Over the last decade, phishing – a type of social engineering attack – has transformed from something more like spam to the threat most likely to cause a breach. During that same period, the number of adults on social media platforms like Facebook increased by almost 1,300%.
Every photo we post, status we update, person we tag, and place we check into reveals valuable information about our personal and professional lives. And hackers use this information to craft targeted – and effective – attacks at scale.
-
What is social engineering?
Social engineering is the act of tricking someone into handing over information (bank details, PII, etc.) or carrying out a desired action by taking advantage of the victim’s natural emotional responses and reactions. While these attacks occur most frequently over email (phishing), they can be delivered by text message (smishing) and phone call (vishing).
How big are our digital footprints?
Our digital footprints are bigger than ever. There are over:
- 2,701,000,000 users on Facebook
- 1,158,000,000 users on Instagram
- 722,000,000 users on LinkedIn
- 353,000,000 users on Twitter
And it shouldn’t surprise you that, according to research, 90% of people post information related to their personal and professional lives online. This number is even higher among 18-34 year olds. And, across LinkedIn, Instagram, and Facebook, 55% of people have publicly visible accounts.
[infogram id=”how-to-hack-a-human-the-social-network-1hmr6g77rer5z6n?live”]
When an account is public, anyone can see the information you post online, whether it’s a photo of your boarding pass, or a birthday shout-out to a colleague. Harmless, right? Unfortunately not.
This information is gold dust to hackers and makes reconnaissance impossibly easy.
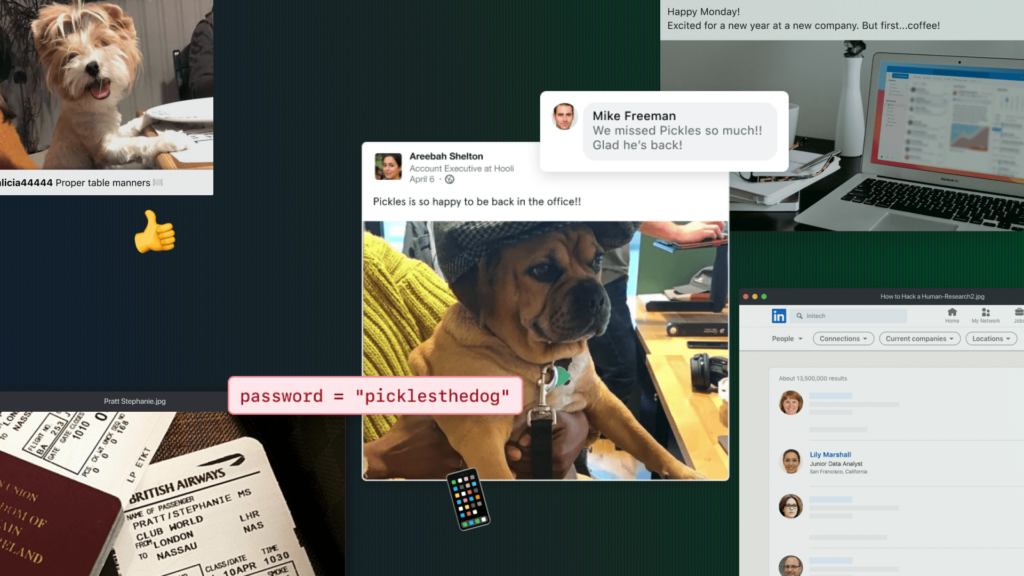
Take the former Australian Prime Minister, Tony Abbott. He posted a picture of his boarding pass on Instagram. From the booking reference, hackers found his passport number and phone number – information that could have helped them gain access to other accounts, including sensitive personal and government information.
It didn’t take much work. According to an ethical hacker we spoke to, “Anyone who saw that Instagram post could also have [his passport number and phone number].”
Mr. Abbott isn’t the only person who posts this kind of information online…
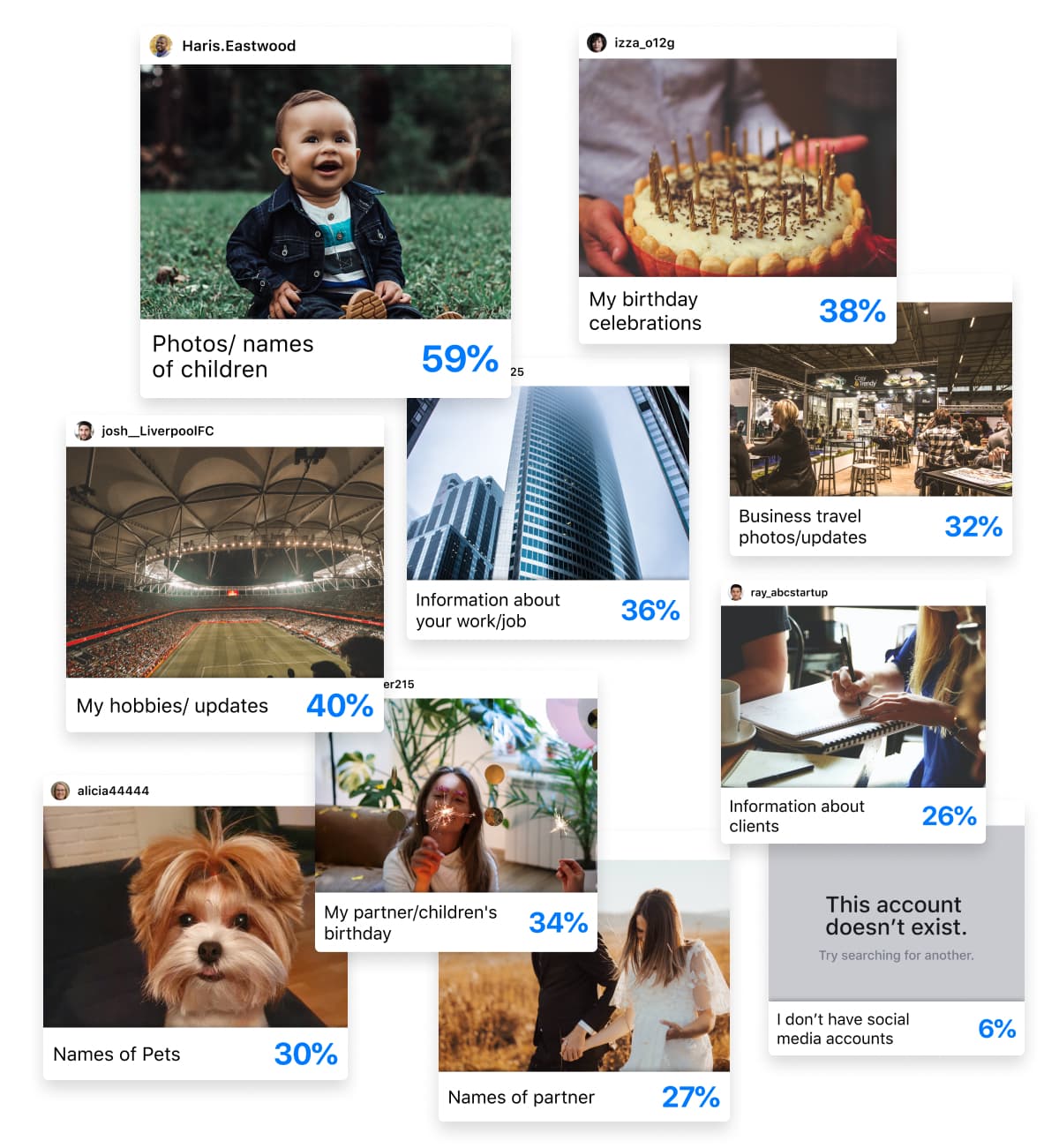
32% of employees post business travel photos and updates. Nearly 72% mention birthday celebrations. 36% share information about their jobs. And don’t forget about all the information we share about our pets, partners, and children.
Hackers use all of it. Yep, even that photo of your pup.
How do bad actors use this information?
To understand exactly how hackers leverage all of this information, we have to look at a social engineering attack from start to finish.
First, a hacker identifies a target organization.
Depending on their motivations, they could choose an asset management firm with hopes of initiating a wire transfer or a pharmaceutical company with hopes of getting their hands on R&D. From there, they’ll research supply chains and vendors, study company org. charts, map employee relationships, and monitor individual behavior. And, by running scripts, they can do this automatically and at scale.
Why do all this reconnaissance? To pinpoint potential entry points, identify viable third-parties to impersonate, and to collect information (however subtle) that’ll help them nudge their targets towards unconscious (and conscious) confirmation and – eventually – trust and compliance.
“Hackers start by looking for vulnerabilities. Not necessarily exploits but vulnerabilities. Today, those vulnerabilities are people.”
Alon Gal
Co-Founder & CTO, Hudson Rock
While behavior varies by region, most of us eagerly announce when we start a new job. In the US, almost everyone does – with 93% of employees in the US saying they update their job status on social media.
We share press releases about new clients and mergers and acquisitions. We post photos of our employee IDs and screenshots of Zoom calls. We tag our colleagues and customers in our updates and comment on theirs. We share all of this information regularly.
Almost half (43%) of us post every day, giving hackers up-to-date intelligence about where we’re working, who we’re working with, and what we’re working on.
Passwords play a role, too
When it comes to Business Email Compromise, information related to your professional life is important. But your personal information can be just as valuable.
Hackers can use information about your pets, partner, children, and even your interests to crack passwords and answer security questions, giving them full access to personal and work accounts, including password managers and even your email.
Don’t believe us? 21% of people use information like their favorite football team, their pet’s name, or birthdays when creating passwords and some of the most common security questions include:
- What is your mother’s maiden name? What was your first car?
- What elementary school did you attend?
- What year were you married?
This is all readily available online. 34% of people share the names of their pets, 34% mention their children/partner, and 40% share information about their interests.
People may even unwittingly share this information via gimmicks or memes that make their rounds on social media. For example, “name generators” that ask you to combine your pet’s name with your childhood street address. Sound familiar?
“Think about when you have to verify your identity or your account. What information do they ask you for? First name, last name, birth date. All you need is a ‘Happy Birthday!’ post on social media to garner all that information. It really is that easy.”
Alyssa Miller
Hacker, Researcher and Security Advocate
An example of a social engineering attack leveraging social media
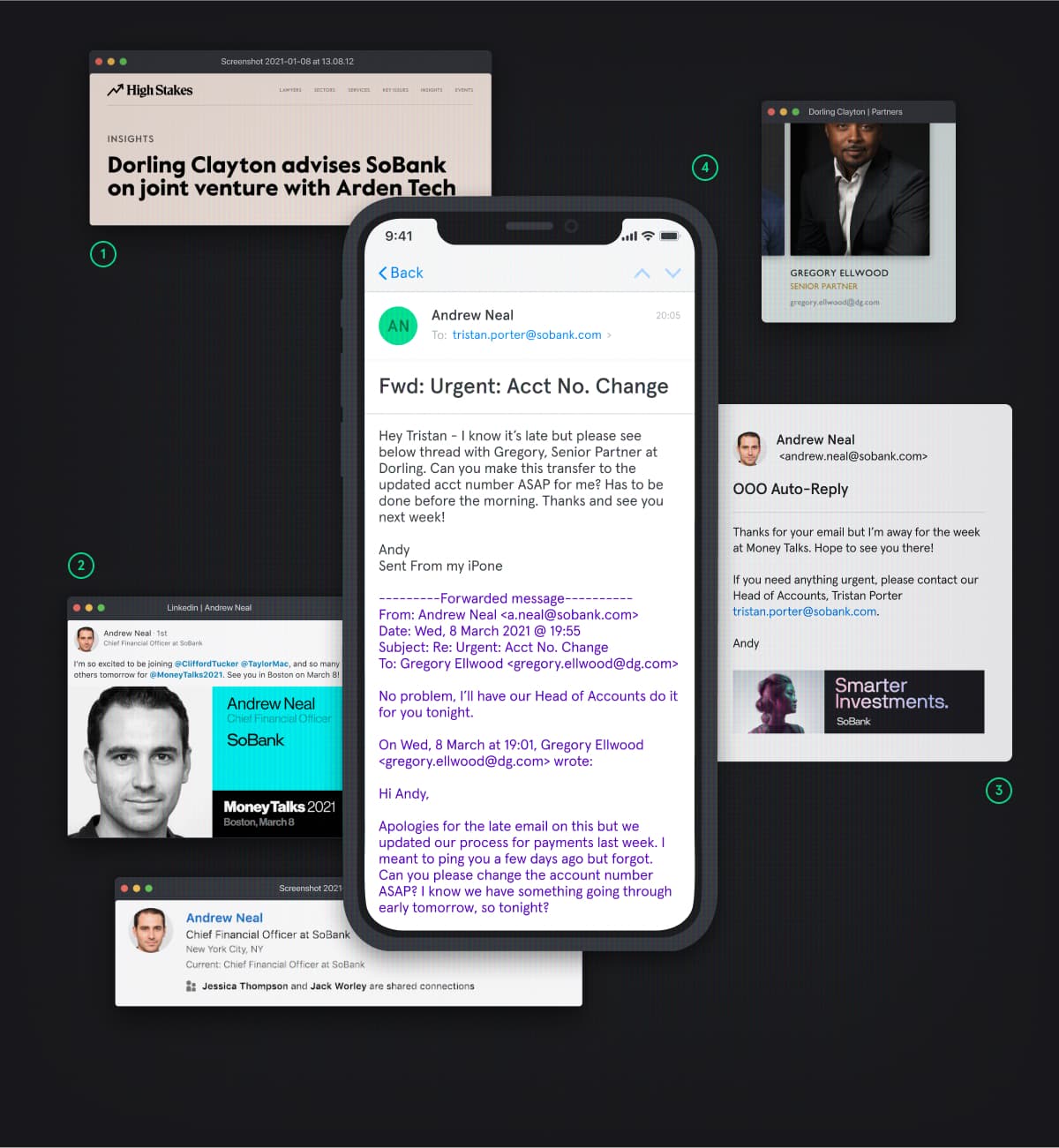
In this example of a social engineering attack, hackers use an OOO message and other publicly available information to initiate a wire transfer.
Type of Attack: CEO/CXO Fraud
Industry: Financial Services
Hacker Motivation: (Quick) Financial Gain
- The hacker group monitors news wires for up-to-date information about banks in the United States to find their target, an asset management firm called SoBank.
- They see that the company’s CFO – Andrew Neal – is OOO at a conference.
- Thanks to his OOO message, they’re able to identify their target, Tristan Porter. They also learn that Andrew goes by “Andy” at work.
- The hacker group sends a fabricated email chain that appears to be between Andy and Gregory Ellwood, Senior Partner at Dorling Clayton – SoBank’s advising firm – urging Tristan to make a wire transfer.
Cybersecurity best practice
Want to better manage your digital footprint and avoid being targeted by (and falling for) a social engineering attack?
Here’s a list of do’s and don’ts.