Healthcare organizations handle some of our most sensitive and personal data, which makes them highly vulnerable to cyber attacks. Here’s how to prevent them.
Electronic protected health information (ePHI) breaches over email occur when sensitive patient information is transmitted or stored through unsecured email communication. The cause of this type of breach can be unauthorized access, hacking, human error, and technological malfunction.
Healthcare organizations are complex with employees and contractor stakeholders across medical records teams, practitioners in clinic settings, non-technical employees, medical officers, and patients themselves accessing data. This diverse set of users and use cases makes managing ePHI and understanding when a breach has occurred that much more challenging.
In the US, the Health Insurance Portability and Accountability Act’s Breach Notification Rule (45 CFR §§ 164.400-414) requires covered entities and their business associates to provide notification of a breach that involves unsecured protected health information.
For breaches that affect over 500 individuals, organizations must notify the Department of Health & Human Services (HHS) and prominent media outlets within their state within 60 days following a breach. Additionally, many states including California, Michigan, Florida, and Arizona have similar or more stringent reporting requirements.
Impact of ePHI Breaches
Breaches not only cause reputational damage, but the HHS’ Office for Civil Rights (OCR) imposes fines based on the severity of a breach and an organization’s compliance with recommended security controls. For example in 2022, Oklahoma State University Center for Health Sciences was fined $875,000 for a breach affecting 279k records.
To help reduce these large fines and to drive the right security controls, the recent amendment to the HITECH Act in 2021 incentivizes HIPAA-regulated organizations to adopt “recognized security practices” to better protect patient data.
There are 18 HIPAA Identifiers considered ePHI. These identifier elements include: Name, Address, Dates related to an individual (e.g., DOB, discharge date), telephone number, email address, social security number, medical record numbers, health plan beneficiary numbers, account numbers, IP addresses or web URLs, biometrics, and photographs.
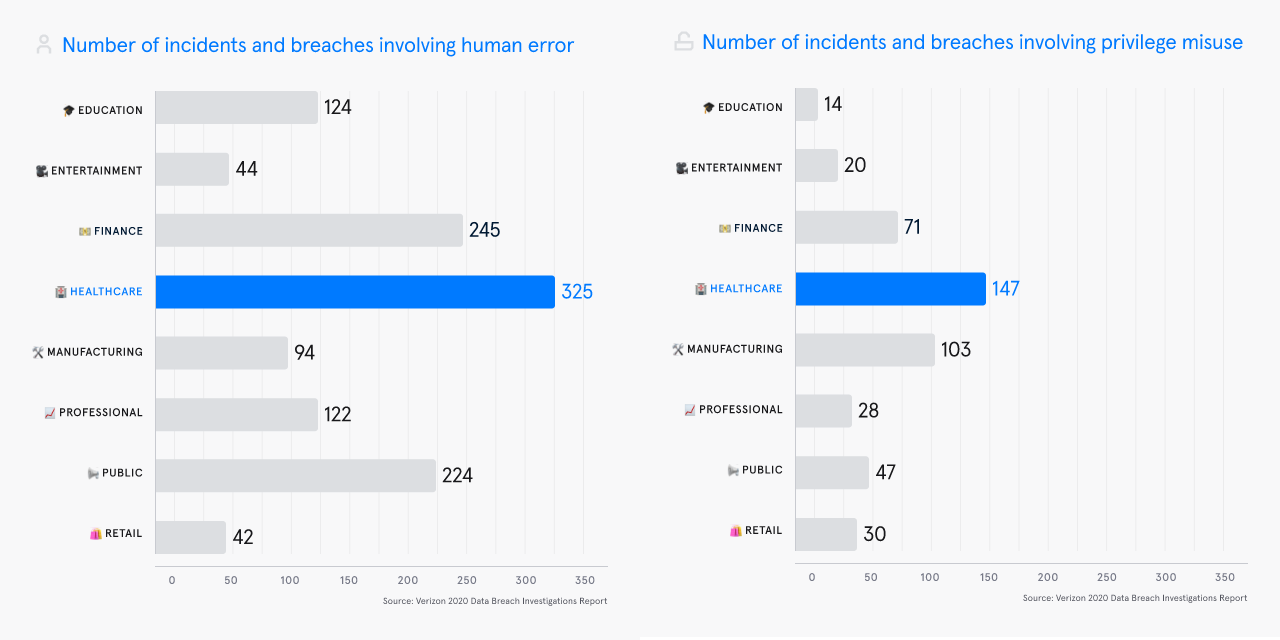
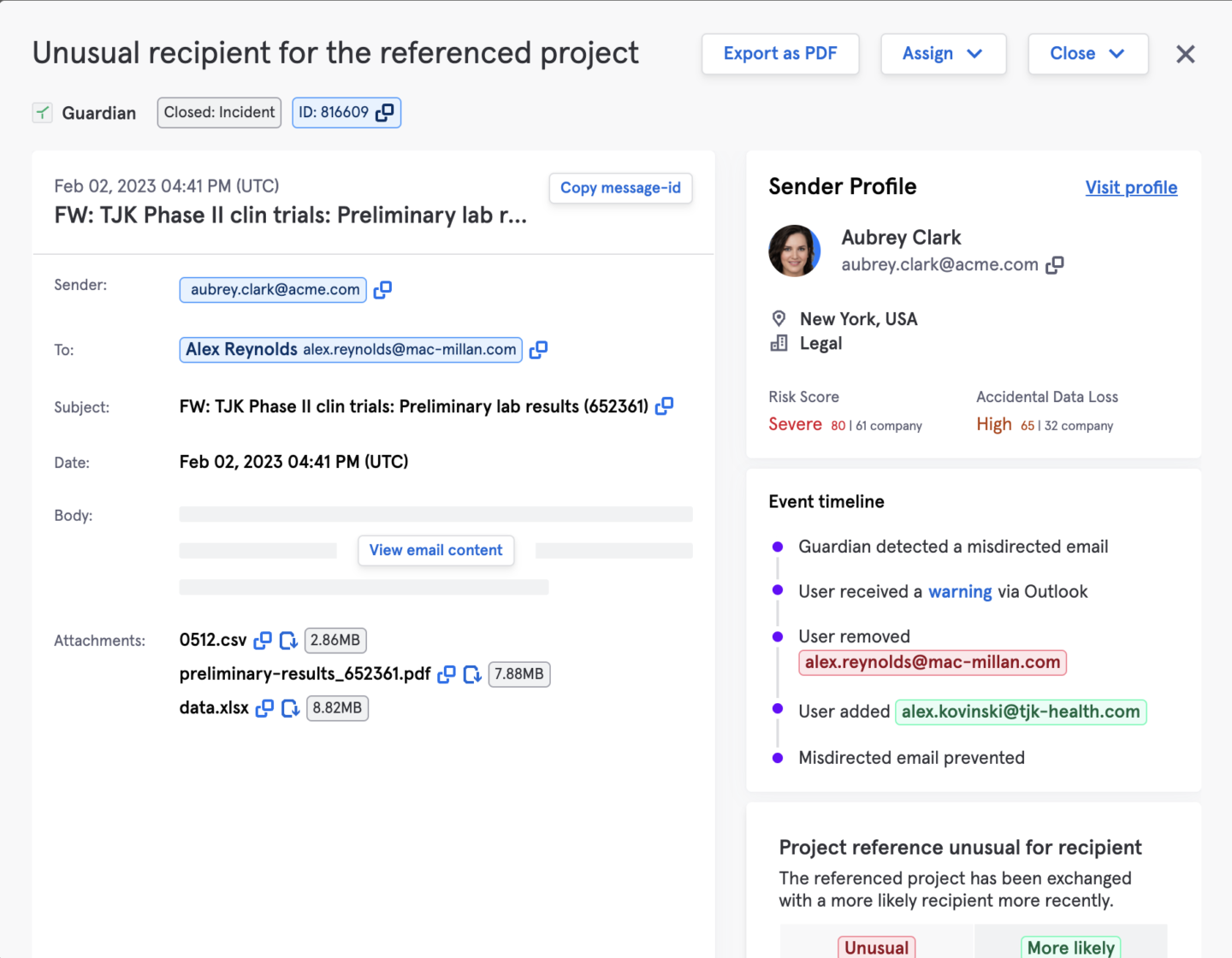
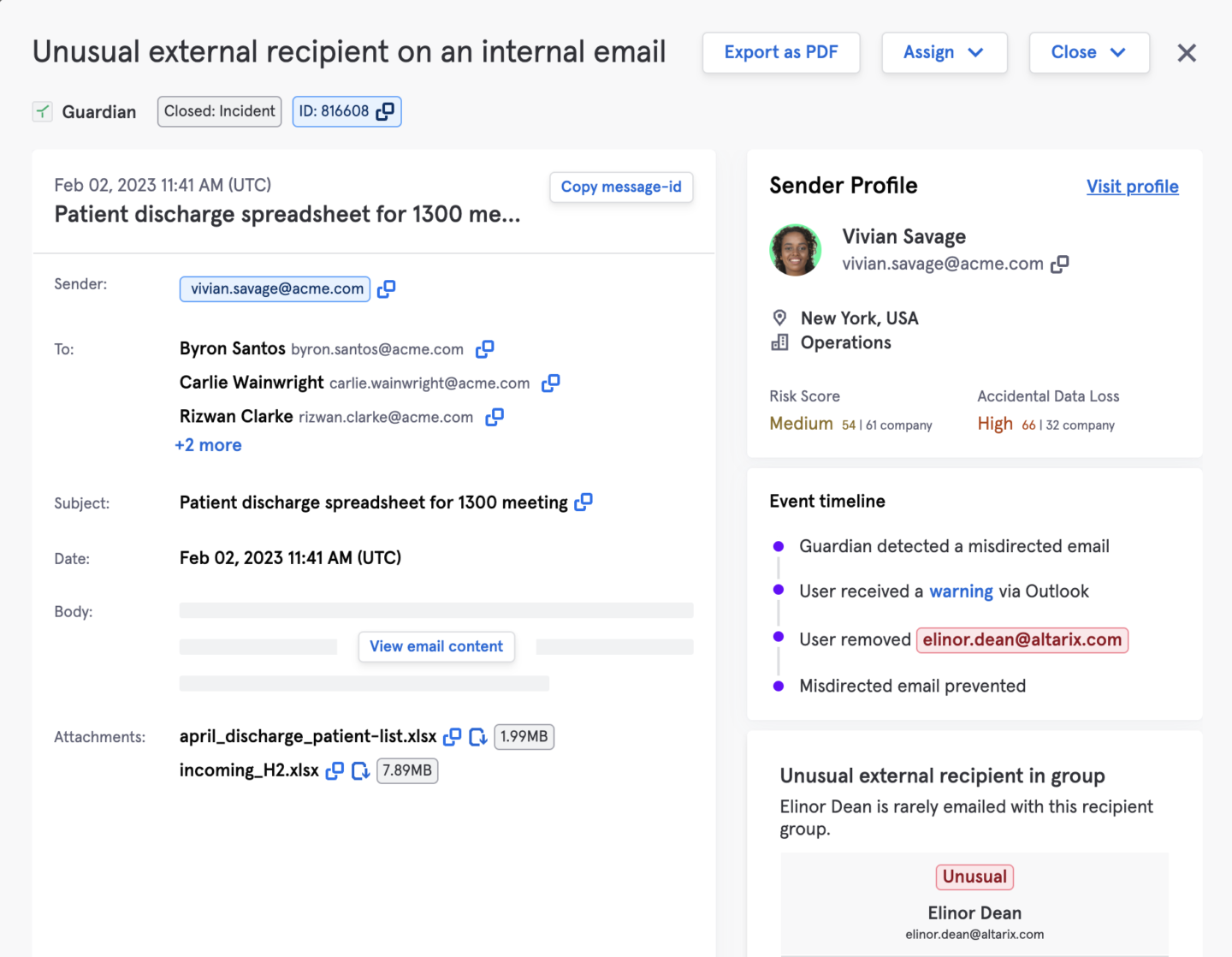
A common breach scenario is when an employee or contractor sends an email with ePHI to the wrong recipient. This can occur when an incorrect email address is entered, autocorrect selects a different email, a recipient forwards an email to another person, or the recipient’s email account is compromised. Privacy and GRC leaders in healthcare struggle with user error and user accidents with ePHI as it is a top cause of data breaches.
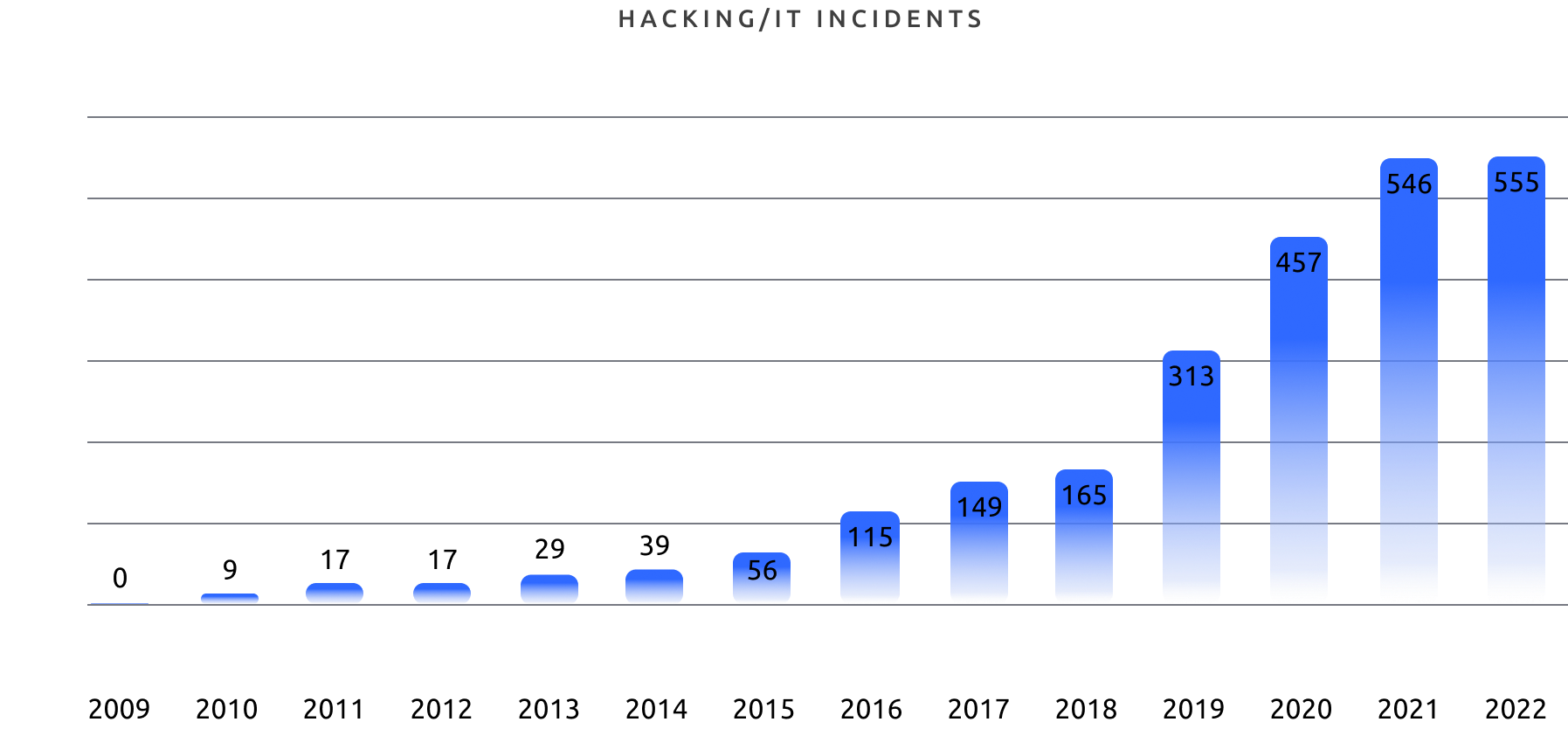
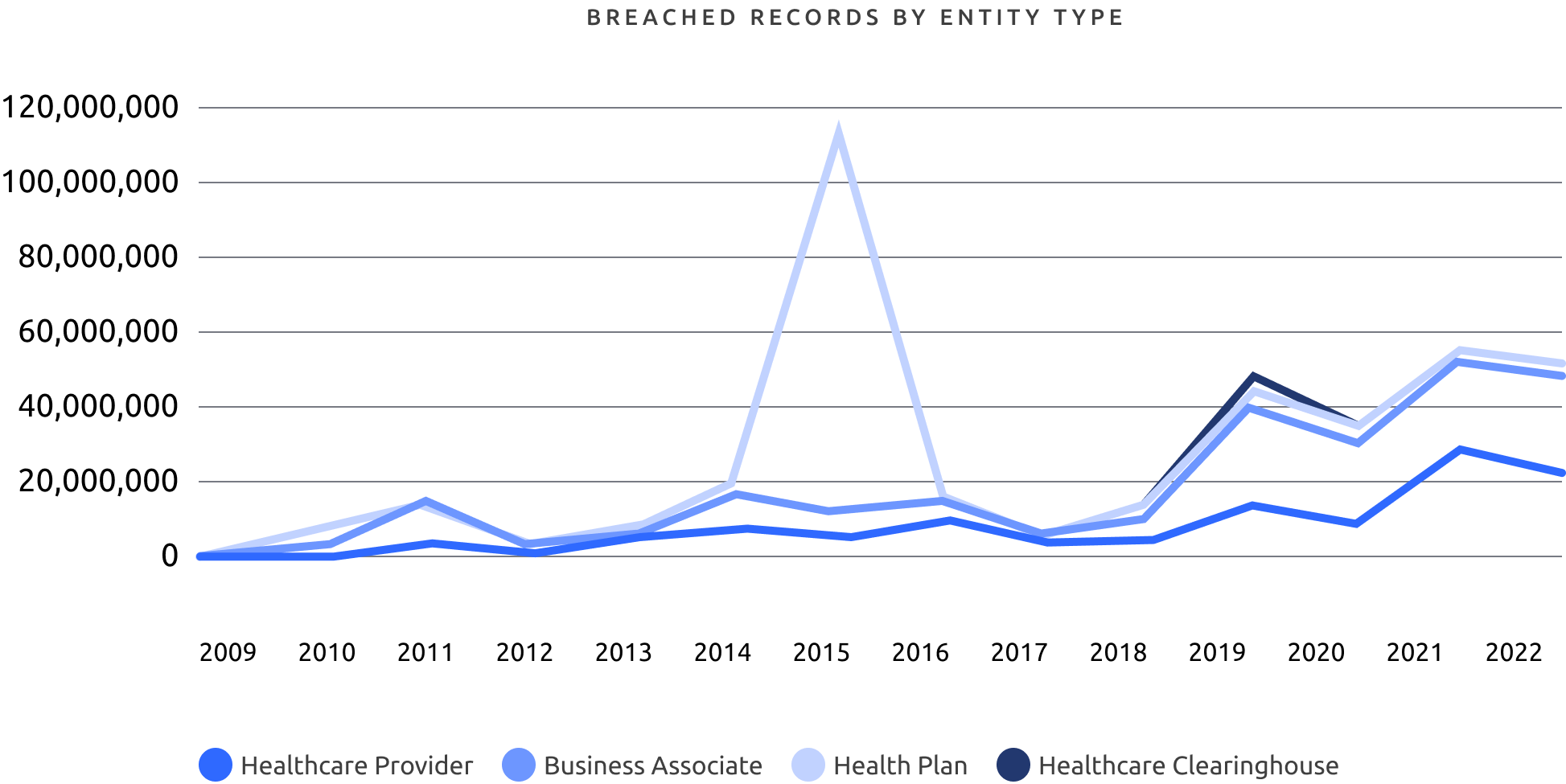
Let’s look at the numbers. The HIPAA Journal Breach report has been documenting breaches for the last 23 years. To date, there have been 5,150 data breaches reported between October 21, 2009, and December 31, 2022. What’s more, 882 of these breachers are still under investigation
The HHS’ Office for Civil Rights reports show a sharp increase in business associate reported breaches. These are the business partners and counterparties to healthcare providers who access ePHI. Many larger healthcare organizations now require security audits and data protection reviews for their business counterparties to mitigate this risk.
Why? Because In 2022, nearly 90% of healthcare breaches involved third party vendors. In one example, a large health plan provider recently mandated stricter email data loss controls with one of their business partners (and subsequent acquisition) to ensure the ePHI shared between the parties was closely monitored and accidental sharing was eliminated.
Preventing ePHI Data Loss Over Email
There are few solutions that can effectively prevent cases of ePHI data loss via email without implementing complex and time-consuming policies and rulesets. Tessian is used today at many large healthcare organizations to protect ePHI data loss over email by:
- Ensuring confidentiality that ePHI data being is being sent to the correct, authorized recipient via email (preventing misdirected emails)
- Preventing impermissible disclosure of sensitive or unauthorized data from leaving the org (i.e. data exfiltration)
- Enforcing proper classification and compliance of emails being sent out (data labeling, keyword matching, etc.)
Tessian protects ePHI data over email in 3 main ways:
- Historical analysis of email activity, behavioral context, and natural language processing to create a Behavioral Intelligence Model for each employee
- Understanding the working relationships between individuals and their external contacts to detect anomalous activity
- Classifying email content and warning users with in-the-moment training or automatic blocking of ePHI data
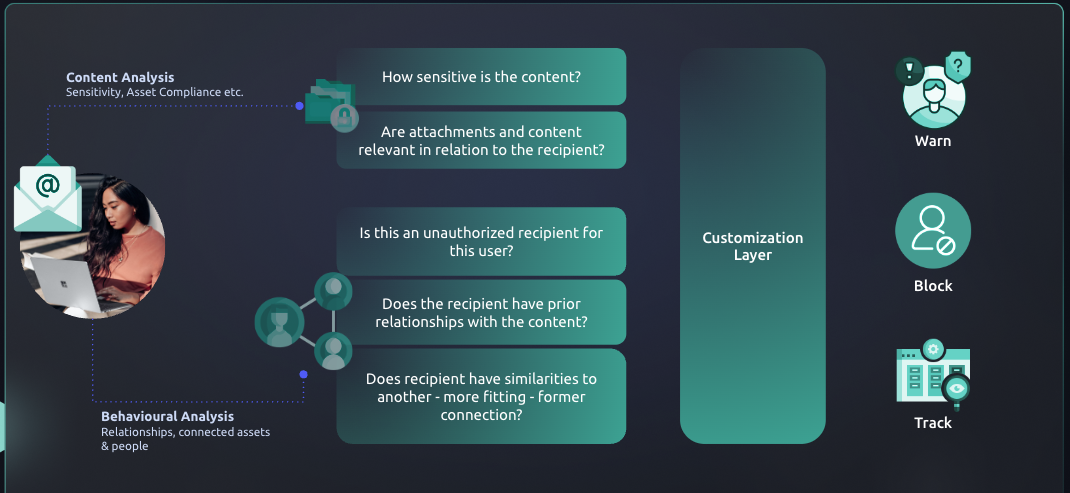
Through historical email analysis of an organization’s email activity as well as constant email monitoring and threat intelligence, Tessian applies advanced machine learning techniques such as content analysis (URLs/Attachments), Behavioral Context, Natural Language Processing, Linguistic Styles (sense of urgency), Intent Analysis (payment request/fake invoice) to form a customer-specific Behavioral Intelligence Model that detects and filters unintentional and malicious data loss events on email.
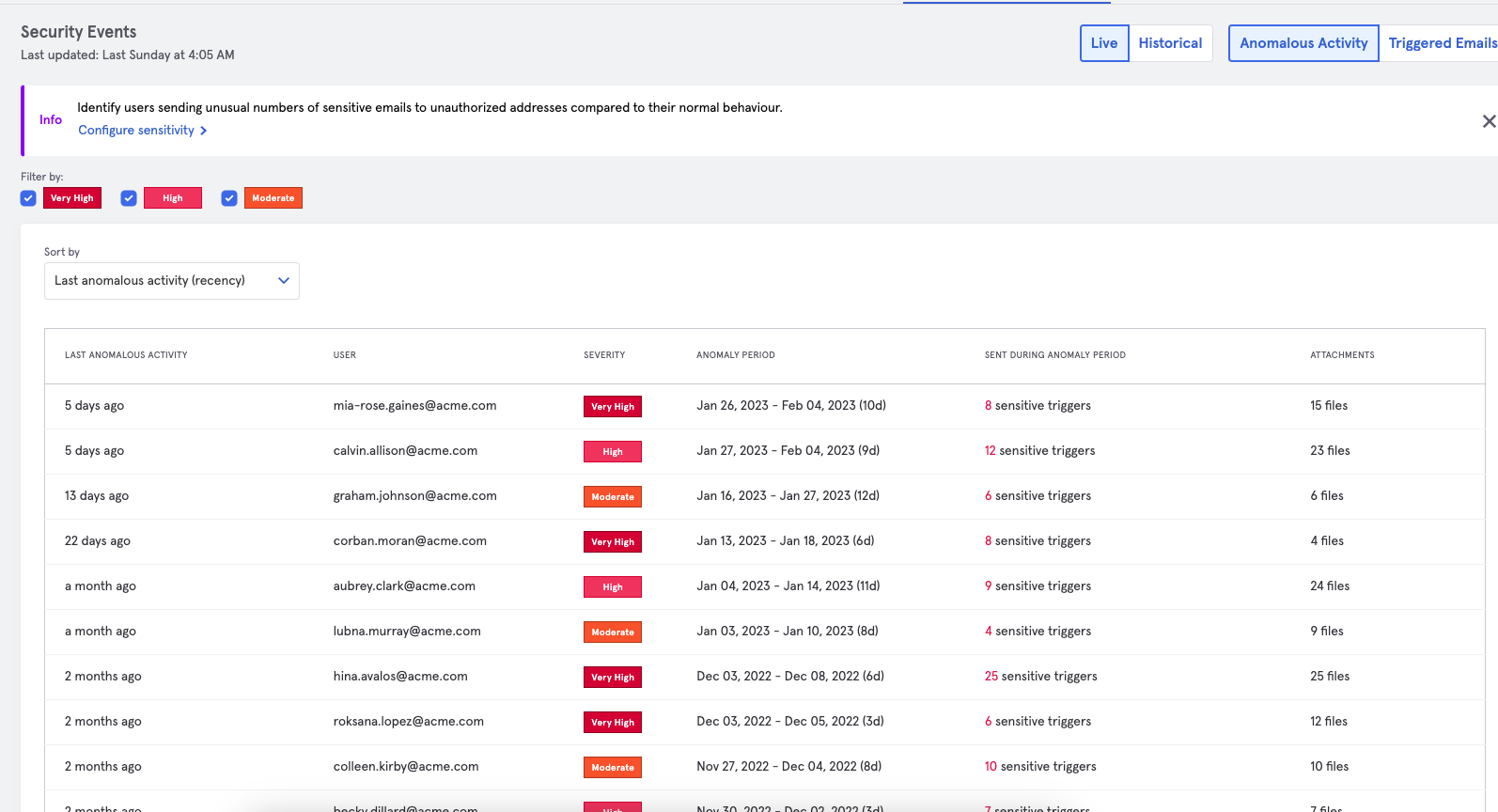
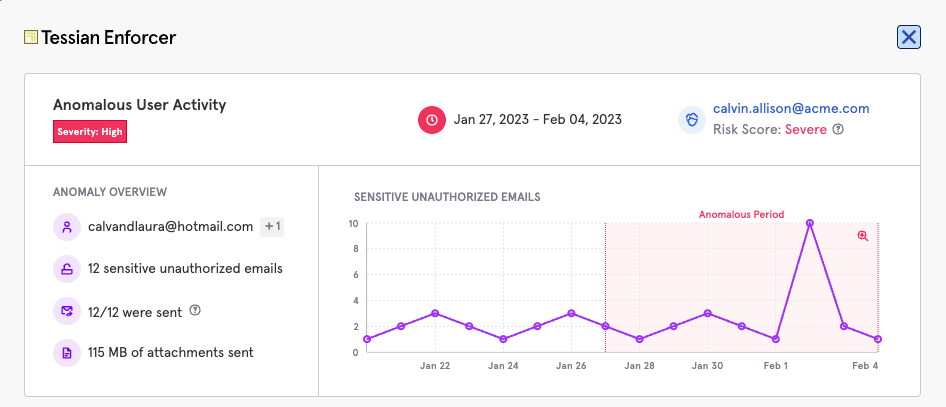
By forming an understanding of the expected working relationships between individuals and baselining normal end-user behavior on email, Tessian can detect anomalous activity such as misdirected emails as well as identify end-users who have the riskiest behaviors. Often ePHI breaches result in data being accidentally shared with the wrong party which often results in a reportable event.
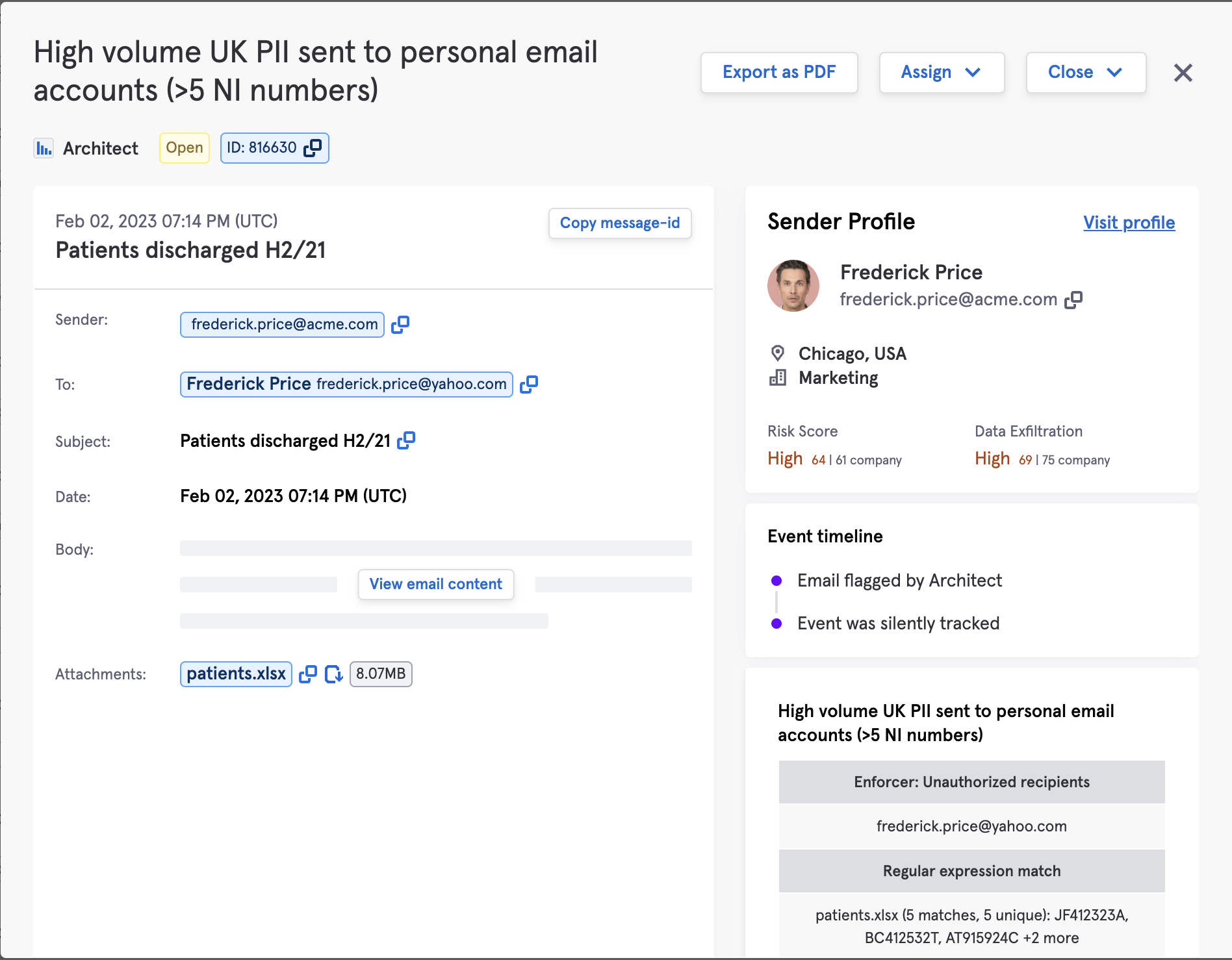
Tessian’s ML Algorithm identifies the level of sensitivity of email content (e.g., containing social security numbers) while warning users with in-the-moment training or blocking exfiltration attempts where required.
Within the Tessian portal, administrators can automatically detect data leaving the organization that contains ePHI. Admins can choose to just monitor, warn, or automatically block emails that contain sensitive data. These controls are automatic and do not require building extensive policies using regex or other lists
With Tessian’s reporting capability a security team can provide a clear summary of potential breach events to share with the Data Protection or Compliance Officer for further investigation. Using the unique anomaly detection reporting, analysts can see these reports in seconds as opposed to the content search in Microsoft or other platforms that can take hours.
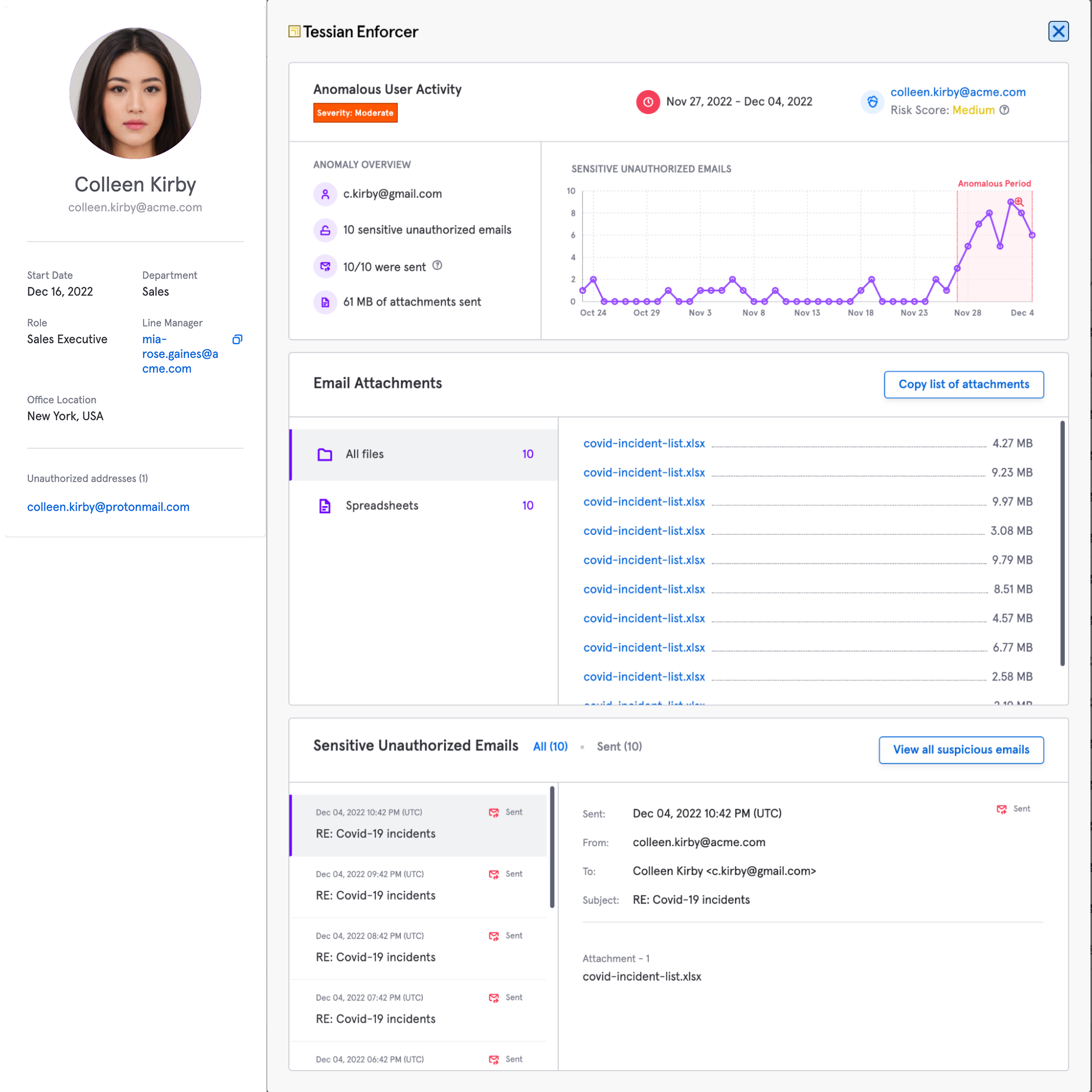
Within the Risk Hub, Tessian automatically identifies the personal email addresses associated with all employees in an organization. This is useful in determining the risk level of a potential breach. HIPAA allows an organization to conduct a risk assessment to “demonstrate a low probability that the protected health information has been compromised by the impermissible use or disclosure.” see this link for details.
For example, if an employee emails ePHI to their personal email account for printing at home or to conduct work from a home device, an organization can (a) identify that this was a personal email address for an employee and (b) require the employee to delete this data from the personal device. This example is a risk mitigation practice used by a current Tessian healthcare customer.
Here’s how Tessian can automatically detect and monitor of data sent to personal email addresses
Easily monitor and respond to anomalous user activity, with full visibility of actions taken by the user.
Want to find out more about how Tessian can help protect your organization? Find out more here
Matt Smith
Chief Strategy Officer