A single spear phishing email can deeply damage your organization’s cybersecurity. After a data breach, credentials could be compromised and systems left unguarded, all as the result of someone’s failure to detect an impersonation of a colleague, supplier or partner.
What makes the threat of impersonation especially worrisome is the fact that you don’t have to be a highly skilled cybercriminal to impersonate someone on email. In fact, many kinds of impersonation are startlingly simple. In this post we’ll cover display name impersonation, perhaps the easiest way for an attacker to dupe employees and extract money, data and/or credentials from enterprises.
What is display name impersonation?
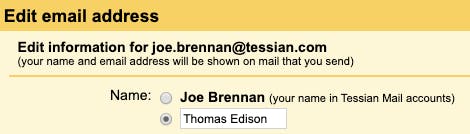
Display name impersonations involve attackers setting deceptive display names on their email accounts in order to mislead recipients. The display name is not part of the email address itself: it’s the name affiliated with the account that usually appears before the email address in inboxes.
Display name impersonations are often combined with domain impersonations to execute sophisticated impersonation attacks, which use social engineering to threaten organizations’ most sensitive data and systems.
How do attackers manipulate display names?
Even for people with little or no technical knowledge, impersonating a display name is very easy: the operation can be carried out within almost all major email clients. Here, we’ll take you through how to do this with Gmail:
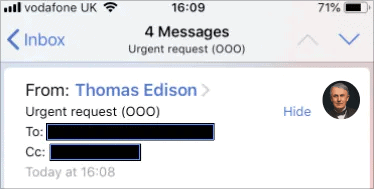
This approach is especially effective on mobile devices (pictured above), because the From: email address is hidden on mobile screens. Very little work has gone into creating a potentially convincing impersonation that could fool busy, distracted employees – especially if the sender being impersonated is a high-ranking executive or a demanding supplier. With CEO fraud losses totalling more than £14m in the UK in 2018, organizations should be aware of the growing threat of executive impersonations.
Attackers can also change a sender’s display name to include both a genuine-seeming name and email address, such as “Thomas Edison <thomas.edison@nationalphonograph.co>”. In this case, the attacker is betting the target won’t notice that the email address they see first isn’t actually the address from which the email was sent.
Why are impersonations so easy to carry out?
Email is an extraordinary tool that offers effectively free communication to billions of people around the world. But email was never designed to cope with the sheer volume of traffic we now see on a daily basis (almost 125 billion business-related emails were sent per day in 2018).
Simplicity is a core ingredient of email’s success. But being so simple means it’s dangerously easy for malicious actors to take advantage of inbuilt vulnerabilities.
Email as a channel has many vulnerabilities, but despite being a multibillion-dollar industry in its own right, email security products – and the protocols that underpin email infrastructure more generally – have historically done a poor job of preventing impersonations. Organizations that have spent energy configuring DMARC, DKIM and SPF cannot rest on their laurels: authentication tools like DMARC are limited in their scope and are unable to prevent display name impersonation attacks.
The legacy tech problem
For decades now, Secure Email Gateway (SEG) products have defended organizations’ networks from attacks. The main methods of defense employed by SEGs are:
- Payload inspection like scanning URLs and attachments. (Attackers know that zero-payload attacks, which rely on social engineering techniques to persuade targets to take dangerous actions, are much more likely to evade SEGs’ defenses.)
- Spam and “bulk” phishing prevention. (By focusing on past known attacks and basic email characteristics like domain authentication, these techniques fail to prevent advanced impersonation, which is low-volume and crafted to evade such systems.)
- Rules to prevent impersonation. (Basic rules can prevent simple email impersonation attacks by detecting newly registered domains, different sender/reply-to addresses, etc.)
SEGs were designed to protect networks and devices from inbound cyberattacks. More or less, they still do a good job of defending against the bulk spam and phishing scams that were so prevalent years ago. The problem? They are not flexible and intelligent enough to identify anything but the most basic impersonations.
Being able to inspect suspicious URLs and attachments doesn’t help when an advanced impersonation spear phishing attack consists only of persuasive, urgent language to coerce an employee into taking a dangerous action like transferring money. Blacklisting known examples of names and addresses used in phishing attacks only prevents attacks that have been reported already; any new spear phishing or impersonation attack will bypass these perimeters.
Meanwhile, rule-based email security services are limited by the ability of system administrators to continually update rules based on new edge cases and evolving threats. Static rules do not equip enterprises with the ability to identify and predict new anomalous email attacks in real time.
SEGs find it hard to deal with advanced email threats, and even “simple” display name impersonations pose them serious challenges. Using rudimentary logic to determine whether a display name is “close” to the display name of an employee doesn’t work for external impersonations, for example. In addition, rules that trigger when (for example) a display name has one or two characters that are different from a genuine employee’s name are inherently limiting.
Attackers are able to easily reverse engineer SEGs and find ways around their defenses. So should enterprises be looking elsewhere to defend their email environments?
Display name impersonations: a summary
For attackers, changing a display name is startlingly easy. The combination of display name impersonation with domain impersonation can lead to very sophisticated spoofing attacks that can have seismic repercussions for enterprises and the sensitive information they control.
Cyberattacks continue to evolve and become more dangerous. But security products like Tessian Defender offer a way to combat display name (and other) impersonations. Using machine learning, Defender learns and adapts to threats by analyzing behavioral and communication patterns on email, preventing advanced impersonation spear phishing attacks before they wreak havoc within organizations.
Every email employees receive is analyzed for anomalies: this might be the use of language, prior communications with the email’s recipients, discussion of sensitive topic areas, and many more factors besides. (This applies whether the email is from a colleague or from an external partner.) With this information to hand, Tessian’s algorithm predicts which emails represent a danger to the employee and the organization. Real-time notifications let employees take the right course of action before the threat can harm their employer’s defenses.
Organizations need to respond by investing in products that are designed to deal with a newly advanced generation of cyber threats. Speak to an expert today to learn more.