Detecting and preventing Insider Threats isn’t easy. Why? Because unlike external bad actors, Insiders – whether a disgruntled employee, a distracted freelancer, or a rogue business partner – have legitimate access to systems and data. That means they’re in an ideal position to exfiltrate data.
So, how do you spot one?
To start, you have to know what an Insider threat is and understand the different methods and motives behind these data exfiltration attempts.
What is an Insider Threat?
We’ve covered this in detail in this article: What is an Insider Threat? Insider Threat Definition, Examples, and Solutions.
But, to summarize:
Insider Threats can be malicious or the result of negligence.
- Malicious Insiders knowingly and intentionally steal data and generally do so for one of three reasons: financial incentives, a competitive edge, or because they’re dissatisfied at work.
- Negligent Insiders are just your average employees who have made a mistake. For example, they could send an email to the wrong person, misconfigure a system, fall for a phishing email, or lose their work device.
How often do incidents involving Insider Threats happen? More often than you might think. In fact, there’s been a 47% increase in incidents over the last two years. We discuss seven recent examples in this blog: Insider Threats: Types and Real-World Examples.
While every incident is different, there are some tell-tale signs of an Insider Threat.
Insider Threat indicators: Malicious Insiders
Malicious Insiders may act suspiciously well before they actually exfiltrate any data. For example:
1. Declining performance or other signs of dissatisfaction
As we’ve said, one reason why Insiders exfiltrate data is that they’re dissatisfied at work. It could be because of a poor performance appraisal, because they were denied a promotion or raise, or because of a disagreement with a co-worker or manager.
Whatever the reason, 1 in 10 Insider Threats is motivated by a grudge.
Look out for a consistent or sudden decline in performance or attitude and for employees who become angry or combative. Employees who are actively looking for other jobs should also be on your radar. While they could simply be moving on to a new opportunity, they may be inclined to steal data in order to impress or bribe a new or potential employer.
Don’t believe us? 45% of employees download, save, send, or otherwise exfiltrate work-related documents before leaving a job or after being dismissed. This number nearly doubles in highly competitive industries like Financial Services and Business, Consulting, & Management.
[infogram id=”financial-services-bad-leavers-1h7j4d8g9wq96nr?live”]
2. Unusual working hours
While passion and enthusiasm are generally considered positive attributes when talking about an employee, these can occasionally be early signs of bad intent.
For example, if an employee consistently volunteers for extra work, regularly works in the office late, comes in early, or attempts to perform work that’s outside of the scope of their normal duties, they could be trying to gain access to sensitive systems or data.
Then, of course, there are signs of the data exfiltration attempt itself. For example:
3. Large data transfers or downloads
There are a number of ways to exfiltrate data, including email, Cloud Storage, USB sticks. In fact, 23% of insiders exfiltrate data via USBs and 24% exfiltrate data via laptops/tablets. Nevertheless email is the threat vector most IT leaders are concerned about. After all, it only takes one click to transfer dozens of files.
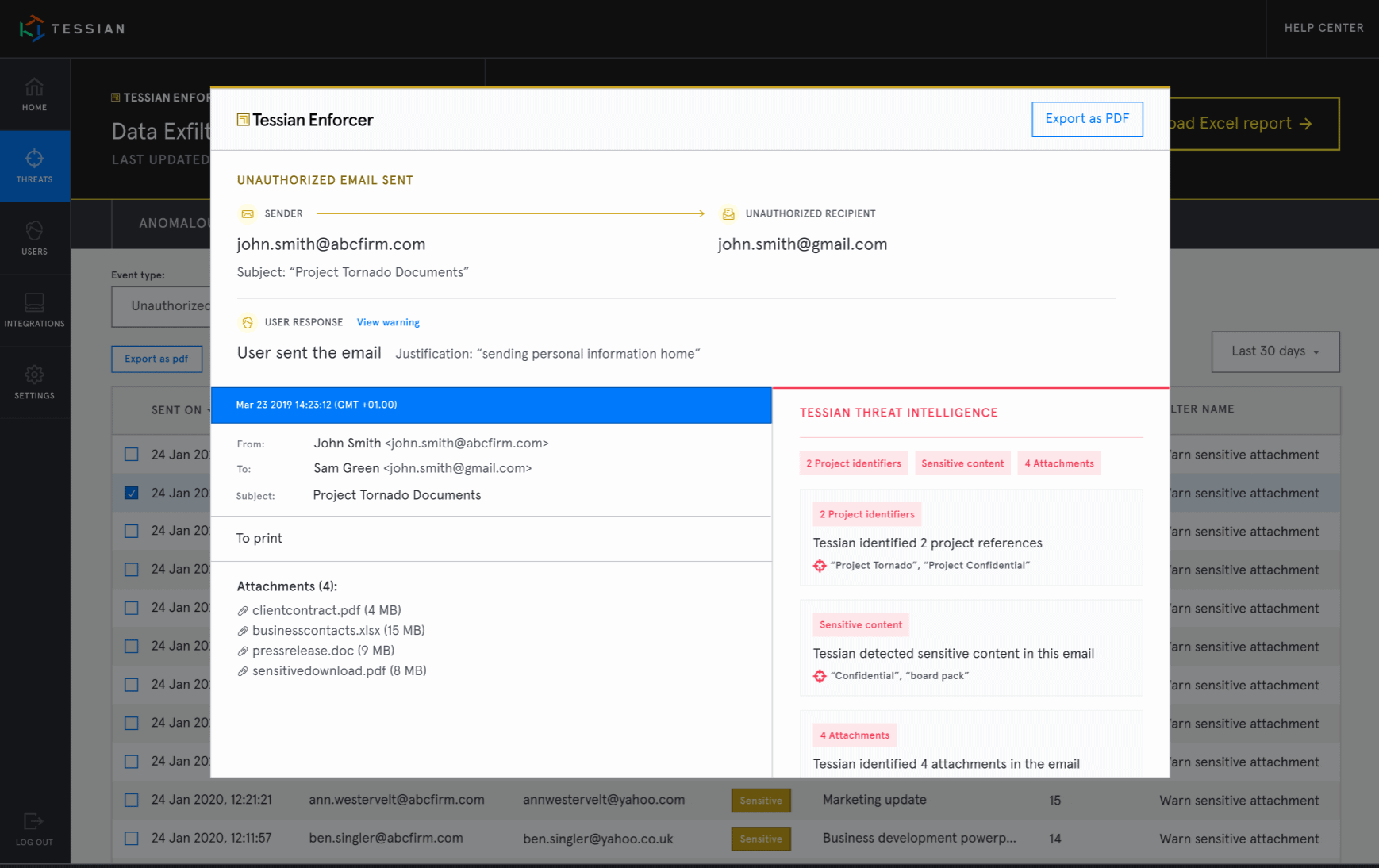
But, monitoring data movement is a challenge. How can you realistically monitor every email sent and received within your organization? With Tessian Human Layer Security Intelligence, it’s easy.
Security, IT, and compliance leaders can get detailed insights around employee behavior in a single click. No manual investigation required.
4. Multiple failed logins (or other abnormal login activity)
Whether it’s an employee trying to access networks or systems they don’t have access to or an employee with legitimate access logging in more frequently than usual, login activity can offer security teams clues about Malicious Insiders.
Certainly the employee could simply be curious and may even be going above and beyond to get their job done, but these behaviors could also be indicative of nefarious intent and should be investigated.
5. Upgraded privileges or sharing access
When someone is promoted or there’s some other shift in the structure of an organization, it makes sense that access to systems and data might change. But, what about when someone’s privileges or access are escalated without a clear reason why?
It could be an administrator granting him or herself more privileged access or it could be a team effort. For example, an administrator could be bribed to upgrade another employee’s access. Both are signs of a Malicious Insider.
Finally, there are signs that the Insider has successfully exfiltrated data or is still successfully exfiltrating data. For example:
6. Unexpected changes in financial circumstances
86% of breaches are financially motivated.
Whether it’s a list of customer email addresses being sold on the Dark Web or trade secrets being sold to a competitor, data is valuable currency. So, if you hear of or notice an employee suddenly and unexpectedly paying off debt or making expensive purchases, you may need to investigate the source of the additional income. It could be a sign that they’re profiting from company or customer data.
7. Consistent (and unusual) overseas travel
Like many of the other indicators on this list, there could be a perfectly good reason why an employee travels overseas. He or she could be going on vacation, visiting friends or family, or may be traveling for work.
But, as we’ve seen, it could also be a sign of corporate or foreign espionage. Case in point: A former engineer at a massive aerospace company frequently traveled to China, claiming he was lecturing. In reality, he was acting as an agent of the People’s Republic of China and was selling trade secrets. This went on for nearly 30 years before he was caught and later convicted.
Insider Threat indicators: Negligent Insiders
While certain behaviors exhibited by Malicious Insiders may set off alarm bells for security teams before exfiltration attempts occur, Negligent Insiders can be harder to preempt.
Nonetheless, there are four key things to look out for.
8. Failure to comply with basic security policies
Whether it’s consistently using weak passwords, refusing to enable 2FA, or frequently downloading tools or software that haven’t been approved by security teams, an employee who disregards security policies could be more likely to accidentally exfiltrate data than one who consistently plays by the book.
That’s why reminding employees of existing policies and procedures is so important.
9. Low engagement in security awareness training
Most employees (and even some security leaders!) would agree that security awareness training is “boring”. And, while that may be the case, training is absolutely essential. It could be training around how to spot a phish (see below) or training around new and existing compliance standards or data privacy laws.
Employees who either don’t attend training at all or who perform poorly on assessments related to that training should be closely monitored and be re-targeted with tailored programs.
You can read more about how to up-level your training and create a positive security culture here.
10. History of falling for phishing attacks
Phishing and other social engineering attacks are designed for one of three reasons: to extract sensitive information or credentials, to install malware onto a network, or to initiate a wire transfer. If the attack is successful – meaning the target (an employee) falls for the scam – there could be serious consequences.
That means any employee who falls for a scam should be reminded of phishing tools and techniques and may need to be more closely monitored.
11. General carelessness or haste
Accidents happen. Whether it’s firing off an email to the wrong person or accidentally leaving a computer unblocked, we all make mistakes. Nonetheless, they aren’t trivial and any employee who consistently makes mistakes will need to be reminded of security best practices and may, in some cases, need to be monitored with more stringent policies.
How can you detect and prevent Insider Threats?
When it comes to detecting and preventing Insider Threats, there are a number of solutions, including:
- Training
- Physical and Digital Monitoring
- DLP tools and software
Importantly, all of these have a place in security strategies. Training should be used to reinforce existing policies, especially for those employees who consistently break the rules or make mistakes.
Security teams should be diligent in their physical and digital data monitoring and should always look out for the above warning signs.
And DLP tools like rule-based solutions, endpoint scanning, firewalls, and anti-phishing software do, in some instances, help curb the problem of data loss.
But, as we’ve said, incidents involving Insider Threats are on the rise which means security stacks are missing something. What they’re missing is protection for their people and at Tessian, we call it Human Layer Security.
How does Tessian prevent Insider Threats?
Tessian turns an organization’s email data into its best defense against inbound and outbound email security threats.
Powered by machine learning, our Human Layer Security technology understands human behavior and relationships, enabling it to automatically detect and prevent anomalous and dangerous activity.
- Tessian Enforcer detects and prevents data exfiltration attempts
- Tessian Guardian detects and prevents misdirected emails
- Tessian Defender detects and prevents spear phishing attacks
Importantly, Tessian’s technology automatically updates its understanding of human behavior and evolving relationships through continuous analysis and learning of the organization’s email network.
Oh, and it works silently in the background, meaning employees can do their jobs without security getting in the way.
Interested in learning more about how Tessian can help prevent Insider Threats in your organization? You can read some of our customer stories here or book a demo.