With Business Email Compromise (BEC) attacks remaining the number one cybercrime in 2022, and 82% of data breaches involving humans – email continues to be the largest threat vector for any organization.
Organizations that have already begun adopting cloud-hosted productivity suites, like Microsoft 365, are finding an overlap in their native-security capabilities, which legacy email security solutions have traditionally addressed.
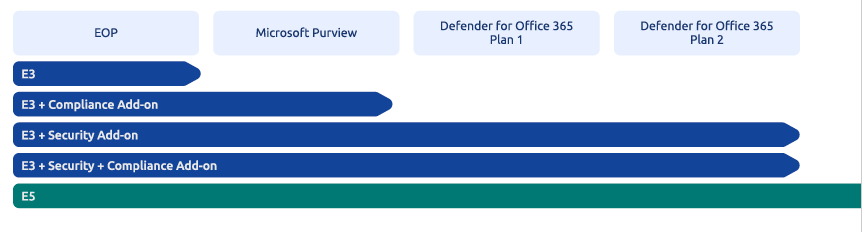
Microsoft has made significant strides in improving the native-security features built into their different licensing models. This allows security leaders to reduce cost and complexity within their security stack, as the email security capabilities offered by Microsoft 365 mirror that of a Secure Email Gateway (SEG):
- Traditional Email Security
- URL & Attachment Protection
- Manual Investigation & Response
- Rule-Based DLP Policies
These overlapping capabilities have given security leaders a good enough option to move beyond legacy SEGs, but understanding what is included within each Microsoft licensing model is key to effectively securing an organization’s email environment. Microsoft offers various packaging bundles and add-ons, allowing flexibility for security leaders to maintain the same level of protection offered by their legacy gateway solutions.
Microsoft 365 Tessian Guide
Is good enough really good enough?
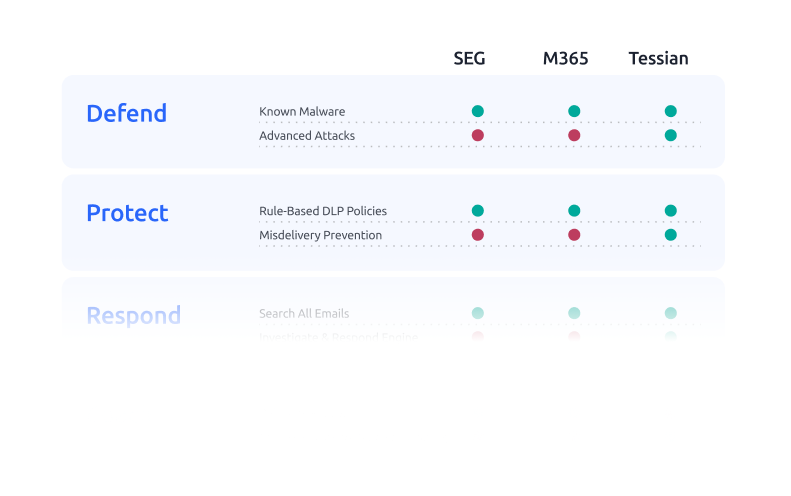
The global shift to a remote workforce has also opened up new threat vectors and emerging attack types that security leaders are still struggling to prevent. Round-the-clock access to sensitive data has increased the human risk of malicious, negligent, and accidental data loss. Attackers are leveraging social engineering to trick end-users by abusing trusted relationships. Relying solely on traditional detection methods to defend against advanced attacks and rule-based policies to protect against insider risk, is leaving organizations more vulnerable than ever before.
A more intelligent approach is needed. Organizations can continue to rely on traditional detection methods to filter out bulk phishing and spam, but simply put, scanning for malicious signatures based on known threat intelligence doesn’t stop the advanced threats that security leaders face today.
Microsoft 365 Tessian Guide
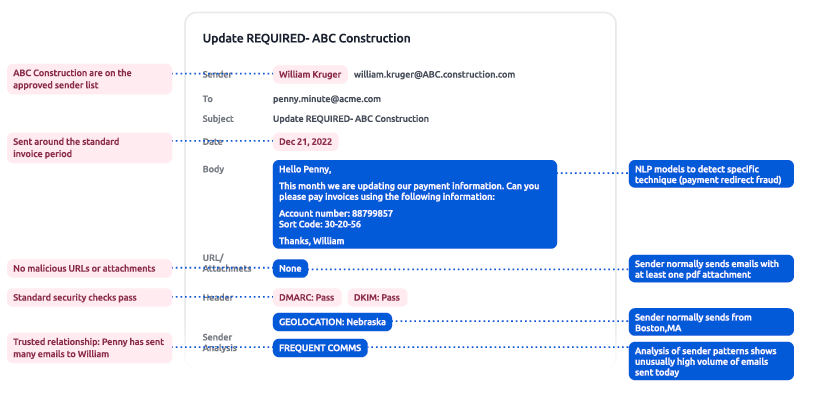
There is, however, a solution. The advanced detection capabilities of an Integrated Cloud Email Security (ICES) solution close the gaps where legacy, rule-based detection or current Microsoft tools fall short. ICES solutions employ advanced machine learning to map an organization’s typical email behavior and detect unusual communication patterns, providing a more accurate defence against BEC attacks. In addition, ICES solutions can warn end-users of potential misdirected emails or instances of sensitive data loss.
“Tessian stops the threats that you just can’t make a rule for. The platform really has evolved along with our own security stack and with the risk environment. It reinforces our training and complements Microsoft”
Mike Vieira
Cloud and Perimeter Security Capability Lead, Schroders
In this Solution Guide, we discuss the decline of legacy gateway solutions, how to reduce cost & complexity by migrating to Microsoft 365, and what email security capabilities are available in each Microsoft licensing package. In the end, readers will understand how Tessian + Microsoft 365 enables the most complete Integrated Cloud Email Security platform.
Microsoft 365 Tessian Guide
Bob Boyle
Product Marketing Manager II















