Only two things are certain in life, death and taxes. As the 2022 Tax Day rolls around, making a payment to the IRS isn’t the only thing you need to be worried about.
These phishing attacks can take many different forms. In the US, these attacks will use the deadline of Monday, 18 April to file your income tax returns as bait. Meanwhile in the UK, these attacks will use your potential tax refund as bait.
But we’re here to help. Here’s what you need to look out for and what to do in case you’re targeted by Tax Day scams.
What do Tax Day scams look like?
As is the case with other phishing and spear phishing attacks, bad actors will be impersonating trusted brands and authorities and will be, in some way, motivating you to act.
In this article, we’re exploring Tax Day scams that arrive via email. You may also receive phone calls or text messages from bad actors, claiming that you’re being investigated for tax fraud or have an overdue bill. They may also simply request more information from you, like your name and address, or bank account details. You shouldn’t give any of this information away over the phone. Government organizations will never call you or use recorded messages to demand payment.
Now, let’s take a closer look at some real scam examples.
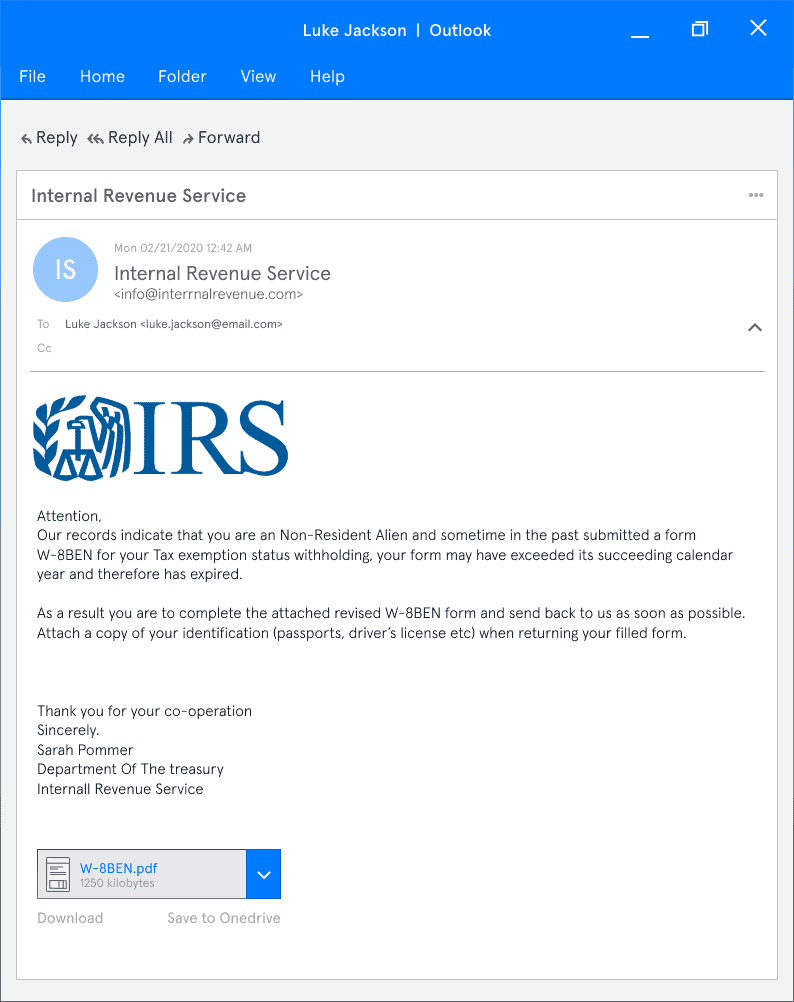
Example 1: IRS Impersonation
What’s wrong with this email?
- The IRS has said they never contact taxpayers by email, so any correspondence “from” them is illegitimate
- There is an extra “r” in “internal” in the sender’s email address
- Email addresses from government agencies will always contain the top-level domain “.gov”
- There are spelling errors and inconsistencies in the text that you wouldn’t expect from a government agency
Example 2: Tax-Preparation Software Impersonation
What’s wrong with this email?
- While the sender’s email address does contain the company name (Fast Tax), the top level domain name (.as) is unusual
- The sender is motivating the target to follow the embedded link by claiming their tax return is incomplete
- Upon hovering over the link, you’ll see the URL is suspicious. Please note, though: A suspicious URL can still take you to a landing page that appears legitimate. These are called malicious websites.
Example 3: HMRC Impersonation
What’s wrong with this email?
- While the Display Name, email template, logos, and language used in the email seem consistent with HMRC, the sender’s email address contains the top-level domain “.net” instead of “.gov.uk”
- Upon hovering over the link, you’ll see the URL is suspicious
Example 4: Client Impersonation
What’s wrong with this email?
- Unfortunately, in this case, there are no obvious giveaways that this is a phishing scam. However, if Joe, the tax accountant in this scenario, knew he hadn’t met or interacted with a woman named Karen Belmont, that could be a warning sign
- Individuals and organizations should always be wary of attachments and should have anti-malware and/or virus protection in place
- This examples demonstrates the importance of having policies in place to verify clients beyond email. And remember, there’s nothing wrong with being extra cautious this time of year.
Example 5: CEO Impersonation
What’s wrong with this email?
- The the sender’s email address (@supplier-xyz.com) is inconsistent with the recipient’s email address (@supplierxyz.com)
- The attacker is impersonating the CEO, hoping that the target will be less likely to question the request; this is a common social engineering tactic
- The attacker is using urgency both in the subject line and the email copy to motivate the target to act quickly
- Because this is a zero-payload attack (an attack that doesn’t rely on a link or attachment to carry malware), anti-malware or anti-virus software wouldn’t detect the scam
Who will be targeted by Tax Day scams?
From the examples above, you can see that cybercriminals will target a range of people with their Tax Day scams. Taxpayers, tax professionals, and businesses are all susceptible and savvy hackers will use different tactics for each.
Here’s what you should look out for.
Taxpayers
- Attackers will be impersonating trusted government agencies like the IRS and HMRC and third-parties like tax professionals and tax software vendors
- Attackers will use coercive language and the threat of missed deadlines or promises of refunds to motivate their targets to act
- Many phishing emails contain a payload; this could be in the form of a malicious link or attachment
Tax Professionals
- Attackers will be impersonating either existing clients/customers or prospects. In either case, they’ll be pretending they need help with their tax return or tax refund
- Attackers will use the lure of new business or the threat of losing a customer to motivate their targets to act
- Many phishing emails contain a payload; this could be in the form of a malicious link or attachment.
Businesses
- Attackers will be impersonating CEOs, HR representatives, Finance Directors, or other individuals or agencies who need access to sensitive tax information
- Attackers are strategic in their impersonations of people in positions of power; people are less likely to question their superiors.
What do I do if I’m targeted by a Tax Day scam?
While it’s true that attackers use different tactics and capitalize on different moments in time to trick their targets, individuals and businesses should always follow the same guidelines if they think they’ve received a phishing email.
- First and foremost, always, always, always check the sender. Confirm that the domain is legitimate and that the Display Name matches the email address. Be wary of any emails that aren’t from a “.gov” address.
- If anything seems unusual, do not follow or click links or download attachments
- Check for spelling errors or formatting issues. Be scrupulous! If anything feels off, proceed cautiously. (See below.
- If the email appears to come from an individual you know and trust, like a colleague, customer, or client, reach out to the individual directly by phone, text or a separate email thread
- If you’re an employee who’s been targeted, contact your line manager and/or IT team. Management should, in turn, warn the larger organization
- The best way to avoid falling victim to one of these scams is to simply not provide any personal information until you verify with 100% certainty that you’re communicating with a genuine agency, organization, or agent. Visit the organization’s website via Google or your preferred search engine, find a support number, and ask them to confirm the request for information is valid.
“The IRS does not initiate contact with taxpayers by email, text message, or other online channels to request personal or financial information.”
More resources
As a security start-up, we’re committed to helping you stay safe. If you’re looking for more information on Tax Day scams, consult the following government websites.
- Advice from the IRS
- Advice from HMRC
Looking for more advice about scams? Sign-up to our newsletter below to get articles just like this, straight to your inbox.