2019 was a big year for email security.
While the world did see a record number of data breaches (up 33% from 2018) we also saw tighter security-related policies and regulations drafted and implemented, and, in general, an increased awareness amongst businesses about the importance of proactive security strategies.
While we may be biased, it seems note-worthy that human error became more and more of a talking point in the cybersecurity space. In fact, human error and the importance of machine learning and artificial intelligence in protecting people has been one of the most talked about trends by analysts going into the new year.
Similarly, companies are waking up to the fact that humans are their biggest risk.
It’s about time.
After all, misdirected emails – emails accidentally sent to the wrong person – have been one of the top data security incidents reported under GDPR according to the Information Commissioner’s Office.
We believe it’s unreasonable to expect employees to do the right thing 100% of the time when it comes to making security-related decisions; people break the rules, people make mistakes, and people can be hacked. To err is human!
What’s more, we have seen how quickly the threat landscape continues to evolve, which is why throughout 2019, we rolled out a series of important product updates that have kept our user base – which saw triple digit growth over the last 12 months – safe.
Here are the most important product updates to Tessian’s Human Layer Security platform for 2019.
1. Human error, quantified. The new Tessian Dashboard gives customers an at-a-glance view of breaches and near-misses on email
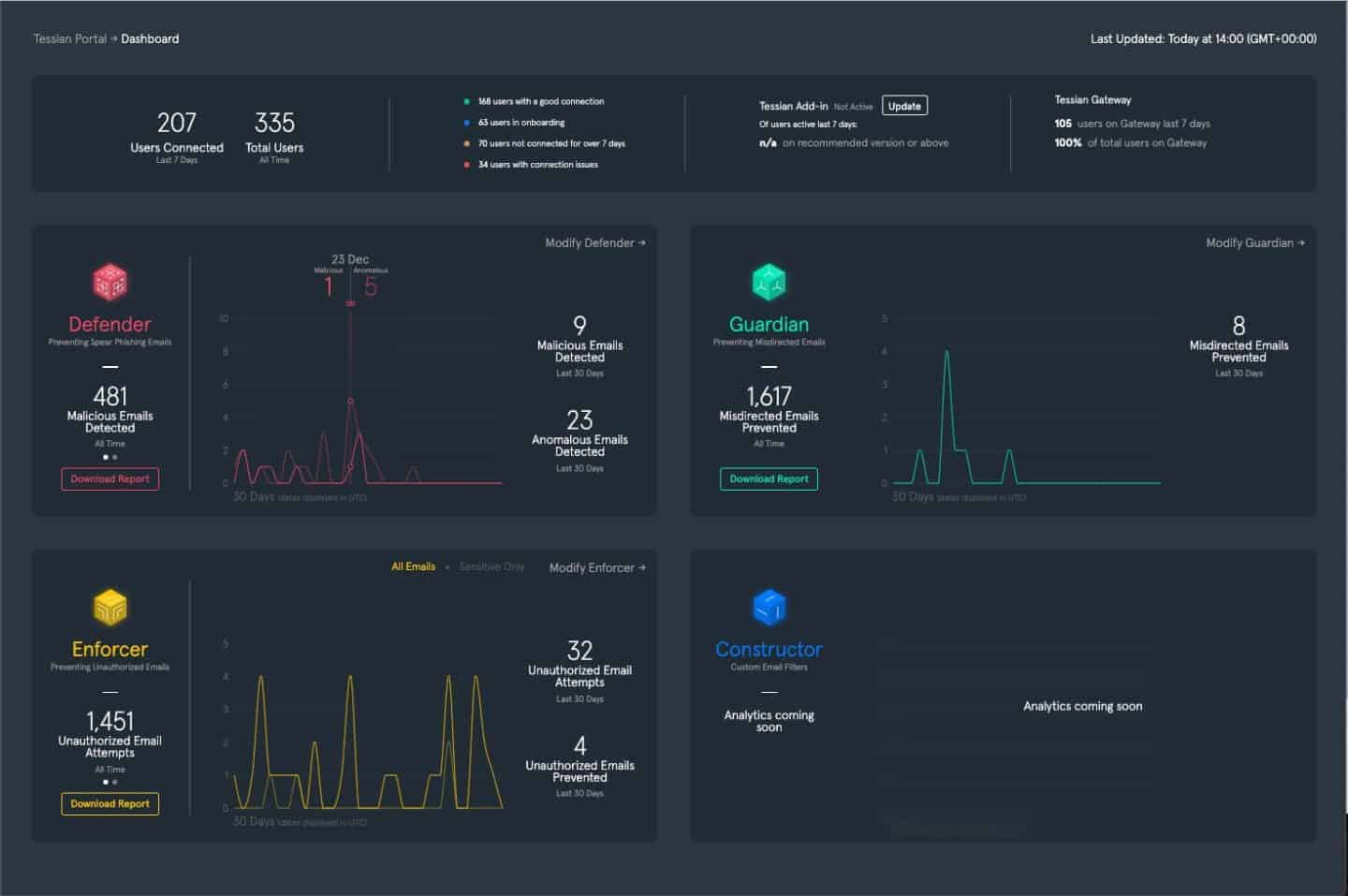
Keen to discover trends related to the number of breaches that were prevented by Tessian over the last 30 days? Our easy-to-navigate dashboard gives administrators a complete overview of activity, including any malicious and anomalous emails detected, misdirected emails prevented, and unauthorized email attempts thwarted.
Module performance for Tessian Defender, Guardian, Enforcer, and Constructor are all visible on one page, and visual representations of data make it easy to monitor and drill down on activity day-by-day. If suspicious activity is spotted, you can quickly and easily generate a report without navigating off the page.
The Tessian Dashboard also allows administrators to view user health at a glance, including the percentage of users active on the Add-in and Gateway and any connection issues across the network. This will help in-house security teams ensure every employee within their organization is protected by Tessian’s modules at all times.
2. Evolving algorithms. Tessian Defender can now detect and prevent more spear phishing attempts than ever
Throughout 2019, Tessian Defender was improved through a series of subtle but impactful tweaks to our algorithms to be even more adept at detecting spear phishing attempts, including advanced, difficult-to-detect direct spoof attacks.
The fact is, bad actors are using increasingly sophisticated techniques to trick unsuspecting people into handing over sensitive information or granting access to controlled networks. It’s imperative that we stay ahead of the curve, hence the regular updates. Tessian Defender has improved over time – and will continue to improve – enabling the detection and prevention of even the most advanced spear phishing attempts.
-
What is Tessian Defender?
Tessian Defender detects and prevents advanced spear phishing attacks in real time by analyzing hundreds of data points within email headers, body text, and attachments.
3. Thwarted first-attempts. It’s now even more difficult for employees to exfiltrate sensitive data
Tessian Enforcer can now detect the first attempt an employee makes to exfiltrate data over email. How? By inferring what is and isn’t likely to be authorized communication based on the vast amount of data Tessian’s ML algorithm was trained on, which doesn’t necessarily rely on prior email history of a particular email address.
For example, if an employee attempts to send an email to their personal, freemail account and that email address contains the employee’s first name or surname, Tessian Enforcer presents a warning to the user advising them that the behavior is potentially unsafe and prompting them to reconsider the action.
Data exfiltration remains an incredibly unwieldy problem for businesses. Tessian gives businesses much-needed oversight of the problem over email.
-
What is Tessian Enforcer?
Tessian Enforcer prevents data exfiltration by allowing organizations to track and prevent sensitive information being sent to unauthorized or unsafe destinations based on triggers controlled by administrators.
4. In-situ learning opportunities. Employees have an opportunity to understand why an email is unsafe with contextual warnings
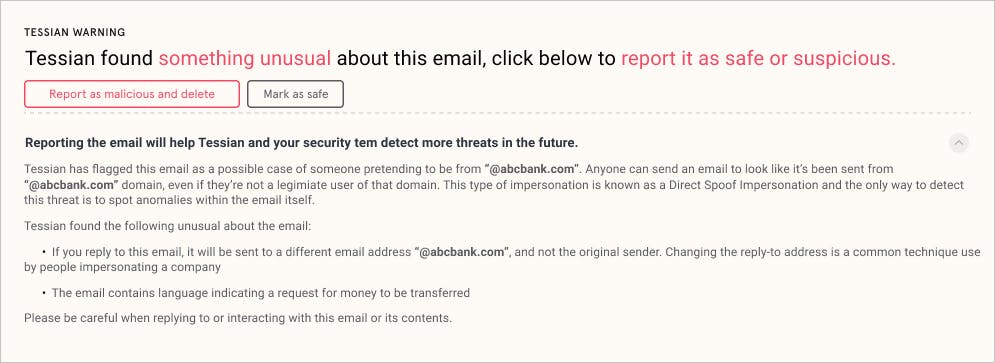
While Tessian prides itself on low flag rates so that security doesn’t impede productivity, we wanted to maximize the opportunity to educate users through our warnings. This way, when users do see a notification, they understand why.
Improved warnings across all four modules were designed for a more user-friendly experience that seamlessly reinforces any previous or ongoing security training. With more context included, employees can now see exactly why an email is being flagged as suspicious and – importantly – they can make their own decision on how to proceed.
This is at the core of Tessian’s mission. Employees should be empowered by security solutions instead of burdened by them.
5. New detection capabilities. Customers can create rules that are specific to their environment
Every business or enterprise is different and IT and Infosec security leaders need some flexibility in creating filter conditions that are applicable specifically to their operations. Because we’ve introduced new detection capabilities, users can now combine more conditions to create filters for their individual use cases; for example, scanning attachment content, identifying hidden fields in spreadsheets, and reading Azure Information Protect and other DLP labels.
At the most basic level, these rules look something like this: If A and B, then C, except when D or E. These variables can apply to a number of elements contained in an email, from the recipient(s) to language patterns.
One way an administrator might use these new detection capabilities would be to configure a filter which only allows the finance team, for example, to share spreadsheets with people outside of their organization if the recipient’s email address is recognized as a customer, except when the attachment contains a hidden row titled “social security numbers”.
Protect your most valuable asset: your people
Tessian is committed to creating the world’s first Human Layer Security platform and exciting developments lie ahead as we build out a holistic platform to protect people using email and, eventually, other interfaces frequently used in the workplace.
Not yet a Tessian customer?
Across four modules, Tessian protects the human layer by detecting and preventing both inbound and outbound threats. This includes advanced spear phishing attacks, accidental data loss, and data exfiltration. Tessian is quickly and easily deployed to Office 365, Exchange, and G-Suite, product updates are seamlessly rolled out for users and administrators, and the technology – which doesn’t disrupt workflow – was built with productivity in mind.
To understand how Tessian can fit into your existing security framework, request a demo now.
Harry Wetherald
Group Product Manager