Email spoofing is a common way for cybercriminals to launch phishing attacks — and just one successful phishing attack can devastate your business. That’s why every secure organization has a strategy for detecting and filtering out spoofed emails. Do you?
This article will walk you through some of the best methods for preventing email spoofing. Want to learn more about email spoofing, how hackers do it, and how common these attacks are? Check out this article: What is Email Spoofing and How Does it Work?
And, if you’re wondering how to prevent your email address or domain from being spoofed…the first step is to enable DMARC. But, even that isn’t enough. We explain why in this article: Why DMARC Isn’t Enough to Stop Impersonation Attacks.
Security awareness training
Email spoofing is a common tactic in social engineering attacks such as spear phishing, CEO fraud, and Business Email Compromise (BEC). Social engineering attacks exploit people’s trust to persuade them to click a phishing link, download a malicious file, or make a fraudulent payment. That means part of the solution lies in educating the people being targeted.
It’s important to note that cyberattacks target employees at every level of a company — which means cybersecurity is everyone’s responsibility. Security awareness training can help employees recognize when such an attack is underway and understand how to respond.
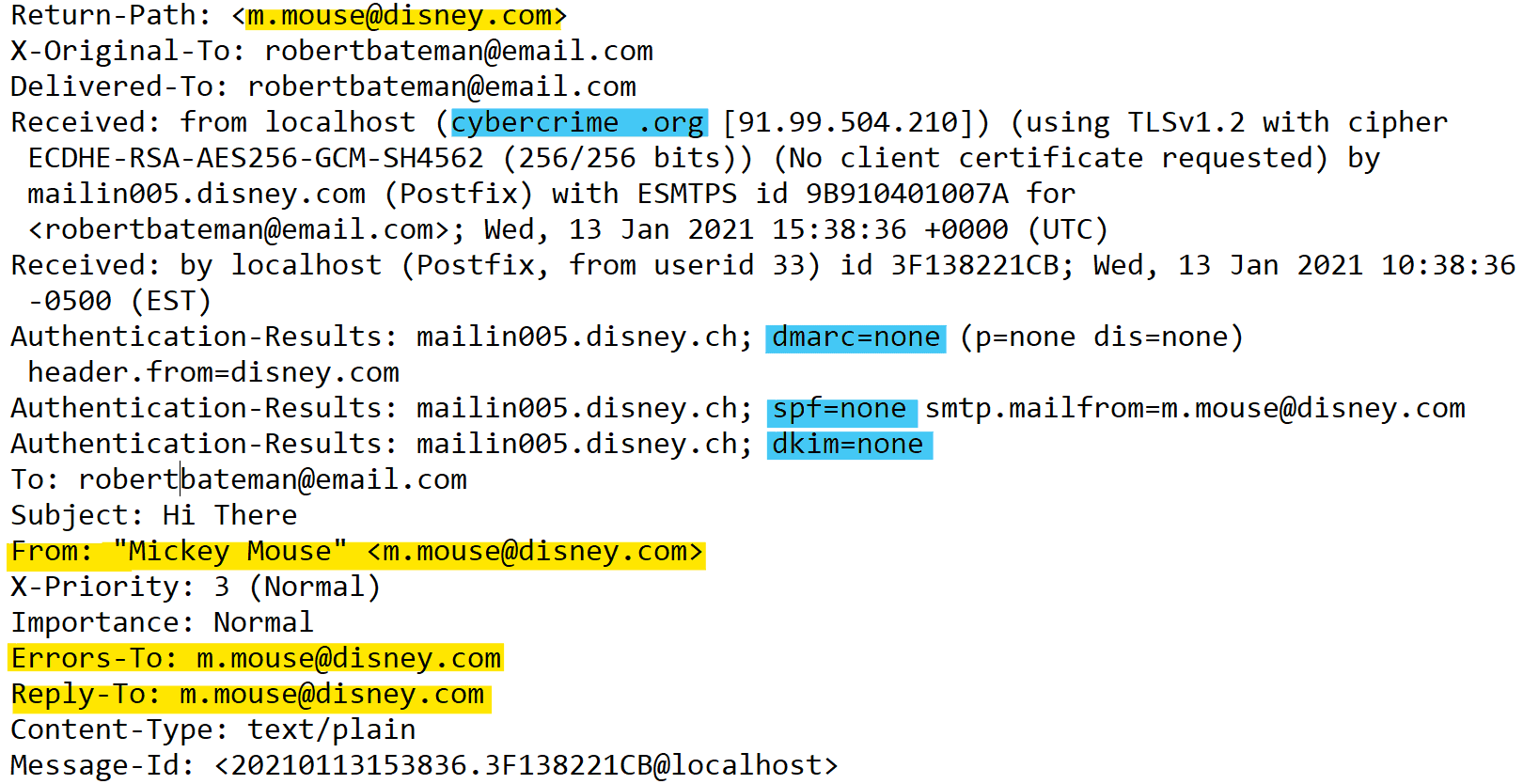
In this article – What Is Email Spoofing and How Does it Work? – we looked at how an email’s header can reveal that the sender address has been spoofed.
Looking “under the hood” of an email’s header is a useful exercise to help employees understand how email spoofing works. You can see if the email failed authentication processes like SPF, DKIM, and DMARC, and check whether the “Received” and “From” headers point to different domains.
Take a look at the example below. See how the “Return-Path”, “From”, “Errors-To”, and “Reply-To” fields (from “disney.com”) differ from the “Received” field (from “cybercrime.org”).
This is an example of an email header. You can see who the genuine sender is, who they're pretending to be, and that DMARC, SPF, and DKIM aren't enabled.
Note: Disney does have DMARC enabled. This is a hypothetical example! Want to find out which companies don’t have DMARC set up? Check out this website.
Although email headers can provide valuable indicators that an email has been spoofed, it’s obviously not realistic to expect people to carefully inspect the header of every email they receive.
So what are some other giveaways that might suggest that an email spoofing scam is underway?
- The email doesn’t look how you expect. The sender might be “paypal.com.” But does the email really look like PayPal’s other emails? Most sophisticated cybercriminals use the spoofed company’s branding — but some can make mistakes.
- The email contains spelling and grammar errors. Again, these mistakes aren’t common among professional cybercriminals, but they still can occur.
- The email uses an urgent tone. If the boss emails you, urgently requesting that you pay an invoice into an unrecognized account — take a moment. This could be CEO fraud.
You must get your whole team on board to defend against cybersecurity threats, and security awareness training can help you do this. However, Tessian research suggests that the effectiveness of security training is limited.
Email provider warnings
Your mail server is another line of defense against spoofing attacks. Email servers check whether incoming emails have failed authentication processes, such as SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance).
In the “spoofed email header” we provided above, you can see that the spoofed email failed DMARC, SPF, and DKIM checks. Many email providers will warn the user if an email has failed authentication. Here’s an example of such a warning from Protonmail:
This is an example of a warning issued by an email provider about email spoofing.
As part of your company’s security awareness training, you can urge employees to pay close attention to these warnings and report them to your IT or cybersecurity team. However, it’s not safe to rely on your email provider. A Virginia Tech study looked at how 35 popular email providers handled email spoofing. The study found:
- All except one of the email providers allowed fraudulent emails to reach users’ inboxes.
- Only eight of the providers provided a warning about suspicious emails on their web apps.
- Only four of the providers provided such a warning on their mobile apps.
Even the most powerful companies in the world get spoofed, and email filters frequently let these spoofed emails sail through their filters. In October 2021, for example, security experts warned of a highly convincing Amazon spoof email designed to steal customers’ personal and financial information. The email arrived from the domain “secure.amazon.update@gmail.com”
And in March 2021, a widespread email spoofing campaign targeting C-suite executives was uncovered. The attackers created spoofed spear phishing emails that evaded “Office 365’s native defenses and other email security defenses.”
Authentication protocols
As noted by the Virginia Tech study, email providers often allow fraudulent emails through their filters — even when they fail authentication. But, perhaps more importantly, whether a fraudulent email fails authentication in the first place is out of your hands.
For example, SPF lets a domain owner list which email servers are authorized to send emails from its domain. And DMARC enables domain owners to specify whether recipient mail servers should reject, quarantine, or allow emails that have failed SPF authentication.
So, for domain owners, setting up SPF, DKIM, and DMARC records is an essential step to prevent cybercriminals and spammers from sending spoofed emails using their domain name.
But as the recipient, you can’t control whether the domain owner has properly set up its authentication records. You certainly don’t want your cybersecurity strategy to be dependent on the actions of other organizations. Want more information? Check out our eBook on this topic, Why DMARC and Authentication Records are Failing to Stop Spear Phishing.
Email security software
Effective email spoofing attacks are very persuasive. The email arrives from a seemingly valid address — and it might contain the same branding, tone, and content you’d expect from the supposed sender.
This makes email spoofing attacks one of the hardest cybercrimes to detect manually. Humans aren’t good at spotting the subtle and technical indicators of a well-planned email spoofing attack. Legacy solutions like Secure Email Gateways and native tools like spam filters aren’t either. The best approach to tackling spoofing — or any social engineering attack — is intelligent technology.
An email security solution powered by machine learning (ML) will automate the process of detecting and flagging spoofed emails, making it easier, more consistent, and more effective.
Here’s how Tessian Defender solves the problem of email spoofing:
- Tessian’s machine learning algorithms analyze each employee’s email data. The software learns each employee’s email style and maps their trusted email relationships. It learns what “normal” looks like so it can spot suspicious email activity.
- Tessian performs a deep inspection on inbound emails. By checking the sender’s IP address, email client, and other metadata, Tessian can detect indications of email spoofing and other threats.
- If it suspects an email is malicious, Tessian alerts employees using easy-to-understand language.