Attention Security, Compliance. and IT leaders: You can now continuously and proactively downtrend Human Layer risks in your organization with zero manual investigation.
How? With Tessian Human Layer Security Intelligence.
Tessian Cloud Email Security intelligently prevents advanced email threats and protects against data loss, to strengthen email security and build smarter security cultures in modern enterprises.
How? With Tessian Human Layer Security Intelligence.
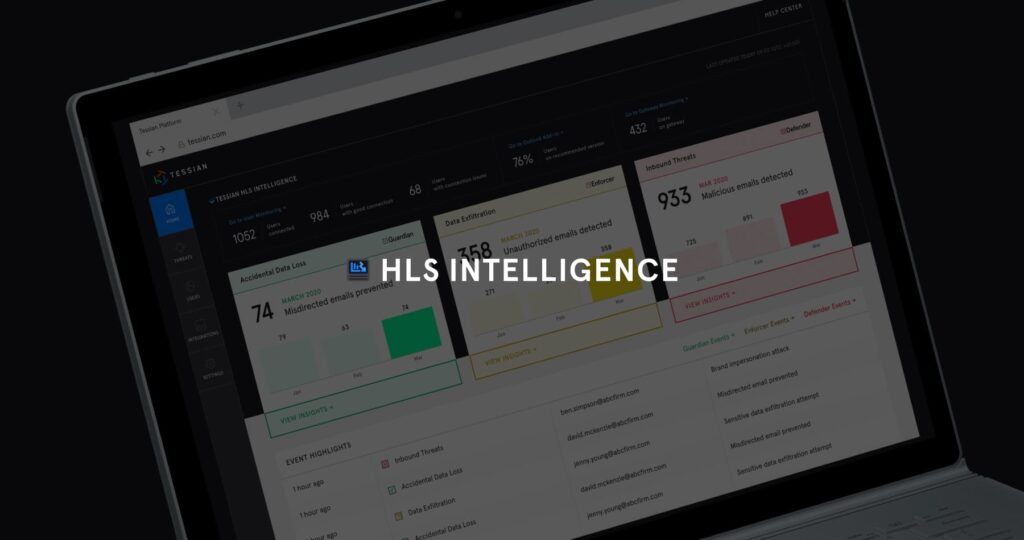
Tessian HLS Intelligence offers unmatched visibility into Human Layer Security vulnerabilities (data exfiltration, accidental data loss, spear phishing, Business Email Compromise, and other targeted attacks) providing security teams with insights, automated intelligence, and robust threat mitigation tools. All of this enables rapid investigation and remediation, and, importantly, helps continuously reduce risk over time.
88% of data breaches are caused by human error.
To combat that, Tessian built, created, and developed Defender to prevent spear phishing, Business Email Compromise, and other targeted impersonation attacks; Guardian to prevent accidental data loss; and Enforcer to prevent data exfiltration.
But, detection and prevention are only one part of the solution. To be truly effective, solutions have to proactively and consistently improve an organization’s broader security posture.
Security leaders should be able to:
Tessian Human Layer Security Intelligence does all of the above.
We provide our customers with real-time insights into risks on email and give security teams the tools they need to downtrend those risks.
We’ve already mentioned some of the key challenges that security, compliance, and IT leaders are up against. So, how does Human Layer Security Intelligence make your jobs easier?
Improving security visibility is key.
With HLS Intelligence, Tessian customers can easily and automatically get detailed insights into inbound and outbound security threats and employee actions.
Why does this matter? It allows security leaders to know precisely where to focus their efforts and which corrective actions to take in order to best allocate their resources.
For example, with clear visibility of employee behavior, it will be easy to spot those employees who frequently attempt to send company data to their personal email accounts to work from home. That way, security teams can then offer additional, targeted training and issue helpful reminders of existing security policies.
Beyond that, customers will also be able to benchmark their risk levels against industry peers. This will help organizations identify strengths and successes and help highlight how and where they can improve their security posture.
Most solutions are a blackbox when it comes to understanding the threats detected. And, without knowing the “who, what, when, and why” behind security events, mitigation can be difficult.
In an effort to pin down the “who, what, when, and why”, security and IT teams spend countless hours aggregating data, analyzing data, and investigating incidents. But, this is a slow, manual process which means remedial response times are often longer than they should be.
Not with Tessian’s HLS Intelligence.
HLS Intelligence offers a curated list of high priority events so security leaders can immediately zero in on those that are most critical. No manual investigation required.
It’s simple:
While the goal is to prevent incidents from happening in the first place, robust mitigation tools are an essential part of any security solution.
With email quarantine and post-delivery protection like bulk email removal and single-click clawback, it’s easier than ever for security teams to take action.
And, with shared threat intelligence across the entire Tessian ecosystem, machine learning models automatically update and protect all Tessian Defender customers from all blocked domains. That means Tessian customers automatically benefit from Tessian’s network effect and new threats can be prevented before they’re even seen in your environment.
The benefits of Tessian Human Layer Security Intelligence are best understood in the context of real situations. So, let’s look at three example use cases.
Several employees receive an email that appears to be from a health organization with advice around COVID-19. The email automatically triggers a warning advising employees that the email is suspicious based off of the content and sender information.
Simultaneously, you’re alerted of the burst attack and are able to first delete the email from user inboxes and then block the domain. Each of these two actions requires a single click.
But, it’s not just your organization that’s protected from the threat. All Tessian customers will benefit as the domain is automatically blocked across the Tessian ecosystem.
In reviewing outbound events, you notice two employees are frequently sending emails with attachments to their personal accounts. When presented with a warning that explains why the action is being flagged as suspicious, they opt to send the email anyway. Why? Because these exfiltration attempts aren’t intentionally malicious, they’re simply trying to ensure they have access to the documents they need to work, wherever they are.
Instead of implementing a blanket rule that blocks all emails to freemail accounts across the company, you can take a more targeted approach. You can use this as an opportunity to reinforce security awareness training and in-house policies and explain why the email is considered unauthorized despite the employees’ good intentions.
You can also offer alternatives that would enable the employees to access relevant documents without having to email attachments to themselves.
In reviewing outbound events, you notice a spike in data exfiltration attempts by an employee. In the last week, he’s sent upwards of 20 attachments to a recipient he has no previous email history with.
With this information in mind, you approach his line manager and find out that two weeks ago, the employee was denied a promotion and subsequent raise.
You now have oversight of the “who, what, why, and when”.
This employee is planning on resigning and is taking company data with him. To prevent any further data exfiltration attempts, you can create custom filters specifically for that user, including customized warning messages or you could create a filter that would automatically block any future exfiltration attempts. For example, you could block email communications containing attachments to specific a domain or block emails containing attachments altogether, depending on the severity of the previous incidents.
Interested in learning more about Tessian Human Layer Security Intelligence and how it can help you strengthen your defense against human error on email? Get in touch with your Customer Success contact.
Not yet a Tessian customer? Book a demo!