QR codes made a comeback this year in more ways than one. We’ve seen them used for restaurant menus, package delivery, wedding invitations, identity authentication and more. It’s the quickest way to drive mobile web traffic when you can’t have a direct link. But there is an evil side of every tech innovation. The latest attack hitting inboxes is QR code phishing (sometimes — unfortunately — referred to as quishing). This emergent threat is evading traditional defenses and forging a new way for users to click on attacks.
If this has been keeping you up at night, you’re not alone. This week, Tessian caught over 3,000 QR code phishing attempts in just 24 hours. This attack technique, along with exec impersonations, spear phishing, and social engineering, has become one of the top concerns for email threat defense. Tessian has responded, launching new capabilities for QR Phishing detection and prevention.
What is a QR Code Scam?
A QR code scam is when a fraudulent QR code is used to trick the recipient into downloading malware or sharing credentials. Common QR code scams include payment scams, package scams, donation scams, and email scams. Email scams or QR code phishing attacks encode a malicious URL within the QR code itself to be sent by email. Because all QR codes look the same to recipients, they scan the code and then unknowingly visit a malicious website intended to deliver malware or harvest credentials. The site mimics a legitimate login or data entry form. Within the past two weeks we’ve seen a concerning uptick in the number of inquiries regarding QR code phishing attempts. Why? A running theory is that a popular phishing kit sold online included several QR code templates. Bad actors are likely finding they’re effective and traditional email security providers have difficulty detecting them.
Why are QR Code Phishing Attacks getting through?
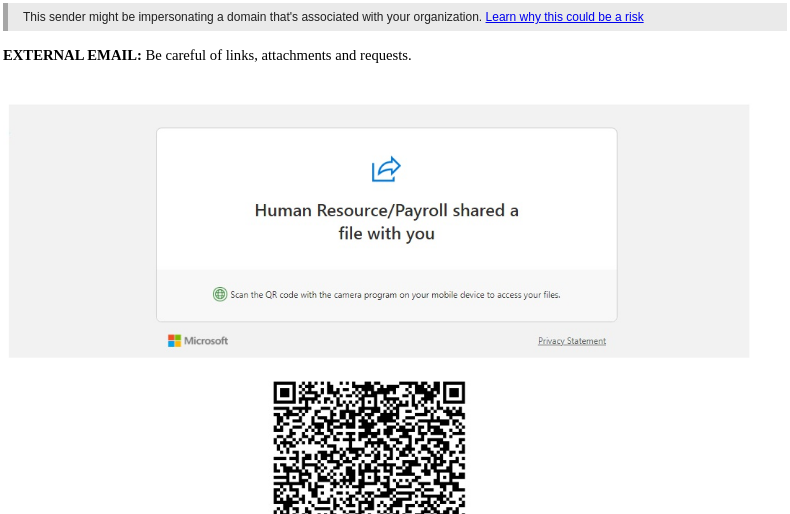
In these attacks, malicious actors craft convincing phishing emails that contain QR codes. The email triggers a natural response to take action and scan (or click on) the code, which often asks to verify their account via their credentials. The QR code images are used to evade email security tools that typically scan a message for known malicious links, but not malicious links hidden behind a QR code.
This attack method also creates an additional security blind spot. QR codes are usually scanned using a separate device than where the email was delivered. Smartphones, whether personal or not, are less likely to have robust security technology in place for prevention or detection.
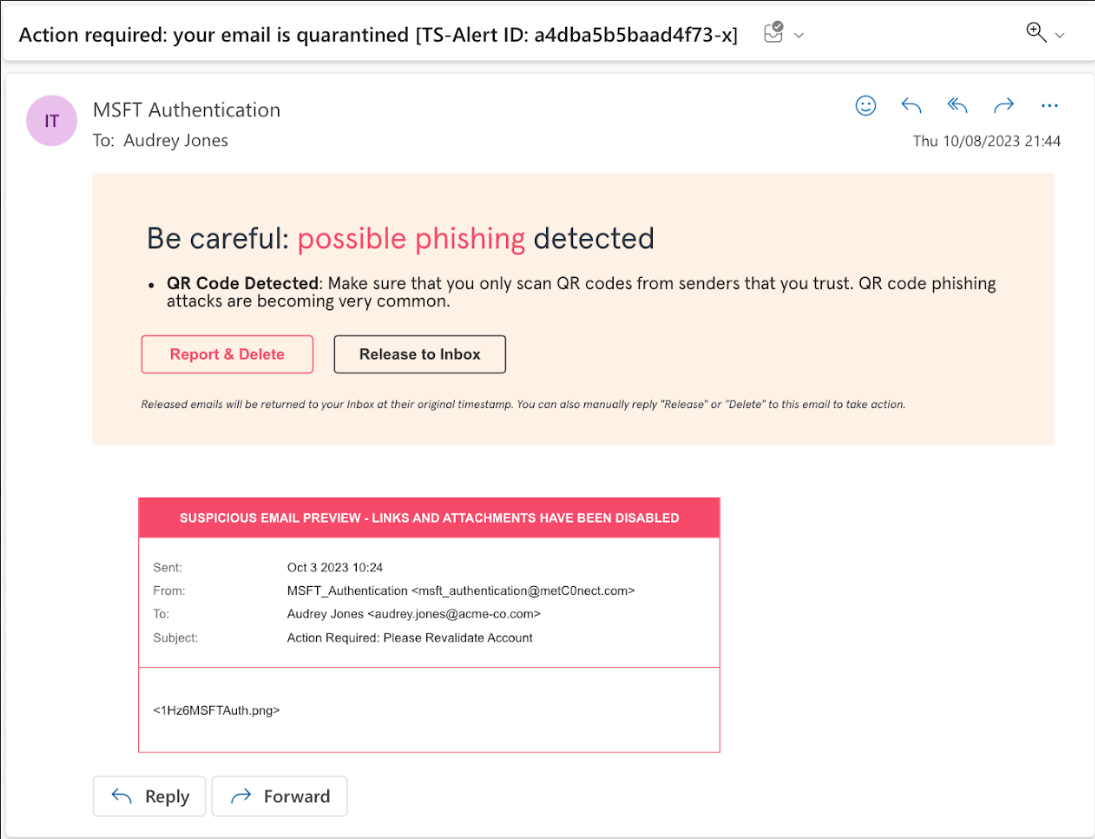
QR code phishing attacks can have severe repercussions, including data breaches, financial losses, and damage to organizations’ reputations. Many of the attacks that Tessian has detected recently, attempt to compromise a user’s credentials, often targeting Microsoft logins or other internal tools. In the anonymized example below, Tessian quarantined a “MSFT Authentication” phishing attempt.
How to stop QR code phishing?
There are multiple ways that QR code phishing attempts can be detected, and email security providers, like Tessian, are innovating quickly to stop these attacks in their tracks.
Here are a few of the methods being deployed:
- QR Code Detection. Perhaps the most important and reliable method of them all — this method leverages advanced scanning technologies and threat intelligence to identify and block malicious QR codes within emails. By extracting the URLs from QR codes for analysis, an email security tool can proactively prevent these threats from reaching employees’ inboxes.
- Behavioral analysis. Tessian uses behavioral analysis to understand the sender’s relationship with the recipient. For example, Tessian can spot and flag sender spoofing or lookalikes. If even one character is off in a lookalike domain, Tessian knows that this domain has not been seen on the organization’s network, and therefore you should be cautious.
- Perceptual Hashing (P-Hashing). P-hashing technology detects the re-use of images similar to those seen before in phishing attacks. For example, when one customer is targeted by a phishing attack that places a QR code along with text and brand logos in a single image, Tessian will store the p-hash of that image and detect emails that use a similar image in the future. However, this feature is limited, p-hashing is only effective on color images and therefore not helpful in detecting QR codes alone.
- Image OCR-Based Detection. Optical Character Recognition (OCR) scans email attachments for patterns and keywords that indicate the presence of a QR code. For example, “scan the code,” which allows Tessian to detect and flag suspicious content for further investigation.
- URL Analysis. The underlying URLs are matched to third party threat feeds and analyzed by machine learning models and heuristics to assess risk.
QR code phishing is not going away. As attackers get smart, we get smarter.
“At Tessian, we're committed to staying ahead of emerging threats. With the recent surge in QR code phishing attacks, our team mobilized to rapidly build, deploy and launch detection and protection against QR code based phishing, so our customers could close a critical gap in their security controls.”
Allen Lieberman
Chief Product Officer, Tessian.
Tessian is stepping it up as one of the only email security platforms that can effectively stop these attacks by combining QR code detection with behavioral AI. When an email contains a QR code and is from an untrusted sender, we’ll automatically flag it for review. At the same time, we’ll extract URLs from QR codes for further analysis, adding additional context. Users see a version of the email with a warning banner that advises not to scan QR codes from untrusted senders. In some organizations where administrators see little or no business use for receiving QR codes over email, Tessian customers can block QR codes from reaching their users all together.
To see how Tessian is stopping QR code phishing attacks, book a demo.
Richard Phillips
Senior Product Manager