The next generation of email security, referred to by Gartner as Integrated Cloud Email Security (ICES) solutions, bring a fresh approach to solving increasingly sophisticated and elusive email security threats. Here’s what to look for when choosing a ICES.
Born in the cloud, for the cloud, ICES solutions are seen as an integral additional layer of email security to complement the native email security capabilities present in cloud productivity suites, such as Microsoft 365 and Google Workspace.
At last count, according to the latest Gartner Market Guide for Email Security (2021) there were 13 ICES vendors – giving customers a lot of choice to choose from.
Not every ICES vendor however, offers the same completeness of vision, degree of protection, or intelligent capabilities.
This short guide will bring insight on some of the key fundamentals that prospective buyers of an ICES solution should be aware of.
Why is there a need for ICES solutions in the first place?
Evidence shows that email remains an important and attractive attack vector for threat actors; according to a recent study, it’s responsible for up to 90% of all breaches.
The fact that the vast majority of breaches are attributed to an email compromise, indicates that the current status quo regarding email security is incapable and insufficient at preventing breaches. This was confirmed in a Forrester survey conducted on behalf of Tessian, with over 75% of organizations reporting on average of 20% of email security incidents getting by their existing security controls.
Threat actors are using more sophisticated email-based techniques, and attacks are achieving greater success. This is largely due to the commercialization of cybercrime, with Phishing-as-a-Service and Ransomware-as-a-Service offerings becoming more prevalent on the dark web.
In this new world, threat actors develop exploit kits and offer their services for sale. This has unfortunately led to a dramatic increase in the ability of attackers to find targets. And this explains why the cost of damages from cybercrime is expected to rocket to $10.5 trillion by 2025 – representing a +350% increase from 2015.
Digital transformation is another key reason too. Cloud adoption was accelerating prior to the Covid-19 pandemic. In the wake of the pandemic, cloud adoption accelerated even more quickly. This dramatic shift to the cloud has significantly expanded attack surface risk, with employees working from home, and often on personal devices.
This structural shift in computing has also revealed the soft underbelly of legacy cybersecurity solutions built for an on-premise world, including the rule-based and static protection for email offered by Secure Email Gateways (SEGs). And this explains why 58% of cybersecurity leaders are actively looking to displace SEGs for the next generation of email security – with behavioral intelligence and machine learning at the core.
ICES fundamentals
Approach to threat detection and prevention
The key differentiator between SEGs and ICES solutions from a threat detection standpoint is that ICES are underpinned by machine learning and utilize a behavioral intelligence approach to threat detection.
The algorithm of an ICES solution develops a historical behavioral map of an organization’s email ecosystem. This historical behavioral map is leveraged along with Natural Language Processing (NLP) and Natural Language Understanding (NLU) capabilities, to dynamically, and in-real-time, scan and detect any anomalous email behavior. Unlike SEGs, this enables these solutions to detect threats as they arise, in real time.
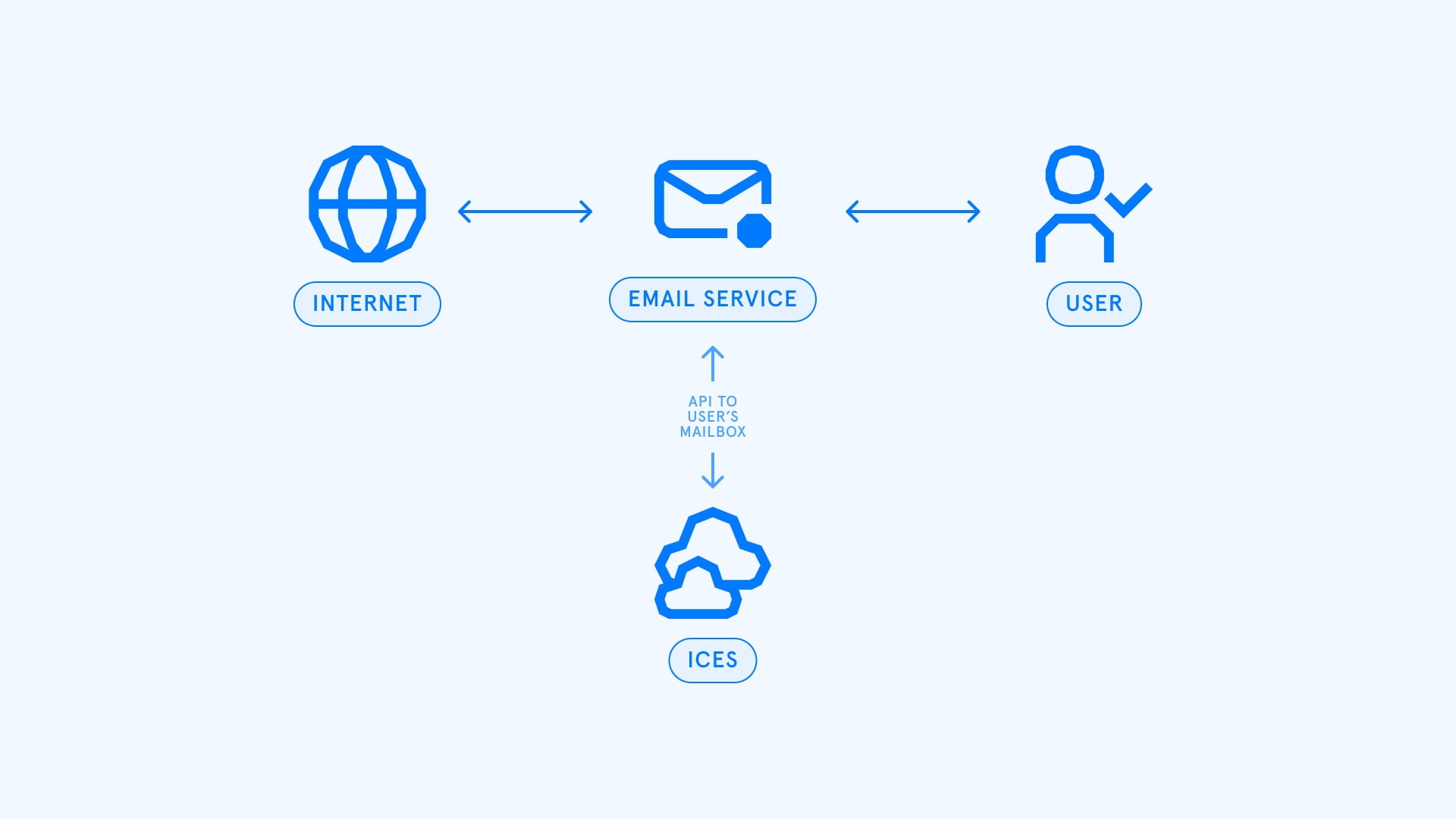
Deployment architecture
There are also important differences in the architecture and configuration of ICES solutions from SEGs. ICES solutions do not sit in-line like SEGs, they also do not require MX re-routing, but rather connect either via connect or API and scan email either pre-delivery or post-delivery – detecting and quarantining any malicious email.
Degree of security automation
ICES solutions also offer a high degree of email security automation, including triaging of security incidents, which significantly reduces alert fatigue and the SOC burden, ultimately improving security effectiveness.
Key differences between SEGs and ICES
| SEGs |
ICES |
- Requires MX records changes, sits in-line, acts as a gateway for all email flow
|
- Requires no MX record changes and scans incoming email downstream from the MX record, either pre-delivery via a connector, or post-delivery via an API
|
- Designed to detect basic phishing attacks, spam, malware and graymail. No zero day protection
|
- Designed to detect advanced social engineering attacks including spear phishing, impersonation attacks, business email compromise (BEC), and account takeover (ATO). Advanced zero day protection
|
- Static, rule and policy based protection. No intelligent component to threat detection for inbound or outbound, resulting in high false positives and significant triaging of email security incidents
|
- Behavioral and machine learning detection engine for advanced inbound and outbound threats, resulting in greater detection efficacy and lower false positives i.e. less business interruption and more SOC optimization
|
- Limited insider threat detection and no lateral attack detection capability. Once the threat has bypassed the gateway the threat actor as unlimited access to the victims’ data and information systems
|
- Advanced insider and lateral attack detection capability, stopping threats where and when they arise
|
- Basic email field scanning capability. Relies a threat engine of previously identified threats, and static rules and policies
|
- All of the email fields are analyzed using machine learning and compared against a historical mapping of email correspondence. Fields scanned include the sender, recipient, subject line, body, URL and attachments
|
- Advanced malicious emails go undetected and reach target inboxes. Some of the less sophisticated malicious emails end up in the spam or junk folder – enabling users to accidentally interact with it
|
- Advanced malicious emails are detected and automatically hidden from users’ inboxes. With the pre-delivery option, only email that is determined to be safe is delivered. Post-delivery solutions will in nanoseconds claw-back a suspected email determined to be malicious.
|
- No in-the-moment employee security warnings. Security alerts are retroactive and aimed at SecOps, offering no context to employees or the ability to improve the security culture
|
- An in-the-moment security notification banner can be added to an incoming or outgoing email indicating the level of risk of the scanned email and the context. These real-time security notifications lead to improved security culture, by empowering employees to take safe action, in real time
|
|
|
- Some ICES like Tessian have advanced DLP capability
|
Five market differentiators for ICES solutions
Not all ICES solutions however, offer the same degree of completeness in product and protection. It is important that prospective customers of ICES solutions understand and interrogate the following key differentiators during the vendor selection process:
1: Completeness of the product offering and product roadmap
Does the solution cover inbound and outbound email protection (i.e. does it prevent email data loss events from occurring?)
Does it have pre-built integrations with other cybersecurity tools such as SIEMs?
2: Degree of protection offered
During the POV it is important to test the efficacy of the algorithm and determine a true baseline of detection, including the % of false positives.
Verify the actual results from the POV against the vendors stated claims.
3: Deployment and management overhead
Some vendors have unrealistic claims of “protection within seconds” – understanding the actual amount of FTE resources and time needed for deployment is crucial, as well as the product’s ability to scale.
Determining the degree of management FTE required for managing the tool on a day-to-day basis is equally important.
4: UX and reporting capability
The overall UX including UI for SecOps teams, and feedback from employees after using the product during the POV is essential. Evidence shows that if the UX is poor, the security effectiveness of the tool will be diminished.
Having the ability to on-demand pull or automate risk metric reporting down to the employee level, for inbound and outbound email, is crucial for cybersecurity and risk compliance leaders.
5: Degree of automation
Automation is fast becoming a buzzword in cybersecurity. Here buyers need to be aware of the degree of automation that the ICES solution actually delivers, ranging from threat detection to the triaging of threats, as well as risk reporting.
The final word
All it takes is one click on malicious content for a breach to take place. When assessing and selecting an ICES solution, it is important that customers consider the above listed criteria as part of their general vendor assessment criteria.
The considerations on the completeness of the product offering and the degree of protection offered should be weighed carefully.
Finally, it’s the human-side that often never gets mentioned in vendor assessments. The experience interacting with the vendor from the first interaction through to the end of the POV should provide key insight into what the future partnership with the vendor will look and feel like.
About Tessian
Tessian is one of the few ICES vendors that offers comprehensive protection for inbound threats like advanced spear phishing attacks, as well as outbound protection, preventing malicious and accidental data loss.
Unlike many of our ICES competitors, we don’t treat our customers as test subjects – our algorithm was developed and fine tuned for 4 years before we went live. Due to this level of product maturity, we boast among the lowest percentage of false positives in our industry.
We have among the most attractive UI, delivering a phenomenal UX. This includes advanced and automated cyber risk reporting, making security and risk leaders lives’ easier.
We never make claims that we can’t back up. We deploy in seconds and protect within hours. Both the deployment and management overhead are extremely efficient due to product maturity and the degree of automation inherent in our product.
Finally it’s worthwhile mentioning we take our customers seriously. Here’s what some of them have to about using our product:
“Apart from being an excellent product, Tessian has to be the easiest installation and deployment I’ve ever had for an enterprise security software product to date.”
Gary Murton
Head of IT at Com Laude