Looking back at the last 12 months, Tessian’s Human Layer Security platform has scanned nearly 5 billion emails, identified over half a million malicious emails, stopped close to 30,000 account takeover attempts, and prevented over 100,000 data breaches due to a misdirected email…
At the same time, we rolled out a number of important product updates to help keep our customers safe. Here are the most important product updates to Tessian’s Human Layer Security platform from 2021.
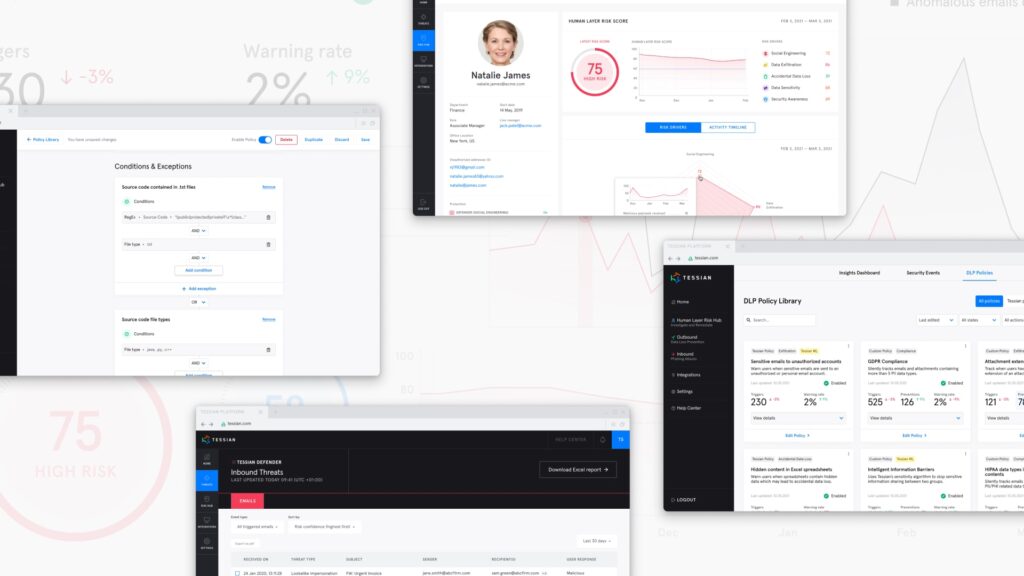
We built world’s first Intelligent Data Loss Prevention Engine
We believe that the next generation of Data Loss Prevention is fundamentally about shifting away from entirely rule-based techniques towards a dynamic, behavioral approach. That’s why we built Guardian and Enforcer, to automatically prevent both accidental data loss and sensitive data exfiltration to unauthorized accounts.
But we have also seen that, when combined with dynamic behavioral analysis, custom DLP policies, play an important role in an organization’s data security strategy.
With the launch of Tessian Architect in October 2021, enterprises can now deploy powerful, intelligent DLP policies. Architect is a perfect complement to Tessian Guardian and Enforcer and provides the market’s best-in-class Email DLP platform:
- Architect was built together with leading security teams – it’s intuitive, quick-to-learn and comes with a library of prebuilt policies
- Architect has built-in machine learning capabilities and features a powerful logic engine to address even the most complex DLP use cases
- Architect is designed to educate users about data security practices in-the-moment and guide people towards better behavior
Want to learn more about Tessian Architect? Read more about it here.
“We are seriously impressed by the rule building capability of the product which has made it incredibly easy to construct policies in minutes or less. I have written a book about how to build a more optimized DLP system previously, and the rule construction engine in Architect is exactly how I would envisage the setup.”
Alex Richards
Head of Insider Threat Program, Investec
Tessian Architect displaying an educational alert to an end-user, that was triggered because of a custom policy
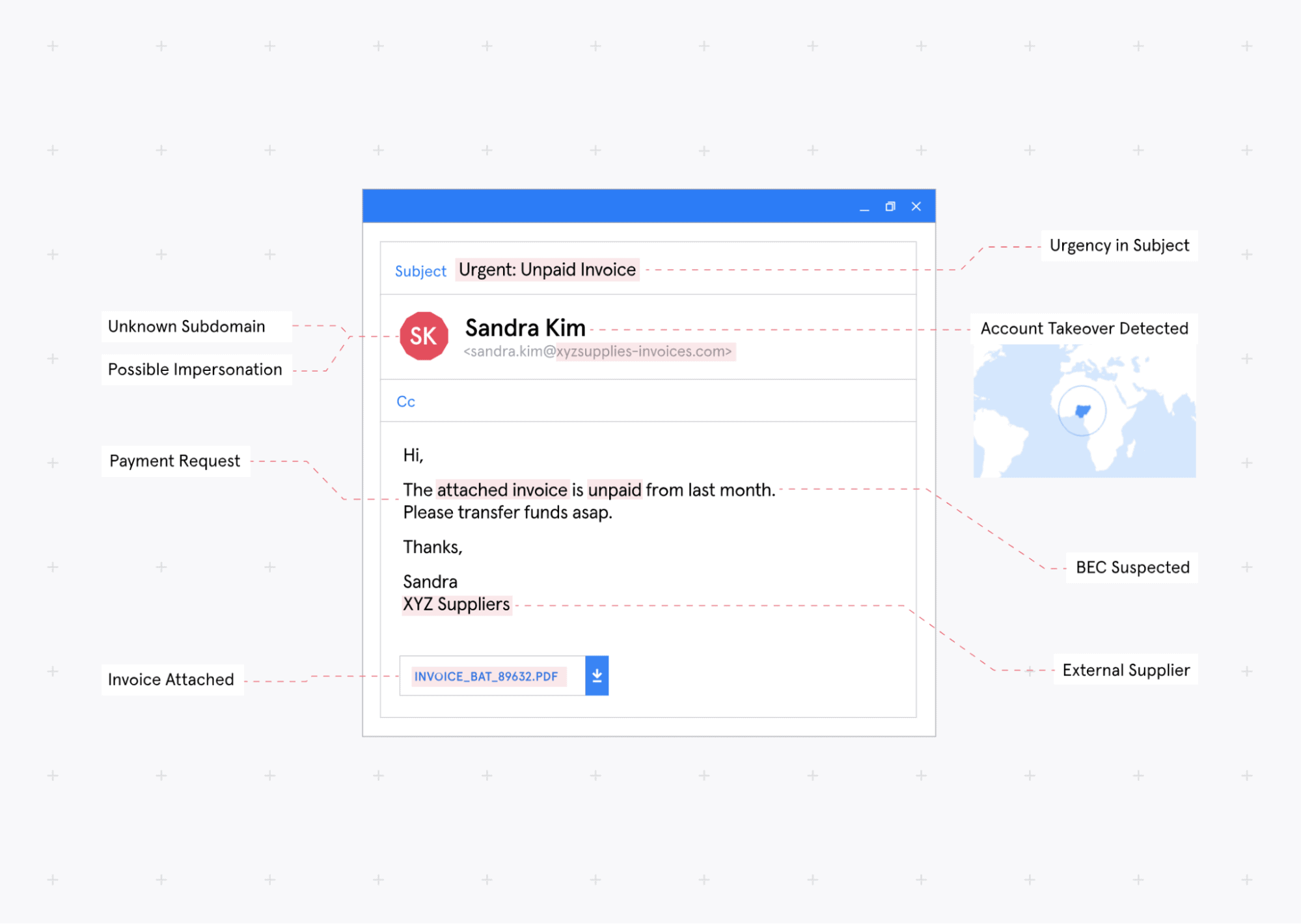
We now protect customers from compromised external counterparties
This year, we saw a record number of bad actors compromising email accounts of trusted external senders (suppliers, customers, and other third-parties) to breach a target company. These attacks are canned external Account Takeovers (ATO), and they’re one of the main pathways to Business Email Compromise (BEC).
Because these malicious emails don’t just appear to have come from a trusted vendor or supplier’s legitimate email address, but actually do come from it, external ATOs are incredibly hard to spot, meaning organizations are exceptionally vulnerable to them.
Tessian Defender now automatically detects and stops external Account Takeover attacks.
By using machine learning to understand a sender’s normal email sending patterns (like where they usually send from, what they talk about, what services they use, and more), it can identify suspicious deviations from the norm and detect malicious emails.
When this happens, Defender can either block these attacks, or show educational alerts to end-users, helping them identify and self-triage attacks.
Learn more about External Account Takeover protection here.
“We’ve had things like account takeover (ATO) on our risk register for two years now, and we recognized that rule-based solutions could only take us so far. But until now, there just wasn’t anything out there that really ticked all the boxes we needed.”
IT Director, Asset Management Firm
Some signals that Tessian Defender learns from to detect ATO attacks
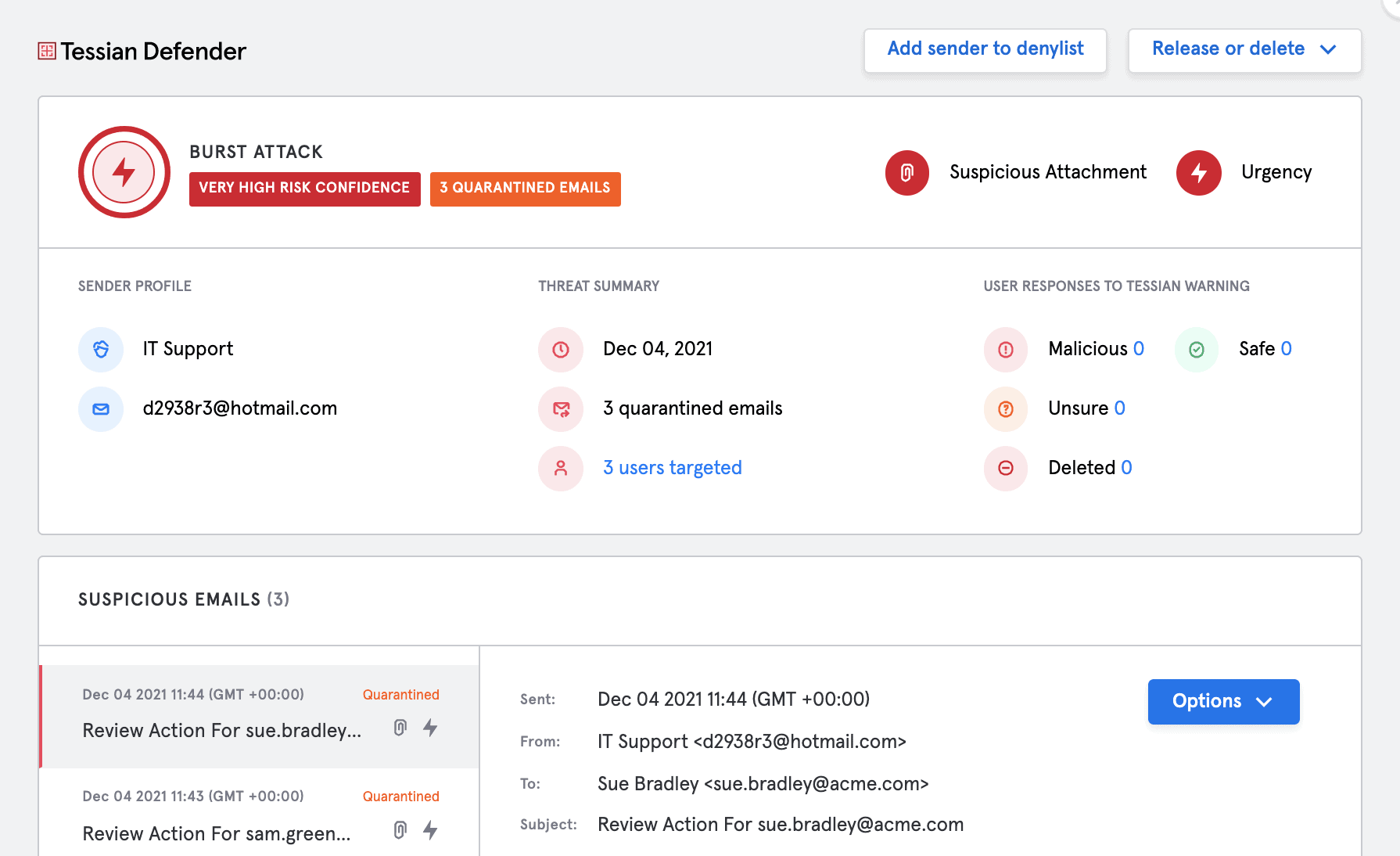
We now stop more threats, with better accuracy, with less admin overhead
In-the-moment warnings are one of the features that set Tessian apart from the competition. When Tessian Defender detects a potentially malicious email, it warns users with a pop-up, explaining exactly why the email was flagged.
But, we know that sometimes, it’s better to automatically block phishing emails.
Tessian Defender now automatically blocks attacks, before they reach a user’s mailbox. This gives security teams an additional layer of email security, preventing end-users from receiving emails that are highly likely to be phishing attacks.
Defender can also adapt the response it takes to remediate a threat. If our machine learning is close to certain an email is malicious, it can quarantine it. Otherwise, it can deliver it to the end-user with an educational warning. This adaptive approach is so powerful because it strikes a balance between disrupting end-users and protecting them.
Finally, this year, Tessian Defender’s detection algorithm made some big strides. In particular, improvements in our risk confidence model allowed us to reduce false positives by significantly providing a better experience to end-users and security teams.
Within the Tessian platform, security teams can review specific incidents, including burst attacks
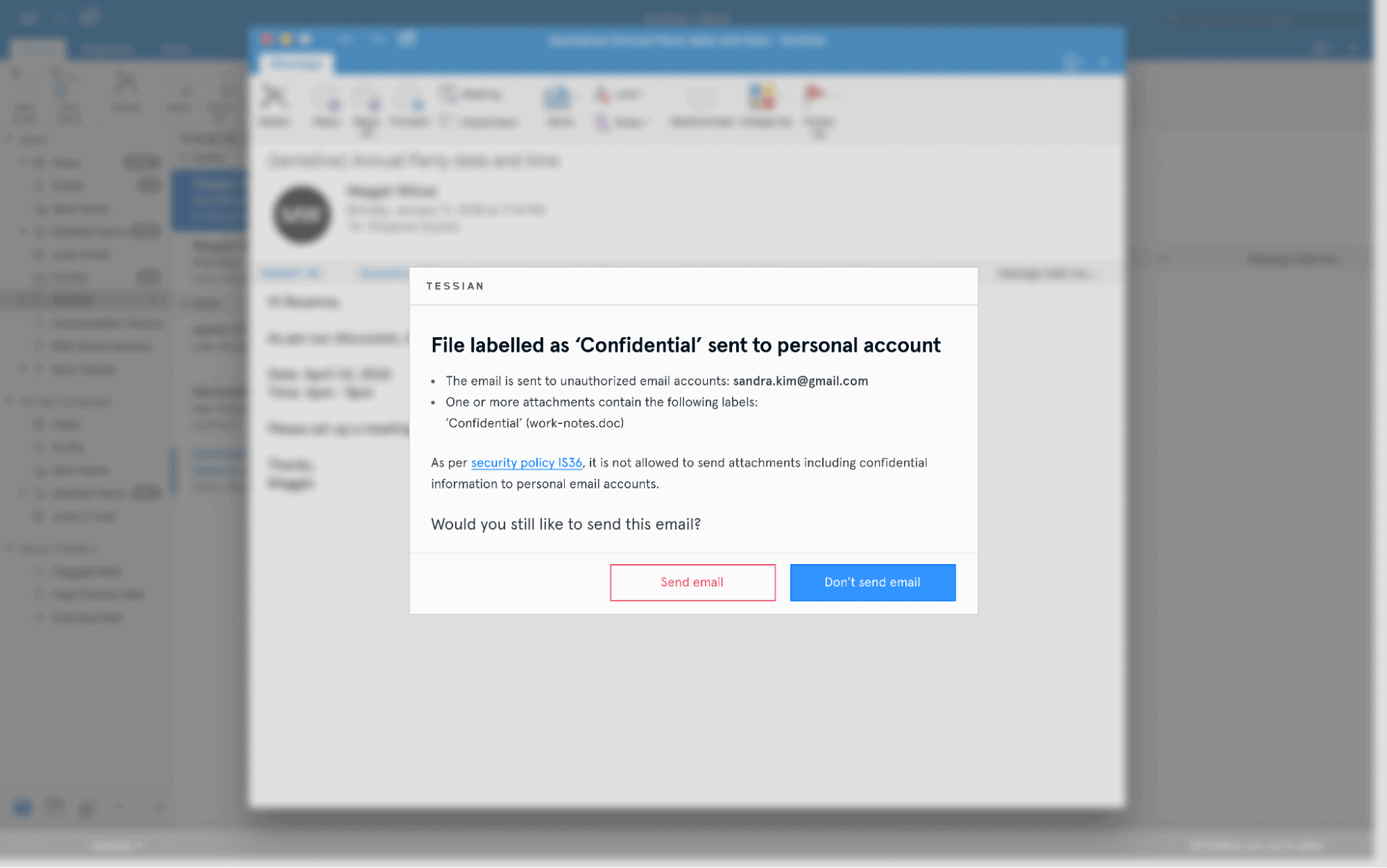
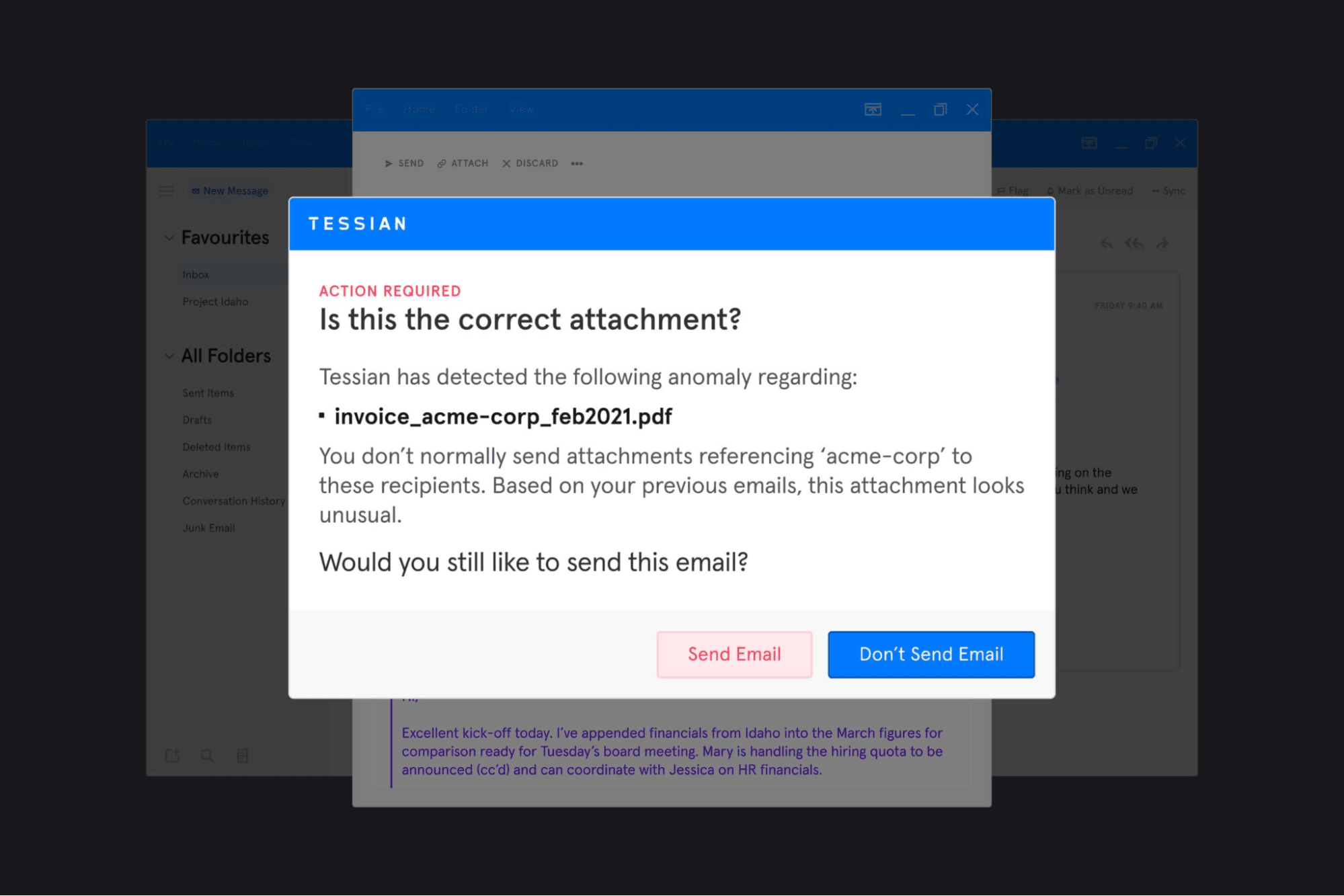
We now stop employees from accidentally sending the wrong attachment
Accidental data loss is the number one security incident reported to the Information Commissioner’s Office, and sending an incorrect attachment is part of that problem. In fact, 1 in 5 external emails contain an attachment, and research shows nearly half (48%) of employees have attached the wrong file to an email.
- 42% of documents sent in error contained company research and data
- 39% contained security information like passwords and passcodes
- 38% contained financial information and client information.
- 36% of mistakenly attached documents contained employee data
Thanks to an upgrade to Tessian Guardian, organizations can now prevent employees from accidentally sending the wrong attachment in an email.
The upgrade uses historical learning, deep content inspection, natural language processing (NPL), and heuristics to detect counterparty anomalies, name anomalies, context anomalies, and file type anomalies to understand whether an employee is attaching the correct file or not. If a misattached file is detected, the sender is immediately alerted to the error before the email is sent. This is completely automated, requiring no overhead from IT teams.
Best of all, the warnings are helpful, and flag rates are extremely low. This means employees can do their jobs without security getting in the way.
Learn more about misattached file protection here.
“Tessian uses very advanced technology. The old-fashioned way is to use rule-based tools. You have a human being attempting to think of every angle and then setting up rules to combat them. With Tessian, this is all done using advanced technology, machine learning, which is far more flexible, targeted, and adapted. It allows us to avoid a huge administrative burden and mistakes being made.”
Adam Jeffries
CIO, JTC
A warning that Tessian Guardian could show when detecting a misattached file
We can now quantify and measure human layer risk
Comprehensive visibility into employee risk is one of the biggest challenges security leaders face. With the Tessian Human Layer Risk Hub, our customers can now deeply understand their organization’s security posture, with granular visibility into employee risk, and insights into their risk levels and drivers.
How does it work? Tessian creates risk profiles for each employee, modelled from a range of signals like email usage patterns, indirect risk indicators, and employee security decisions (both historic and in real-time). Because of this unique data modelling, Tessian can gauge employees’ risk level, including whether or not they’re careful, careless, frequently attacked, and more.
This offers organizations protection, training, and risk analytics all in one platform, providing a clear picture of risk and the tools needed to reduce it.
Learn more about the Human Layer Risk Hub here.
“Tessian is doing the heavy lifting for us now. We’re no longer looking through spreadsheets with hundreds or thousands of events. With the Human Layer Risk Hub, we get incredible visibility within the portal into high-risk users and high-risk events. We can now identify users whose behavior could put us at risk, whether it’s via misdirected emails, unauthorized emails, or spear phishing attacks. This all helps massively with incident response since our security and compliance teams do not have limitless resources.”
Richard Mullins
IT Security Engineer, Penningtons Manches Cooper
We now integrate with KnowBe4, Sumo Logic, Okta, and more…
Tessian is even more powerful when integrated with other security solutions that help address the risk posed by employees. That’s why, in the last 12 months, we’ve announced exciting integrations with Okta, Sumo Logic, and KnowBe4, each with their own unique benefits for joint customers.
With Sumo Logic + Tessian, security and risk team can understand their risk through out-of-the-box monitoring and analytics capabilities.
“Sumo Logic is excited to announce the General Availability of Tessian's Human Layer Security dashboard. By ingesting Tessian data, joint customers will be able to monitor and mitigate email based security threats as well as the people behind them. ”
John Coyle
VP of Business and Corporate Development, Sumo Logic
With Okta + Tessian, security and risk management teams geet granular visibility into their organization’s riskiest and most at-risk employees and consequently enable them to deploy policies that can help protect particular groups of users from threats like advanced spear phishing and account compromise and prevent accidental data leaks.
“By integrating our solutions, customers will be able to automatically detect their most high risk employees and put in place stronger security measures and policies to keep them safe, without disruption the normal flow of business.”
Austin Arsensberg
Director, Okta Ventures
And with KnowBe4 + Tessian, security and risk management teams get more visibility into phishing risk than ever before.
“Security and IT teams invest a lot of time and resources training their employees - so they want to understand that these training sessions are actually reducing risk within their organizations. Tessian provides hugely valuable data on email behaviors and the state of a company's human layer risk. Together, we can empower security teams to deploy taiolors training - at scale - in order to reduce the risks associated with phishing and improve people's security behaviors. ”
Stu Sjouwerman
CEO, KnowBe4
Want to help us solve more challenges across use cases? Come build with us.
Harry Wetherald
Group Product Manager