Training is an essential part of every organization’s security strategy.
Monthly phishing simulations can help employees spot inbound attacks. Quarterly training sessions can help reinforce existing policies and procedures around data handling and password hygiene. And introducing new joiners to the cybersecurity team during onboarding is a great way to build a positive security culture.
But sadly, even with all of this, employees still get phished, still ignore or workaround cybersecurity policies, and still mishandle data.
Why? Because security just isn’t top of mind for the average person. That’s why security leaders have to find ways to consistently educate their people and reinforce policies.
In-the-moment warnings can help.
What are in-the-moment warnings?
When Tessian detects a threat (for example, a spear phishing email or an attempt at data exfiltration) employees see a warning message. It’s written in plain English, and offers context around why the email was flagged.
A picture’s worth a thousand words, right? Here are a few examples.
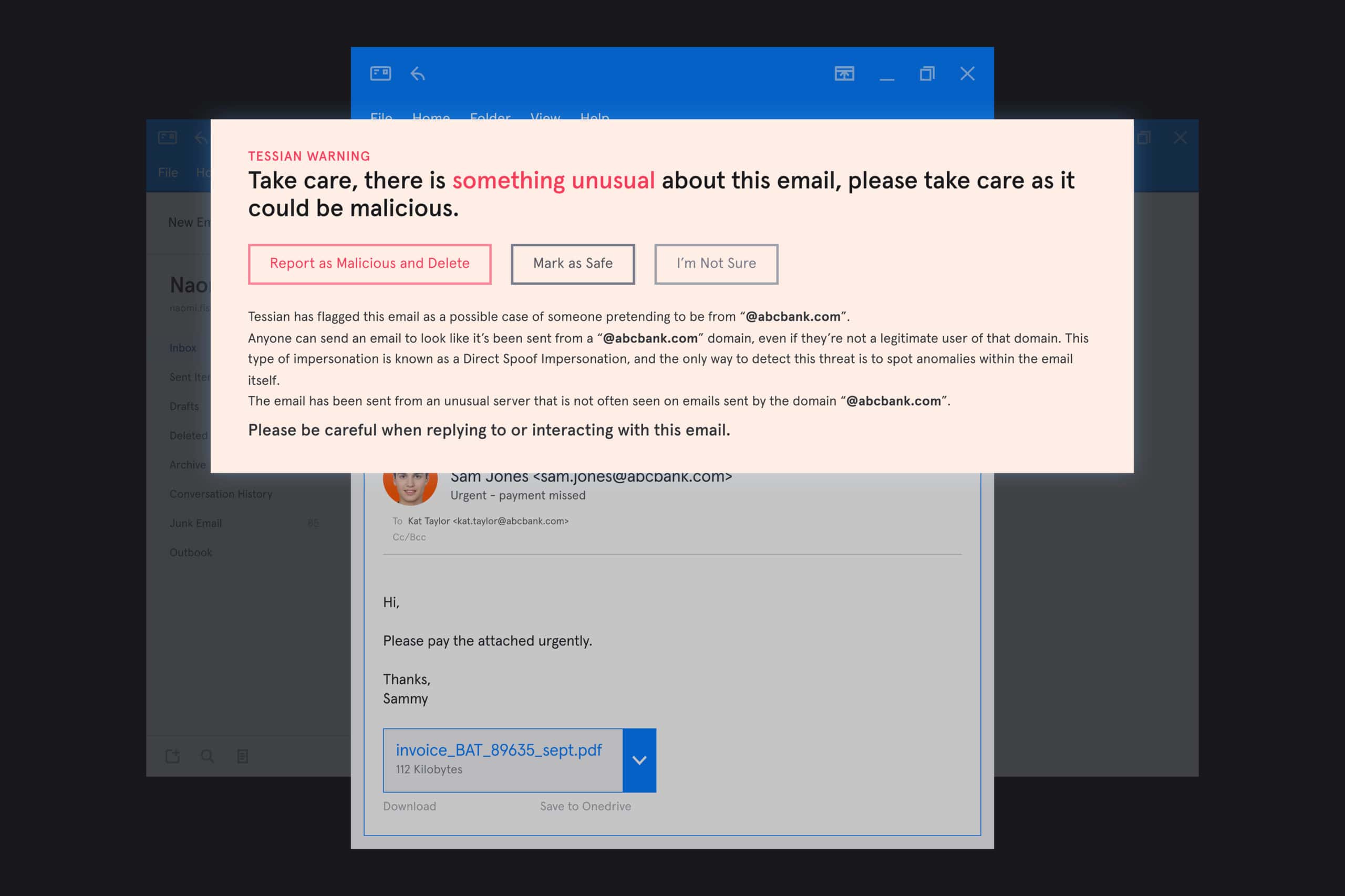
In this example, Tessian Defender has flagged an email as a potential impersonation attack.
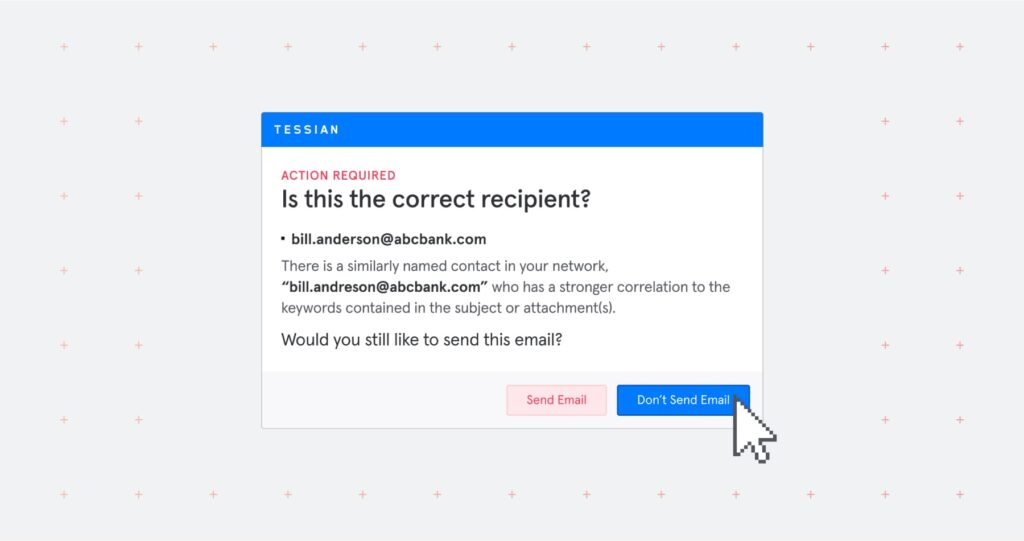
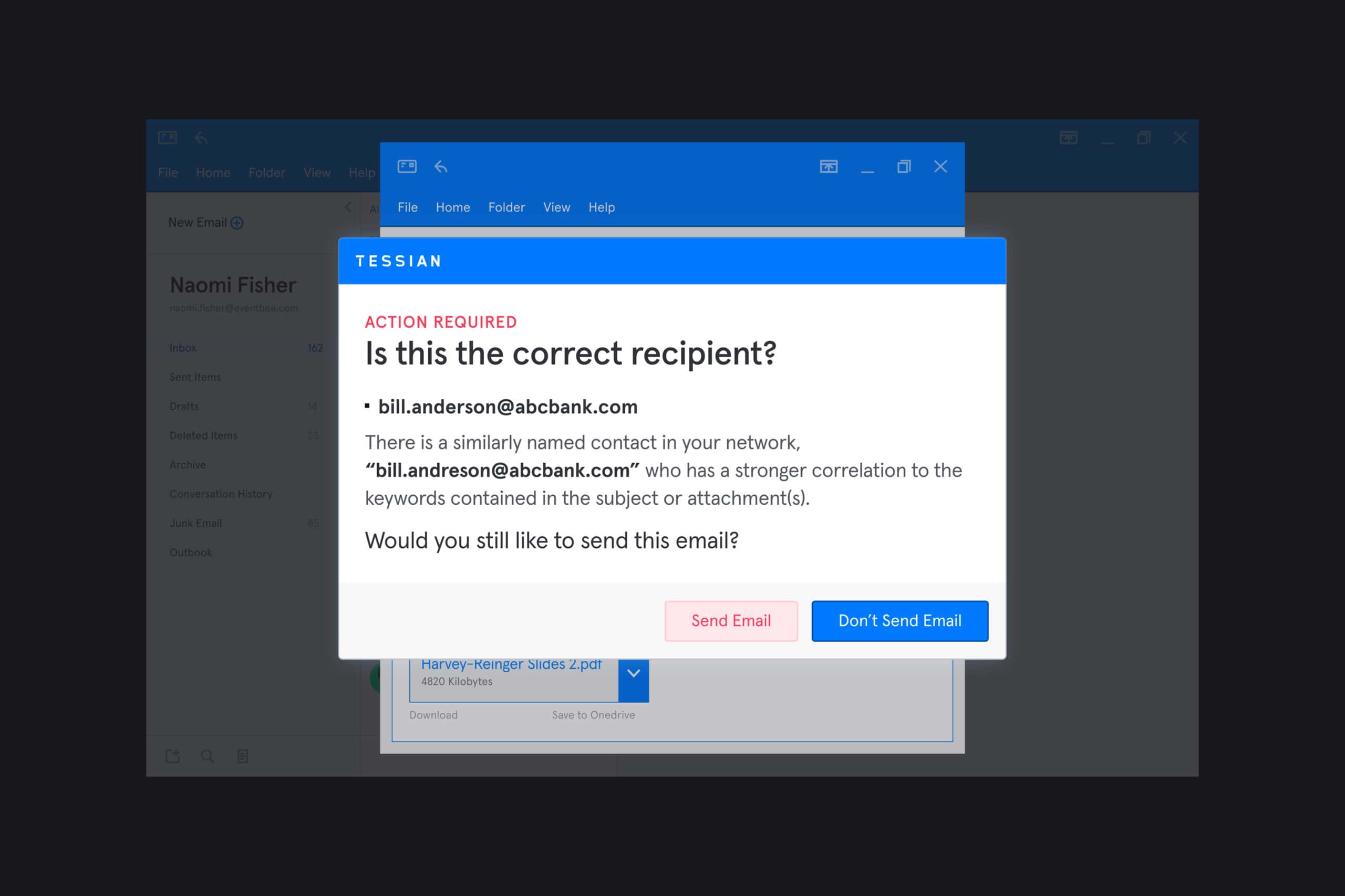
In this example, Tessian Guardian has flagged an email that's likely being sent to the wrong person.
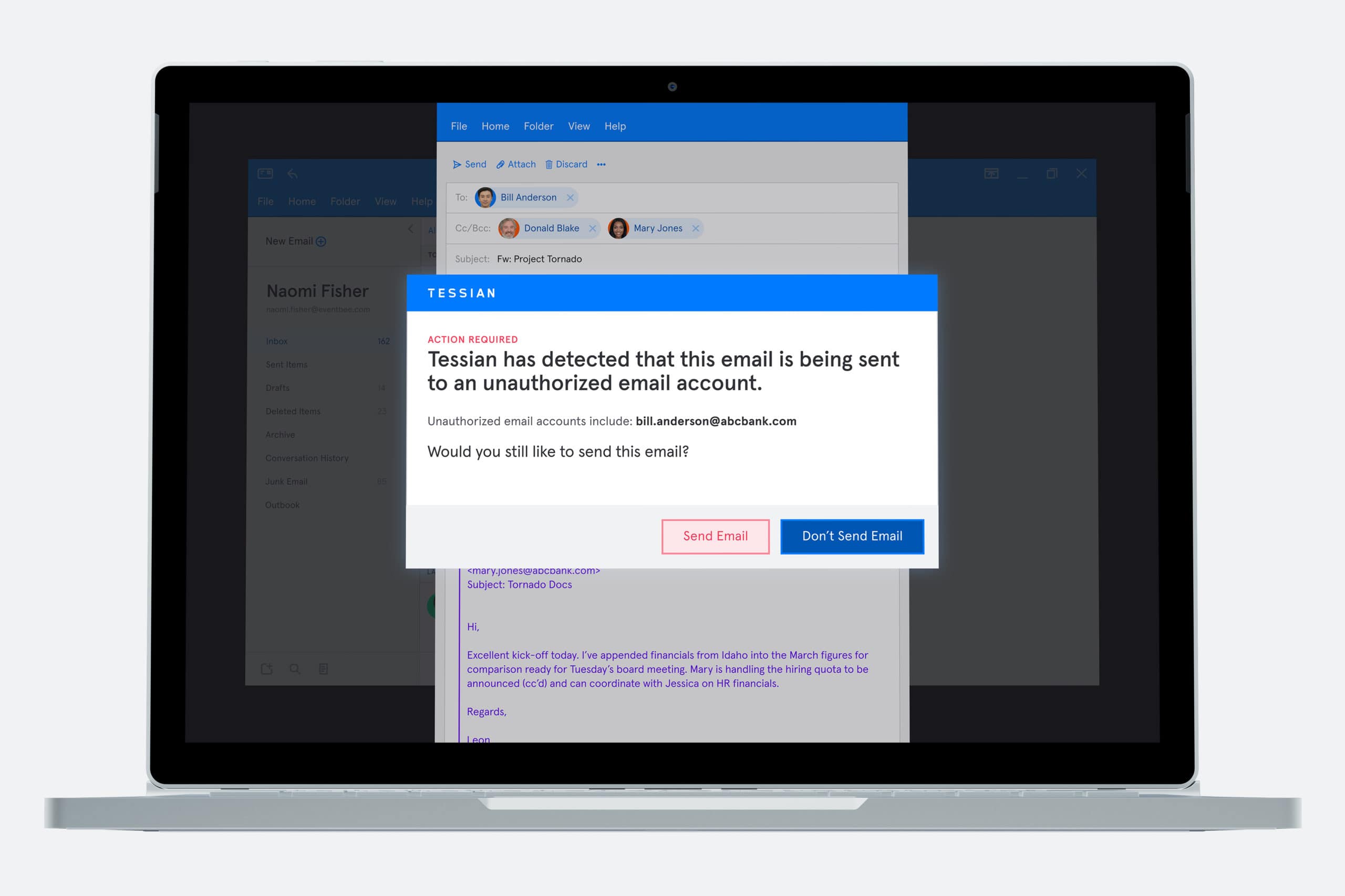
In this example, Tessian Enforcer has flagged an email containing sensitive information that's being sent outside the company's network.
Think of these as a sort of “yield” sign. They introduce a pause and give employees the information they need to make the right decision.
If they realize “Oops! I certainly was about to send that email to the wrong person” or “Yes! This email does seem a little fishy”, they can easily change the recipient’s email address or mark the email as malicious. All it takes is a single click. Crisis (and breach) averted.
Importantly though, these in-the-moment warnings do more than just prevent threats in real-time. They help change employees’ security behavior long-term, and nudge them towards safer online behavior.
Nudge theory 101
Without diving too deeply into behavioral economics, let’s look at Nudge theory.
There are 5 stages of behavior change:
- Precontemplation: The person is unaware of the problem. That means it’s your job to create awareness.
- Contemplation: The person is aware of the problem and the desired behavior change. The key here is to persuade and motivate them to act.
- Preparation: The person intends to take action. You just need to help them understand what to do and how.
- Action: If you facilitate it, the person can practice the desired behavior.
- Maintenance: Finally, by reinforcing the behavior regularly, the person can work to sustaining the behavior change
In a sentence, Nudge theory uses indirect suggestions and positive reinforcement to influence behavior.
“It shouldn’t be about “catching” people; humans don’t like to get caught. That can breed anger and frustration. It has to be a learning moment, not a “gotcha!” moment. You have to give people a chance to get better. And people can get better!”
James McQuiggan
Security Awareness Advocate at KnowBe4
So, what does this look like in the context of cybersecurity? And where do in-the-moment warnings come in? Let’s go back to the tried and tested example of phishing.
While Joe, your Accounts Payable Manager, is familiar with the term “phishing” and understands that bad actors do target people via email, he thinks the average attack is easy to spot. Poor formatting. Unpersonalized. Grammatical errors. A “too-good-to-be-true” offer.
Step 1 is to create awareness. This is generally done through “standard” training programs. (If you’re looking for a bank of spear phishing examples, check out our Threat Catalogue.)
Now that Joe has a better idea of how sophisticated phishing attacks are, he’ll do his best to spot them and knows that – if he is targeted – he should report the email to the cybersecurity team.
✅ Precontemplation
✅ Contemplation
✅ Preparation
Next, you have to let Joe “practice”. A lot of security leaders rely on phishing simulations for this. The problem is, oftentimes, employees can feel like they’re being tricked instead of educated.
Take this for example. Or this.
The bottom line: well-intentioned phishing simulations can have a negative impact on security culture.
It’s also worth pointing out that while phishing simulations can introduce employees to many different types of phishing attacks, they can’t possibly prepare them for every type of incident. Even the most cyber-savvy people can fall for advanced spear phishing attacks.
That’s where Tessian in-the-moment warnings come in.
Tessian would enable Joe to “practice” every time he sends or receives an email – without feeling like he’s being tricked – by offering context and reinforcing phishing awareness.
If Joe receives a potentially malicious email, he’s given the information he needs to determine whether to delete it, or open it. And this isn’t just once a month. Tessian is always working silently in the background to detect threats and help employees like Joe make the right decisions.
Every warning is a learning opportunity.
✅ Action
✅ Maintenance
How can in-the-moment warnings bolster your training program and improve your security posture?
We’ll start by saying that in-the-moment warnings aren’t a silver bullet. (Silver bullets don’t exist in cybersecurity!) But, in concert with technology, policies, and processes, they’ll help you consistently improve your organization’s security posture
“People seem to think that if you do one thing, you’ll be good. We’ll buy a firewall, we’ll be secure. We’re in the cloud, our data is protected! We’ll do training, and our employees will become experts in cybersecurity. But it’s just not true. A company must have processes that promote their policies, along with technology, and training. That’s the holy grail.”
James McQuiggan
Security Awareness Advocate at KnowBe4
Tessian customers have seen click-through-rate on phishing simulations drop below 1% after deploying Tessian. And, on average, customers see an 84% reduction in data exfiltration. (For reference, according to KnowBe4’a 2021 Phishing By Industry Benchmarking Report, 31.4% of untrained employees fail phishing simulations…)
But it’s not just about the numbers. It’s also about how employees interact with the tool.
According to Else Ferreira, CISO at Evercore, “They say security is a thankless job. But Tessian was the first security platform that we deployed across the organization where I personally received “thank you’s” from employees who would have made a mistake with potentially dire consequences, but didn’t because of Tessian”.
Looking for more customer stories? Click here.