Research & Reports
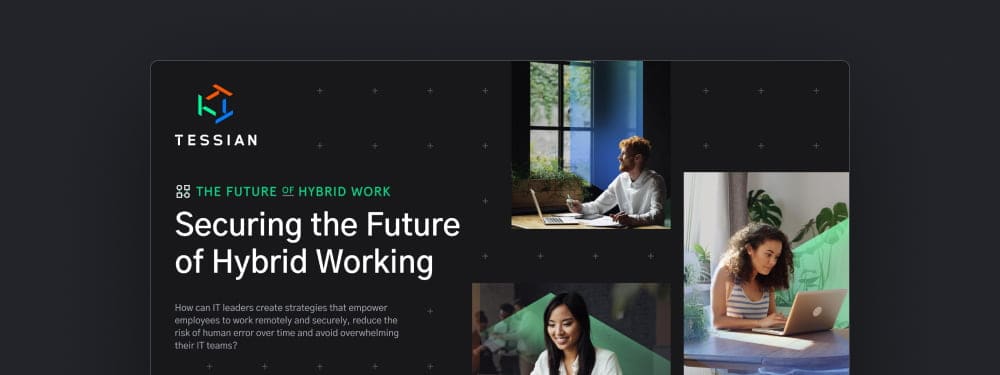
How to Hack a Human
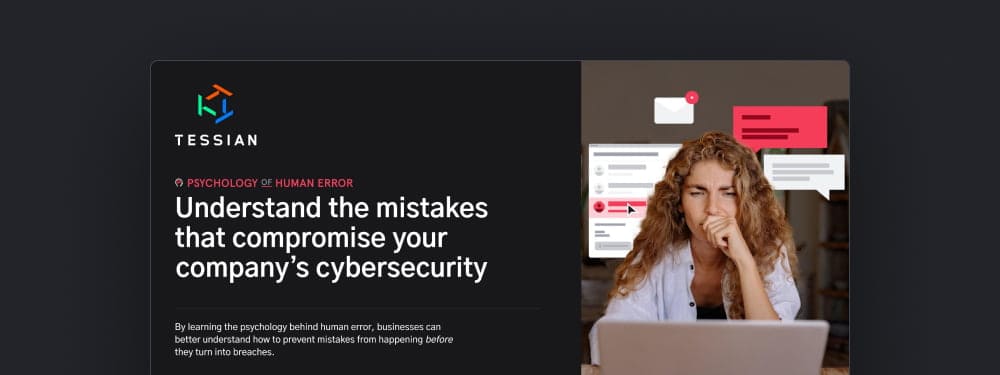
Over the last decade, phishing – a type of social engineering attack – has transformed from something more like spam to the threat most likely to cause a breach. During that same period, the number of adults on social media platforms like Facebook increased by almost 1,300%.
See the correlation? To find out just how vulnerable people and businesses are, we surveyed 4,000 employees and interviewed ten hackers.
Download the report now.