The National Cyber Security Centre (NCSC) recently revealed that it removed more online scams in 2020 than in 2016-2019 combined, due to a surge in malicious activity related to the Covid-19 pandemic.
In a report published by the NCSC’s Active Cyber Defence program, it’s revealed that more than 120 phishing campaigns in which the NHS was impersonated were detected in 2020 – up from 36 in 2019. The lure commonly used in these scams? The vaccine roll-out.
How have cybercriminals taken advantage of the Covid-19 vaccine?
Tessian researchers have been monitoring phishing campaigns related to the vaccination roll-out since the start of 2021, and their findings clearly demonstrate how quickly cybercriminals will jump on milestone moments to craft convincing scams.
In fact, in the week commencing January 4th 2021, Tessian data shows that the number of scam emails related to the vaccine was 188% higher than the weekly average of such scams detected in 2021. It was during this week that the UK began distributing the AstraZeneca/Oxford vaccine.
Our researchers also saw significant spikes in suspicious emails related to the vaccine during the:
- Week commencing 25th January, when the Biden administration promised to have enough coronavirus vaccine for the entire US population by the end of summer. During this week, the number of suspicious emails relating to vaccines increased by 585% compared to the previous week.
- Week commencing February 8th, when U.S. government officials announced that around 1 in 10 Americans had received the first dose of the two-part Covid-19 vaccine. The number of suspicious emails was 148% higher than the weekly average of vaccine related scams detected by Tessian in 2021.
- Week commencing February 15th, when G7 countries pledged $4 billion to global Covid-19 vaccine initiatives. Suspicious emails related to the vaccine were 133% higher than the weekly average.
- Week commencing March 1st, when President Biden announced that vaccines will be available for every US adult by May. The number of suspicious emails related to vaccines during this week were up by 161% compared to the previous week.
Now that the vaccine roll-out is well and truly underway, with many people having received both doses of the jab, Tessian researchers reported a significant drop in the number of scams. This a clear indication that hackers were responding to hot topics in the news to apply a sense of urgency and timeliness to their malicious campaigns.
“When the UK began distributing the AstraZeneca/Oxford vaccine, the number of suspicious emails relating to the Covid-19 vaccine was 188% higher than the weekly average of vaccine scams detected in 2021. ”
Tessian Threat Intelligence
Why are these phishing attacks so effective?
After a year of stress and uncertainty, people were desperately waiting for the vaccine roll-out. People urgently wanted to find out things such as when they will get the vaccine, where they can receive the jab, and many more wanted to research and understand potential side effects.
In response, cybercriminals capitalized on people’s desire for more information. They created fake websites, in which people were lured to via phishing scams, and tricked their targets into sharing personal or financial data in exchange for the information they were looking for. Tying their campaigns to timely moments in the news added another layer of urgency.
In fact, additional Tessian research revealed that a significant of website domains related to the Covid-19 vaccine were registered in the early days of the roll-out, with over 2,600 new website domains being created between 5 December 2020 and 10 January 2021. Many of these domains impersonated legitimate healthcare websites, touted misinformation around injection side effects, and falsely claimed to offer guidance around timing and logistics of distribution.
The reason why these phishing scams are so effective is because hackers use techniques to prey on people’s vulnerabilities during times of crisis. In a report we published with Jeff Hancock, Professor of Communication at Stanford University and expert in trust and deception, he said, “when people are stressed and distracted, they tend to make mistakes or decisions they later regret.”
What does a vaccine scam look like?
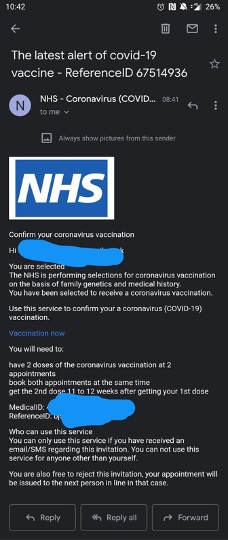
Oftentimes, cybercriminals impersonated trusted healthcare organizations or government agencies to trick their victims into thinking they’d received an email from a legitimate source, as shown in the example below.
Example of vaccine scam. Source: Reddit.
In other examples detected by Tessian, bad actors would impersonate Human Resource departments, urging staff to click on links or download malicious attachments that supposedly contained information about the vaccine roll-out and/or infected employees.
Below is an example received by a global financial services enterprise, and detected by Tessian Defender. In this case:
- The attacker registered a domain to impersonate an outsourced Human Resources function in a phishing email.
- The phishing email used Covid-19 as the theme and used fear and urgency tactics to announce an “Covid-19 Emergency”, seemingly providing a list of known infected persons.
- The aim of this was to encourage those who received the email to click a link to a PDF which claimed to contain information about the emergency and a list of infected individuals.
- The attacker used the name of the financial services organization in the name of the file which was linked to in the URL. This implies that this attack was highly targeted; the recipient would assume that the link was legitimate.
- It’s likely that the PDF linked to in the URL would have contained malicious macros designed to infect the target’s device.
Examples of Covid-19 phishing emails, detected by Tessian Defender.
How to spot a Covid-19 scam
Always be wary of emails purporting to come from healthcare organizations asking you to click on links to ‘find out more’. Always check the sender name and address, particularly if you have received an email on your phone in order to verify the sender’s identity.
It’s also important to question any websites that request personal data. Domains that spoof government healthcare websites, like the Centers for Disease Control and Prevention (CDC) are especially dangerous, as cyber criminals could potentially steal extremely sensitive information such as Social Security numbers and health information like insurance or medical history details.
At a time when phishing scams are only growing in frequency and sophistication, always think twice before entering your personal information online and remember, if it doesn’t look right, it probably isn’t. Remember, you can always verify any question by contacting the sender directly, via another means of communication, to check it’s the real thing.