Scammers and threat actors are continuing to use the COVID-19 pandemic as a theme for their phishing campaigns. The latest trend? Asking people to download their ‘proof of vaccination’ or vaccine certificates.
In fact, in a recent Tessian survey, 35% of US citizens and 22% of UK citizens said they’d received a ‘proof of vaccination’ phishing email this year.
That’s because (as you likely know) most businesses and travel companies are requesting that people now provide proof of vaccination or digital vaccine credentials. Attackers see this as an incentive to get targeted recipients to click links in phishing emails.
What do these emails contain?
Tessian researchers have been analyzing emails related to ‘proof of vaccination’ scams over the past six months and found that, in many of the emails, cybercriminals will apply a sense of urgency to their messages, using subject lines that include “IMPORTANT” and “OFFICIAL”.
This is a common social engineering tactic, prompting the person to act quickly so that they don’t spend too much time thinking about the consequences of complying with the request.
The call to action in 80% of the emails analyzed is to click a link to request and download a COVID-19 vaccination passport or certificate, explaining that if the recipient doesn’t have their proof of vaccination, they won’t be able to travel or must remain in quarantine.
Wouldn’t you want to act fast?
Most emails also contained a payload of either a malicious link or attachment which would direct the recipient to a web page designed to trick them into entering sensitive information such as personal details, credit card or banking details in order to receive their proof of vaccination.
Example of phishing website: hxxps://nhs-vaccinepass.com/
Of the emails analyzed, 20% of them contained language indicating an intent to steal information. Once cybercriminals have this information, they can use it to access your other online accounts or commit identity fraud.
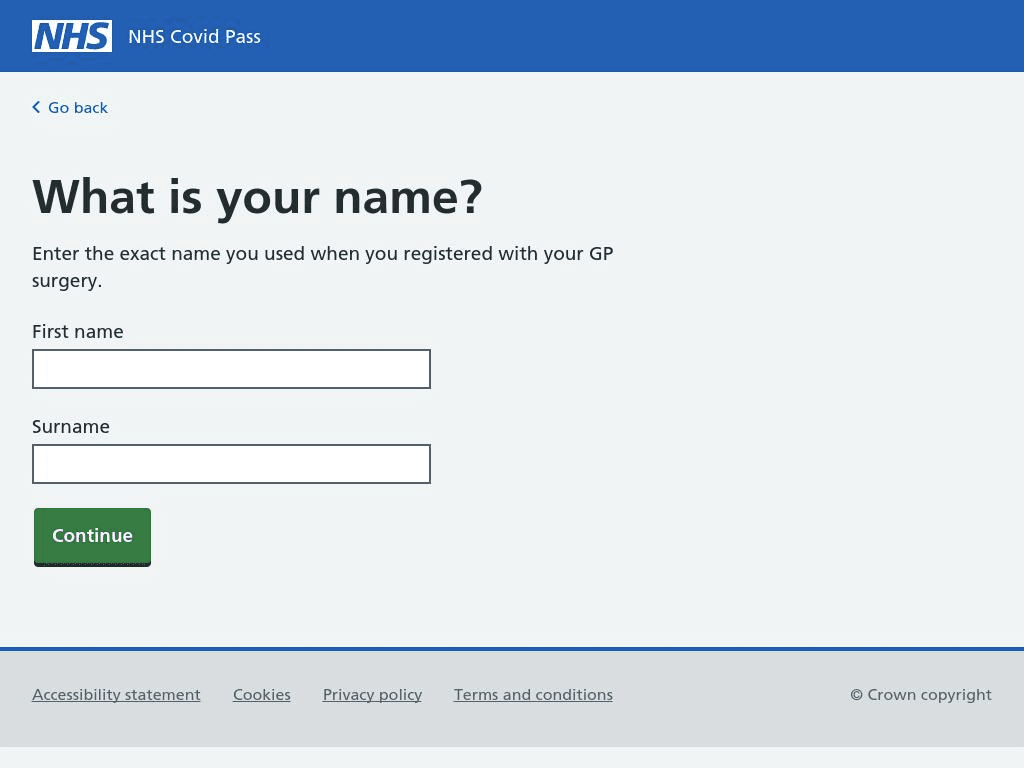
In the UK, the majority of the ‘proof of vaccination’ scams saw attackers impersonate the National Health Service (NHS), tricking their targets into thinking they’d received an email from a legitimate and trustworthy source.
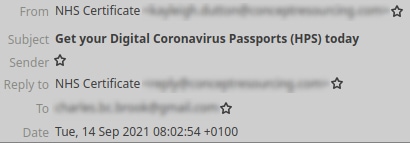
Here’s an example of an email sent from a business email address using compromised credentials:
This screenshot captures the sender's Display Name, Email Address, and Subject Line
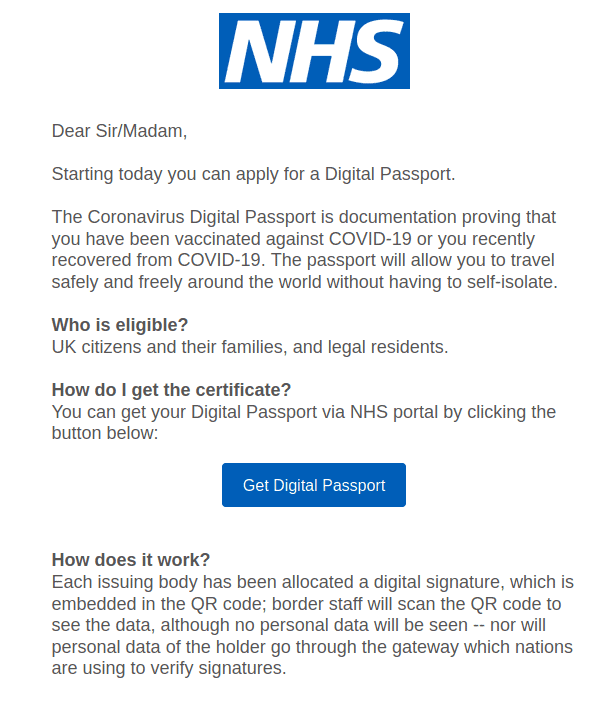
This screenshot shows the body copy of a vaccine scam email, which appears to be from the NHS
For anyone quickly glancing at this email, it looks like the real deal.
The attacker has spoofed the NHS in its display name, used the correct logo, and avoided any spelling mistakes. Only when you look at the sender’s email address can you see that it’s not actually from the NHS.
How can you avoid falling for a ‘proof of vaccination’ scam?
If you require ‘proof of vaccination’ for any of your upcoming holidays, plans, or activities, or if you have any questions, always go through direct channels with your local authority. You can find their email addresses or phone numbers via their website.
Remember;
- For UK residents, the NHS App is free, the NHS Covid Pass is free, and the NHS will never ask for payment or any financial details.
- For US residents, COVID-19 vaccination providers cannot charge you for a vaccine or charge you for any administration fees, copays, or coinsurance.
So, if the sender of the email is asking you for money or payment information, such as bank details or card details, it is likely a scam.
If it looks suspicious, avoid clicking any links or attachments. Mark the email as spam or move it to your junk folder to help improve dedication against the type of malicious email and if you’ve received the email on your work email, then report it to your IT team. Then, hit delete.
Charles Brook
Threat Intelligence Specialist