In late January 2022 a specialist law firm was the target of a spear phishing campaign flagged by Tessian Defender where the threat actor attempted to impersonate the Chairman of the firm. Leveraging common social engineering tactics, the threat actor then targeted the firm’s junior employees. This is known as CEO Fraud.
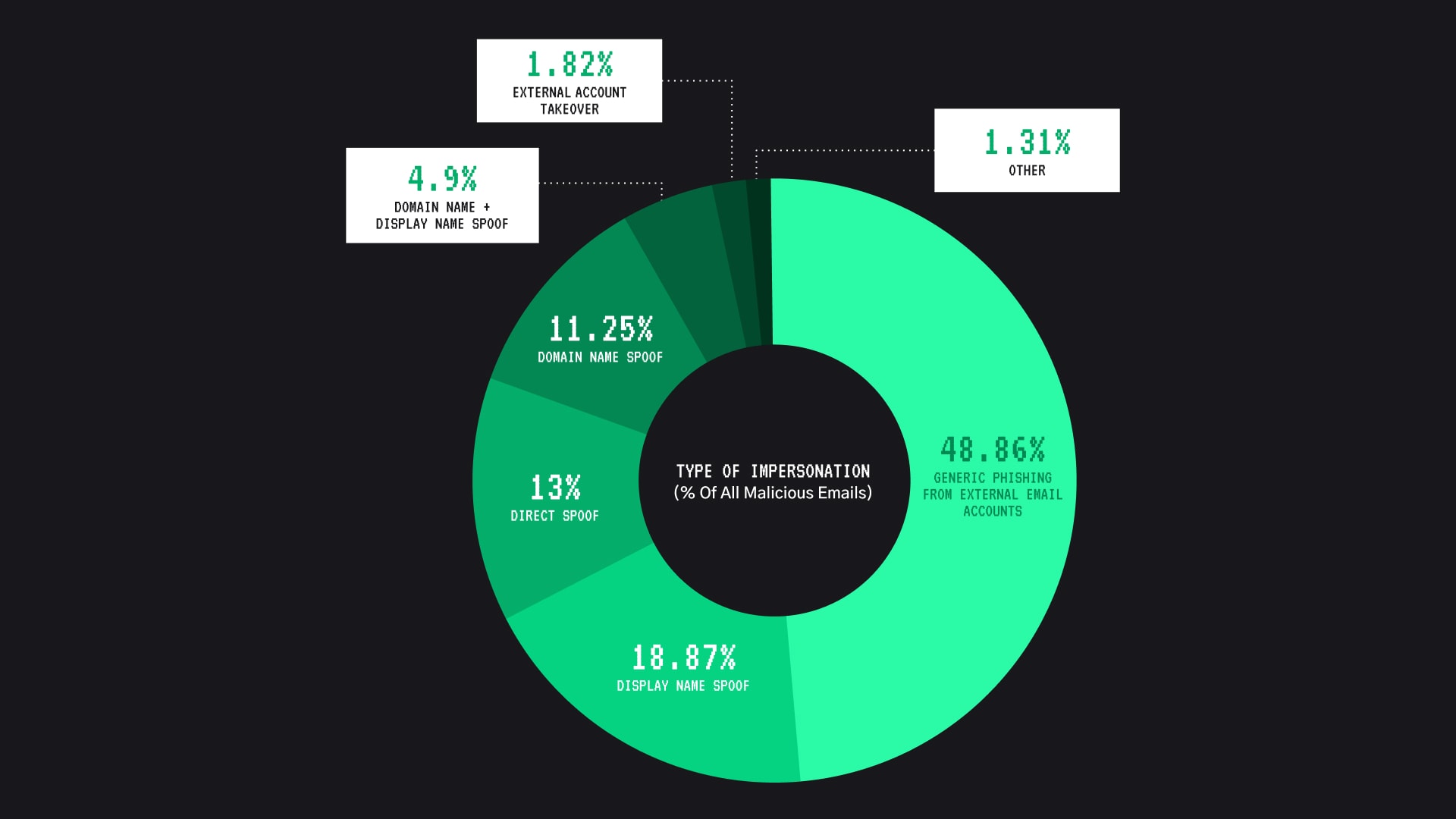
Impersonation attacks are becoming a mainstay for threat actors. Based on our investigation into the 2021 spear phishing landscape, we determined that 60% of the malicious emails seen in Tessian’s network relied on generic impersonation techniques, including freemail impersonation and Display Name Impersonation. An additional 30% relied on more advanced impersonation techniques, including direct impersonation like domain spoofing, direct spoofing and account takeover (ATO).
Tessian Spear Phishing Threat Landscape 2021: Types of Impersonation Levergaged in Spear Phishing Attacks
The Attack
The attacker leveraged the name of the chairman and used a freemail domain. Display name and domain name impersonation spoofs accounted for 4.9% of all malicious email detected and prevented by Tessian in 2021.
Tessian detecting anomalous inbound emails
Email Content:
- Sender Address:
- <Name of Chairman>.<Website Domain>@gmail[.]com
- Body:
- Asking if recipients have time available
- Expressing a sense of urgency
The threat actor registered an email address using Gmail and chose a username that contained the name of the law firm’s chairman, together with the domain used for it’s website. They also changed the display name associated with the account to match the name of the chairman as it appeared on the firm’s website.
After that, the attacker drafted an email with a generic message containing a call to action, asking the recipient “are you available?”. It was sent to +200 individuals at the firm.
The email did not contain links or attachments when it was sent, just the message added by the threat actor. This indicates intent to engage in social engineering via correspondence with recipients.
This style of phishing usually leads to the threat actor trying to convince the recipient to send money or share information that could be leveraged for a more advanced phishing attack. This low-cost-of-effort phishing attempt explains why social engineering now accounts for 70-90% of all successful breaches.
In other cases it can involve sending a few messages back and forth to establish a baseline of trust, before sending a malicious attachment or URL in subsequent emails. Having established trust, the recipient is more likely to click without feeling much concern or suspicion. This also explains why advanced social engineering threats bypass detection by legacy Secure Email Gateways (SEGs), either due to the sophisticated degree of subterfuge in name and domain name spoofing, or because the malicious payload is not present in the initial email.
The Approach
The majority of phishing attacks using this approach will typically come from addresses registered by a threat actor, for example, looking something like “partner1234@gmail[.]com” or “manager5678@hotmail[.]com”.
Attackers use freemail accounts because of their utility in carrying out attacks and zero cost. Freemail accounts that deliver malicious payloads via a proxy server are also notoriously difficult to trace for attribution. Accounts like this will continue to be used to target multiple organizations.
In the case of this attack the address was created as “<Name of Chairman>.<Website Domain>@gmail[.]com”, this indicates deliberate intent to target this firm specifically.
The fact that the threat actor sent the email to +200 junior members of the firm indicates a higher level of planning and reconnaissance than most of these types of attacks typically have.
Our research confirms that law firms are targeted 31% of the time for impersonation style phishing attacks. And firms tend to post details of most employees on their websites including names, email addresses and positions held. Many are also active on networking platforms like LinkedIn. This makes reconnaissance very easy for threat actors.
In the case of this impersonation campaign, the threat actor will have found the firm’s people page, searched for a senior individual to impersonate, then filtered down to the more junior individuals to target.
The C-Suite was impersonated in this attack to amplify the call to action in the messaging and to increase the sense of urgency felt by the targets. Likewise, junior employees were targeted in this attack because they were possibly seen as being more likely to comply with instructions received from senior management.
Another hypothesis could be that the threat actor was seeking to gain more information to wage a secondary spear phishing attack, targeting more strategic positions in the firm such as the finance department.
Real-time, comprehensive email protection
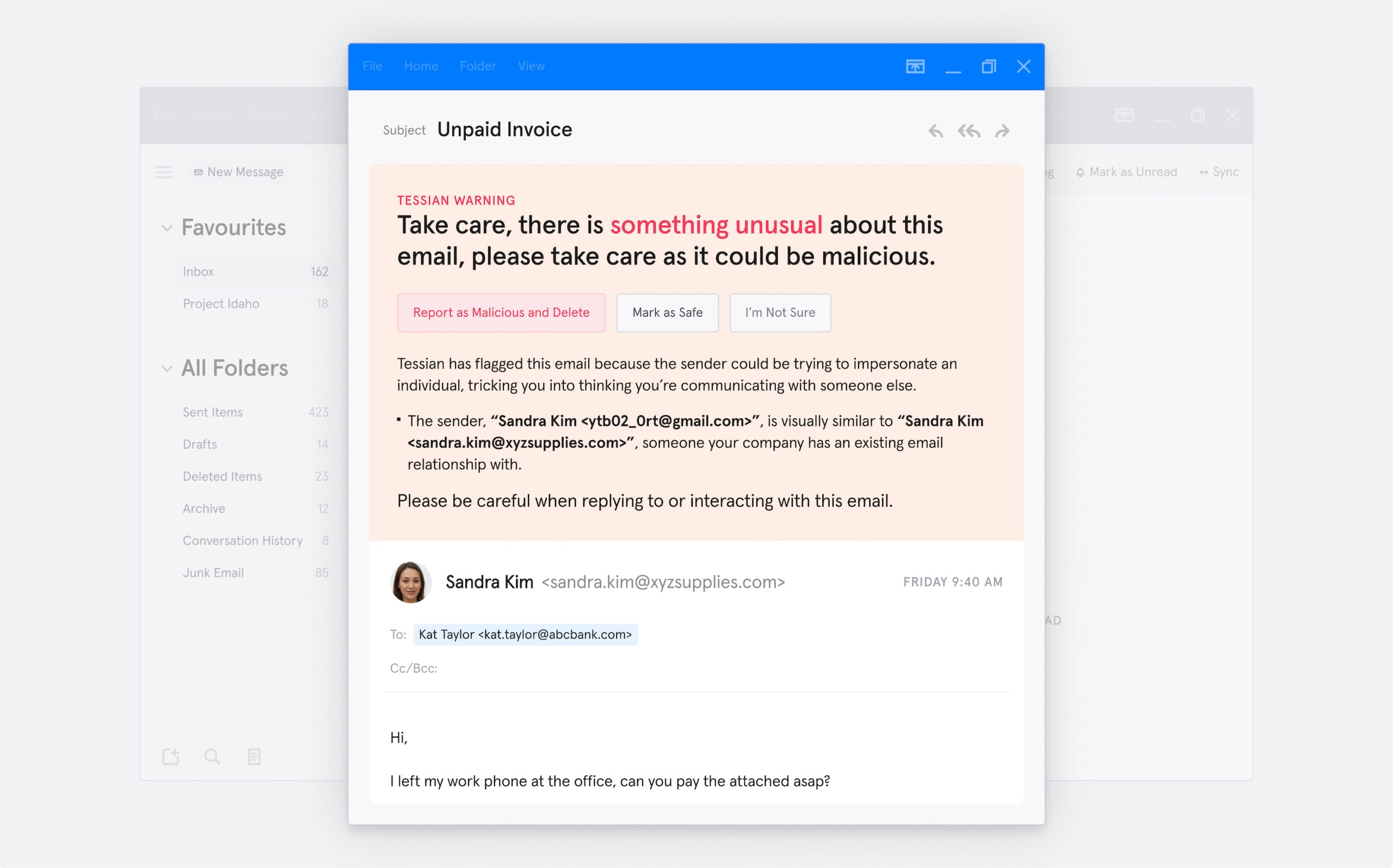
Tessian was able to detect the phishing techniques deployed by the threat actor for this campaign. Tessian recognized the law firm’s domain in the local part of the email address and the name of the chairman in the display name. It also detected suspicious keywords indicative of an urgent call to action, which included “are you available?” and “quick”.
Tessian also detected that the address used by the attacker had not been observed in historical emails sent to anyone at the law firm.
Many of the recipients at the law firm responded to the in-the-moment security warning message from Tessian and confirmed that the email was actually malicious.
All it takes is one click.
This example underscores the relentless pursuit of threat actors, attempting to gain access to an organization’s crown jewels. As attacks become more advanced, it requires a defense-in-depth approach to email security. Leveraging email security solutions that have behavioral detection and in-the-moment security awareness training capabilities is now table stakes to securing your email ecosystem.
Appendix: MITRE ATT&CK Framework
The tactics and techniques used by the threat actor can be inferred up to the point the email was received.
The threat actor carried out reconnaissance activities against the target’s website. Here they identified the key individuals to impersonate and target. Using the people directory available on the website they were able to identify the chairman of the law firm to impersonate via email and get a list of names and email addresses for associates at the firm to target.
After identifying a high ranking member of the firm, the threat actor registered an email account with Gmail. They created an account with a username containing the name of the chairman of the firm as well as the domain used for the firm’s website. They also changed the display name associated with the account to that of the chairman.
With a free email address registered, a senior staff member to impersonate and a list of victims to target, the threat actor sent an email to more than 200 associates at the firm. The email contained a message explaining they were the chairman of the firm and wanted to know if they were available to help them quickly.
The threat actor avoided detection through conventional means by registering a new email address and not including a malicious link or attachment in their initial email. SEGs typically rely on known IOCs to be able to detect malicious activity. Since there was no attachment or URL in this case, there was nothing to scan or lookup the reputation for.
MITRE D3FEND Framework
Most of the techniques used by the threat actor were reconnaissance-based and occured at the pre-compromise phase outside of the scope of typical defenses and controls meaning they could not be easily mitigated without advanced email protection.
Sender reputation analysis can be used to detect unwanted or malicious emails by analyzing information about the sender. This can include information over time such as the number of emails received, number of recipients, number of emails replied to etc.
The problem with this attack is the email address used by the threat actor will likely have been recently registered using a reputable freemail service and would have been unseen to the law firm before. This means there is limited information available to determine the sender reputation. Detection can be done based on the email address having not been seen before; however with legacy email security controls this type of detection can generate high levels of alerts and false positives.
Charles Brook
Threat Intelligence Specialist