From the CEO to that new intern, everyone in the company email directory is a potential risk for sending misdirected emails. Misdirected emails are common — sending an email to the wrong person is an easy mistake. Who hasn’t done it? But they can also be disastrous, potentially damaging a company’s reputation, revealing its confidential data, and breaching its customers’ privacy.
One new group, however, can potentially present more of a risk than most – Sales Engineers (SEs) and Tech Ops (TOs) teams. SEs and TOs are mainly found in enterprise-level, technology-focused *aaS businesses in sectors such as software systems, manufacturing, or telecoms, where the product is some form of data handling solution.
According to the Bureau of Labor Statistics Occupational Outlook Handbook, there were 63,800 SEs in the US in 2020. Their role is like a SWAT team, called in by the sales team to help ‘seal the deal’, either when a lead is deep into the process and needs extra clarity, or when they have too many technical obstacles for the sales rep to handle. SEs have a sales mentality, but couple that with a deeper understanding of the form and function of the product, processes, or service.
Here’s five reasons why they might be at higher risk, and how you can mitigate that risk.
They support several salespeople
In a typical large enterprise, one SE might support several sales reps. Numbers vary depending on the size and scope of the business in question, but a typical ratio might be one SE to four or more sales people. The higher the number, the higher the potential risks, because they now touch four times the amount of data and contacts flowing through an organization compared to their colleagues.
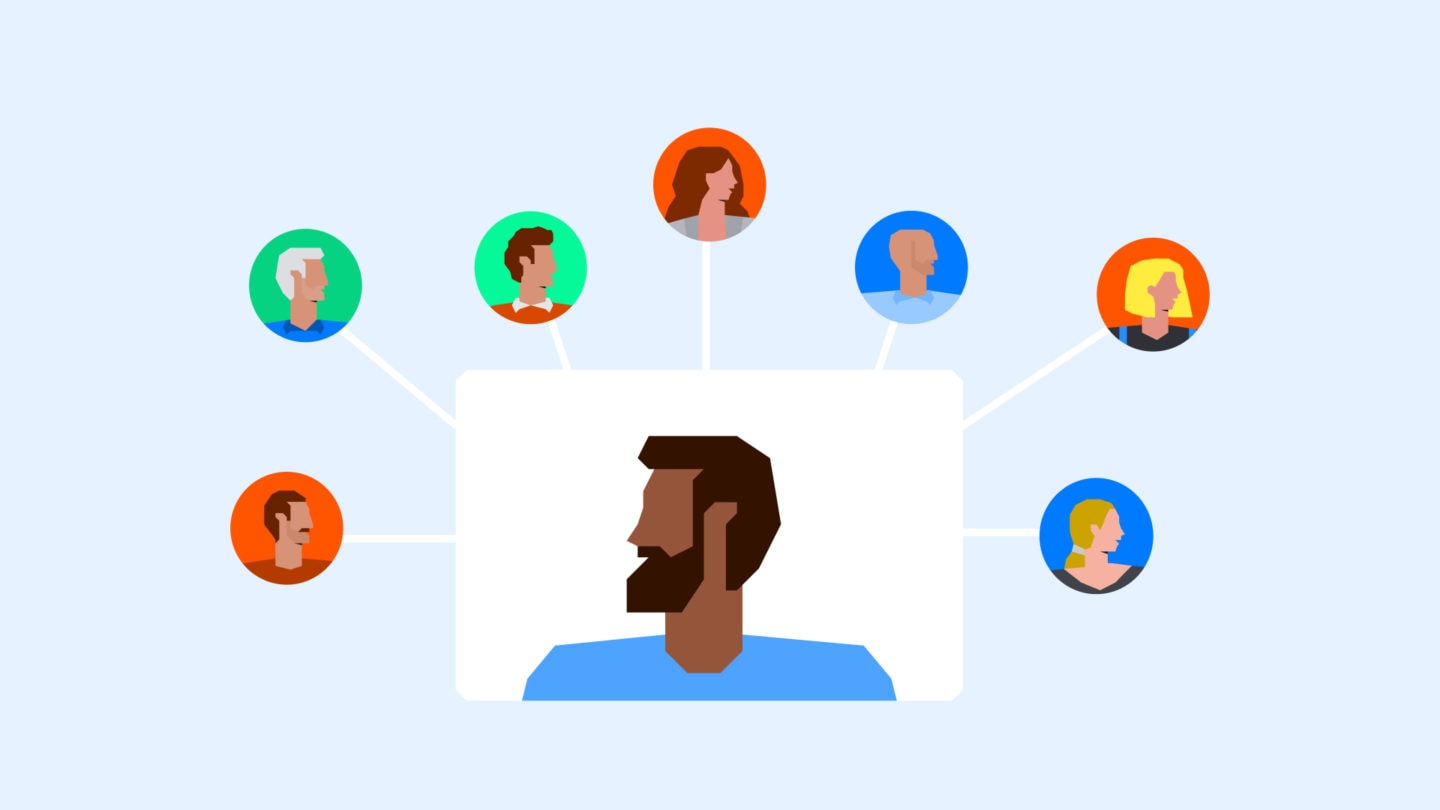
…And several other teams.
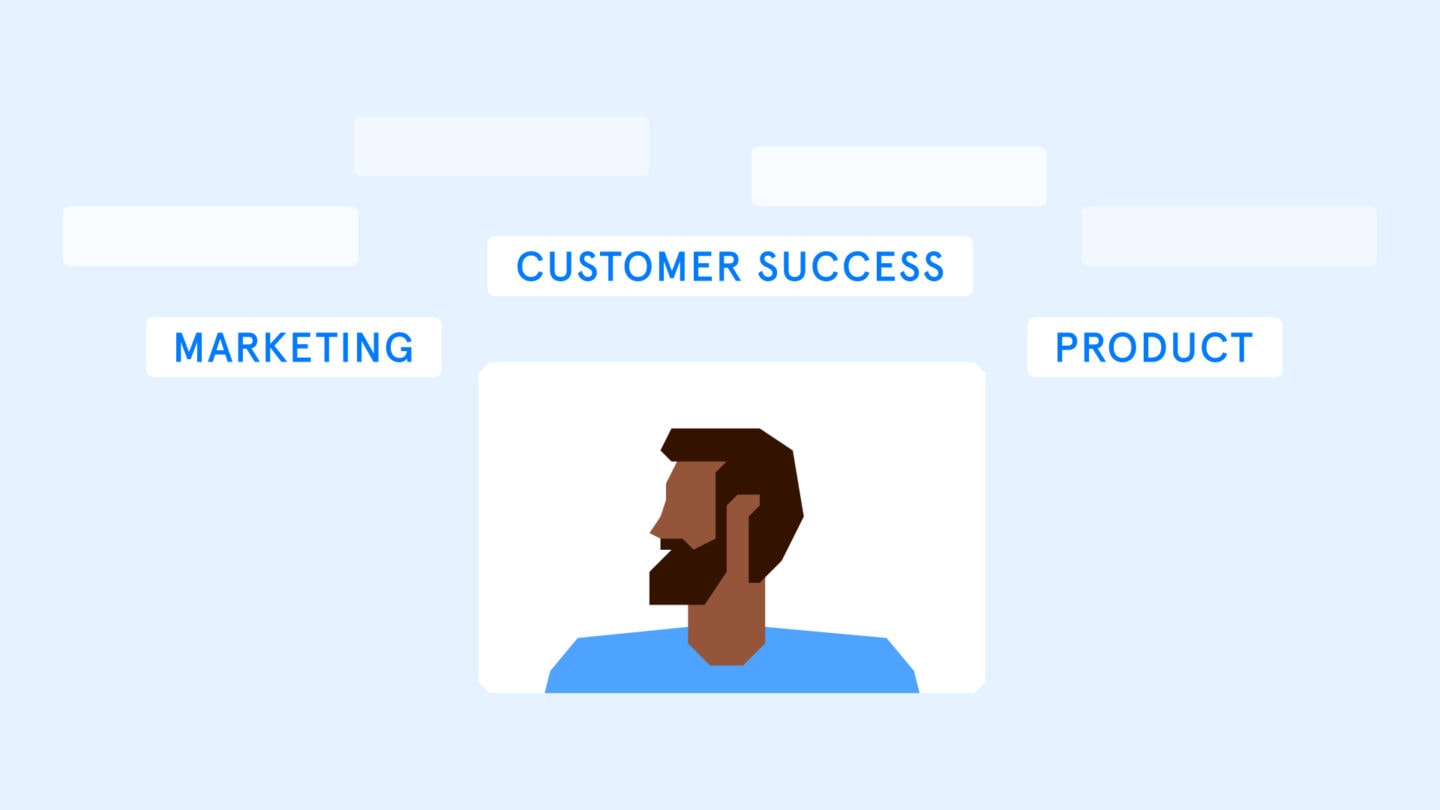
SEs not only work hand in hand with salespeople on new leads, they might also help Customer Success teams move existing customers to higher plans or additional services – again, more potential risk.
Of course, being deep in the workings of the product means they also interact regularly with the product or engineering team. They might even work with marketing on case studies and testimonial content. So as you can see, they occupy a highly central function within large, complex matrix organizations.
Meaning they have access to lots and lots of data…
SEs not only have access to leads’ personal details, they might also have access to that company’s critical data such as customer information, financial data, or intellectual property.
Many firms conduct proof of concept (PoC) and proof of value (PoV) tests, where the solution is prototyped with the lead’s firm. Depending on the solution and the customer firm, this can involve actual company data, assets, or information.
All of this data is highly attractive to bad actors who can ransom it back to you, sell it to others, mine bitcoin using your systems, and generally trash your processes and reputation. As one security analyst from our friends at KnowBe4 put it, we’re in the age of the ‘quintuple extortion’.
…and highly sensitive information.
They They could be privy to what the company’s employees are doing, where they are, or their Personally Identifiable Information (PII) such as staff’s social security numbers, bank details, and personal email addresses. There’s also sensitive details on business structure things, like potential mergers and acquisitions, reorganizations, or redundancies. In short, SEs have access to a wide group, and interact with that group at a higher frequency.
Which means they’re severely time pressured.
Reps might call in an SE as a last ditch effort to save a deal from potentially falling through. Perhaps the lead is thinking of walking away because they have several technical questions that the rep can’t answer. The SE is needed fast and plunged deep into the deal to try to save it.
That creates a time sensitivity pressure for the SE. As this blog post by GoConsensus says, the problem supporting several sales people is that at times, a sales rep may not have access to a sales engineer to provide the support they need.
That can mean the SE is under pressure from both their colleagues to save the deal, as well as the lead who might be cooling on the idea because it doesn’t appear to fit their needs. As the time ticks down and the pressure increases, so do the potential risks of making mistakes.

We know this because our Psychology of Human Error Report revealed that working in tech doesn’t necessarily make you cybersecurity savvy. Employees in the technology industry were the most likely to click on links in phishing emails, with nearly half of respondents in this sector (47%) admitting they had done so. This was closely followed by employees in banking and finance (45%).
The tech industry also had the highest percentage of employees that agree there is an expectation in their organization to respond to emails quickly (85%), while 77% in the financial sector said the same. This suggests that quick-to-click and fast-paced working cultures could result in employees mistakenly clicking on phishing emails.
Why? Because nearly half of respondents (45%) cited distraction as the top reason for falling for a phishing scam.
[infogram id=”a62b439e-5b6e-4bf7-970f-ffdc541c53ff” prefix=”eOy” format=”interactive” title=”MISTAKES 2.0 MODULE 4″]
So how does this threat manifest itself at enterprise level?
In many ways, these issues at enterprise level are a double edge sword. On the one hand, enterprises can have great software and processes, as well as the budget and teams to support it. On the other hand they’re larger and more complex, so the potential for danger is greater.
So how many people are we talking about here? Take a big global company like Salesforce for example, with 64,000 employees according to LinkedIn. A quick search for ‘Sales Engineers’ in their people section returns 3,955 people. For Amazon (868,467 employees) it’s even bigger – 5,792.
Yet our State of Data Loss Prevention report revealed an average of 800 emails are misdirected in organizations with 1,000 employees during a single year. What’s more, Forrester Consulting’s recent Take Control Of Email Security With Human Layer Security Protection report, commissioned by Tessian, found that the percentage of employee-related email security incidents by company size was significantly higher in companies with more than 20,000 employees.
With all that it’s clear why 61% of security and risk leaders surveyed in the Forrester Consulting report believed that an employee’s actions will cause their organization’s next data breach. They’ve simply done the math.

How can enterprise organizations secure themselves against these dangers?
The consequences and fall out of any potential misdirected email can be mundane, or they can be utterly catastrophic (as these real world examples reveal). We spoke to one CISO on condition of anonymity, who told us, “For the C-Suite, the most important thing is understanding risk scoring – who’s the most targeted departments and what data do they handle?” – SEs and TOs fall into this category.
That risk has to be balanced more broadly with having processes that still let employees do their jobs in highly dynamic environments. A process where a deal is lost because an email is in a quarantine outbox with several thousand others waiting for the IT department to approve it isn’t going to help your team hit their quarterly targets.
This ‘human first’ approach centers on two things: using great tools that don’t hamper the workflow, and flagging when potentially moving data with the communication chain.
Both these things drive what we do at Tessian. Our Human Layer Security platform detects and prevents advanced inbound and outbound threats on email, automatically stopping data breaches and security threats caused by employees.
Powered by machine learning, Tessian provides unparalleled visibility into human security risks, detects and prevents accidental data loss, data exfiltration, and advanced phishing attacks while continuously driving employees toward secure email behavior through in-the-moment training.
Built as a cloud-native platform, Tessian integrates seamlessly with O365, Google Workspace, and MS Exchange environments within minutes, learns in hours, and starts protecting in a day closing the critical gaps in the email security stack
The Tessian differentiators:
- Threat prevention: Tessian protects against both known and unknown email attacks, including business email compromise, account takeover, spear-phishing, and all impersonation attacks that bypass SEGs, M365, and G Suite
- Education and awareness: With Tessian’s in-the-moment training, organizations can educate and empower users to build continuous email security awareness
- Reduced admin overhead: Tessian removes the burden on SOC and admins by automating repetitive tasks such as maintaining triage and review. This eliminates the need for human verification of email threats, reducing FTE requirements.
- Data-rich dashboards: With Tessian, security teams have clear visibility and the ability to demonstrate clear ROI
So if you want to ensure your Sales Engineers can do what they do best – be that SWAT Team for your sales reps – rather than a higher risk to your business, get in touch today and see how we can help you secure your organization’s Human Layer.
Andrew Webb
Senior Content Manager

















