Legacy Data Loss Prevention is quickly becoming an antiquated technology that isn’t evolving to meet the needs of enterprise organizations. Most of these solutions rely heavily on rules, create massive overhead for admin teams, and typically require constant manual fine-tuning to manage the myriad of false alerts.
And even with legacy DLP in place, data breaches continue to happen.
Perhaps the most important aspect to consider with legacy data loss prevention, is that static policies are often not as effective as we need them to be. They tend to be severely limited, and often restrict employees far more than what is necessary. These cumbersome solutions are based on known signatures, which don’t account for unknown anomalies, or consider the friction and latency they produce when implemented.
Here at Tessian, we believe that the next generation of Data Loss Prevention is fundamentally about shifting away from a static, rules-based approach, to a dynamic, behavioral approach that can address the specific context of each potential incident.
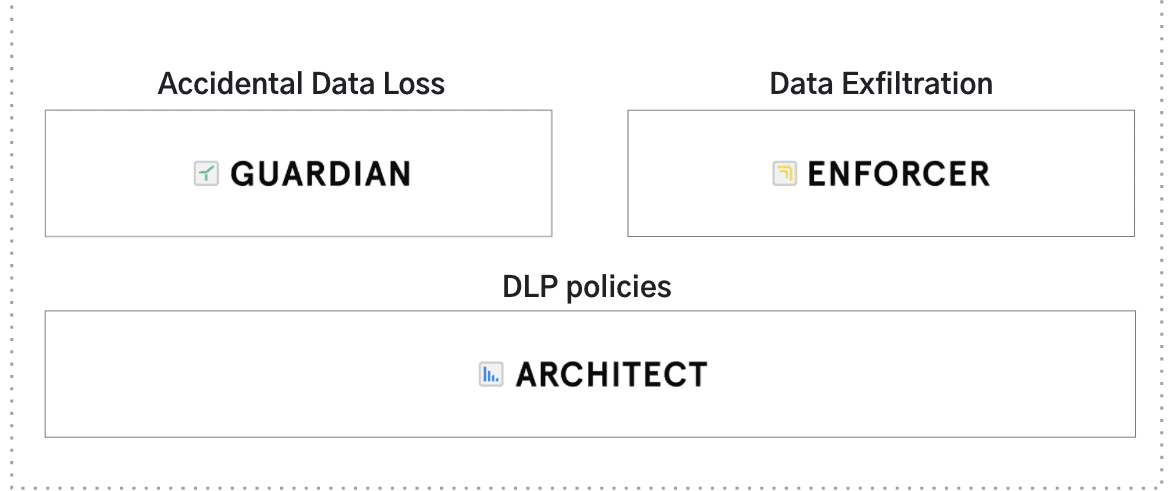
We have seen first hand how Data Loss Prevention has become too reliant on static rules and places far too much burden on admin to identify, investigate and remediate sensitive data loss. That’s why we built Guardian and Enforcer, to automatically prevent both accidental data loss and sensitive data exfiltration to unauthorized accounts.
However, we have also seen that custom policies, when combined with dynamic behavioral analysis, plays an important role for an organization’s DLP strategy. When policies are used, they should be intelligent where applicable, be easy to configure and manage, and leverage end-user remediation to reduce administrative burden.
Now with Tessian Architect, enterprises can now deploy powerful intelligent DLP policies. Architect completes Tessian Guardian and Enforcer and provides the market’s best-in-class Email DLP platform.
“Traditional DLP has a low return on investment, and it’s expensive to run. It does stop some malicious emails, but it’s very low volume. On the other end of the spectrum, you have Tessian. For example, it’s stopping data loss every day. Now, misdirected emails aren’t a malicious activity, but the consequences are no less severe and the ROI is clear and easy to calculate. All we have to do is look at the number of employees who were going to do something - like send an email to the wrong person, move sensitive data outside of the company - but didn’t because of the solution.”
Rob Hyde
Chief Information Security Officer at Schroders
Here Are Some of the Top Use Cases Architect Can Address
- Detect hidden content in Excel spreadsheets to prevent accidental disclosure of sensitive data
- Use regular expressions to detect specific data types and identify high severity breaches by defining unique match thresholds (e.g. more than 5 unique records)
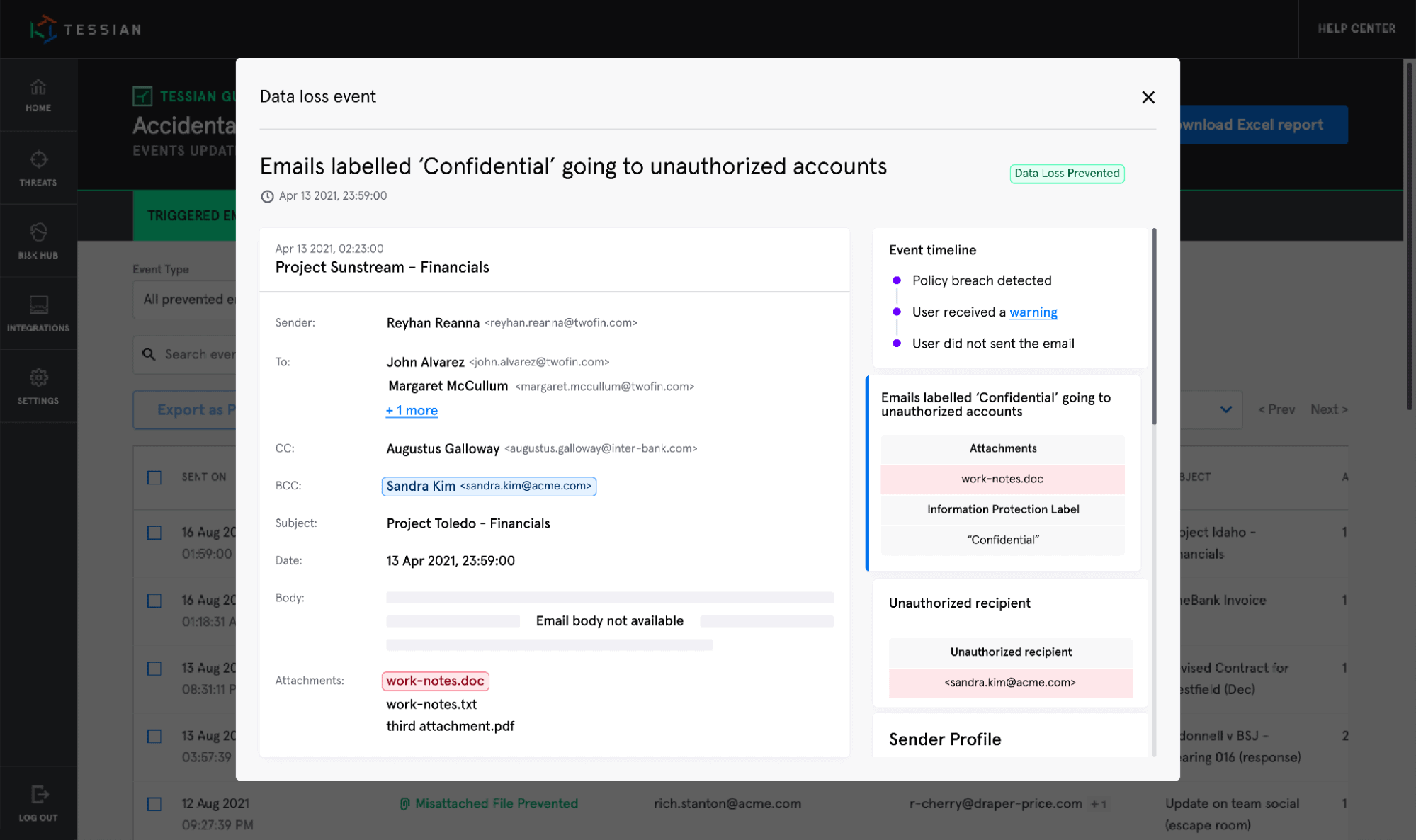
- Warn on sensitive attachments without Microsoft Information Protection labels, and detect when attachments labelled as ‘Confidential’ are sent to unauthorized accounts
- Educate and remind users when a sensitive attachment has been labelled as ‘Public’ or ‘General’
- Set up intelligent information barriers to prevent sensitive data sharing between teams
- Detect PII/PHI shared externally in bulk
- Detect financial data such as credit card numbers and bank account numbers
- Detect unencrypted personal health information shared externally
- Block attachments containing high volumes of PII from being sent to unauthorized accounts
- Use Architect to migrate and simplify DLP policies from legacy tools and consolidate related policies using powerful logic blocks.
- Use Architect to enhance rule-based legacy DLP policies with machine learning such as Tessian’s sensitivity algorithm and minimise the number of false positives
How Does Tessian Architect Work?
Let’s take a deeper look at the product.
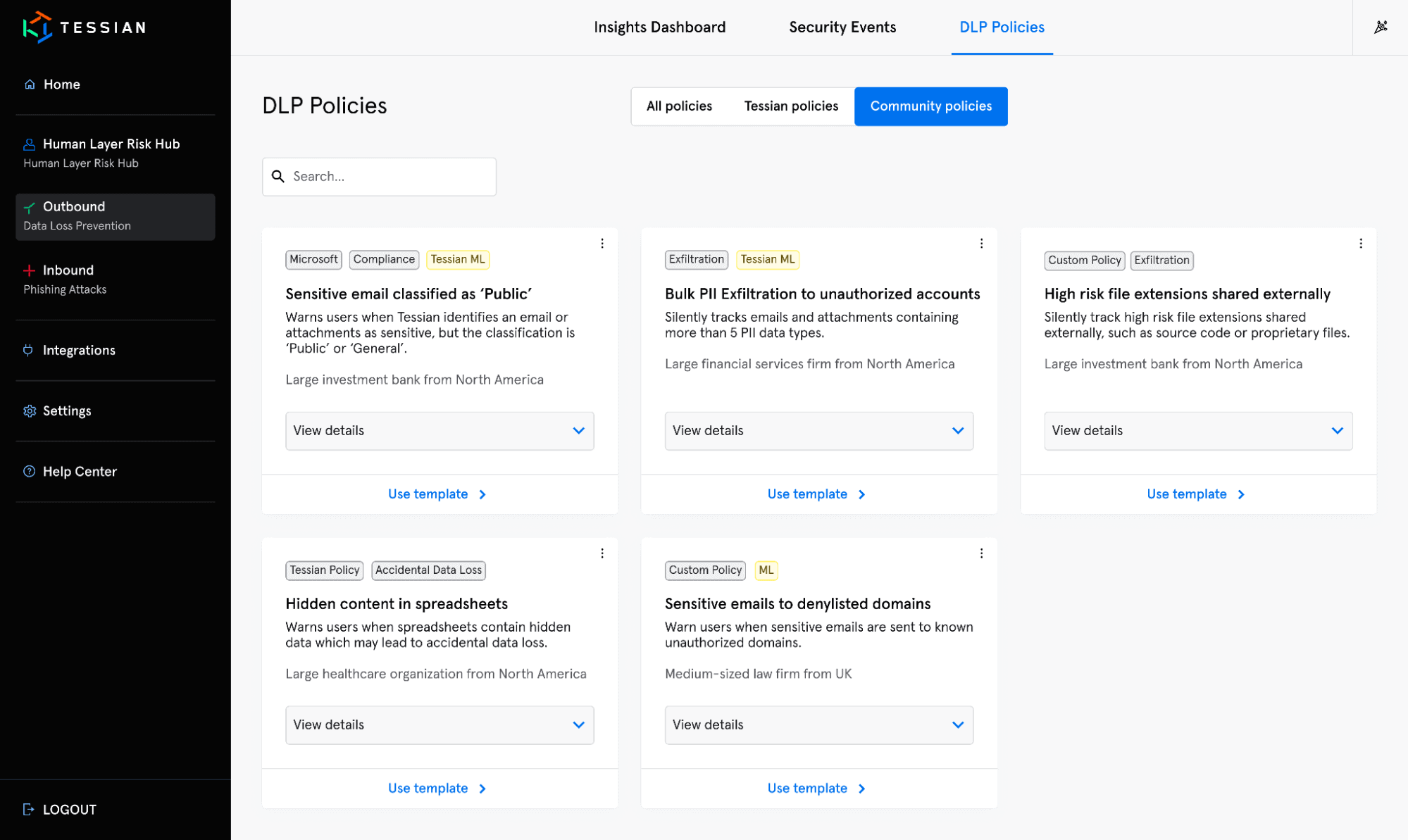
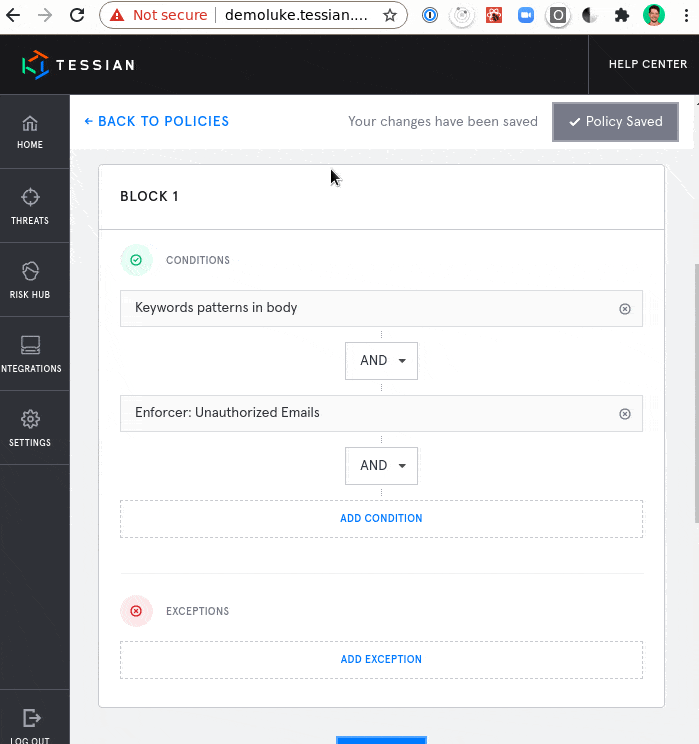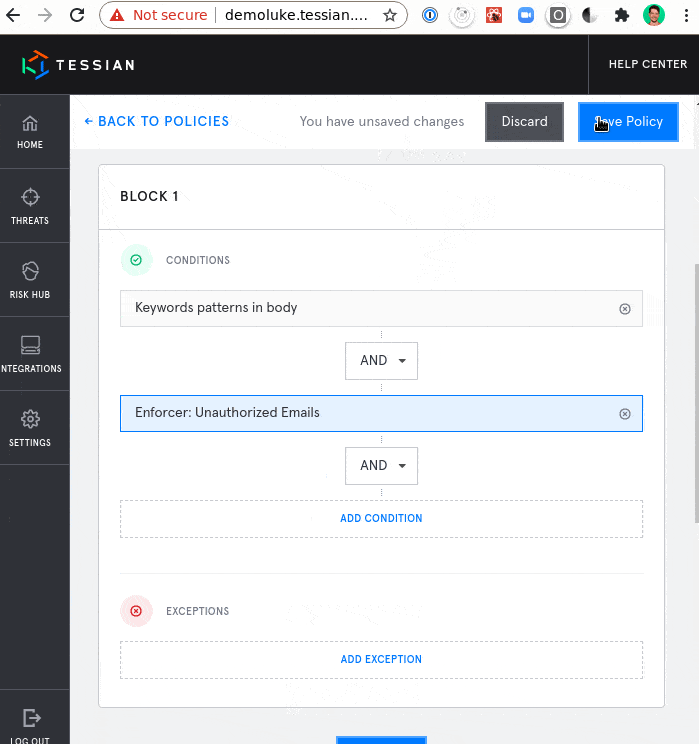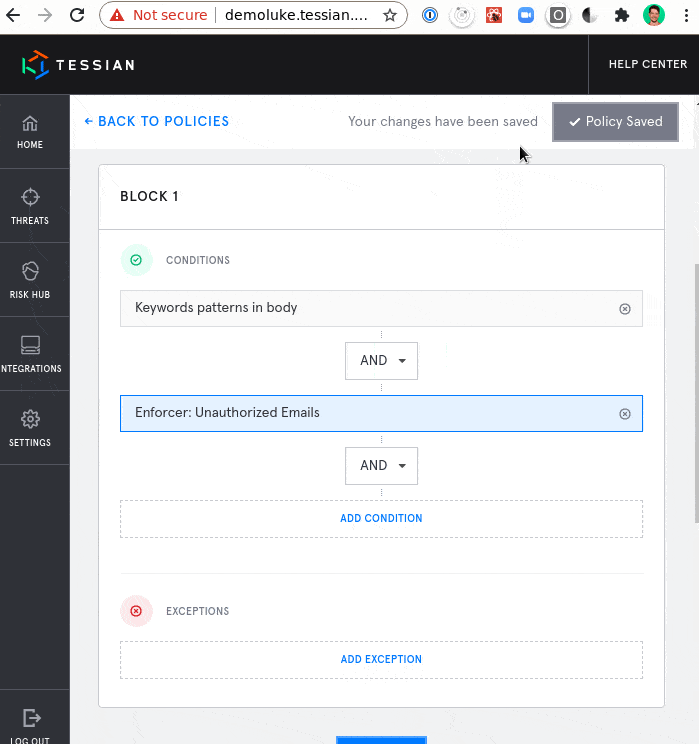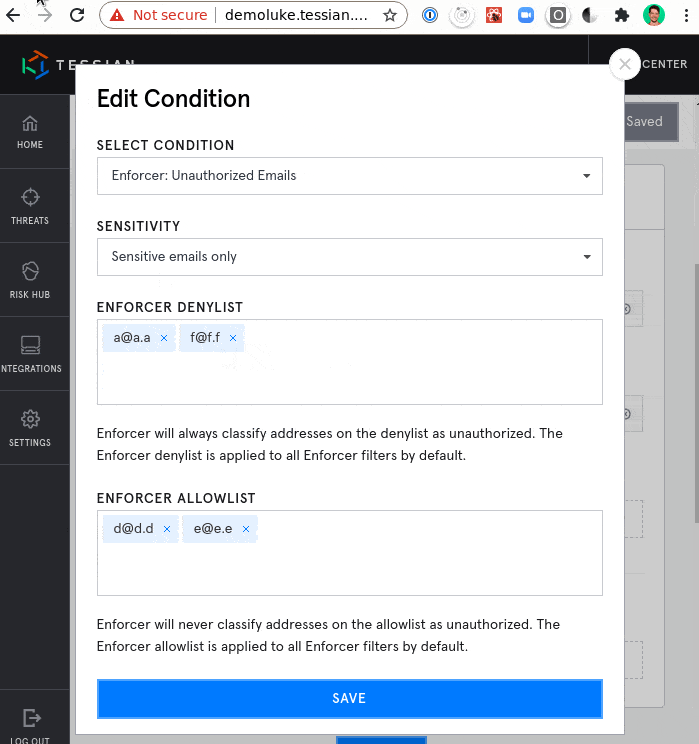
Create Custom Policies or Deploy Pre-built Tessian DLP Policies
These new DLP capabilities allow administrators to quickly and easily build DLP policies to meet basic and advanced data loss requirements, including establishing and maintaining regulatory compliance.
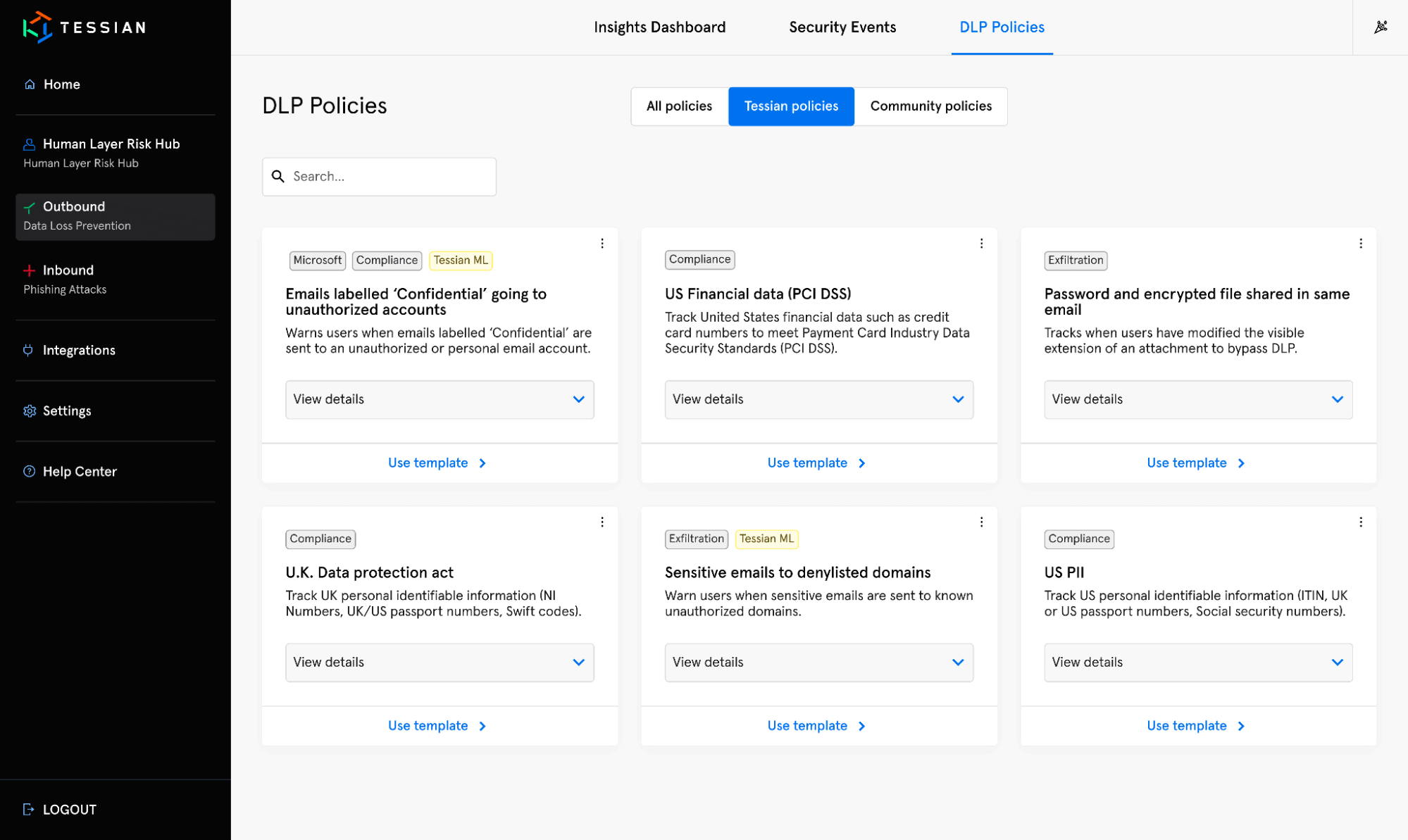
Choose from pre-built policies that solve for your specific use cases or industry requirements, or build your own policies to meet your unique organization’s needs. Use community policies to adopt best practices sources from industry leaders in the Tessian Network. Policies may contain any number of DLP conditions and can be simple or complex, rely entirely on machine learning, basic rules, or both. Testing, tuning and rolling out policies can be done within hours, not days, weeks, or months. Test a policy change in production in as little as one minute.
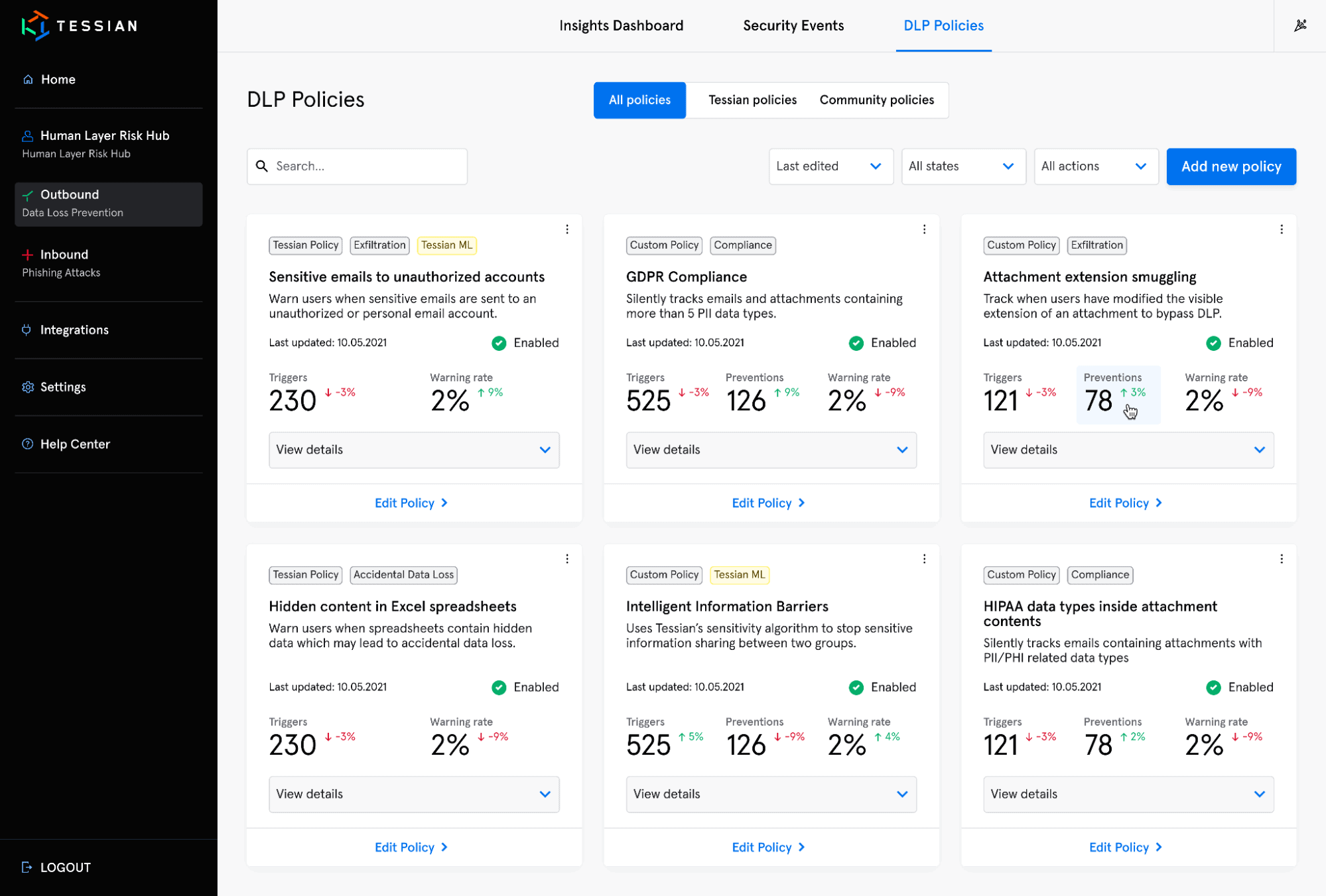
This view shows all policies available in the Architect library
This view shows pre-built, Tessian policies available in the Architect library
This view shows community policies available in the Tessian Architect library
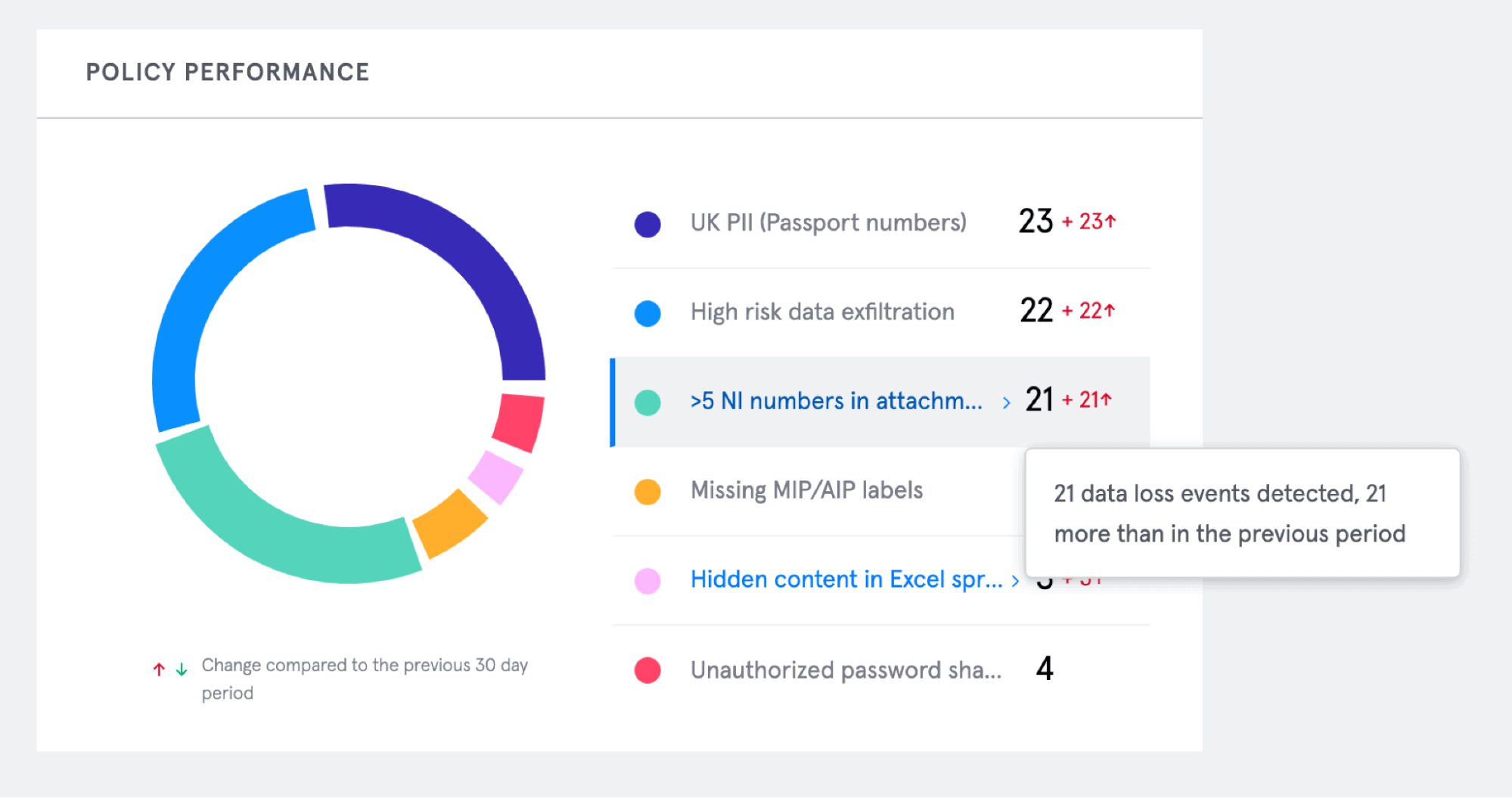
Analyze Email DLP Policy Performance Across Your Security Environment
Quickly view real-time policy performance and determine what types of data loss are most prevalent in your organization. Insights are provided such as the number of data loss events detected, as well as information about those data loss incidents within specified time periods.
The Tessian portal offers makes it easy to track incidents prevented by type, and over specified time periods
Policy Editor Provides Maximum Protection for Sensitive Data
Build advanced, nested-logic policies and consolidate multiple policies that are related to similar topics. This is needed for advanced use cases to allow companies to consolidate and simplify policies as they’re migrating legacy DLP policies.
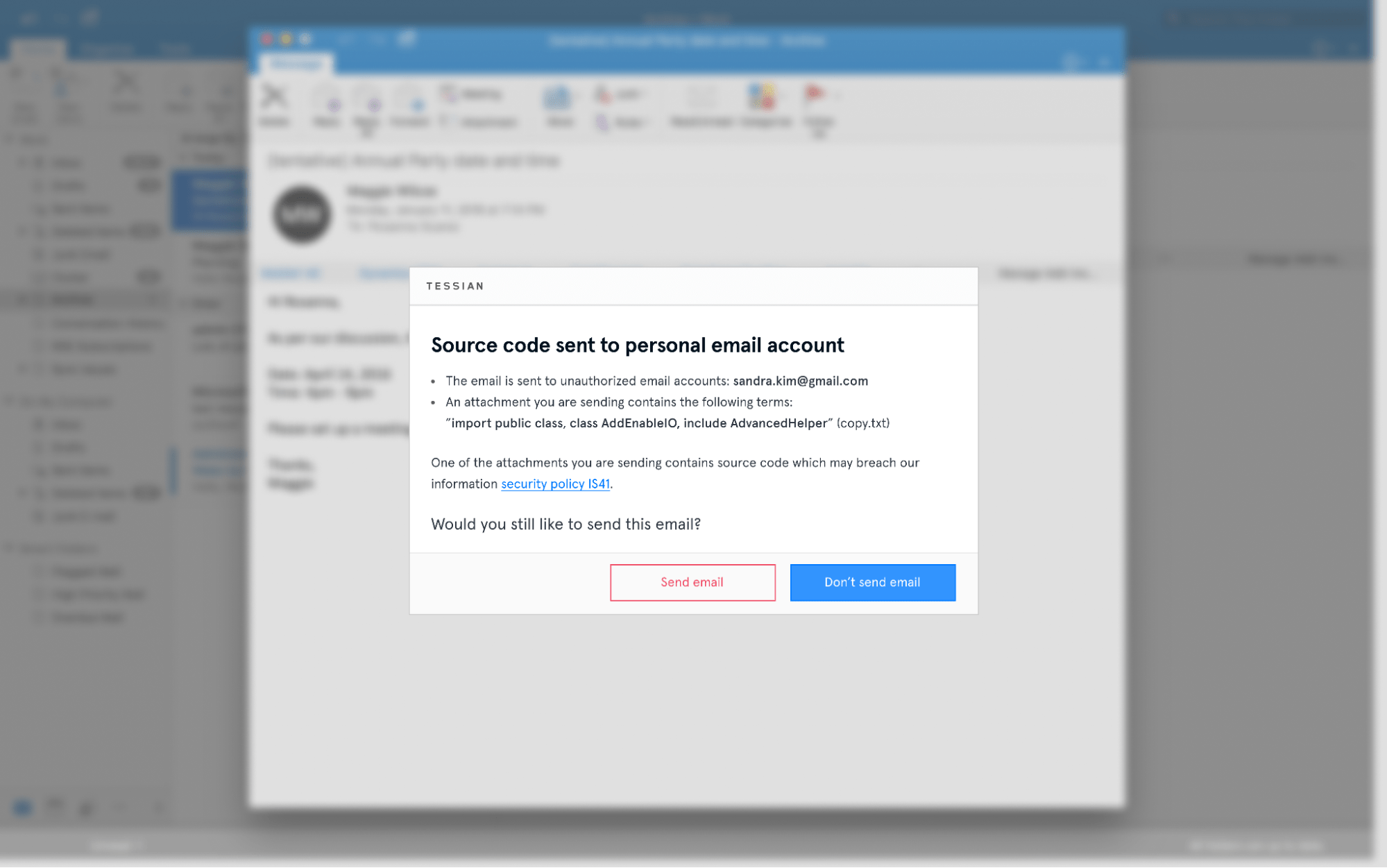
Integrate with Any Data Classification System, including Microsoft Information Protection (MIP)
Combine the machine learning and behavioral approach of Tessian with Microsoft Information Protection and data classification to further protect against sensitive data loss. Tessian detects sensitive attachments without Microsoft Information Protection labels. In addition, Tessian will also detect when data labeled “confidential” is about to be sent to unauthorized parties.
This is an admin's view of the Tessian portal, where they can see specific details related to the prevented event
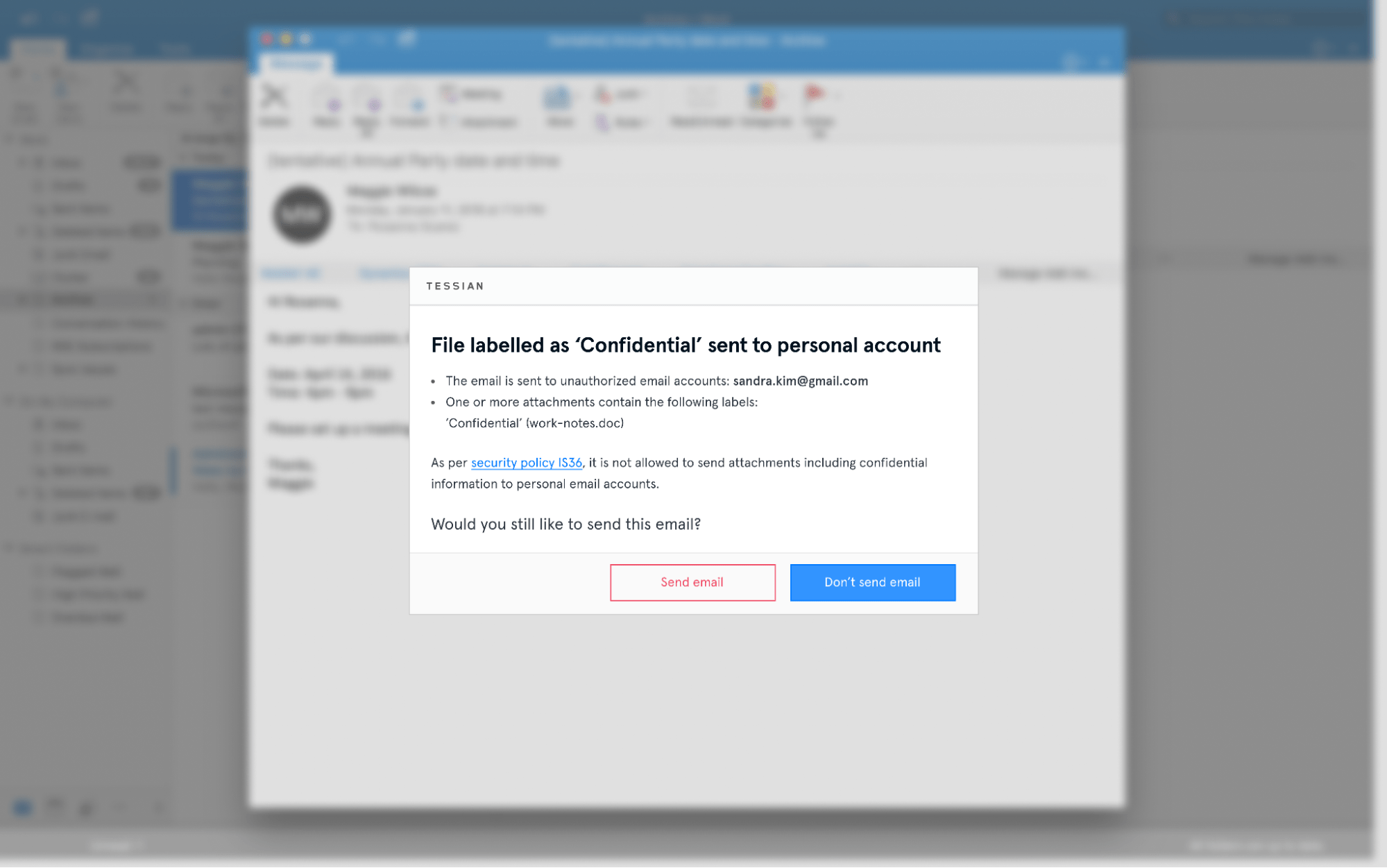
This is an employees' view of Tessian's warning message, which outlines exactly why the email was flagged
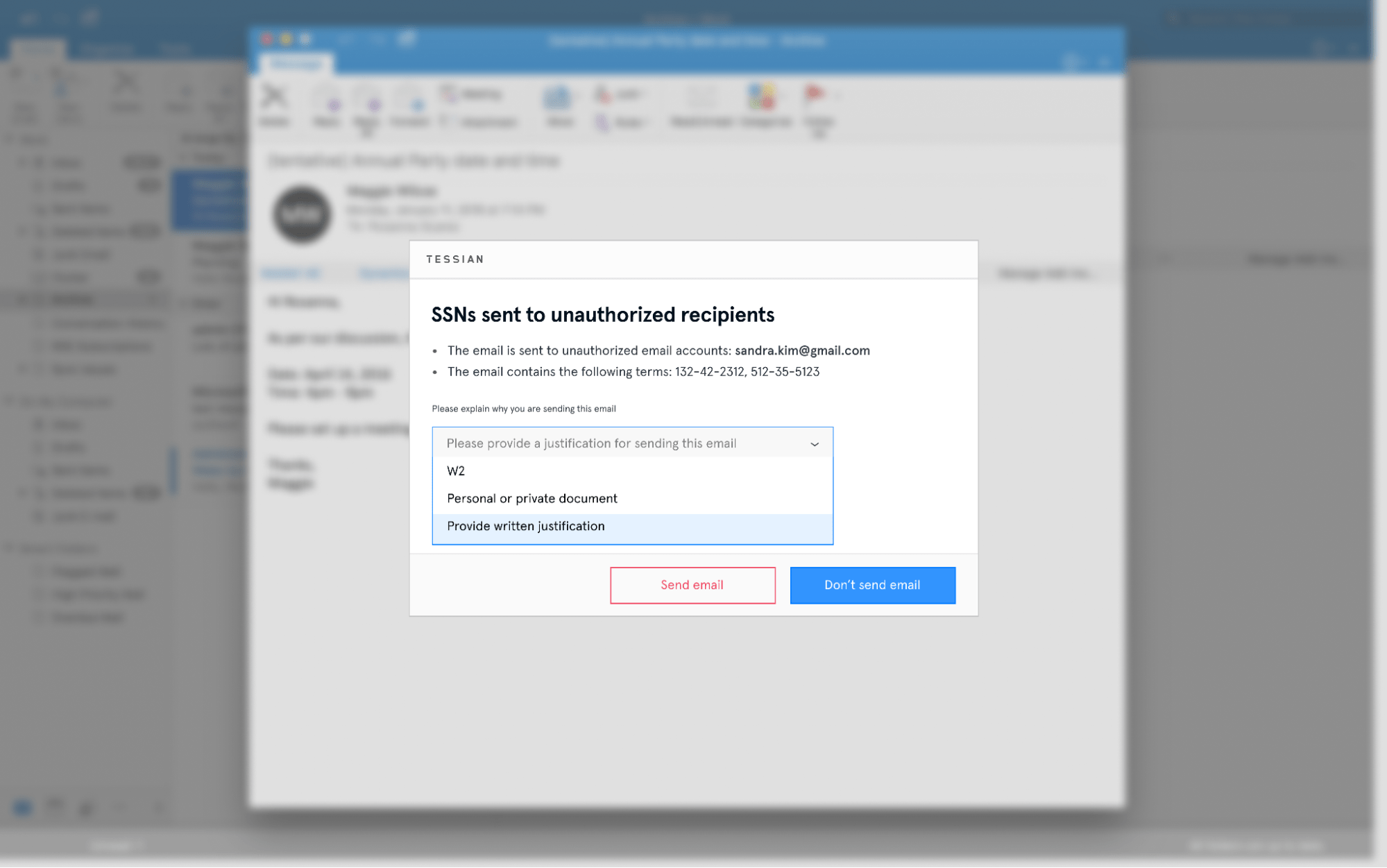
In-the-Moment Educational Warnings to Stop Accidental Data Loss and Sensitive Data Exfiltration in Real-Time
Tessian warnings act as in-the-moment training for employees, continuously educating them about exfiltration, reinforcing your policies, and nudging them toward safe email behavior. Automatically build individualized policies at scale to reduce high-risk email use and track trends in unsafe activity over time.
With this configuration, employees have to select a reason for needing to send sensitive information.
This is an employees' view of Tessian's warning message, which outlines exactly why the email was flagged
Benefits of Tessian Architect
1. Automatically Stop Sensitive Data Exfiltration to Unauthorized Parties: Whether it’s an employee negligently sending emails to unauthorized or personal accounts, or individuals maliciously stealing company intellectual property, Tessian automatically stops sensitive data from being sent to any unauthorized recipients.
2. Automated and Pre-built DLP Policies: Take the guesswork out of building DLP policies with Tessian’s policy library, with the flexibility to build your own to adhere to your organization’s unique data protection requirements.
3. Reduce Admin Burden by Order of Magnitude: Reduce admin overhead with end-user remediation and powerful policy logic that simplifies DLP configurations. Cut through noisy DLP alerts and gain new visibility of high severity incidents and anomalous activity.
4. Ensure Regulatory Compliance: Protect against non-compliant activity and prevent users from sharing confidential data with non-business, personal addresses /unauthorized recipients; track and block compliance breaches in real-time.
5. Clear ROI: Many solutions simply report on data loss events; they don’t actually reduce sensitive data exfiltration and risk to the organization. Tessian is different. Security leaders can easily build and deploy DLP policies and show how those policies are proactively helping to improve the organization’s security posture. The benefit? You’ll become a trusted partner across your organization.
Learn more about Data Loss Prevention for the Human Layer
Tessian uses behavioral analysis to address the problem of accidental or intentional data loss by applying human understanding to data exfiltration incidents.
- Guardian: Automatically prevents accidental data loss via misdirected emails and misattached files. No rules required.
- Enforcer: Automatically prevents data exfiltration and other non-compliant activities on email
- Human Layer Security Intelligence: Comprehensive visibility into employee risks, threat insights, and tools that enable rapid threat investigation and proactive risk mitigation
- Human Layer Risk Hub: Enables security and risk management teams to deeply understand their organization’s email security posture, including individual user risk levels and drivers
Learn more about Tessian
Interested in learning more about Tessian Architect? Current Tessian customers can get in touch with their Customer Success Manager.
Not yet a Tessian customer? Learn more about Tessian Architect, or book a demo now.
Ed Bishop
co-founder and Chief Technology Officer