88% of organizations around the world experienced spear phishing attempts in 2019. And, while security leaders are working hard to train their employees to spot these advanced impersonation attacks, every email looks different.
A hacker could be impersonating your CEO or a client. They could be asking for a wire transfer or a spreadsheet. And malware can be distributed via a link or an attachment. But it’s not all bad news. While – yes – each email is different, there are four commonalities in virtually all spear phishing emails.
Before we go into more detail about these four red flags, let’s get into the mind of a hacker.
What do hackers consider when creating a spear phishing attack?
Hackers prey on their target’s psychological vulnerabilities. For example, immediately after the outbreak of COVID-19, we saw a spike in spear phishing attacks impersonating health organizations, insurance companies, government agencies, and remote-access tools. Why? Because people were stressed, anxious, and distracted and therefore more likely to trust emails containing “helpful” information and take the bait.
We explore this in detail in our report, The Psychology of Human Error. While people cite distraction as the top reason for falling for phishing attacks, the perceived legitimacy of the email was a close second. Looking at real-world examples can help. Below are five articles that outline recent scams, including images of the emails.
- COVID-19: Real-Life Examples of Opportunistic Phishing Emails
- Everything You Need to Know About Tax Day Scams 2020
- Spotting the Stimulus Check Scams
- How to Spot and Avoid 2020 Census Scams
- Look Out For Back to School Scams
Now that you know broadly what to look for and what makes you more vulnerable, let’s take a deeper dive into the four things you should carefully inspect before replying to an email.
4 Things to Inspect Before Replying to An Email
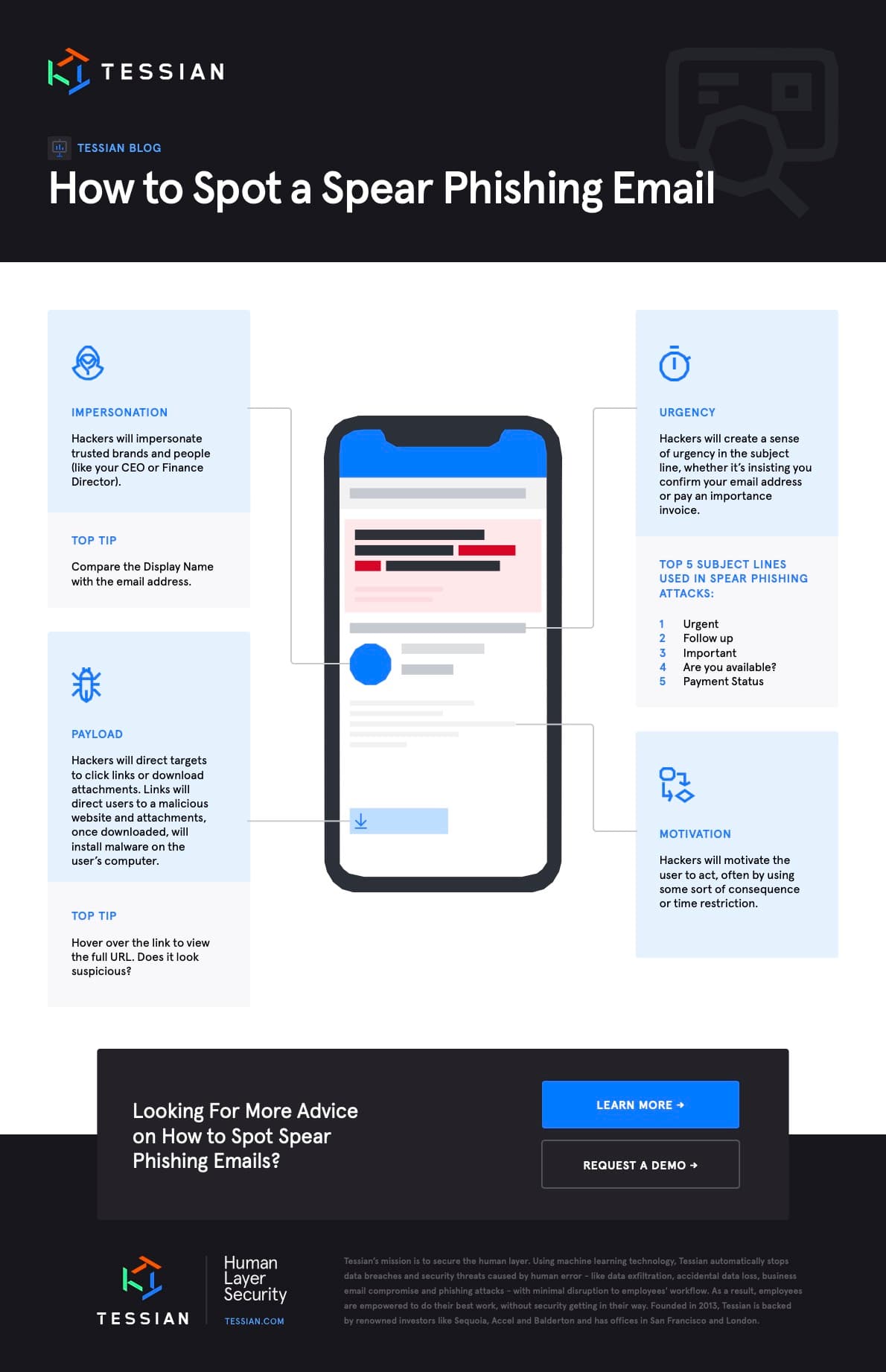
The Display Name and Email Address
The first thing you should do is look at the Display Name and the email address. Do they match? Do you recognize the person and/or organization? Have you corresponded with them before?It’s important to note that some impersonations are easier to spot than others. For example, in the example below, the Display Name (zoom_meeting@tessian.com) is vastly different from the email address (fd29eaab47504bfa8bd773ee581bc7d4@tessian.com).
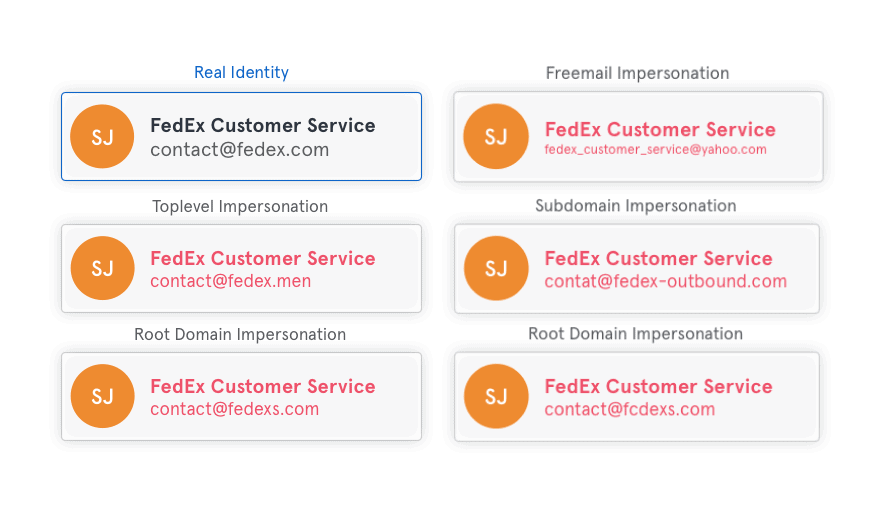
But, hackers can make slight changes to the domain that can be indiscernible unless the target is really looking for it. To make it easier to understand, we’ll use FedEx as an example. In the chart below you’ll see five different types of impersonations. For more information about domain impersonations, read this article: Inside Email Impersonation: Why Domain Name Spoofs Could Be Your Biggest Risk
The bottom line: Take the time to look closely at the sender’s information.
The Subject Line
As we’ve mentioned, hackers exploit the psychological vulnerabilities of their targets. It makes sense, then, that they’ll try to create a sense of urgency in the subject line.
Here is a list of the Top 5 subject lines used in spear phishing attacks:
- Urgent
- Follow up
- Important
- Are you available?
- Payment Status
And, when it comes to Business Email Compromise attacks, the Top 5 subject lines are:
- Urgent
- Request
- Important
- Payment
- Attention
While – yes – these subject lines can certainly appear in legitimate emails, you should exercise caution when responding.
Attachments and Links
Hackers will often direct their targets to follow a link or download an attachment. Links will direct users to a malicious website and attachments, once downloaded, will install malware on the user’s computer. These are called payloads. How can you spot one? While links may often look inconspicuous (especially when they’re hyperlinked to text) if you hover over them, you’ll be able to see the full URL. Look out for strange characters, unfamiliar domains, and redirects.
Unfortunately, you can’t spot a malicious attachment as easily. Your best bet, then, is to avoid downloading any attachments unless you trust the source. Note: Not all spear phishing emails contain a payload. Hackers can also request a wire transfer or simply build rapport with their target before making a request down the line.
The Body Copy
Just like the subject line will create a sense of urgency, the body copy of the email will generally motivate the target to act. Look out for language that suggests there will be a consequence if you don’t act quickly. For example, a hacker may say that if a payment isn’t made within 2 hours, you’ll lose a customer. Or, if you don’t confirm your email address within 24 hours, your account will be deactivated.
While spear phishing emails are generally carefully crafted, spelling errors and typos can also be giveaways. Likewise, you may notice language you wouldn’t expect from the alleged sender.For example, if an email appears to be sent from your CEO, but the copy doesn’t match previous emails from him or her, this could suggest that the email is a spear phishing attack.
To learn more about how tools like Tessian Defender can prevent spear phishing attacks, speak to one of our experts and request a demo today.
What to do if an email if you think an email is suspicious
Now that you know what to look out for, what do you do if you think you’ve caught a phish?
- If anything seems unusual, do not follow or click links or download attachments.
- If the email appears to be from a government organization or another trusted institution, visit their website via Google or your preferred search engine, find a support number, and ask them to confirm whether the communication is valid.
- If the email appears to come from someone you know and trust, like a colleague, reach out to the individual directly by phone, Slack, or a separate email thread. Rest assured, it’s better to confirm and proceed confidently than the alternative.
- Contact your line manager and/or IT team immediately and report the email.
But it’s not fair to leave people as the last line of defense. Even the most tech-savvy people can fall for spear phishing attacks. Case in point: Last month, The SANS institute – a global cybersecurity training and certifications organization – revealed that nearly 30,000 accounts of PII were compromised in a phishing attack that convinced an end-user to install a self-hiding and malicious Office 365 add-on.
That means organizations should invest in technology that can detect and prevent these threats.
Tessian can help detect and prevent spear phishing attacks
Unlike spam filters and Secure Email Gateways (SEGs) which can stop bulk phishing attacks, Tessian Defender can detect and prevent a wide range of impersonations, spanning more obvious, payload-based attacks to subtle, social-engineered ones.
How? Tessian’s machine learning algorithms learn from historical email data to understand specific user relationships and the context behind each email. When an email lands in your inbox, Tessian Defender automatically analyzes millions of data points, including the email address, Display Name, subject line and body copy.