THREAT TYPE
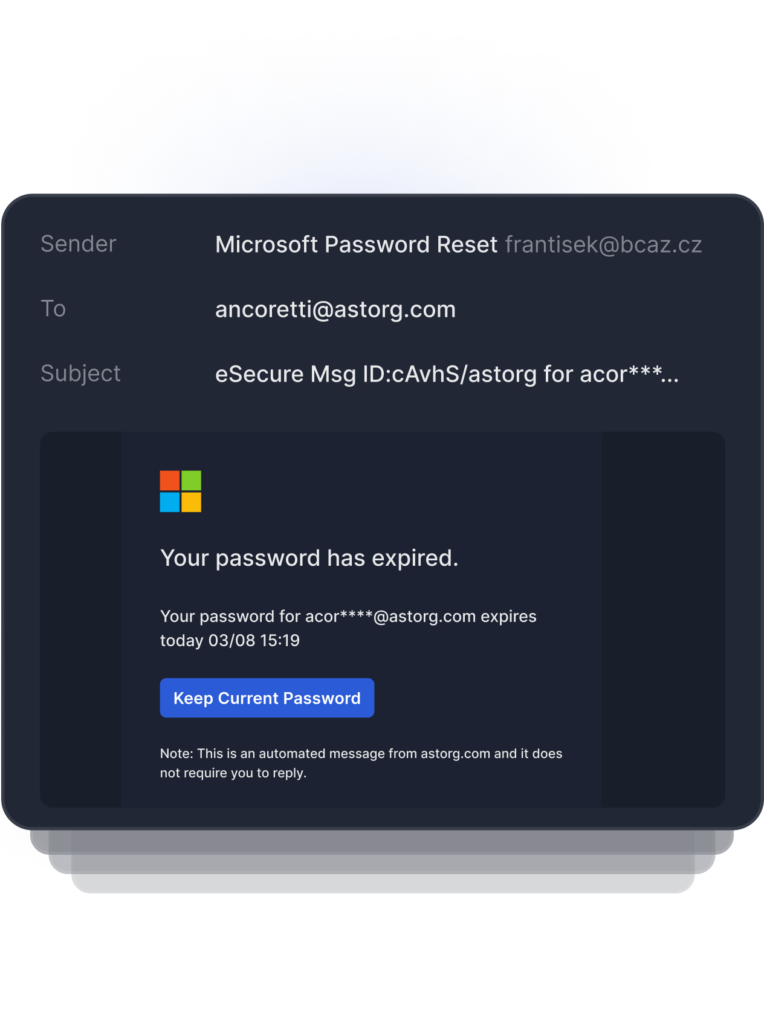
Vendor Email Compromise
Also known as a Supply Chain Attack, a VEC attack is when the attacker targets a company's trusted third-party vendors, suppliers, or partners to gain unauthorized access to the organization.
AI BASED THREAT DETECTION
Tessian AI Explained
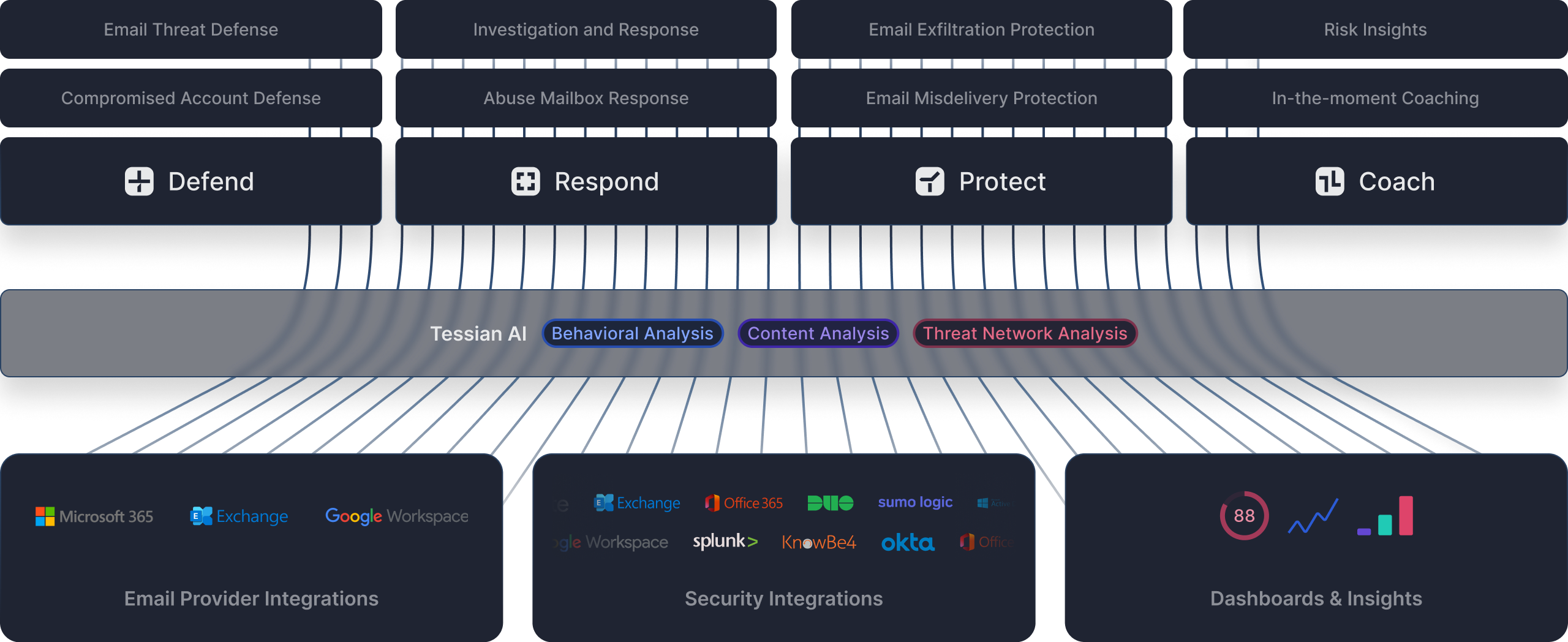
Tessian uses an ensemble of AI based approaches because it's the only way to defend against advanced phishing attacks, and protect against sensitive data loss on email. Through behavioral, content and threat network analysis, Tessian AI automatically adjusts as our customers hire, acquire, and adapt.
Behavioral Detection
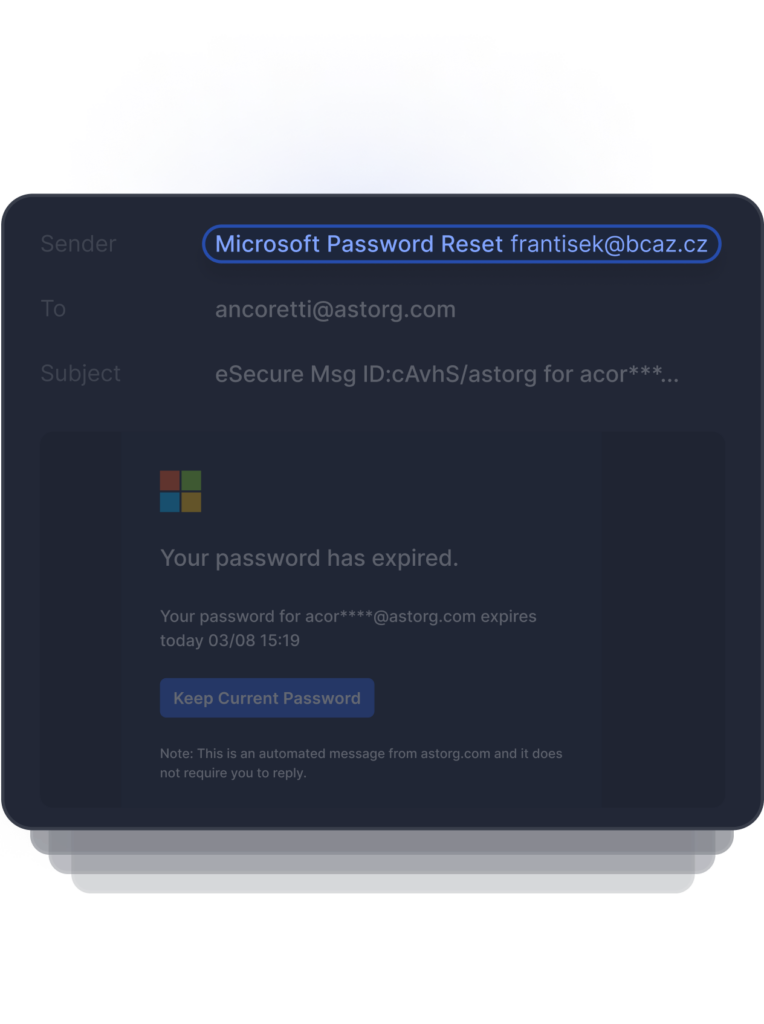
Detects Anomalous Sender
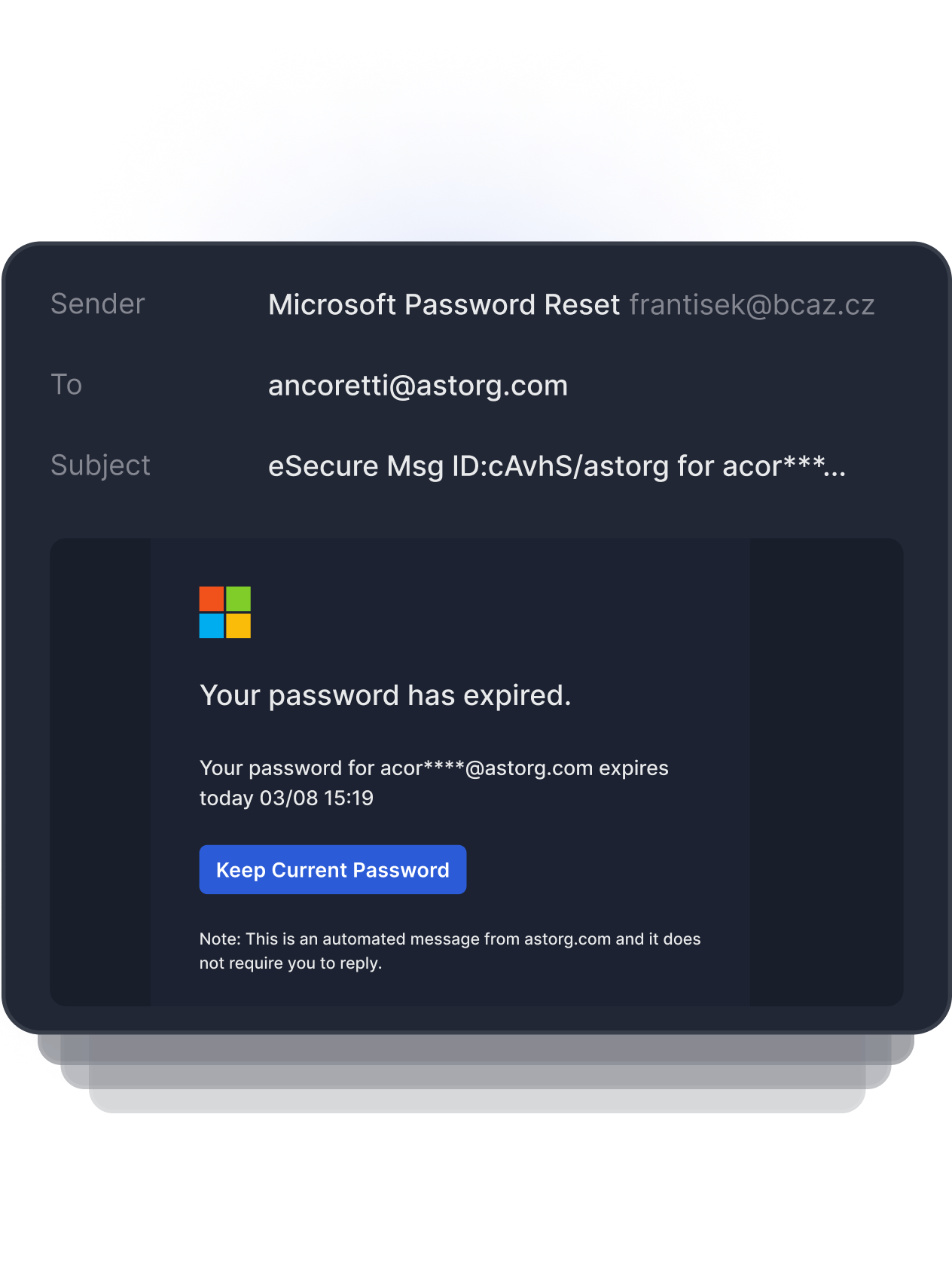
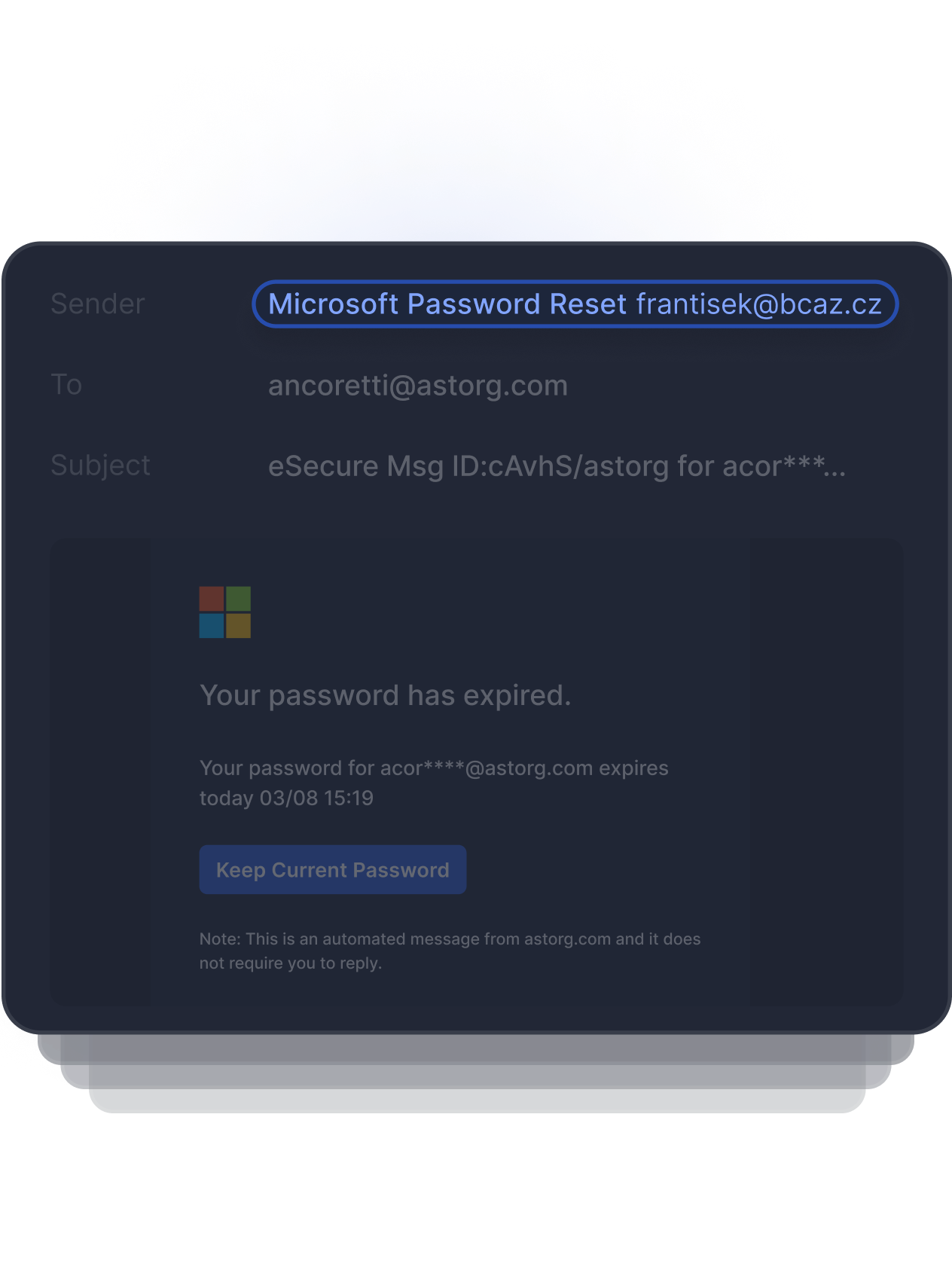
The display name of this sender appears to be a legitimate Microsoft Password Reset, but the domain does not match nor appear to be a legitimate Microsoft account.
Behavioral Detection
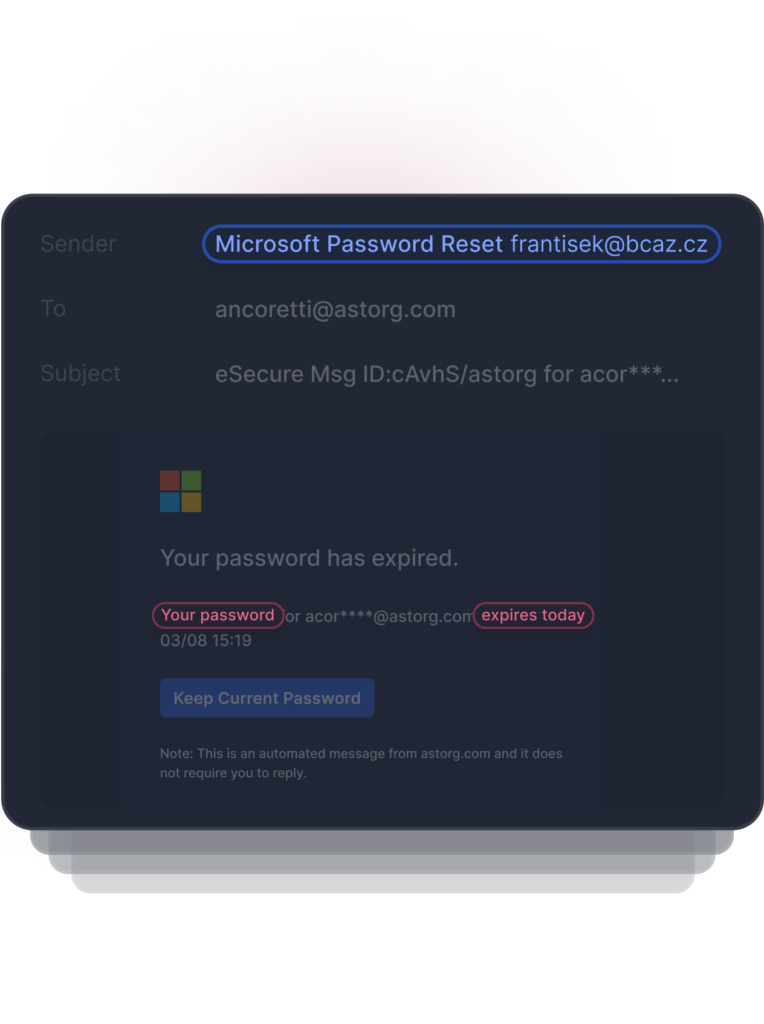
Detects Anomalous Behavior
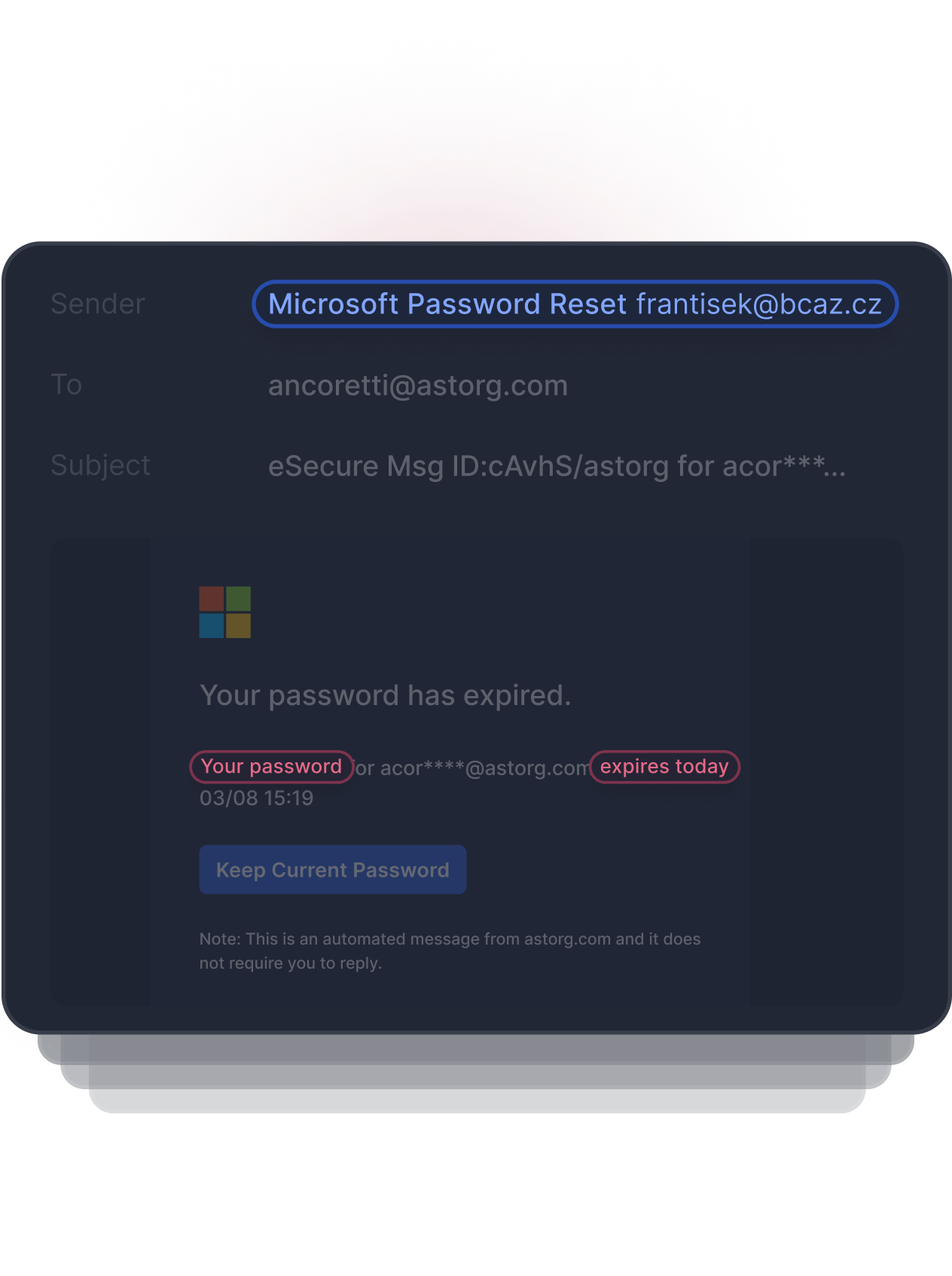
A common tactic in Business Email Compromise attacks is to use urgency to trick the user into completing the call to action before they have a chance to realize something is phishy. Natural Language Processing detects this anomalous behavior by identifying terms that indicate urgency, financials, and calls to action.
Behavioral Detection
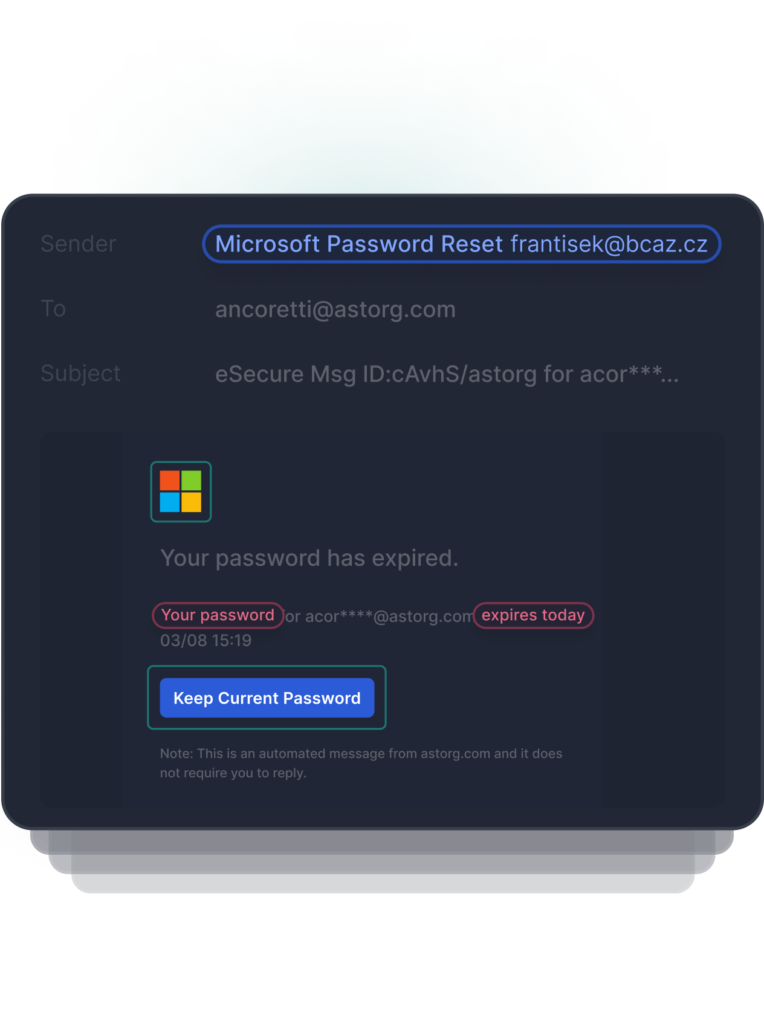
Detects Anomalous Link
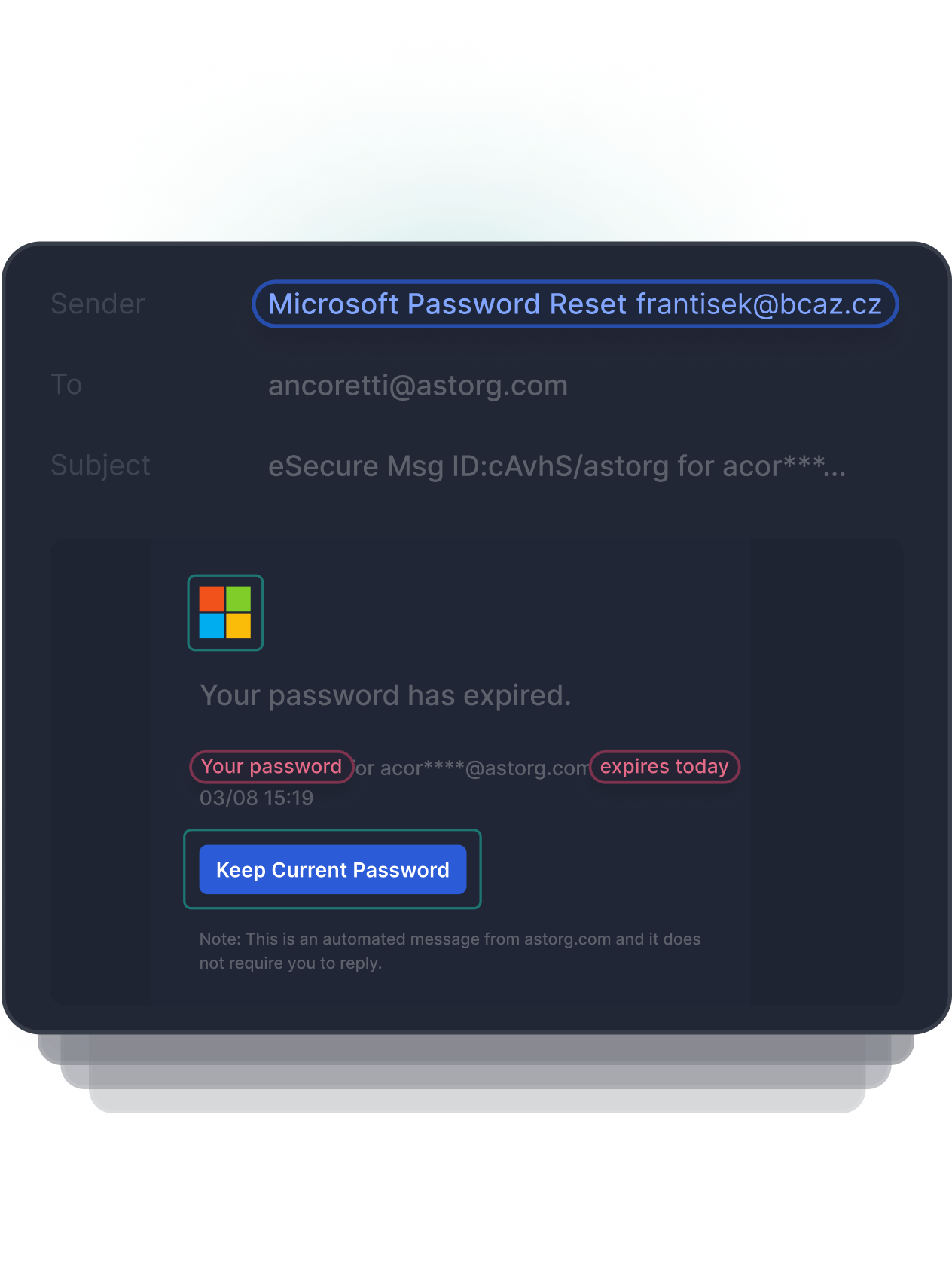
Image based attacks can be used to appear as if a trusted brand is the sender, but when the link is clicked the user is redirected to a malicious website or loaded with malicious content. OCR/Perceptual Hashing identifies image based impersonation attacks with underlying malicious URLs.
“Tessian stops email threats, including Phishing, Business Email Compromise and attacks which could lead to Ransomware or Credential theft on a daily basis. Without Tessian, these threats would've reached our end users.”
Simple stack that deploys in minutes
Tessian is built to augment Microsoft and Google, allowing you to enhance your investments and move beyond your secure email gateway. Tessian is deployed in minutes through native API integrations, add-ins or mail gateway.
Get in touch
See Tessian in Action
Book a personalized demo to see how Tessian detects and prevents advanced email threats and data loss via email
-
2021 Gartner® Market Guide For Data Loss Prevention
A must read guide for security and risk management leaders starting DLP programs to solve complex use cases. Get guidance on DLP market trends and their impact on data security strategies.Download Market Guide -

451 Research: DLP Market Insight Report
451 Research is a global IT analyst firm, part of S&P Global. Read 451 Research's analysis of Tessian's approach to email security using ML.Read the Full Report