Defend against advanced email threats
“Tessian detects email impersonation and account takeover attacks, and protects us against advanced threats that traditional email gateways cannot detect”
-
Phishing attacks are evading existing controls
-

250,000
BEC incidents reported to the FBI since 2013 -
$4.5M
Average cost per breach of Phishing and BEC attacks -
95%
of attacks are the result of successful spear phishing
Defend against advanced phishing attacks
Email Threat Defense
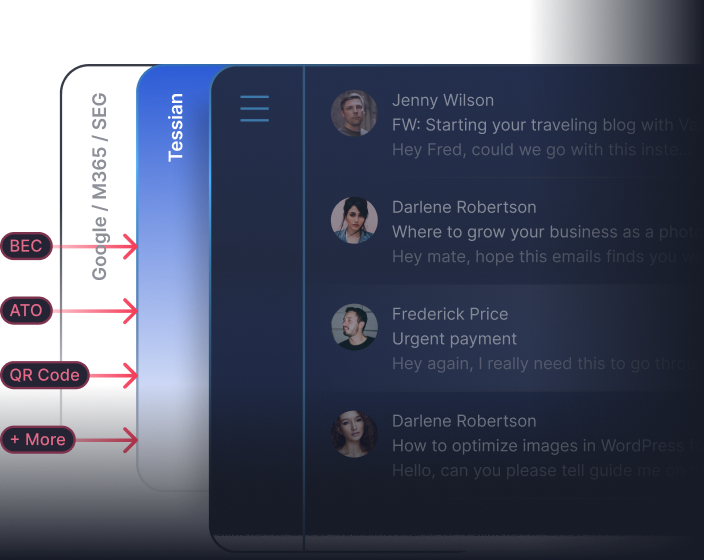
Prevent email threats that slip past your defenses
Tessian automatically stops advanced email threats like BEC, account takeovers, QR code phishing, and executive impersonation attacks that bypass existing solutions.
Email Threat Defense
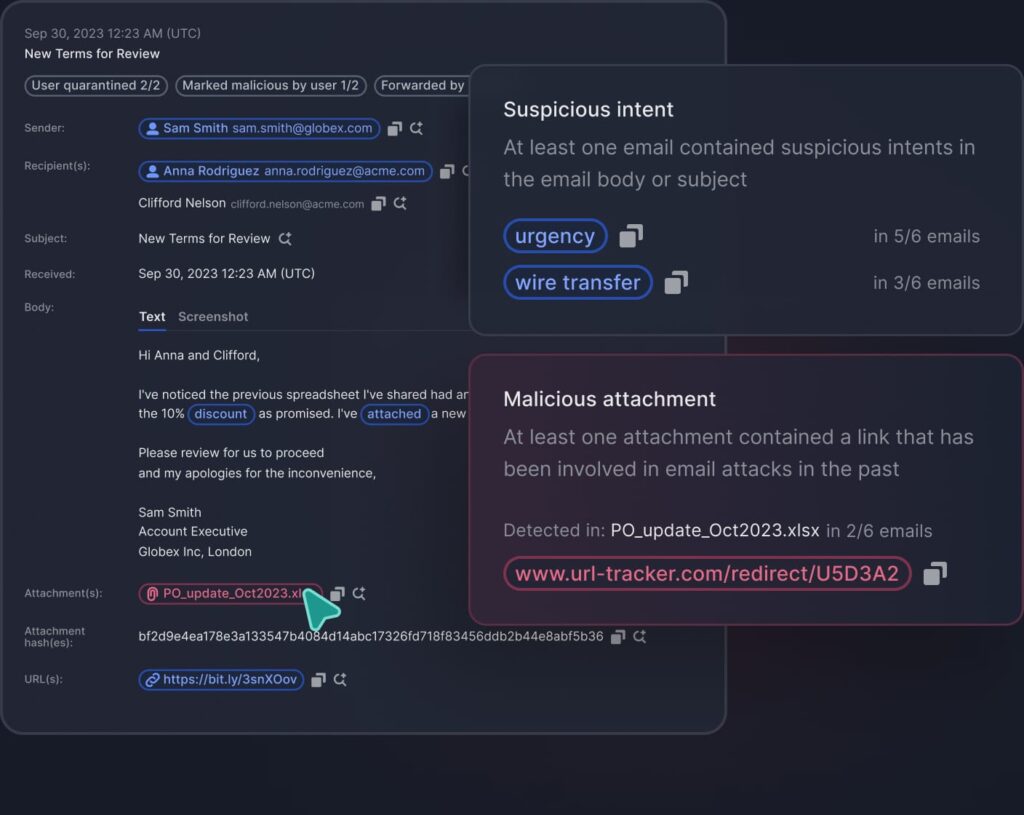
Detect targeted email attacks with AI
Tessian uses an ensemble of AI approaches to power behavioral, content, and threat network analysis.
Email Threat Defense
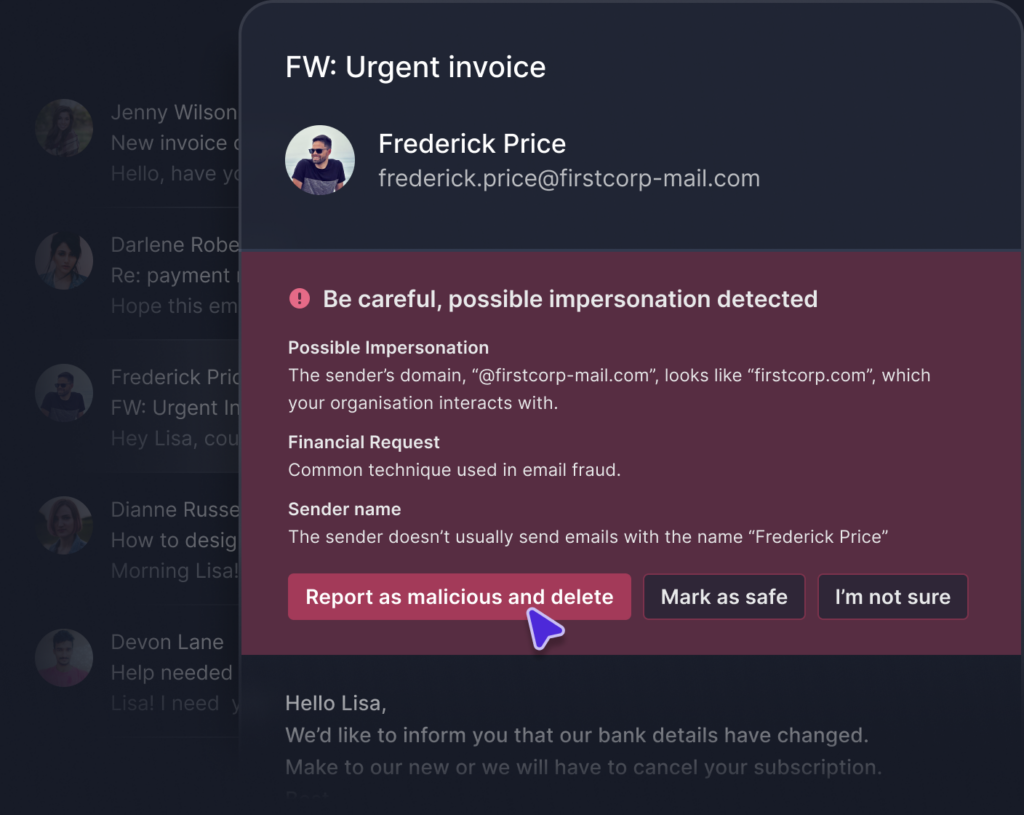
Coach users to keep security and convenience in balance
Empower end users to make informed decisions in the moment, and minimize business disruption with intuitive warnings that provide context for why emails are flagged.
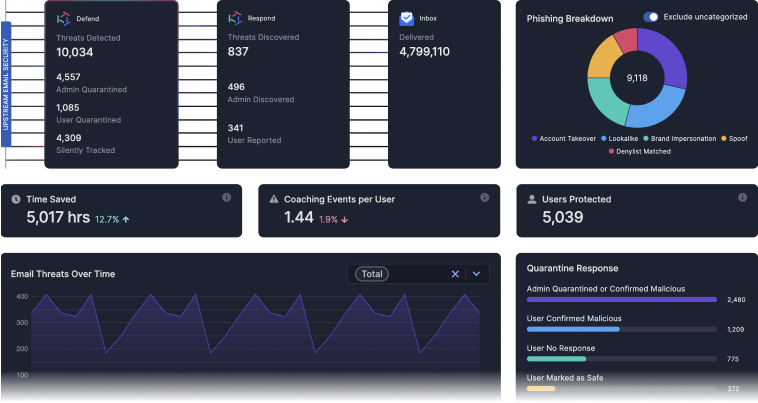
Insights that strengthen your email security
Tessian provides email insights, dashboards, and reporting so you can make better security decisions. Admins can view an up-to-date breakdown of phishing attacks, targeted users, time saved, and more.
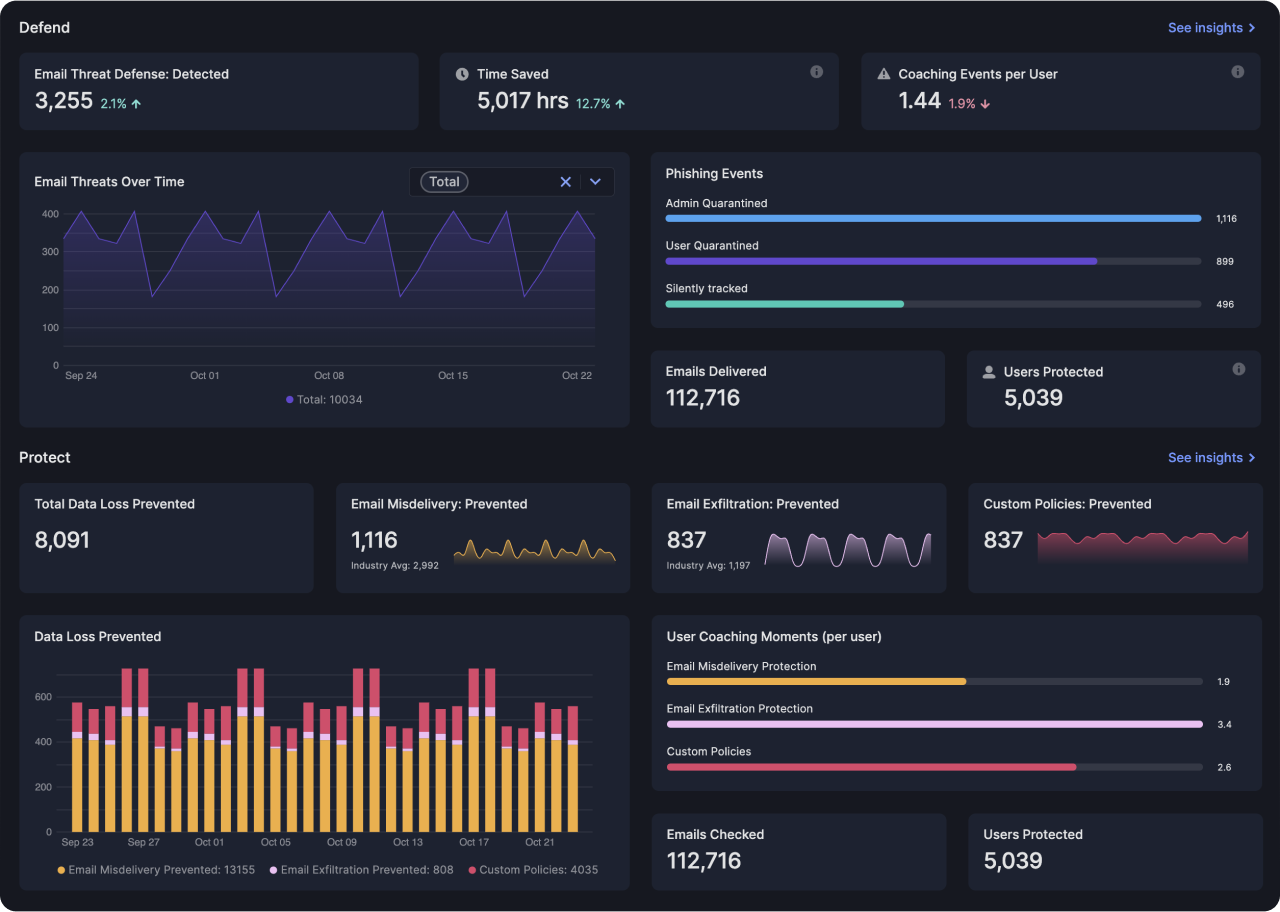
Complete cloud email security, deployed in minutes
Built to enhance Microsoft and Google email environments, Tessian is deployed in minutes through native API integrations with email providers.
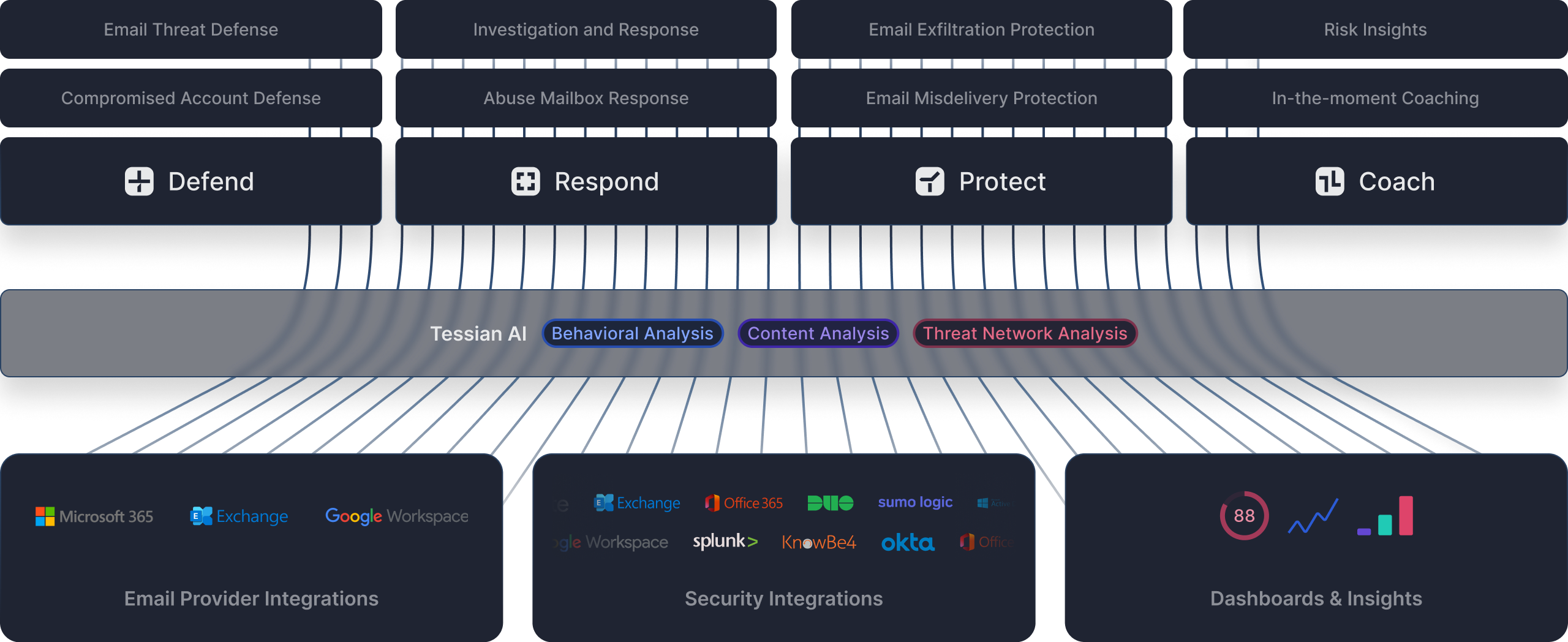
an integrated approach to email security
Better together
Tessian’s cloud email security platform provides full lifecycle email threat management by integrating deeply with your identity, SIEM, SOAR, and CDR platforms. These integrations allow you to get the most from your stack through empowering automated and connected workflows.
get in touch
See Tessian in Action
Book a personalized demo to see how Tessian detects and prevents advanced email threats and data loss via email.