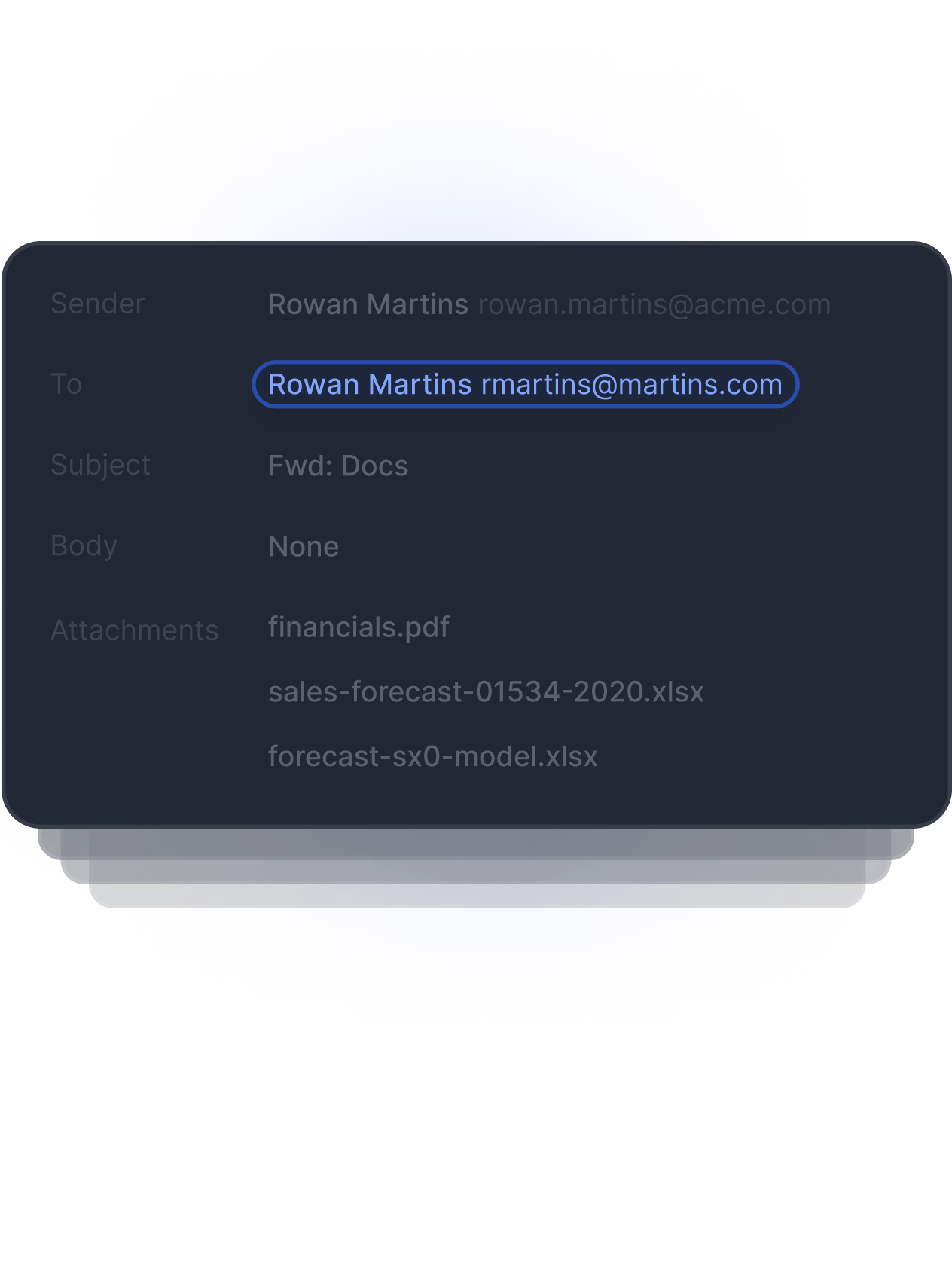
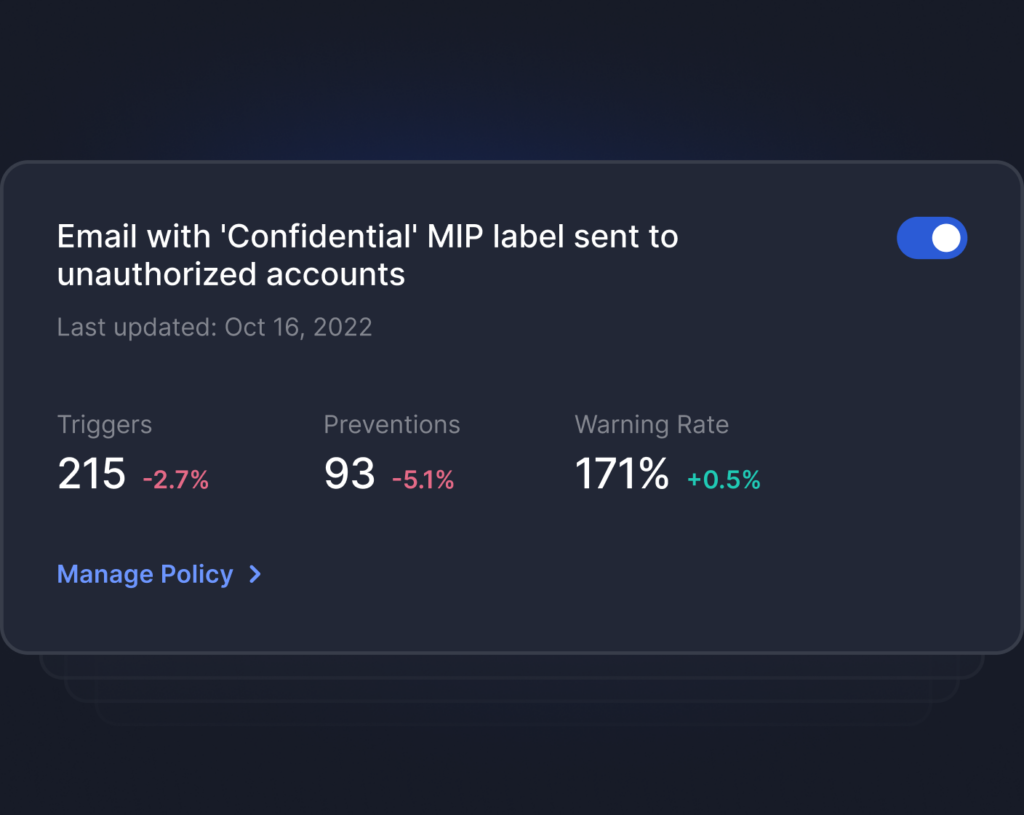
Detects Anomalous Recipient
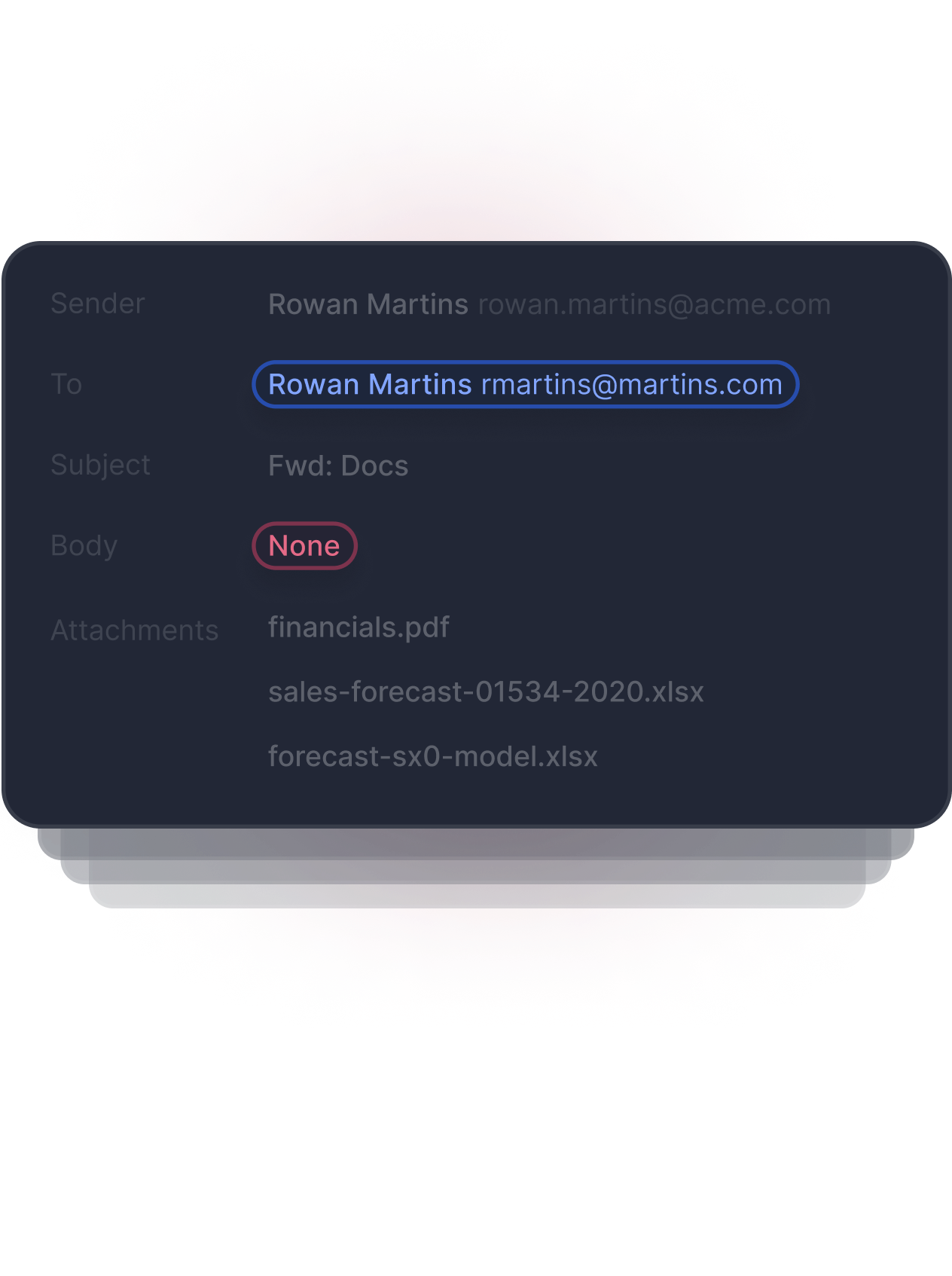
Detects Anomalous Content
Detects Anomalous Attachment
Simple stack that deploys in minutes
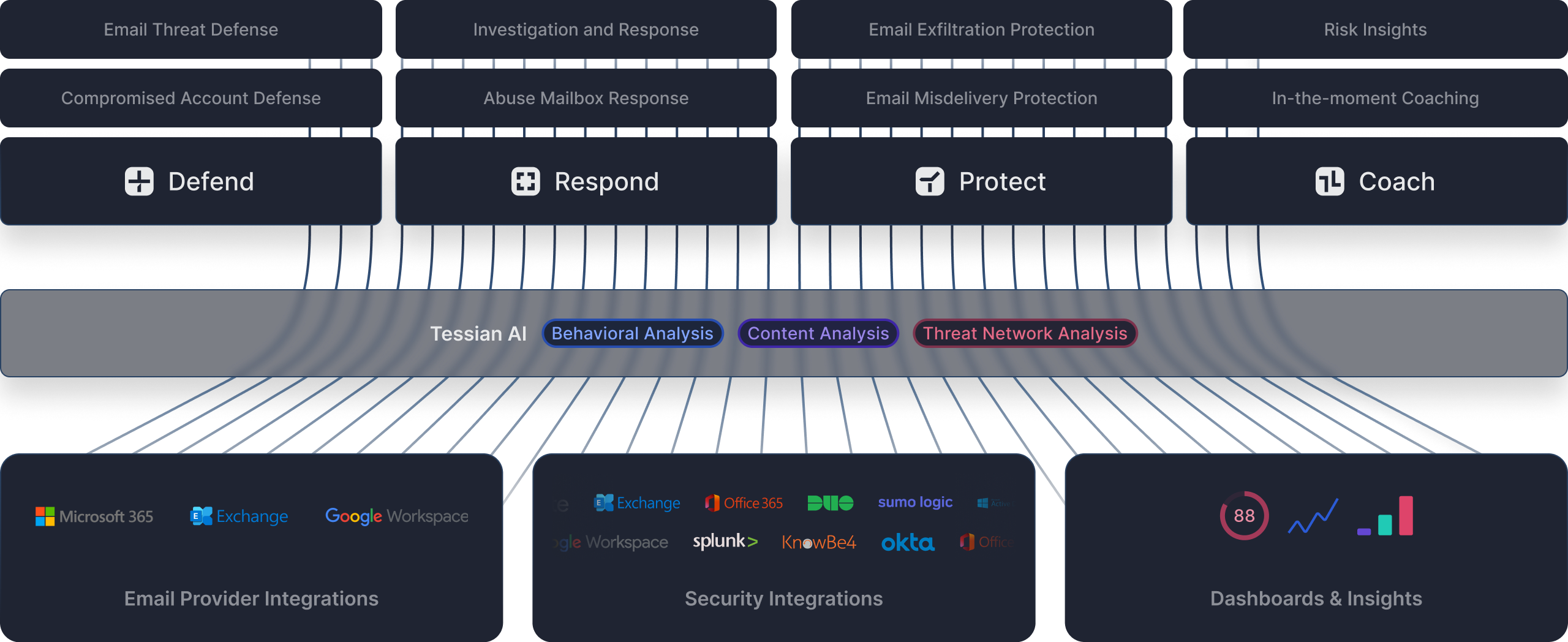
See Tessian in Action
-
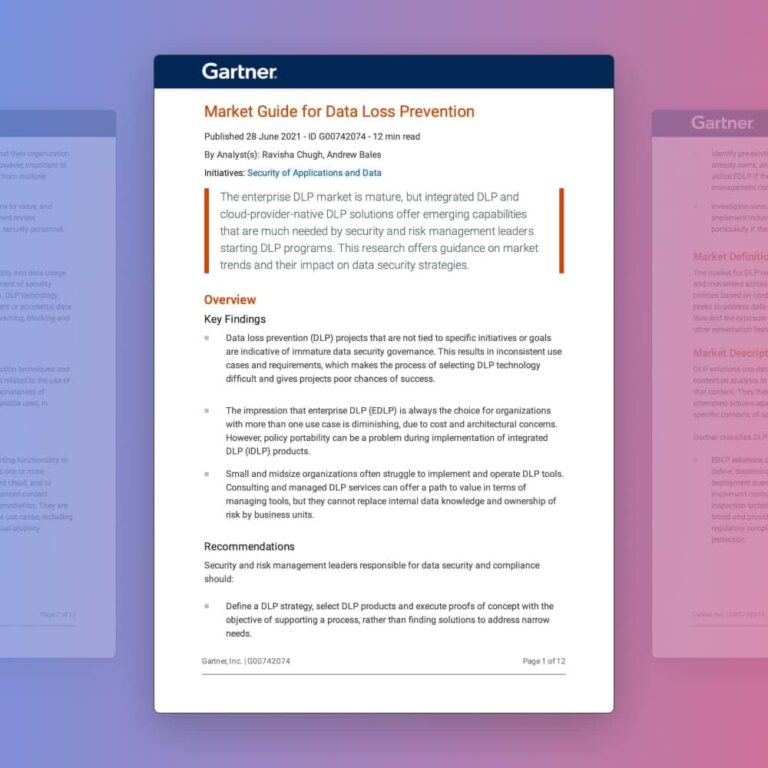
2021 Gartner® Market Guide For Data Loss Prevention
A must read guide for security and risk management leaders starting DLP programs to solve complex use cases. Get guidance on DLP market trends and their impact on data security strategies.Download Market Guide -

451 Research: DLP Market Insight Report
451 Research is a global IT analyst firm, part of S&P Global. Read 451 Research's analysis of Tessian's approach to email security using ML.Read the Full Report