Recently, Tessian Defender detected and prevented an emergent threat across a large number of our legal and financial customers. Here’s how it happened…
This external Account Take Over (ATO) campaign contained over 500 malicious emails that evaded Microsoft’s and customers’ secure email gateway (SEG) controls. Subsequently, it went on to reach 20 of our customers’ inboxes. An ATO often occurs when a user accidentally shares their credentials with a threat actor allowing them full access to their email account.
Because a legitimate account was compromised, this ATO attack was sent from a trusted email address, with the correct domain, meaning it would have been almost impossible for an end user to identify it as malicious.
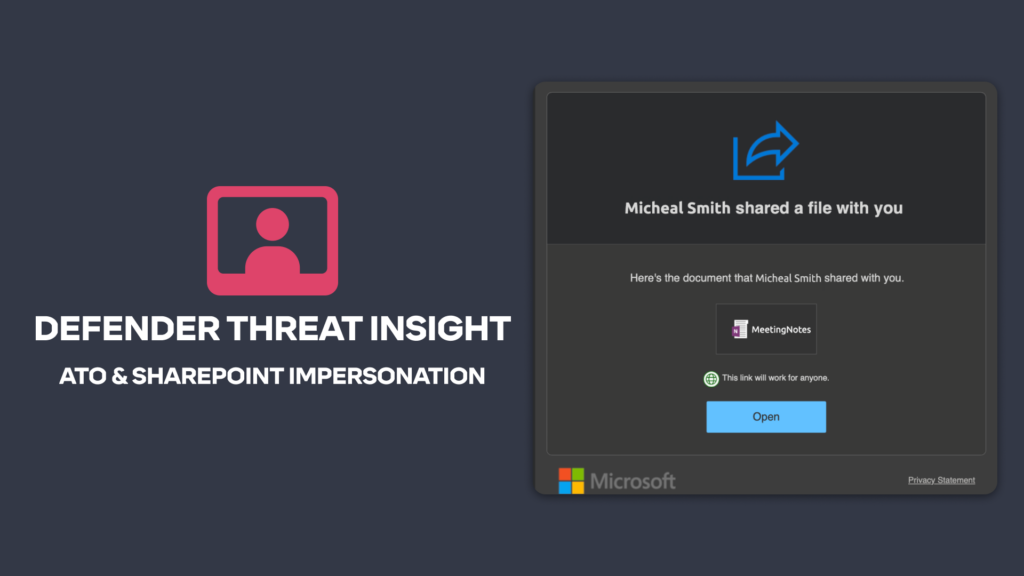
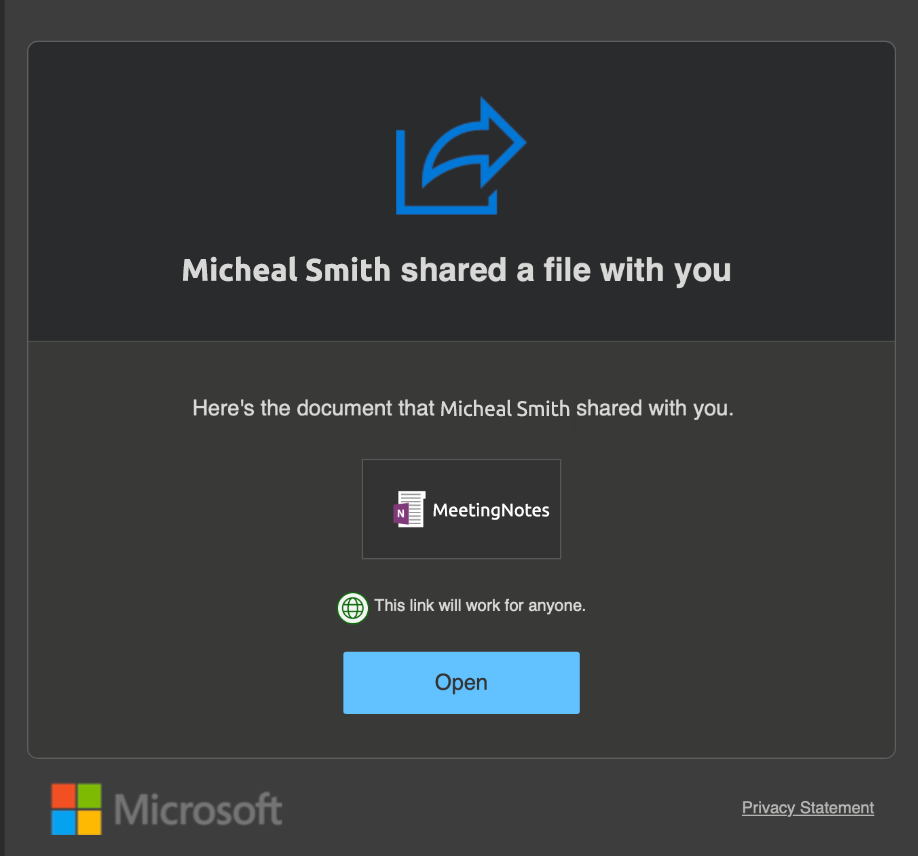
What’s more, the email content was a legitimate Microsoft SharePoint file sharing email pointing to a OneNote file in SharePoint. The hosted file pointed to a malicious website used to harvest user credentials. Here’s a screenshot of the SharePoint email (the name, file and entities have been anonymized).
Why did the SEGs not detect this threat?
There are two main reasons why a traditional SEG didn’t stop this attack. Firstly, external ATOs are extremely difficult to detect because the phishing email is sent from a legitimate account, it’s just a bad actor operating the account. This means all email authentication methods such as Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication Reporting and Conformance (DMARC), will pass.
Secondly, the email pointed to a legitimate SharePoint URL which, at the time of delivery, was not present on URL Threat Feeds. SEG detection relies heavily on signature-based, threat intelligence feeds. But for new and emerging threats, when the URL has not been seen before, there is no signature to detect so the only option they have is to deliver the email.
How did Tessian Defender detect this threat?
Tessian Defender’s behavioral intelligence models identified two clear anomalous signals to predict this ATO attack.
Firstly, Unusual Sender Behavior. A large amount of emails (~500) were sent from the compromised account, to many disconnected users on the Tessian network, in a short period of time. Successfully compromising an account is a rare event for an attacker, therefore the attacker will likely send many emails from the compromised account to trusted contacts in the account’s address book, as quickly as possible, before being discovered and before the credentials are changed.
Secondly, Unusual File Sharing Service Used. As mentioned above, Microsoft SharePoint was leveraged in this attack. There is nothing unusual or suspicious about SharePoint, however because Tessian Defender’s behavioral models have a deep understanding of every relationship in our customer’s accounts, they were able to identify that the sender of this email had never used the SharePoint service in previous interactions.
Depending on the specific customer configuration, Tessian Defender either hard-quarantined this email or displayed the following warning message to end users:
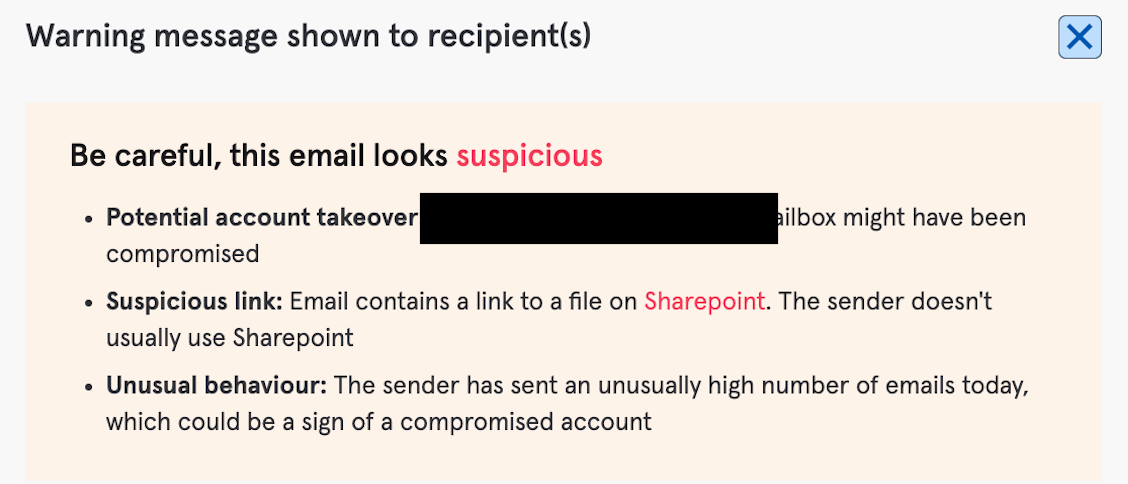
This email was confirmed to be malicious by end users and security analysts across our customer base – reinforcing and strengthening the Tessian Global Threat Network, and nullifying this emergent threat.
Account takeover attacks are becoming an increasingly common category of threat – driven by their ability to evade existing Microsoft and secure email gateway controls. Consequently, there is a strong likelihood of an end user being tricked into trusting the legitimacy of the email. Once inside a threat actor can deploy ransomware, instigate fraudulent fund attacks, and continue to move laterally through a customer by compromising higher target accounts.
Tessian Threat Engineering Group
Tessian Threat Engineering Group