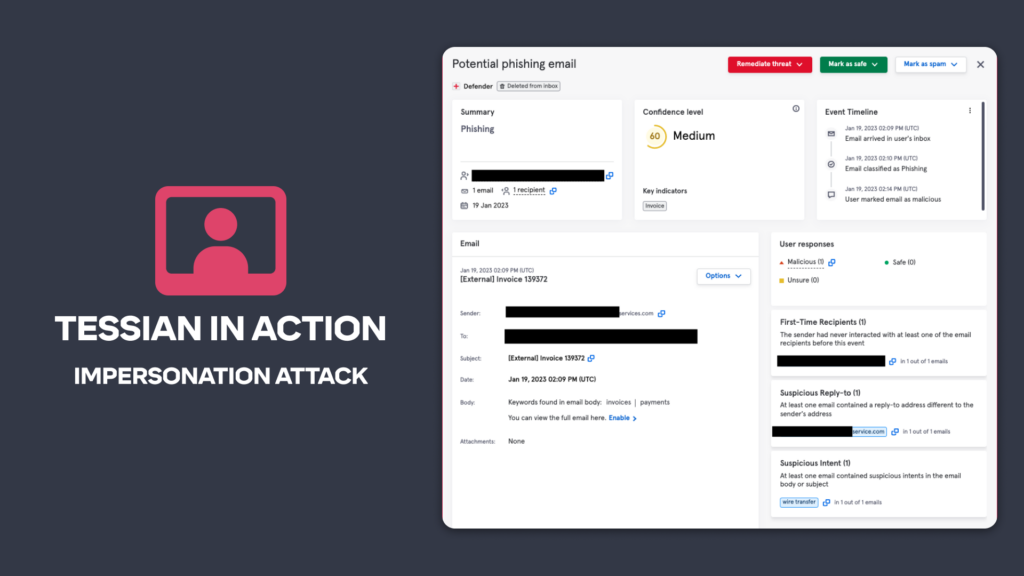
Here’s a real-life example of Tessian in action. On this occasion, Tessian has flagged a potential phishing email chasing an invoice payment from a supplier.
The client is a 3000-user global law firm and receives thousands of emails a day. In this attack attempt the threat actor has spoofed a legitimate existing domain for the approach, *******services.com. But crucially, for the reply address, the attackers used *******service.com, omitting the final S found in the original URL.
It’s a common technique for attackers to use a legitimate domain for the initial email to gain trust, and then use a lookalike as the reply to, so they can then divert all conversations to their own inbox. They hope it won’t look suspicious because the recipient will probably think that it’s the same sender’s address. The science behind the way humans read words would mean that this would be easily scanned over in a busy office.
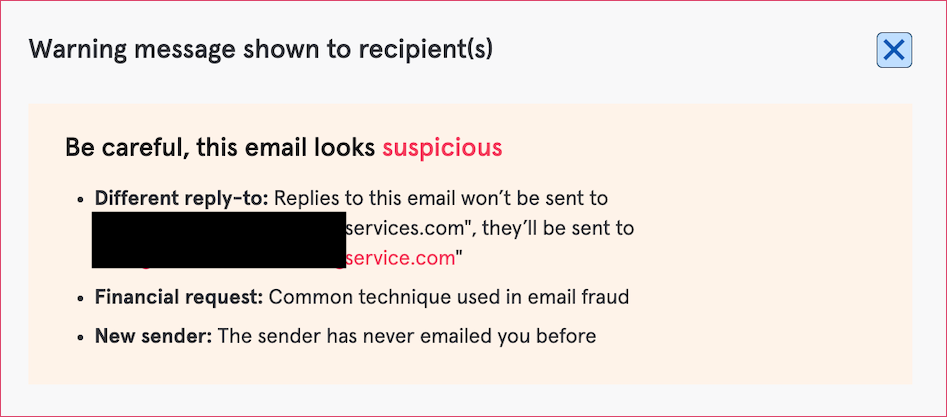
The warning displayed to the end user
Tessian alerted the end recipient that the email was suspicious and explained why in three simple points, after which they correctly marked it as malicious. It’s in-the-moment explaining and training like this that empowers employees to make the right security decisions themselves, without slowing down their workday.
And here’s how the Security Team saw the event in the Tessian portal. You can see that the user safely marked the email as malicious in under five minutes from when it arrived.
Tessian picked up on the fact that the reply to address is extremely similar to the sender address and that *******services.com is not very well known to the customer, based on their statistics. Other flags included keywords such as ‘invoice’ and ‘payment’.
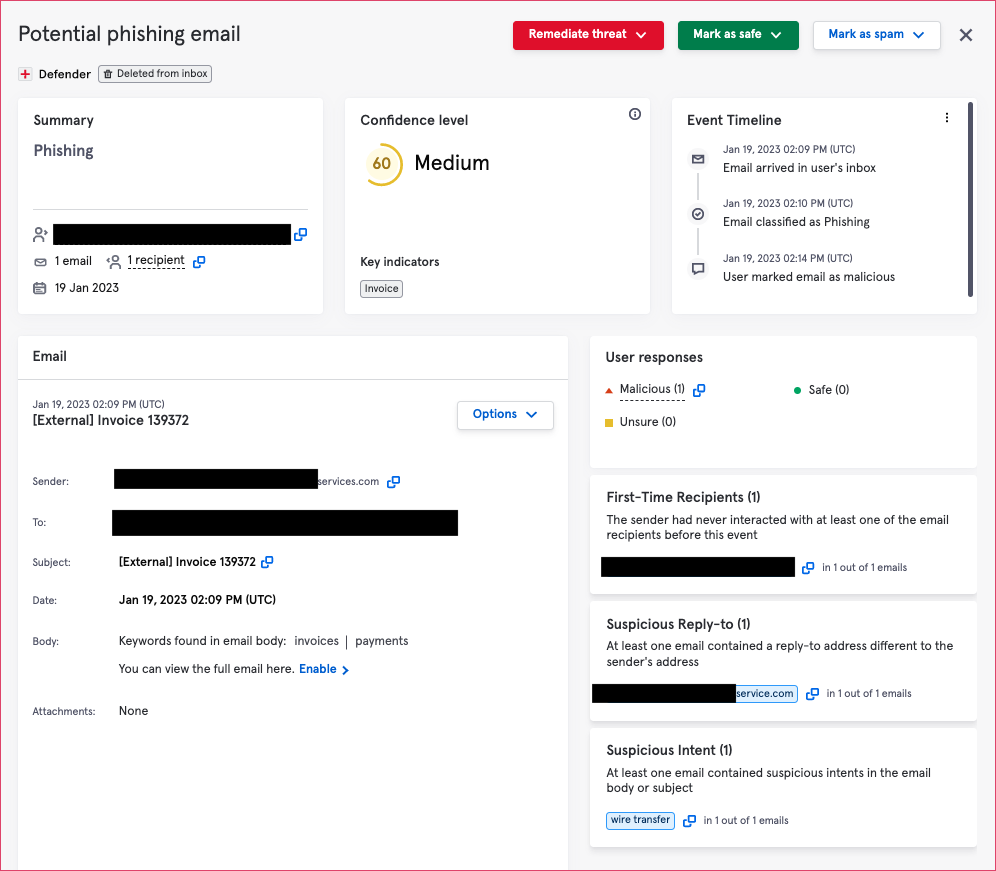
It’s also worth noting the time the email was sent, around 2pm GMT. Our own State of Spear Phishing report shows that the most successful attacks happen just after lunch, or towards the end of the working day, when people are at their most distracted.
Let’s now look at the email itself, and some of the social engineering triggers the attacker has used. It’s worth noting there’s just the right amount of suspicious intent: too much urgency such as ‘please pay immediately’ can cause people to double check and action it there and then, especially if the request comes from a senior manager or the C-Suite. Too little urgency meanwhile, means it might not get done at all.
The email arrived on Thursday 19th of January, with a suggested payment deadline of the 31st – just the right amount of nudging to ensure it’s quietly added to someone’s ‘to do’ list the following week.
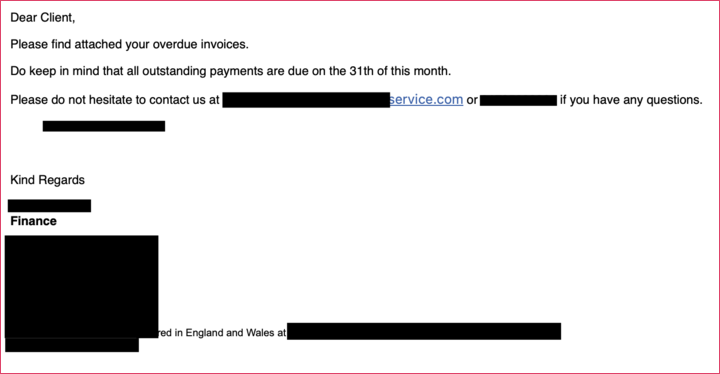
Attacks that mimic your suppliers can be particularly tricky to defend against, as psychologically, your organization and people have probably dealt with them before. Even small firms can have hundreds of different suppliers – from office cleaning to raw materials to payroll. For large multinationals like Walmart, or Total that number can run to over 100,000. That’s a lot of emails back and forth.
Tessian stops attacks like this on a daily basis, delivering a modern email security posture and protecting your end-users and data. But the best thing is we do all that, while reducing your security team’s workload. This ultimately saves you money and reduces complexity, leaving you confident that your organization is protected.
Tessian Threat Engineering Group
Tessian Threat Engineering Group