Product Resources
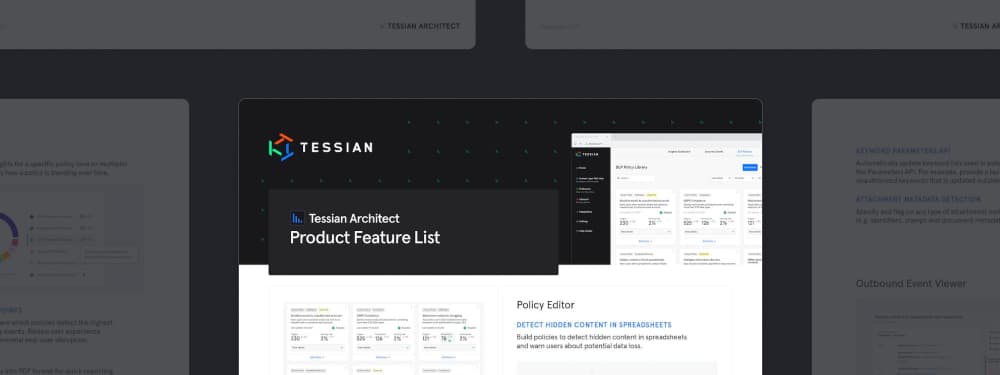
Tessian Architect Product Features List
Tessian Architect is a powerful policy engine for real-time email data loss prevention. It features a combination of the classic elements of DLP policies, as well as intelligent policies that provide custom protection against sensitive data loss.
This in-depth features list provides detailed information about Tessian Architect capabilities, including:
- Intelligent DLP Policies: Choose from a range of policies pre-built by Tessian to meet your organization’s most pressing policy enforcement needs. Use community policies to adopt best practices from other customers in the Tessian network.
- Policy Builders to detect hidden content in spreadsheets and warn users about potential data loss.
- Integrations with data classification tools: Leverage your investments in Microsoft Information Protection (MIP) and detect MIP labels with Tessian policies (e.g. detect when attachments labelled as ‘Confidential’ are sent to unauthorized accounts).
- Many more…
-
 Product Resources
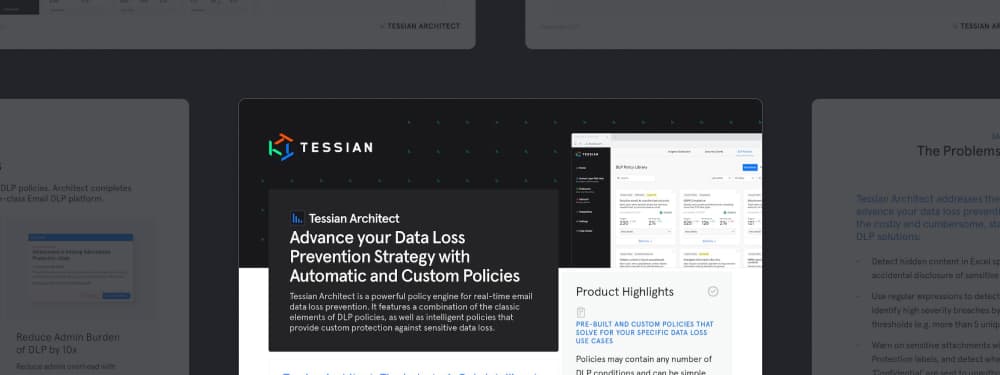
Product ResourcesTessian Architect: Leverage Intelligent and Custom Policies
-
 Solution Briefs
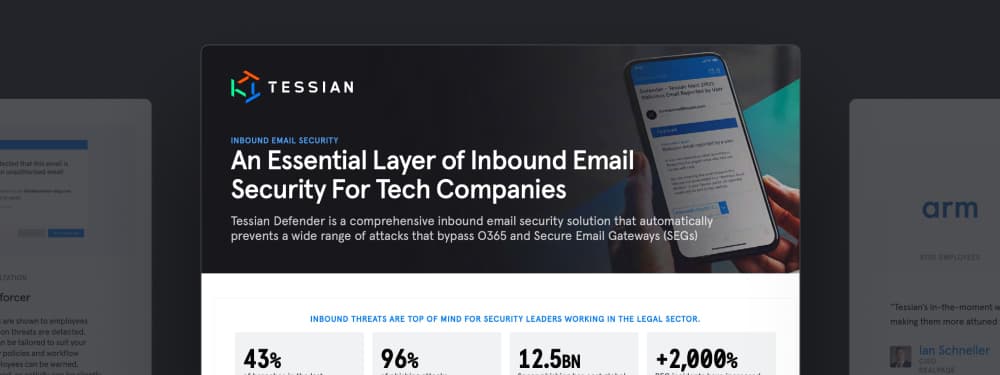
Solution BriefsAn Essential Layer of Inbound Email Security For Tech Companies
-
 Solution Briefs
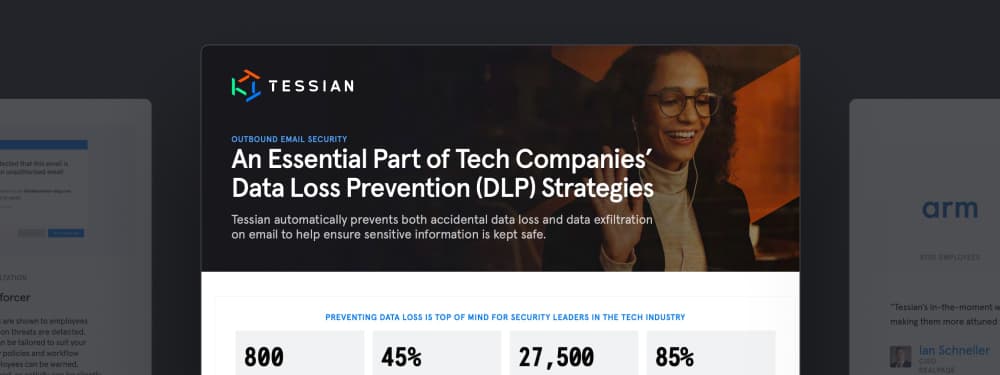
Solution BriefsAn Essential Part of Tech Companies’ Data Loss Prevention (DLP) Strategies
-
The Tessian Human Layer Security Platform Architecture
-
 Whitepapers
Whitepapers451 Research: DLP Market Insight Report