Over the last decade, phishing has evolved from spam to something much (much) more targeted. It’s now the threat most likely to cause a breach. At the same time, the number of adults on social media networks like Facebook has jumped by almost 1,300%.
We explore the correlation between the two in our latest research report “How to Hack a Human”. You can download it here.
Need a few good reasons to download it? Keep reading.
1. You’ll get a hacker’s perspective
Actually, you’ll get ten (ethical) hackers’ perspectives.
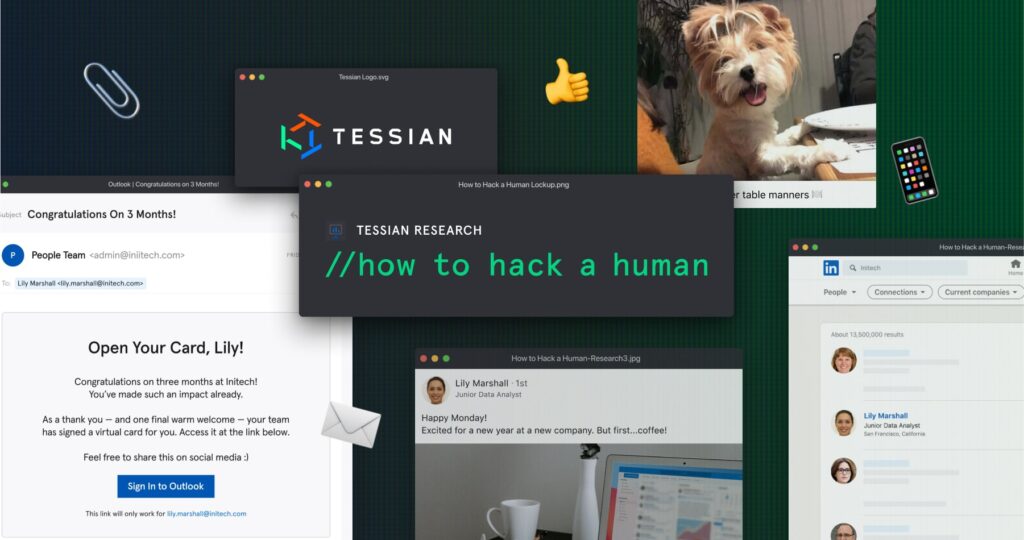
We partnered with HackerOne and other social engineering experts to learn how they use publicly available information – like social media posts, OOO messages, press releases, and more – to craft highly targeted, highly effective social engineering attacks.
In the end, we found out that they use everything. A photo from your gender reveal party can help them uncover your home address. A post about your dog can help them guess your password. An OOO message can tell them who to target, who to impersonate, and give them a sense of their window of opportunity.
2. You’ll learn how vulnerable organizations are to attack
By surveying 4,000 employees and using Tessian platform data, we were able to uncover how frequently people (and the companies they work for) are being targeted by social engineering attacks, business email compromise (BEC), wire transfer fraud, and more.
The numbers are staggering. 88% of people have received a suspicious message in the last year.
Of course, some industries are more vulnerable than others.
[infogram id=”how-to-hack-a-human-suspicious-1hnp27mmrlgwy2g?live”]
And, we expect to see more next year. Why? Between H1 2020 and H2 2020, we saw a 15% increase in attacks.
Read the report to find out more.
3. We show two examples of social engineering – including the “clues” that enabled hackers to carry out the attack
Using social media posts, news headlines, and OOO messages, we breakdown two attacks.
- CEO Fraud in Financial Services
- Account Takeover (ATO) in Healthcare
We explain the hacker’s motivation, what the attack looked like, and – in the end – how it could have been prevented. (More on that below).
4. You’ll get access to a free, educational guide to help employees level-up their personal and professional cybersecurity
As we’ve said, hackers hack humans to hack the companies they work for. So, to help security leaders communicate the threat and teach their employees how to prevent being targeted and how to spot an attack if it lands their inbox, we put together a comprehensive list of do’s and don’ts.
You can find it on page 20.
Bonus: Are you a Tessian customer? We’re happy to co-brand the list. Get in touch with your Customer Success Executive for more information.
5. The dataset is global
In addition to interviewing employees in the US and the UK, Tessian platform data accounts for organizations across continents.
Why does this matter? It goes to show that this isn’t a problem that’s isolated to a specific region. Everyone is being targeted by social engineering attacks.
But – interestingly – the online habits of Americans vs. Brits vary considerably. For example, while 93% of US employees say they update their job status on social media when they start a new role, just 63% of UK employees said the same.
[infogram id=”how-to-hack-a-human-hackers-hack-humans-to-hack-companies-1hxj48ppd31yq2v?live”]
Top tip: New starters are prime targets of social engineering attacks. They’re typically given their full access credentials when they start, but don’t yet know who’s who. They may also not have had their security training yet. Finally, given that they’re new, they’ll be especially keen to make a good impression.
6. You’ll get a peek inside a hacker’s toolkit
Yes, all of the information hacker’s use is easy enough to find online (esspecially if they’re motivated to find it). But. there are plenty of tools that hackers use that make connecting the dots and cracking passwords quick and easy.
We outline ten in the report. You’ll likely recognize some of them…
Most – if not all – of these tools were designed for the “good guys”. Penetration testers, compliance teams, and even law enforcement. In fact, some are even marketing and sales tools! Flip to page 16 to learn more.
Bonus: The report is ungated…for now
For the next few weeks, you’ll be able to download the report without filling out a form. Yep, you just click “download” and it’s yours.
Starting at the end of February, you’ll just need to provide your email address and a few other pieces of information about your role and company.
Ready? Set? Download.