Infographics
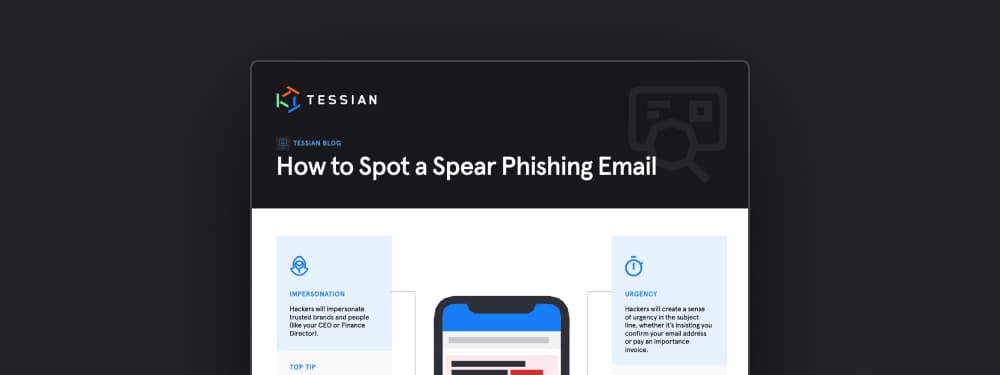
Infographic: How to Spot a Phishing Email: 4 Red Flags
While bulk, “spray and pray” phishing emails may contain easy-to-spot spelling errors and domain spoofs, spear phishing emails and other advanced impersonation attacks are a lot harder to identify.
That’s why we’ve put together this infographic outlining how to spot a spear phishing email.
Red flags including:
- Impersonation
- Urgency
- Motivation
- A payload
Bonus: Learn the five most frequently used subject lines in phishing emails.
Want more information about spear phishing emails and how to know when you’re being targeted? Read the article: What Does a Spear Phishing Email Look Like?