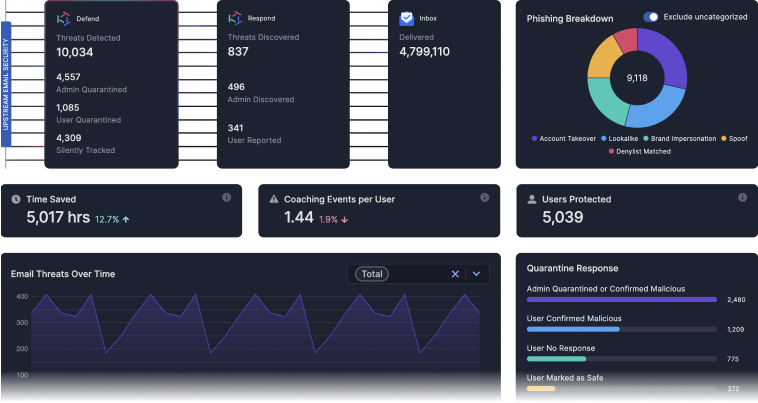
Trusted by world-leading businesses
A context aware, AI-based approach to defending against threats and protecting sensitive data on email.
featured case study
Customer Q&A: Email Security in Financial Services
Tessian sat down with Schroder’s Chief Information Security Officer Rob Hyde to discuss how implementing Tessian has led the organization to stay proactive with their cybersecurity strategy.

featured case study
Focusing on Security Basics with Game Changing Technology
Arm technology is at the heart of a computing and connectivity revolution that is transforming the way people live and businesses operate. Together with 1,000+ technology partners, Arm is at the forefront of designing, securing and managing all areas of computing, from the chip to the cloud.

Customer Stories
Tessian Is Recognized in G2's Spring 2023 Report
get in touch
See Tessian in Action
Simultaneously we had a problem with prisoner drunkenness that we couldn’t figure out.
featured resources
-
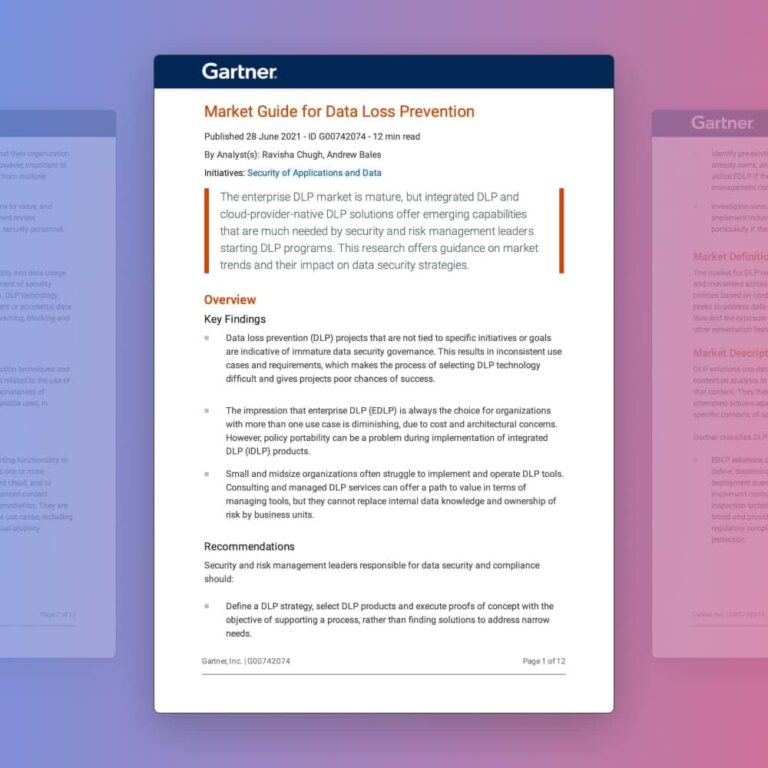
2021 Gartner® Market Guide For Data Loss Prevention
A must read guide for security and risk management leaders starting DLP programs to solve complex use cases. Get guidance on DLP market trends and their impact on data security strategies.Download Market Guide -

451 Research: DLP Market Insight Report
451 Research is a global IT analyst firm, part of S&P Global. Read 451 Research's analysis of Tessian's approach to email security using ML.Read the Full Report