-
What is Business Email Compromise?
Business Email Compromise (BEC) is a cyberattack involving the hacking, spoofing, or impersonation of a business email address. The victim of a BEC attack receives an email that appears to come from a trusted business. The email looks and feels genuine. But it typically contains a phishing link, a malicious attachment, or a request to transfer money to the attacker.
In this article, we’ll look at why cybercriminals use BEC, how it works, and why it remains a serious problem. Looking for examples of BEC attacks or information about how to prevent business email compromise instead? Check out these pages instead:
- How to overcome this multi-billion dollar threat
- Real-world examples of Business Email Compromise
Why compromise a business email account?
BEC is a tried-and-tested cyberattack method that costs consumers and businesses billions every year. So what makes BEC such a prevalent cybercrime technique? Simply put: cybercriminals use BEC as a way to make social engineering attacks more effective.
A social engineering attack is any form of cybercrime involving impersonation. The attacker pretends to be a trusted person so that the target does what they’re told. According to Verizon’s 2021 Data Breach Investigation Report (DBIR), BEC is the second-most common type of social engineering attack. In a BEC or other social engineering attack, the threat actor pretends to be a trusted person so that the target does what they’re told.
Here are some examples of social engineering attacks that can involve BEC:
- Phishing: A social engineering attack conducted via email (smishing and vishing are social engineering attacks conducted via SMS and voice respectively)
- CEO fraud: A phishing attack where the attack impersonates a company executive
- Whaling: A phishing attack targeting a corporate executive
- Wire transfer fraud: A phishing attack where the attacker persuades the target to transfer money to their account
All these social engineering attacks involve some sort of impersonation. Fraudsters use every tool available to make their impersonation more convincing. And one of the best tools available is a genuine — or genuine looking — business email address.
BEC attacks target both individuals and businesses and the attacker will (generally) use BEC to gain access to one of the following:
- Money. According to Verizon’s 2021 Data Breach Investigation Report, the vast majority of cyberattacks are financially motivated.
- Account credentials: A fraudulent email might contain a phishing link leading to a fake account login page. The FBI warns that this BEC variant is on the rise.
- Gift certificates: BEC attackers can persuade their target to purchase gift certificates rather than transferring them money. The FTC put out a warning about this increasingly common type of scam in May 2021.
Now you know why cybercriminals launch BEC attacks, we’re going to look at how they do it.
How does BEC work?
There are various competing definitions of BEC — so before we explain the process, let’s clarify what we mean when we use this term. BEC attack is any phishing attack where the target believes they have received an email from a genuine business. As noted by Verizon, “BEC doesn’t even have to compromise a business email address. Your.CEO@davesmailservice.com comes up all too often in our dataset.”
There are several methods that a cybercriminal can use to achieve this, including:
- Email impersonation
- Email spoofing
- Email account takeover
Let’s look at each of these techniques.
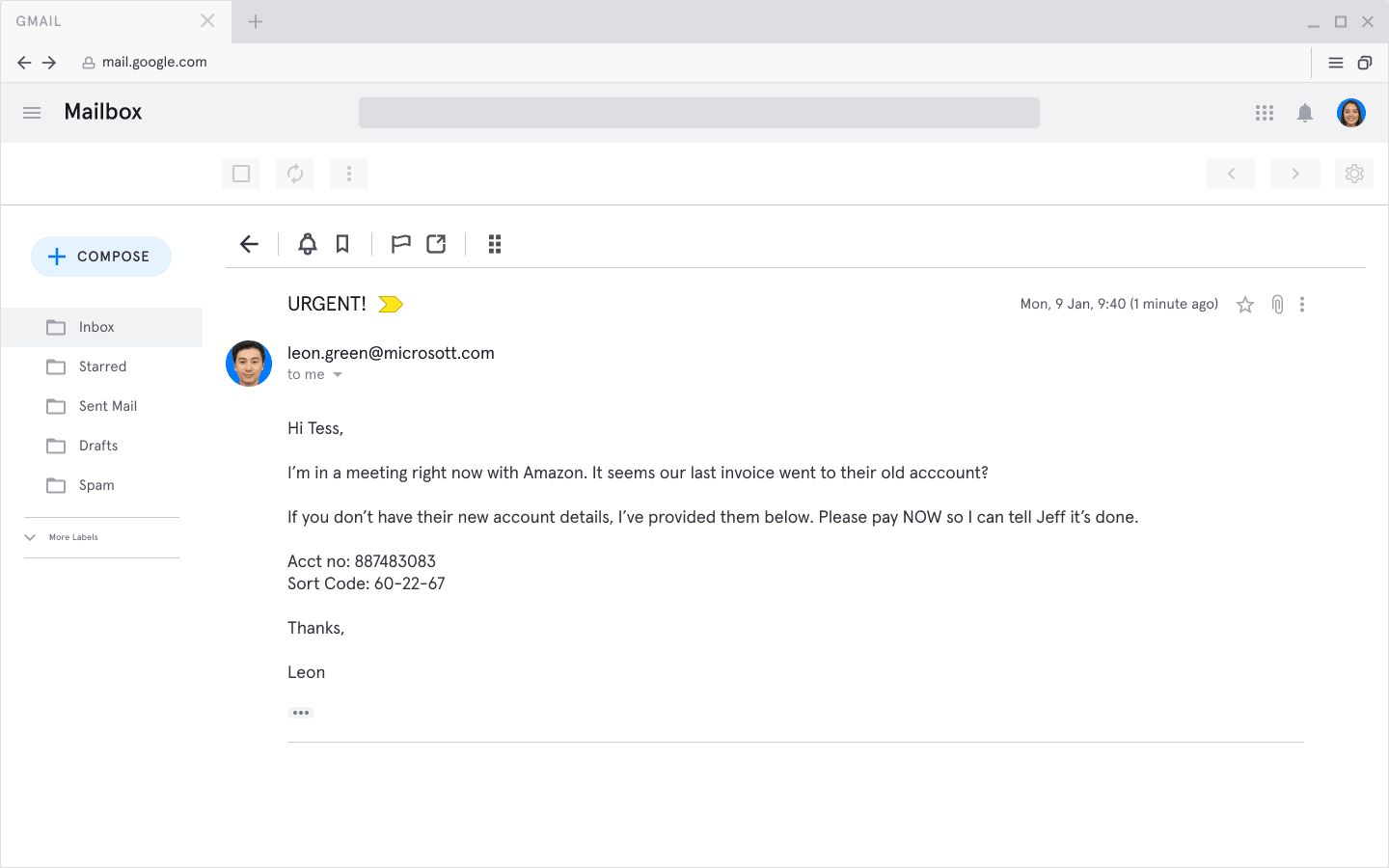
Email impersonation is where the attacker sets up an email account that looks like a business email account. Here’s an example:
In this example, the attacker is impersonating Leon Green. You'll notice the domain is microsott.com instead of microsoft.com
In this case, we can imagine Leon Green really is Tess’ boss and that an invoice for Amazon really is due to be paid. This information is easy enough to find online. But, note that the sender’s email address is “leon.green@micrott.com”. If you look carefully, you’ll see Microsoft is misspelled.
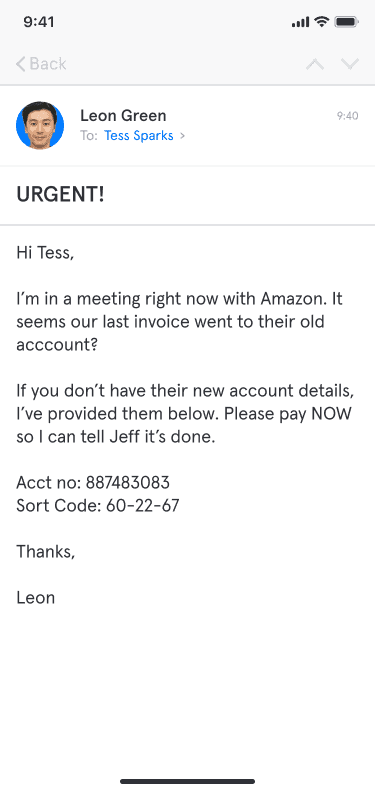
Many people miss small details like this, especially if looking on their phones. Worse still, mobile email clients typically only show the sender’s display name and hide their email address.
On mobile devices, only the sender's display name is shown. This makes it even easier for attackers to dupe their targets.
Email spoofing is where the attacker modifies an email’s envelope and header. The receiving mail server thinks the email came from a corporate domain and the recipient’s email client displays incorrect sender information. You can read more about email spoofing – and see an example of a spoofed email header – in this article: What is Email Spoofing? How Does Email Spoofing Work?
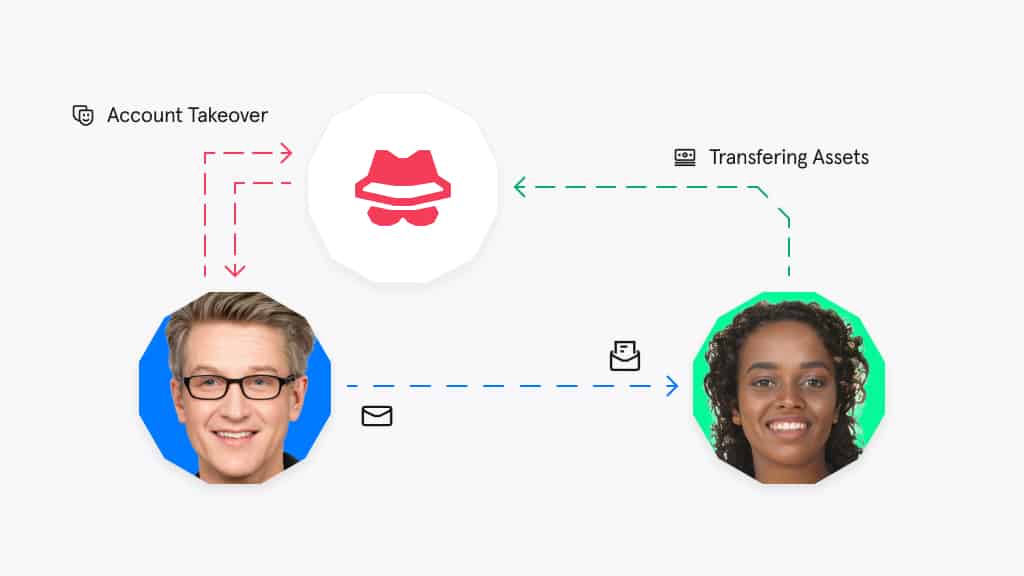
In account takeover (ATO), the attacker gains access to a corporate email account, whether via hacking or by using stolen account credentials. They gather information about the user’s contacts, email style, and personal data — then they use the account to send a phishing email.
The above diagram shows how an attacker takes over the account of a trusted third-party in order to gain access to the target organization.
Application impersonation
In recent years, there’s been a rise in the number of scams that use “application impersonation”. In an application impersonation attack, the target receives an email that appears to be an automated notification sent via a workplace application, such as Zoom, Office 365, or Gmail.
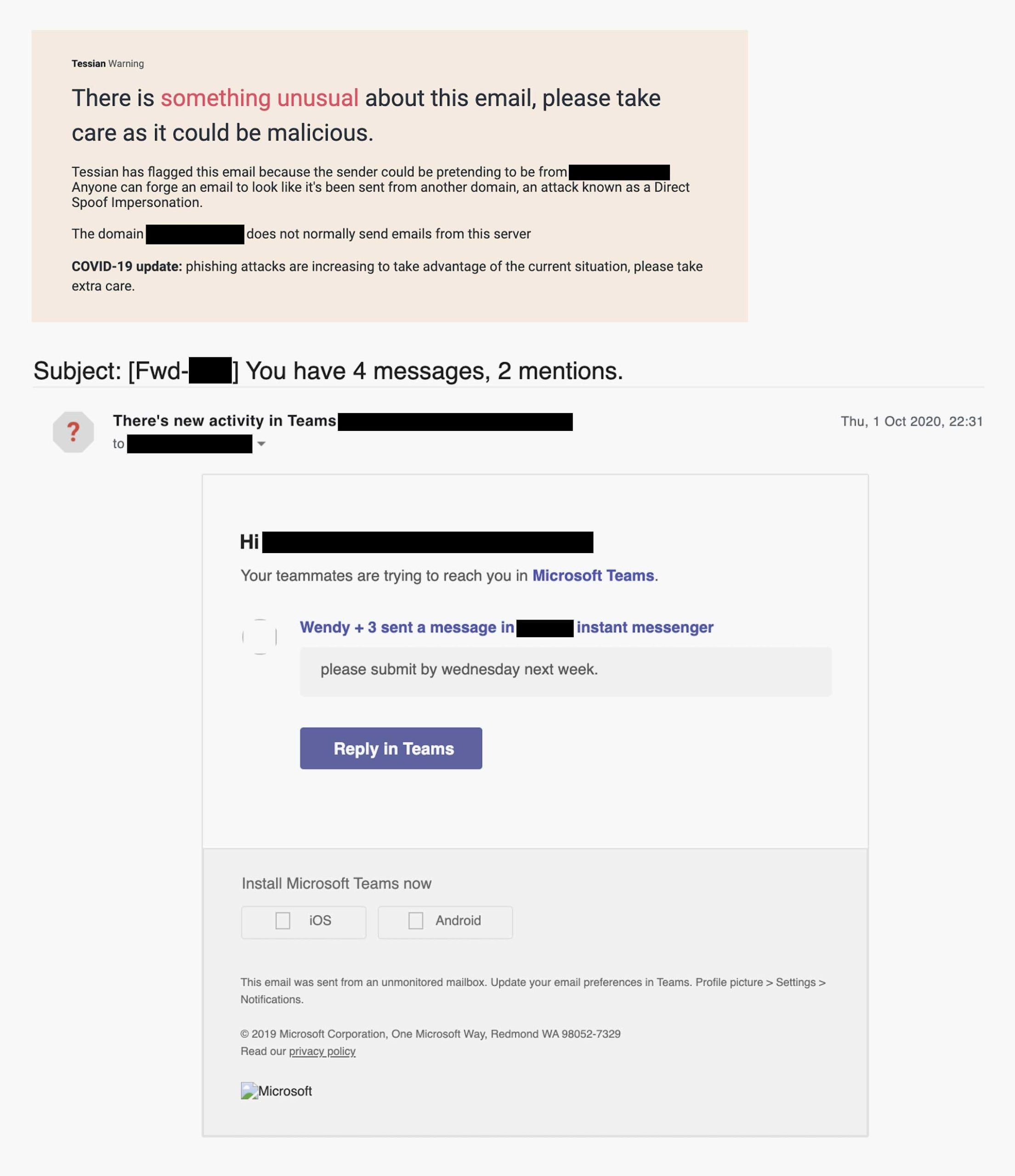
Here’s an example—a phishing email masquerading as a notification from Microsoft Teams, which was detected and prevented by Tessian Defender:
This is an example of application impersonation (Microsoft Teams) detected and prevented by Tessian Defender.
Clicking the link will take the user to a sign-in page which will harvest their login credentials. Impersonation of automated business emails is an increasingly common threat. Research from GreatHorn suggests that business-related applications accounted for around 45% of impersonation-related attacks in early 2021.
How serious is BEC?
We know BEC is a common cyberattack method. But how many businesses are affected, and how badly? Because many BEC attacks go unnoticed — and because different organizations use different definitions of BEC — there’s no simple answer. So what do we know about the prevalence of BEC? The best source of cybercrime statistics comes from the FBI’s Internet Crime Complaint Center (IC3), which reports that:
- Between 2016 and 2020, the IC3 recorded 185,718 BEC incidents worldwide, resulting in losses totaling over $28 billion.
- In 2020, losses from BEC exceeded $1.8 billion—a fourfold increase since 2016.
- The number of BEC incidents went up by 61% between 2016 and 2020.
Next steps
We’ve looked at the different types of BEC, how a BEC attack works, and how serious and pervasive this form of cybercrime has become. Next, let’s look at examples of BEC attacks. This will help you learn from the experiences of other organizations. This will help you learn from the experiences of other organizations. Or you can learn how Tessian prevents BEC attacks here.