If you’re familiar with phishing or malware, you’ve likely heard of “malicious websites”. But, do you know how to spot one? In this article, we’ll answer four key questions (and provide plenty of examples).
- What is a malicious website?
- How many websites are malicious?
- What red flags should I look out for to spot a malicious website?
- How can I avoid visiting or interacting with malicious websites?
So, to start, let’s define what exactly a malicious website is.
What is a malicious website?
A malicious website is any website that’s been designed to cause harm. In this article, we’ll focus on phishing websites and malware websites. A phishing website – sometimes called a “spoof” or “lookalike” website – steals your data. Phishing websites look like legitimate websites. But, when visitors are prompted to enter login credentials, personal information, or credit card details, the data is directed to cybercriminals.
Looking for an example? Tessian researchers discovered 75 domains spoofing websites related to mail-in voting in August 2020. For more information, read this article: How to Avoid Falling victim to Voting Scams in the 2020 Election. In this case, attackers were after personally identifiable information (PII) and credit card details.
Once a phishing website collects your data, it can be used in hacking operations and further phishing attacks, or sold on the dark web. A malware website, on the other hand, installs malicious software on your device. While this could happen after the visitor downloads an application or file, it can also happen without the visitor even noticing.
Why deploy malware? Malicious software can serve many different purposes, including extracting data from a person’s device, taking control of the device, or using the device as an entry point into a network. But phishing and malware sites aren’t the only problems.
Other websites, such as fake news and disinformation websites, might also be considered malicious websites. These sites aim to spread discord, affect election outcomes, and disrupt the activities of human rights groups.
How common are malicious websites?
It’s hard to say exactly how many malicious websites are out there. But one thing we do know is that malicious websites — particularly phishing websites — are popping up more and more frequently. One source that can help us understand the prevalence of malicious websites is Google’s Safe Browsing reports.
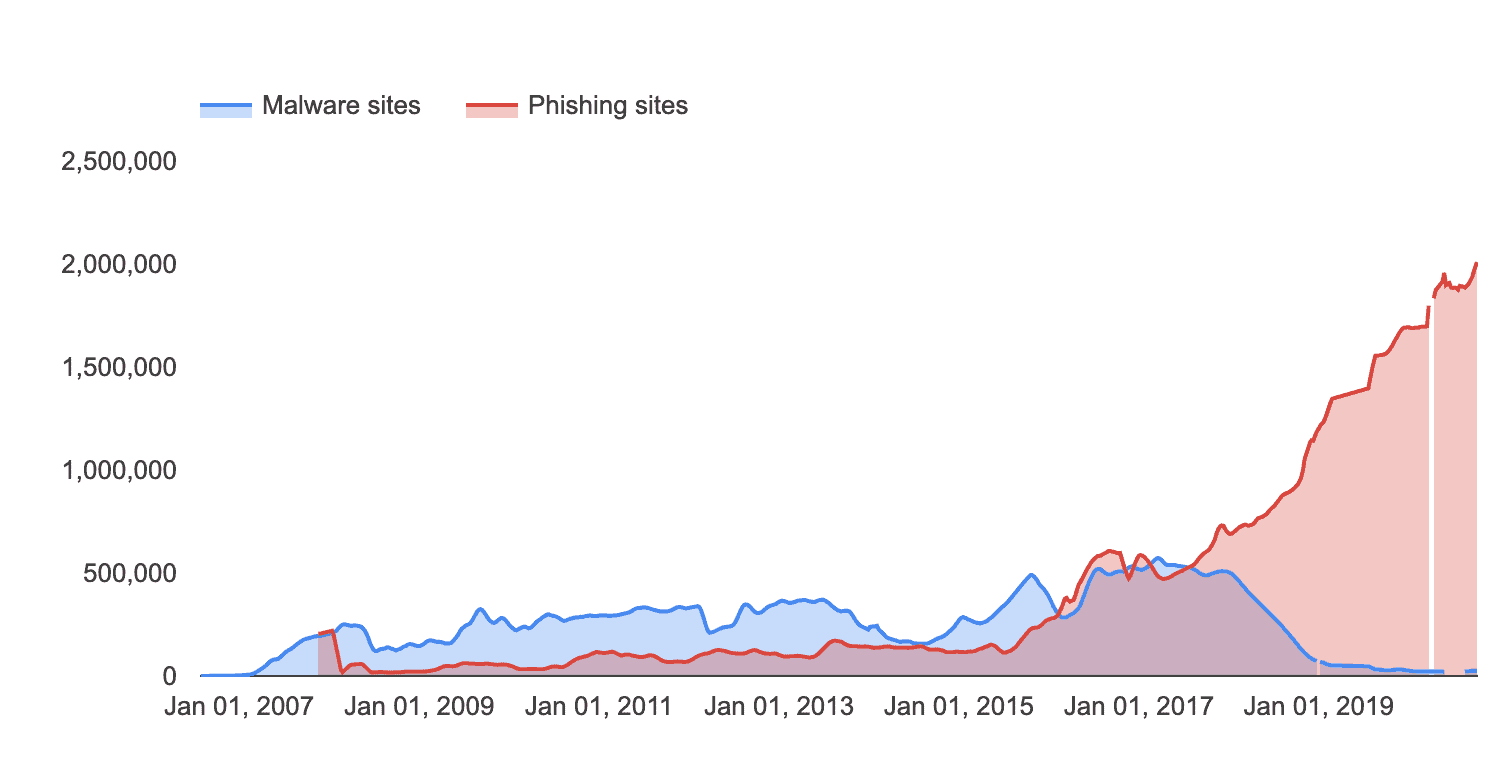
According to Google’s stats, phishing websites are increasingly common, whereas malware sites are less likely to be favored by cybercriminals.
Data from Google's Safe Browsing Report shows the number of phishing sites has increased between 2007 and 2020 while the number of malware sites has started to dip.
In September 2020, Google counted nearly 1,960,000 phishing websites. This is up from around 68,000 in September 2010 — an increase of nearly 2800%. But malware sites have actually decreased in prevalence according to Google, with around 24.500 counted in September 2020, down from 78,500 in September 2010.
Venafi’s 2018 research supports the view that phishing sites are on the increase. In a study of domains associated with major retailers across five countries, Venafi found there were:
- Twice as many spoof retail websites as genuine retail websites
- 12,000 spoof domains associated with one US retailer
Real-World Example: BAHAMUT
Let’s look at a real-life example of how criminals use malicious websites to dupe their targets into handing over data. Research from BlackBerry, published in 2020, studied the activities of a cybercrime syndicate known as BAHAMUT. The group targets consumers, businesses, and government officials via phishing emails, fake mobile apps, and a “staggering” network of malicious websites.
Among many other activities, BAHAMUT set up convincing-looking malicious “news” websites that directly copied headlines from genuine sources. Links on these sites redirected to phishing websites that harvested Google, Yahoo, Microsoft, and Telegram users’ credentials.
BAHAMUT also set up websites designed to distribute a series of malicious mobile apps. Once downloaded, these malicious apps set up a “backdoor” on the target device, allowing the group to track the user’s activities and location, and access the user’s files.
Perhaps the most alarming aspect of BAHAMUT’s activities is the convincing nature of the group’s fake websites. Some of these sites were previously well-established, legitimate news sources, whose domains were re-registered and used as vehicles for cybercrime.
Telltale signs of a malicious website
As we can see from the example of BAHAMUT, it’s not always easy to identify a malicious website. Some may display no obvious signs that they will steal your credentials or distribute malware. But, there are some traits common to many malicious websites. For example:
- The website automatically asks you to run software or download a file when you’re not expecting to do so.
- The website tells you that your device is infected with malware or that your browser extensions or software are out-of-date.
- The website claims you have won a prize and requests your personal information to claim it.
These are outdated tactics, and most sophisticated malicious websites will not be so transparent. There can also be technical indications that a website is fake. For example:
- The URL looks suspicious. https://google.com is safe. https://google.[something].com is not. This is a subdomain of [something].com — which could be a malicious website.
- The site does not use https. Most sites use https, rather than http, which indicates that they are protected by an SSL certificate. However, some sites have not yet made the upgrade to https, and not all https URLs are safe.
It can be very difficult to tell whether you are visiting a malicious website. The best tactic is to avoid arriving at a malicious website in the first place. But how?
How to avoid visiting a malicious website
When it comes to avoiding the harms associated with malicious websites — security and business leaders understand that prevention is better than cure. And, while it is possible to stumble upon a malicious website while browsing the web, search engines, like Google take steps to remove malicious sites from their search results. They can’t catch them all, though.
But it’s important to note that it’s far more common to end up on a malicious website after receiving a phishing email. Phishing emails are extremely common — 88% of organizations experienced spear phishing (targeted phishing attacks) in 2019.
Phishing emails can include links to malicious websites. It’s easy to fall for this type of scam — a phishing email can appear to come from a trusted person, and might look like the sort of correspondence you receive from that person regularly.
That means identifying phishing emails may be more important than identifying malicious websites. If you’re looking for tips, we’ve put together this guide (including an infographic): What Does a Spear Phishing Email Look Like.
Note: Phishing can also take place via social media, phone, or SMS, but 96% of phishing attacks arrive via email. That’s why email is the threat vector security leaders are most concerned about. Email security solutions can help.
How can Tessian help?
Tessian Defender detects and prevents advanced impersonation attacks including spear phishing. If employees don’t fall for the phishing email, they won’t land on the malicious website.
How? Tessian’s machine learning algorithms learn from historical email data to understand specific user relationships and the context behind each email. When an email lands in your inbox, Tessian Defender automatically analyzes millions of data points, including the email address, Display Name, subject line and body copy. If anything seems “off”, it’ll be flagged.
To learn more about how tools like Tessian Defender can prevent spear phishing attacks, speak to one of our experts and request a demo today.