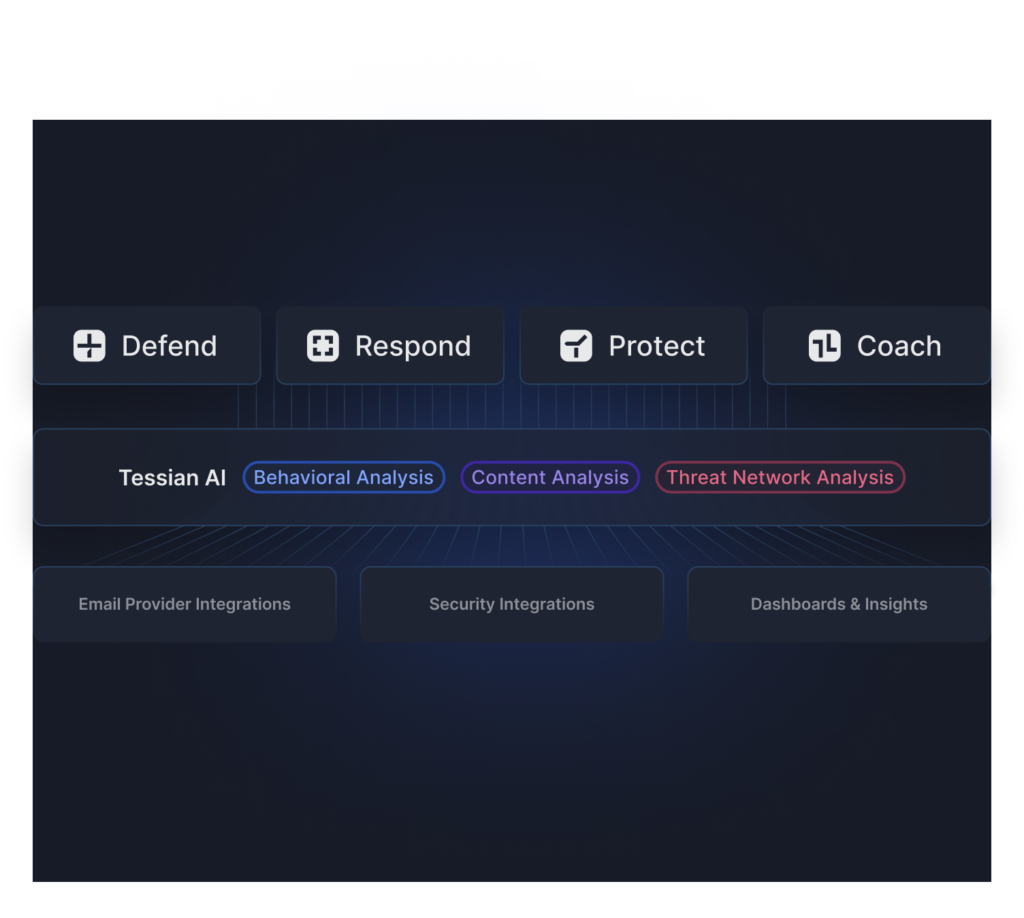
Smarter defense.Stronger protection.Faster response.Effective coaching.
One intelligent platform for complete cloud email security
Tessian uses behavioral, content and threat network analysis to detect and prevent the full spectrum of email attacks, including ransomware, account takeover (ATO), business email compromise (BEC).
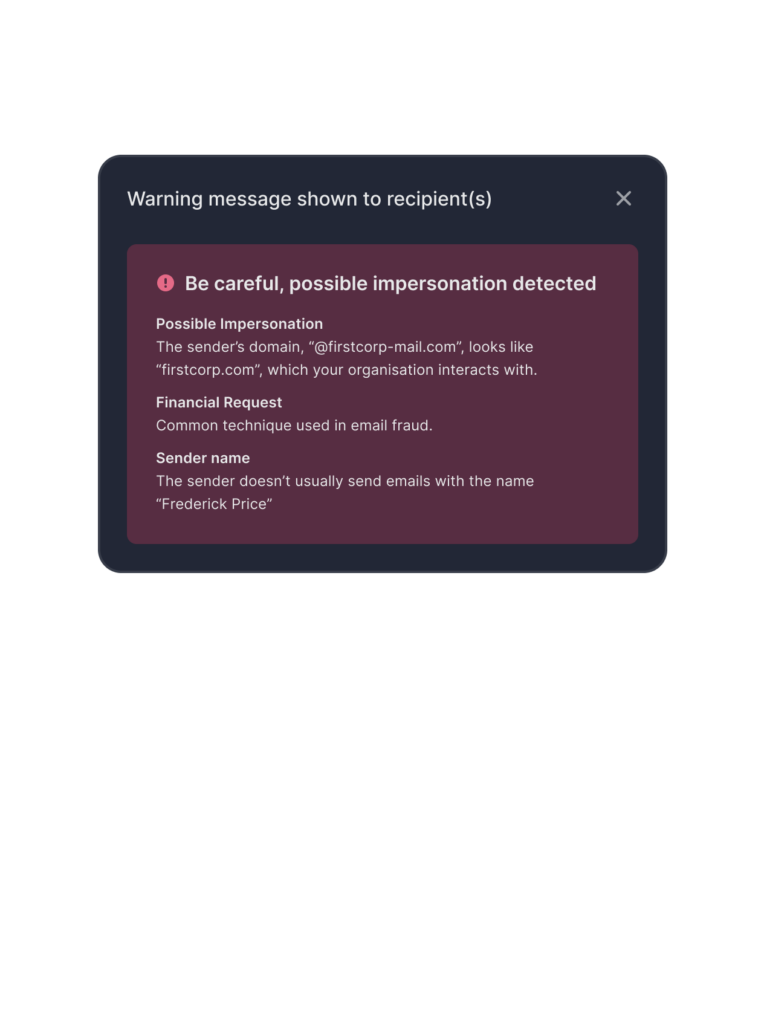
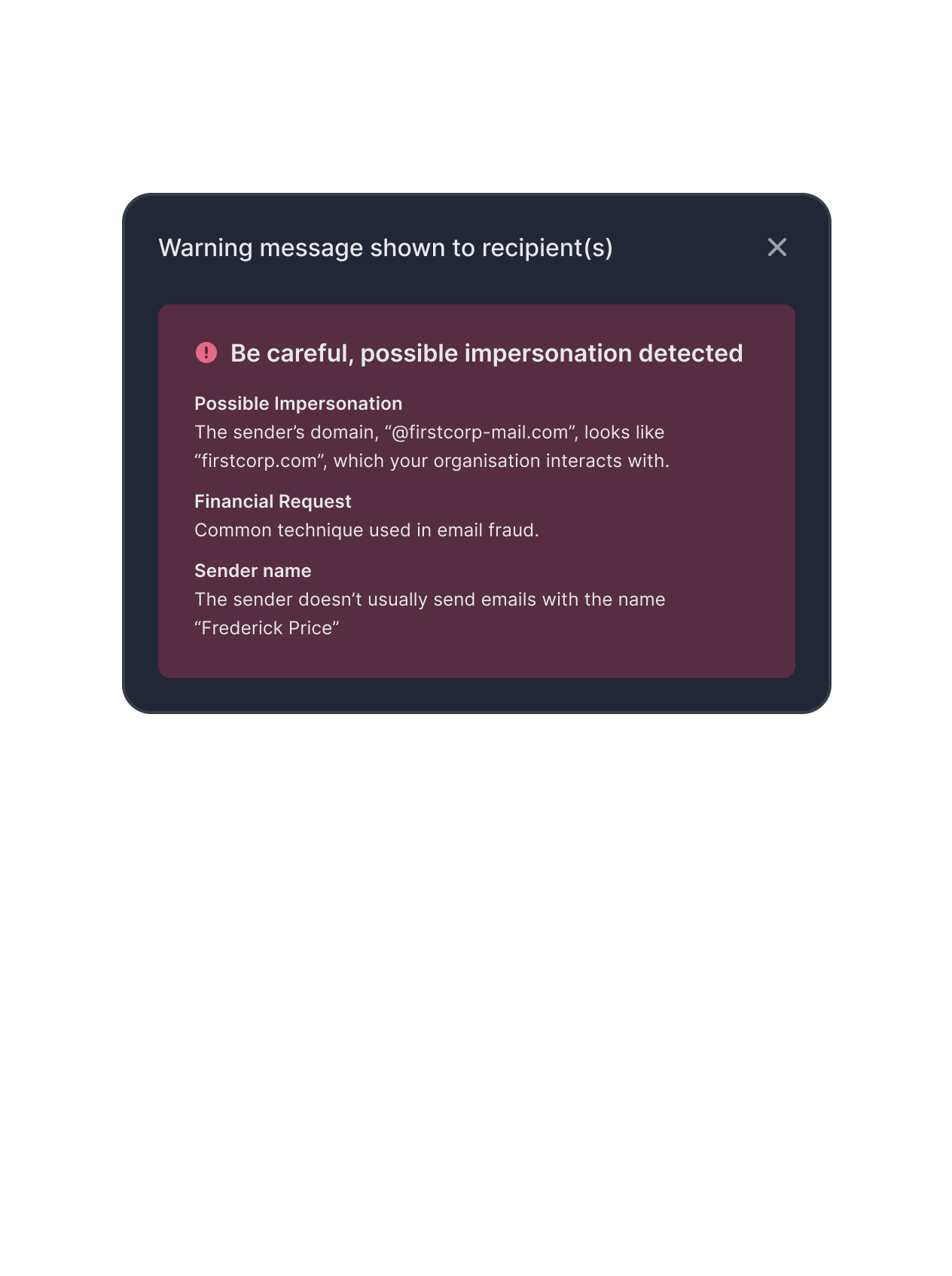
Smarter defense against phishing, stronger protection of your data
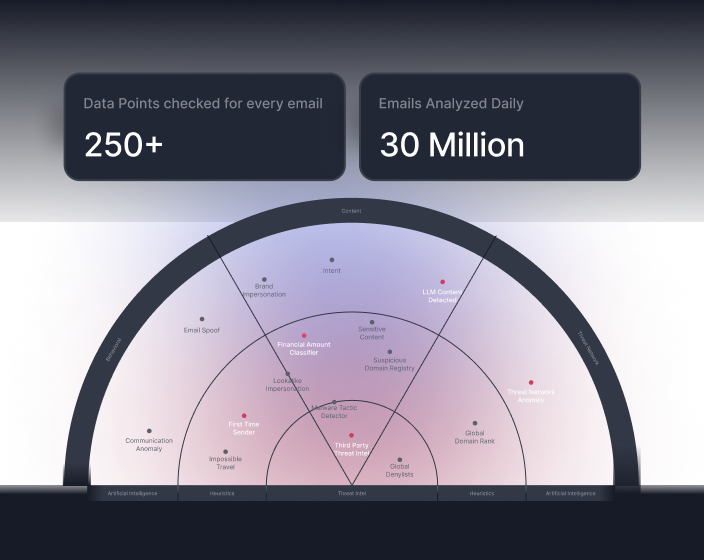
Tessian AI detects sophisticated, targeted email threats, and is purpose built to stop attacks that can’t be caught with signatures or rules. It uses an ensemble model consisting of multiple machine learning models including:
- Deep learning
- Large language models
- Topic clustering
- Natural language processing
- Time series anomaly detection
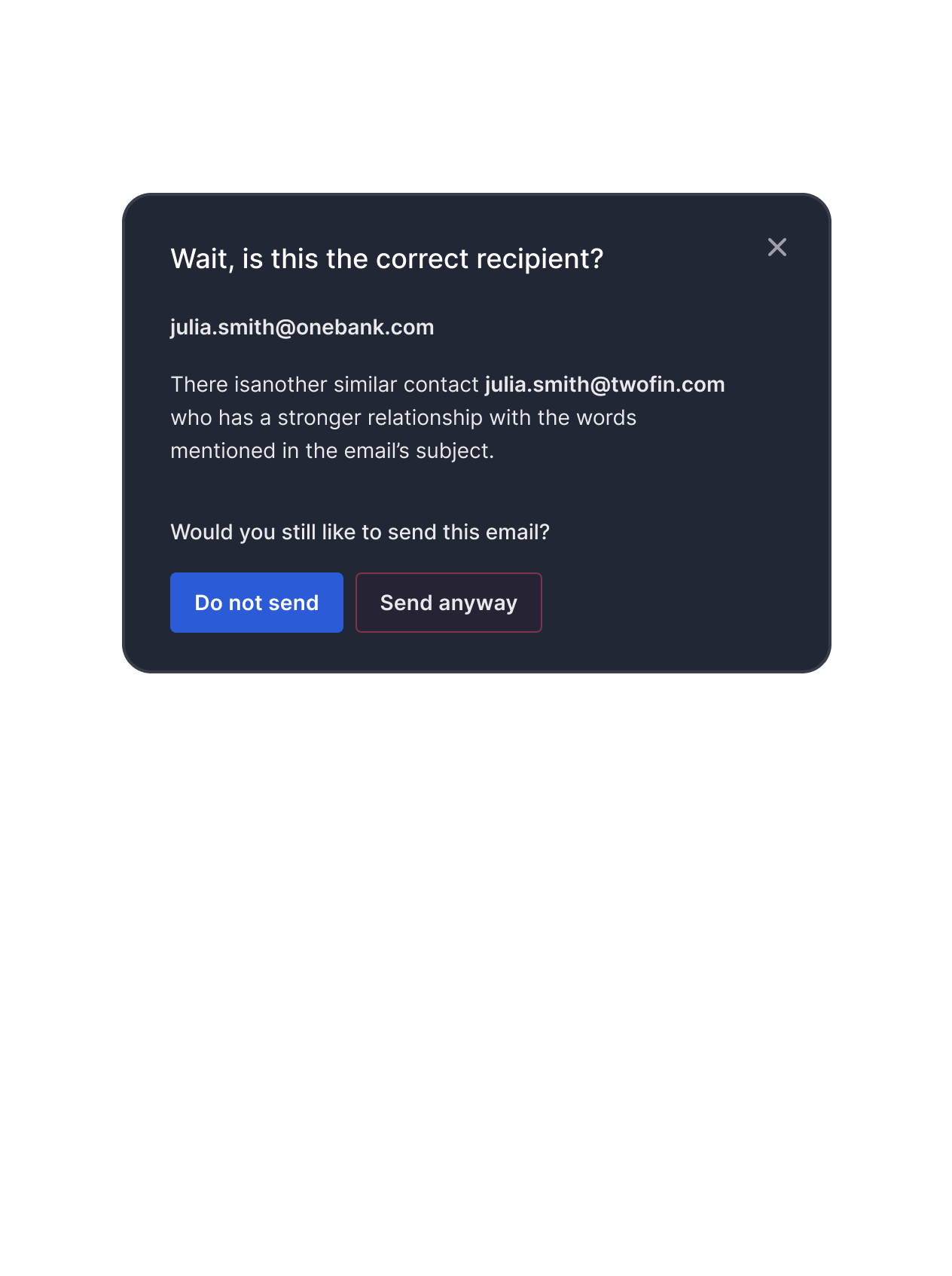
With these methods, Tessian learns an employee’s trusted relationships, the topics and projects they communicate about and what data they handle to stop phishing attacks and protect sensitive data.
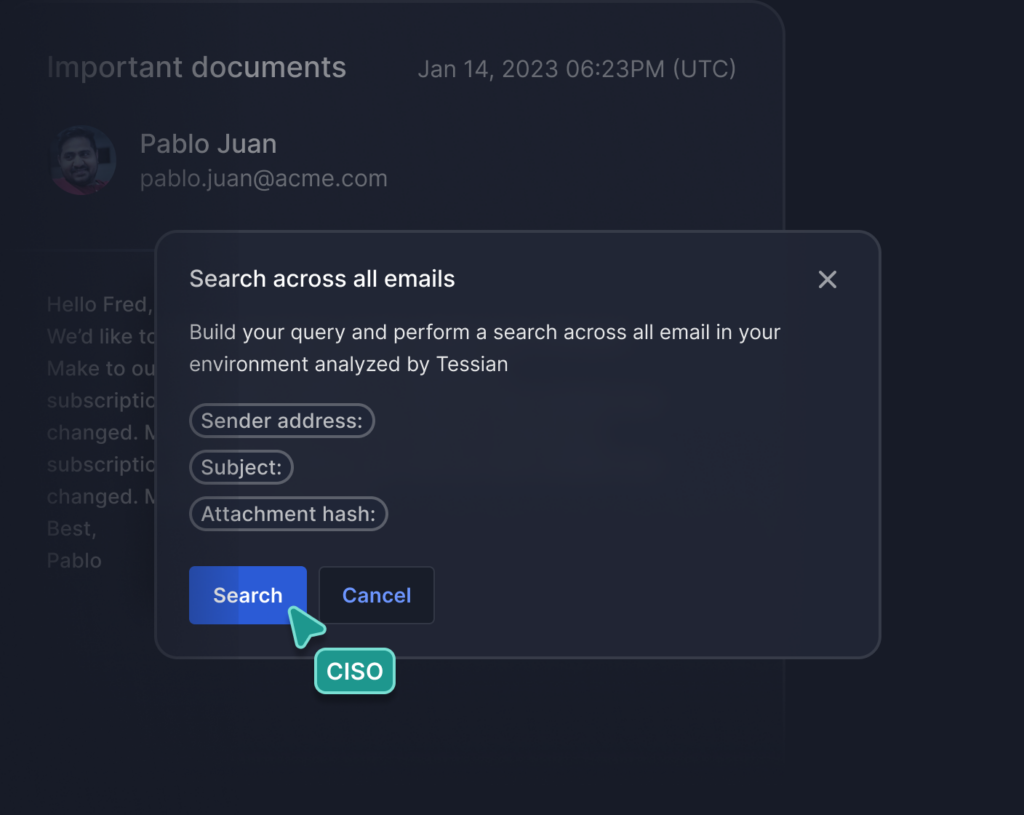
Rapid Email Incident Response
Search across the full body of millions of emails, get results in less than a second
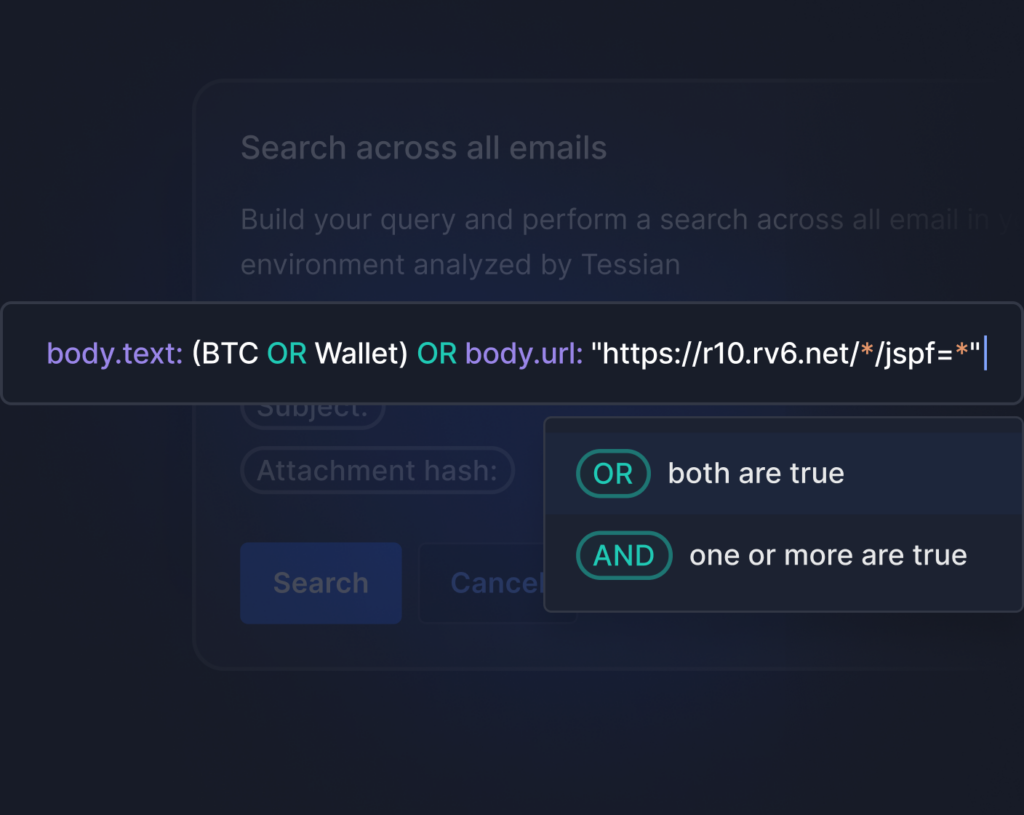
No more copying and pasting. Build searches directly within email events.
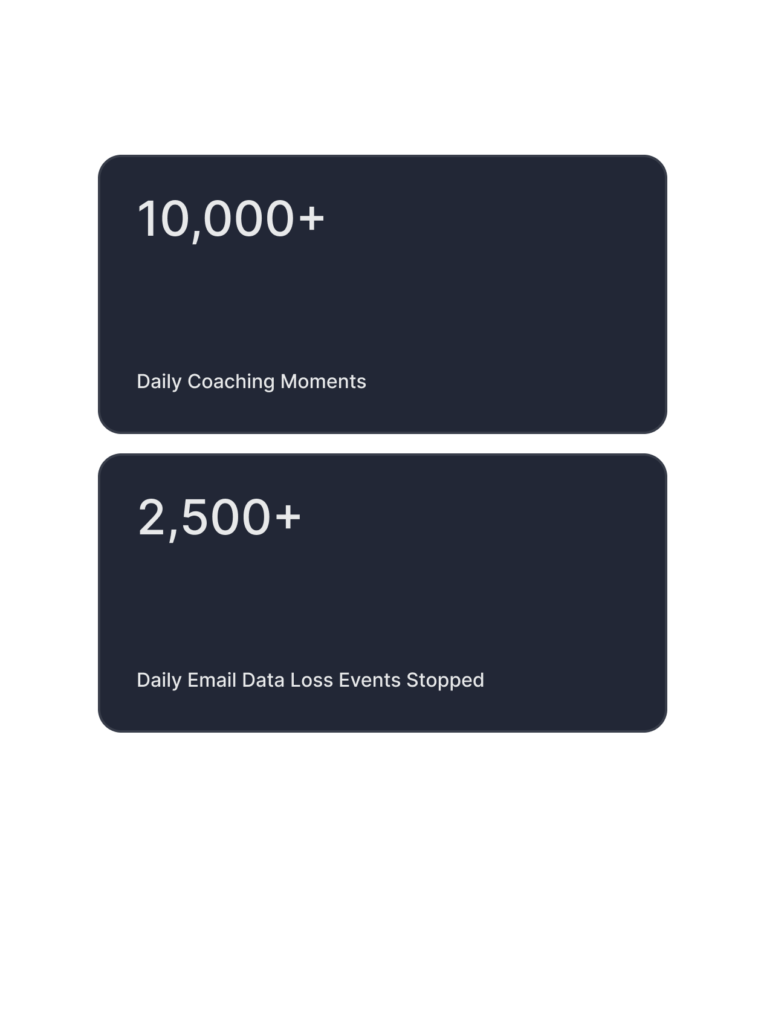
Tessian automatically classifies and remediates 90% of user reported emails as safe.
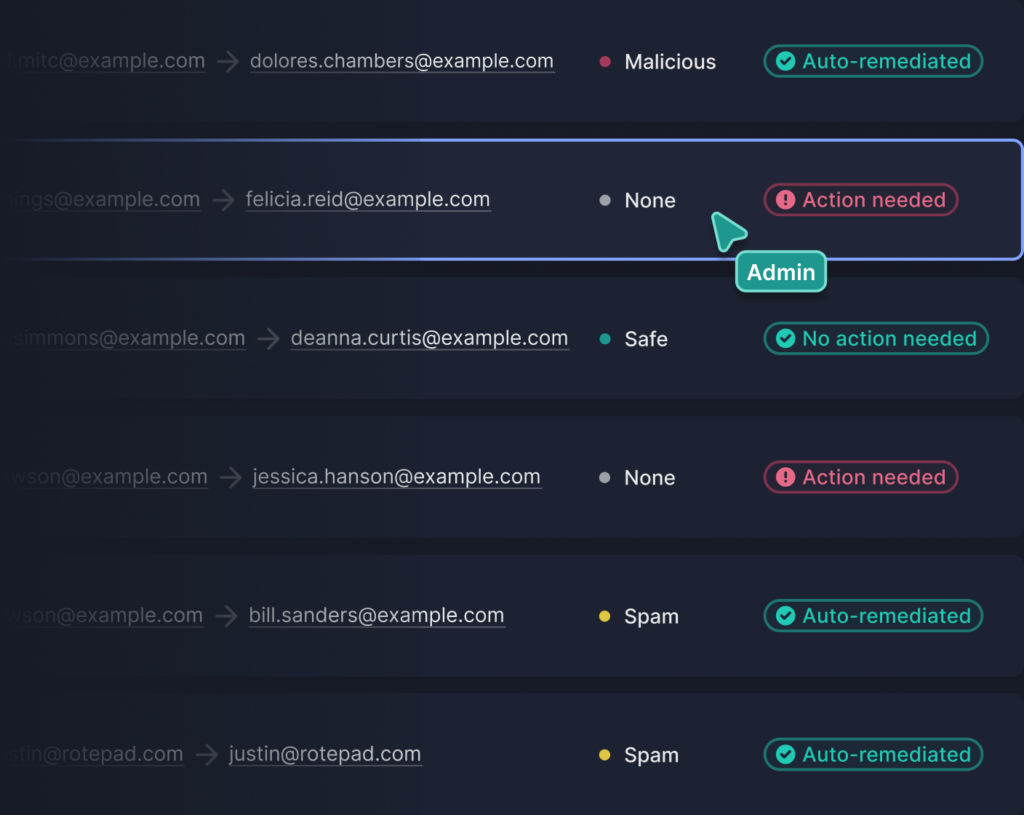
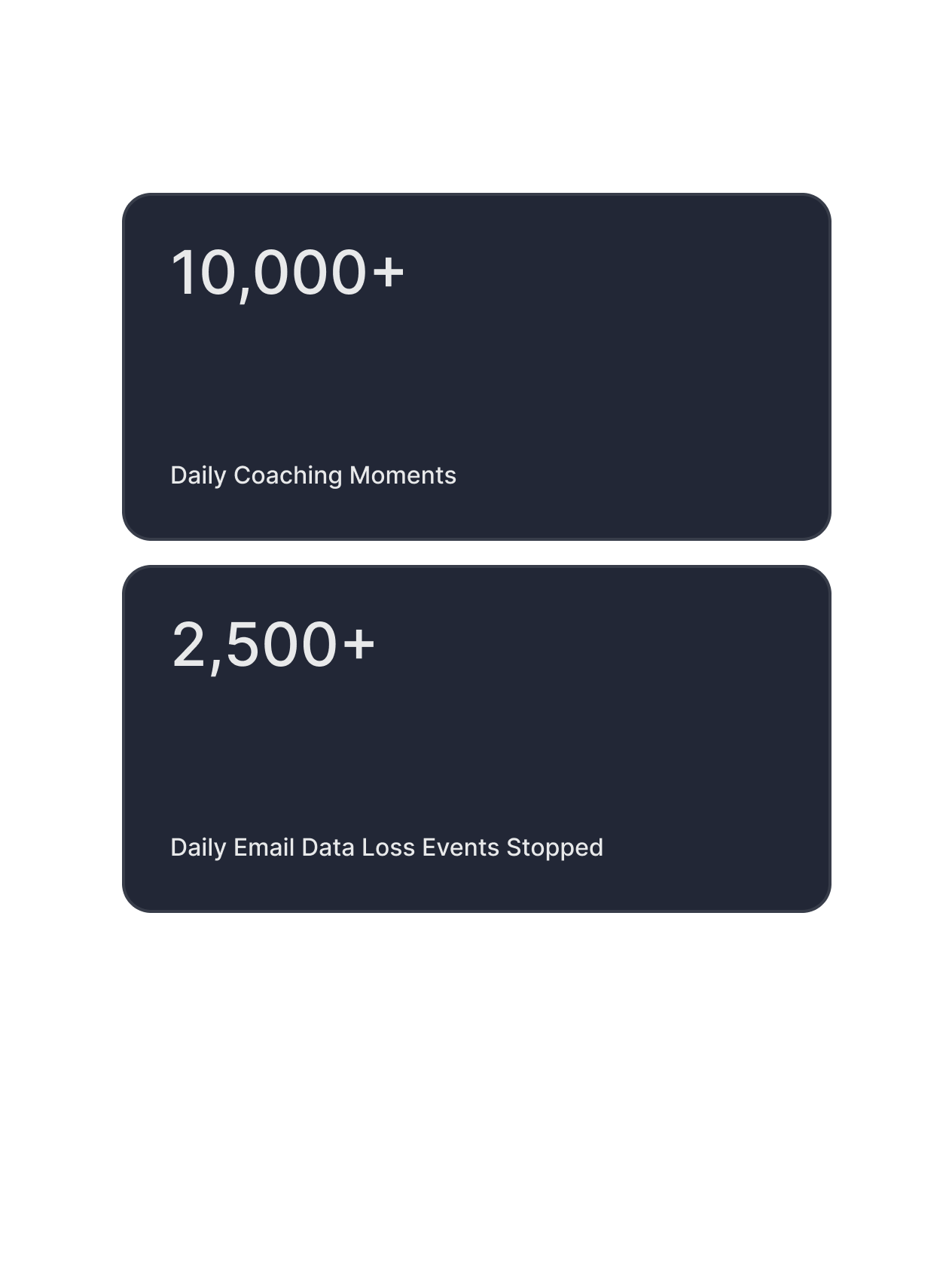
High impact, in-the-moment coaching
Engaging with Phishing Emails
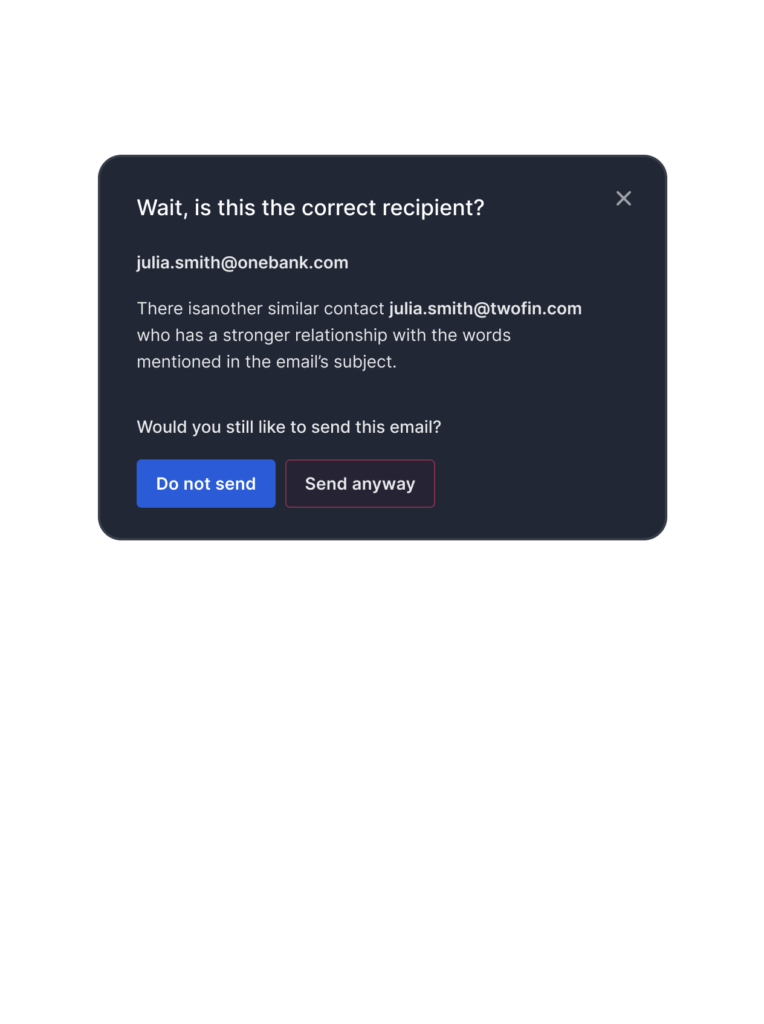
Misdirecting Emails and Attachments
Exfiltrating Data to Themselves and Others
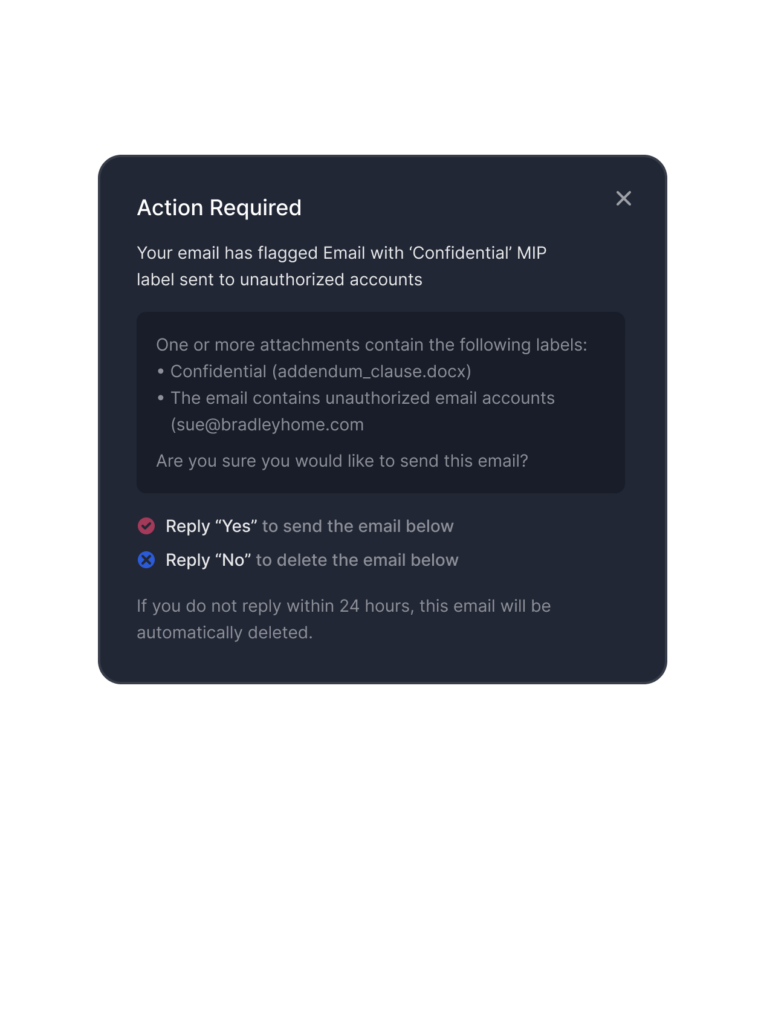
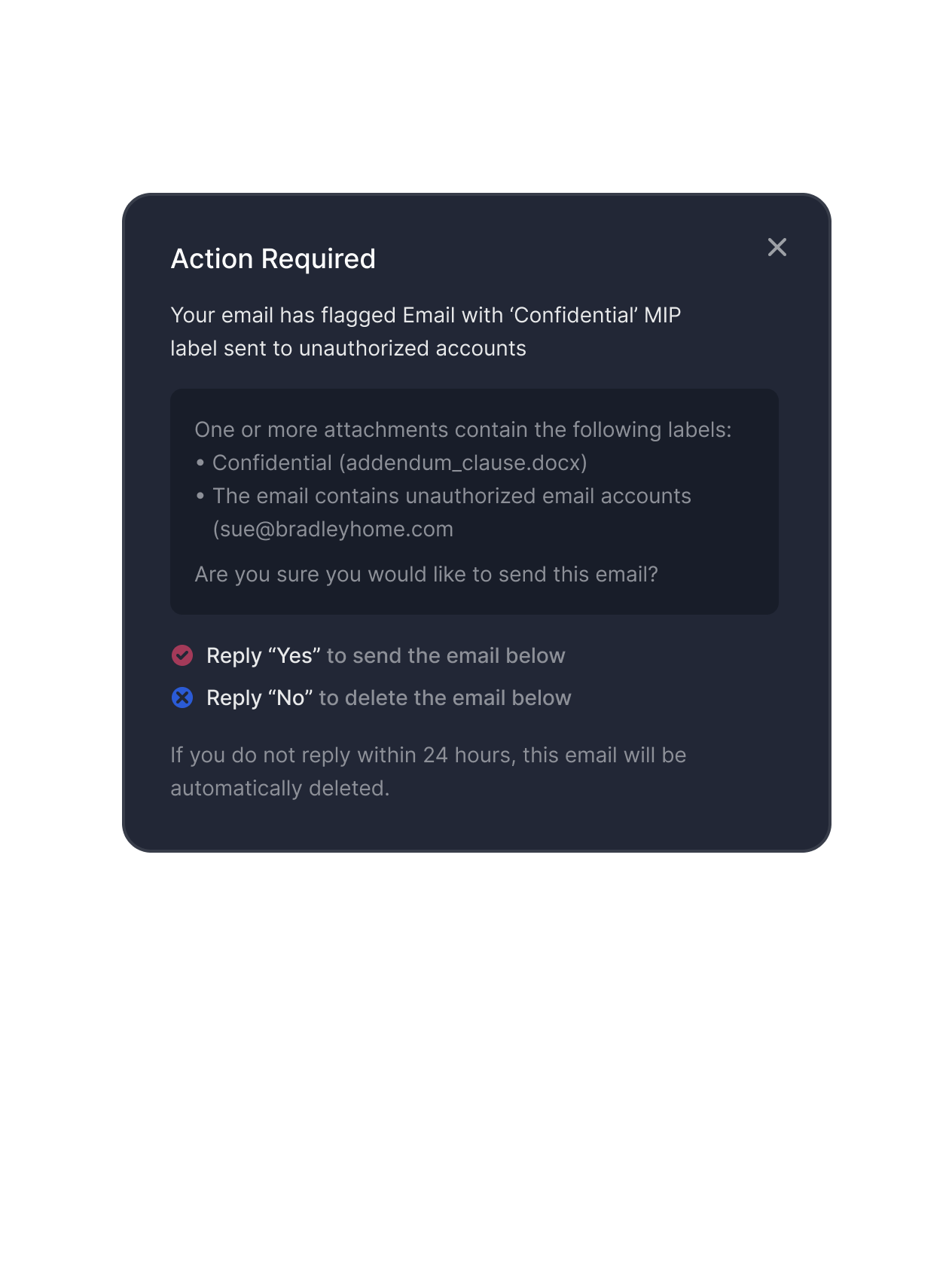
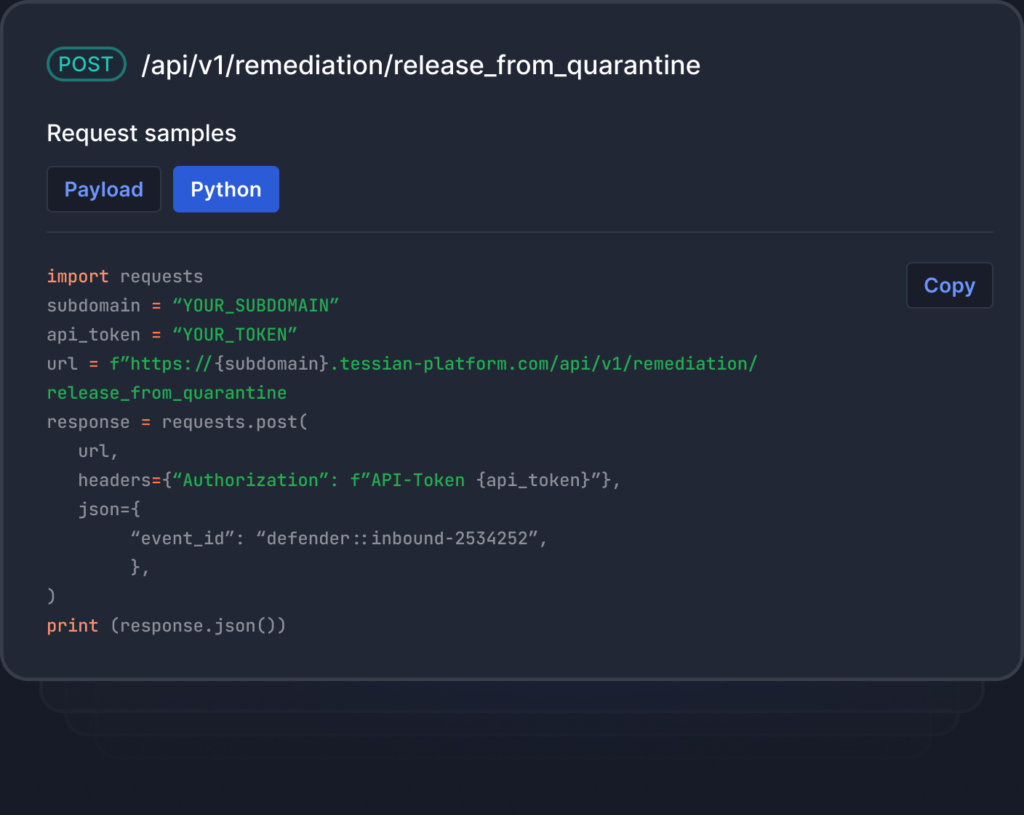
We offer full lifecycle email threat remediation via API, which saves your security admins time, while keeping them in their SIEM and SOAR platforms of choice. Admins can delete emails from user inboxes using our API, while effortlessly pulling critical information, including quarantine status, admin label and deletion counts for inbound and outbound emails.
featured resources
-

16 Tips to get Executive Buy-In for Security Solutions
We talked to security leaders from the world’s most trusted institutions to find out how they get buy-in for security solutions from the C-suite.Download eBook Now -
2021 Gartner® Market Guide For Data Loss Prevention
A must read guide for security and risk management leaders starting DLP programs to solve complex use cases. Get guidance on DLP market trends and their impact on data security strategies.Download Market Guide