Cyber attacks are getting more sophisticated and more targeted. In this Tessian in Action update we explore how an attack got through legacy security solutions, but not Tessian.
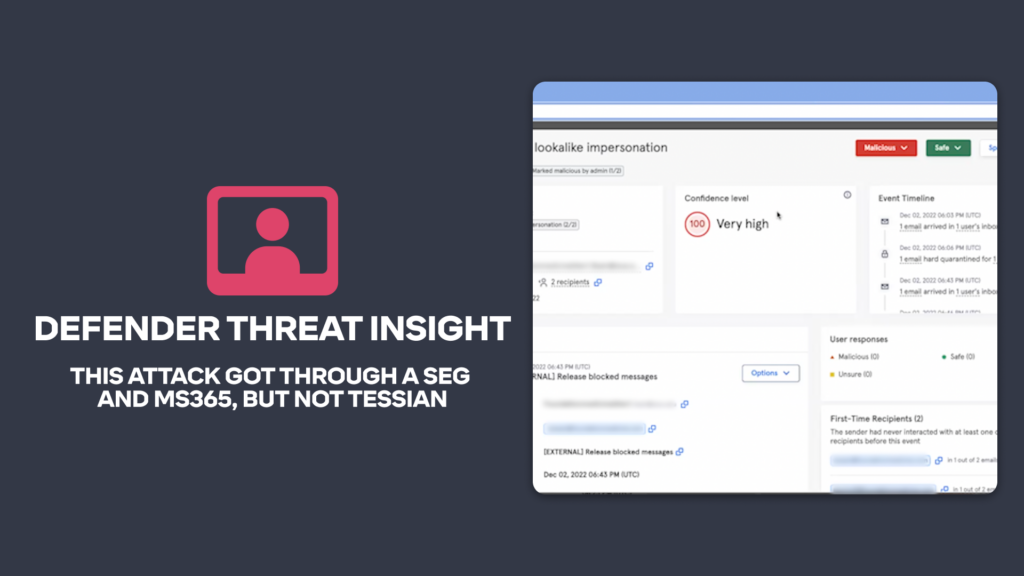
Legacy security solutions just aren’t able to combat advanced threats over email the way that Integrated Cloud Email Solutions can. At Tessian, we’re seeing more and more attacks bypass traditional secure email gateways only to be stopped by our platform. The attack below sailed right through the client’s SEG and their Microsoft 365 defenses, only to be flagged by Tessian. The client, a medical firm, handles highly sensitive data and personal identifiable information. Fines from PII data breaches can be huge. In February 2023 Arizona-based Banner Health was fined $1,250,000 following a 2016 breach.
The target of the attack
The attackers had clearly done their research, as this attack was specifically targeted at the client’s Chief Legal Officer, and one other senior member of the legal team. They were both targeted with a malicious URL sent from a look alike domain. The timing of the attack was 12-1 UTC, which was in the morning of the client’s location, perhaps in an attempt to catch them early and be top of their inbox.
Stopped dead in its tracks
This attack was able to get past the client’s SEG and MS365 but Tessian flagged it as an impersonation attack. Tessian also identified the URL as malicious, and the fact it was a first time sender. Tessian’s Behavioral Intelligence models detected additional anomalies increasing our confidence score to 100/100. Consequently, this email never reached either of the recipients. The security team at the organization are well aware that attacks against their exec team can have devastating consequences.
In fact, the security team that highlighted this attack to Tessian are highly active with the Tessian portal, and so quarantined it themselves, but had they not, Tessian Defender would have hard-quarantined this email or displayed a warning message to end users, coaching them and raising their security awareness ‘in the moment’.
It’s situations exactly like this that more and more firms are facing. Tessian was built exactly to stop these kinds of highly targeted attacks that slip by existing and legacy solutions. If you’d like to see how Tessian can better protect your organization, find out more with our Microsoft + Tessian Solutions Guide.
Tessian Threat Engineering Group
Tessian Threat Engineering Group