Cybersecurity incidents have been identified as the leading global risk for businesses in 2023. And why does securing your email matter more than ever? Because email is the leading threat vector for a breach – responsible for up to 90% of all breaches.
A simpler, bygone world
Email security has come a long way since its first inception around the year 2000. The greatest external threats facing on-premise mail servers at the time was bulk unsolicited mail and spam. The other big concern was ensuring some form of disaster risk redundancy in case the physical location that stored the mail servers was hit by a disaster like a flood or fire.
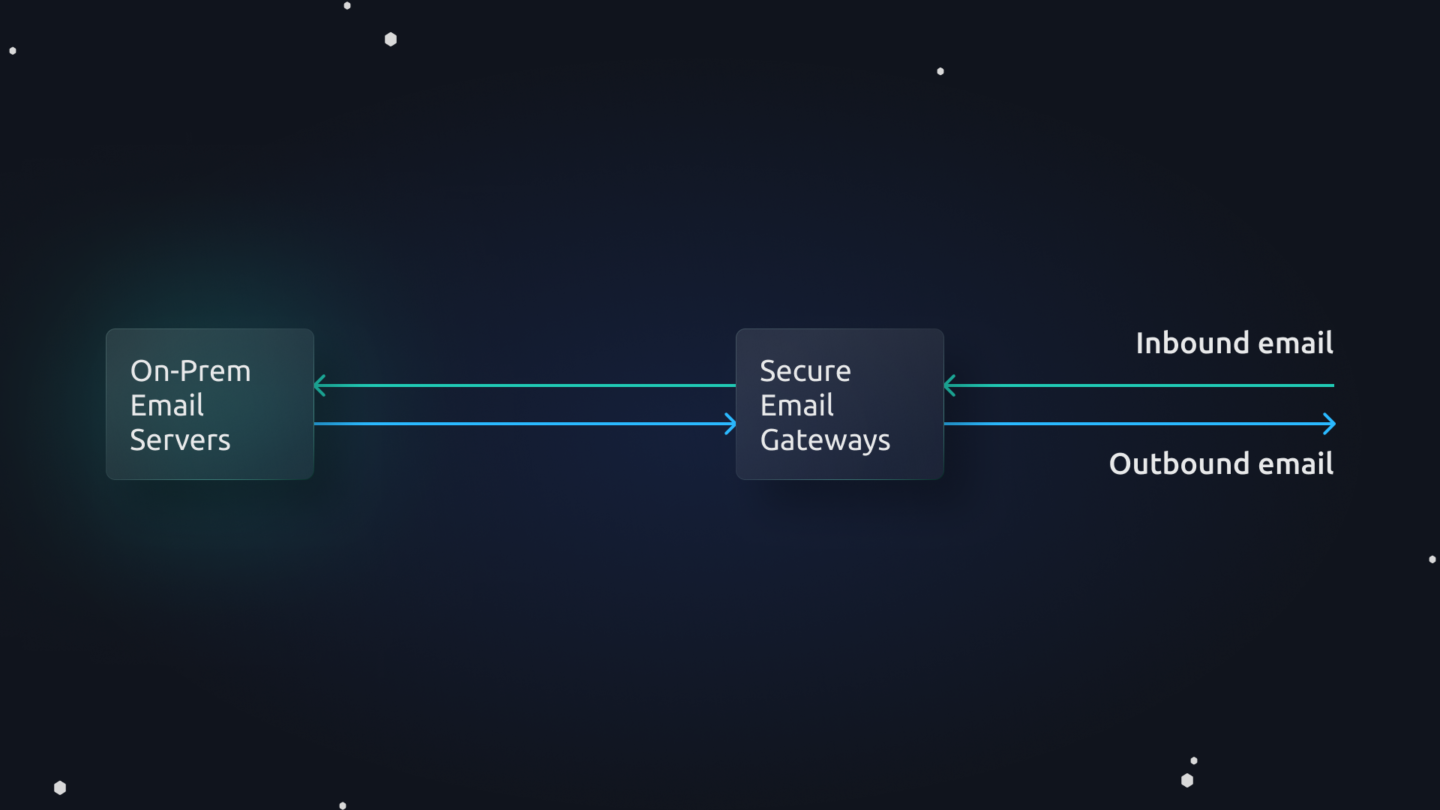
Built for an on-premise world, Secure Email Gateways (SEGs) were focused on solving pretty specific problems. Some vendors focused on filtering spam while others focused on ensuring email communication continually.
Enter the cloud
Public cloud adoption started shortly after this period, however it is only in recent years that it has accelerated, displacing on-premise data centers as the new IT infrastructure of choice. Gartner predicts by 2025, 85% of organizations will embrace a cloud-first principle, and 95% of new digital workloads will be deployed in cloud-native platforms – up from 30% in 2021.
The accelerated cloud adoption is already starting to pose fundamental questions up and down the IT stack, with the efficacy of security solutions developed for an on-premise world, starting to be drawn into question.
The effectiveness of legacy approaches to email security in particular, has been in the crosshairs for quite some time. This is largely due to the declining effectiveness of Secure Email Gateway (SEG) and the pervasiveness of threats hitting inboxes, with email responsible for over 90% of cyber attacks.
More specifically, SEG security effectiveness is declining for two reasons:
- SEGs rely on static, signature and rule-based approaches that are ineffective in safeguarding email users and data from advanced threats such as spear phishing attacks.
- The majority of enterprises have adopted cloud hosted productivity suites such as Microsoft 365, which natively provide SEG capabilities including malware, phishing and URL protection – resulting in duplication of capabilities, increasing cost and complexity, without the benefit of improved security.
Once a threat actor is able to bypass the SEG, they effectively have unmitigated access to carry out their threat campaign. This can (and often does) include Account Takeover (ATO), deploying exploit kits or more damagingly, delivering ransomware. And to compound matters, little protection is offered against insider threats – a growing concern.
The powerful capabilities (and shortcomings) of Microsoft
Microsoft 365, which includes Exchange Online Protection (EOP) and Microsoft 365 Defender for Office, provides a reasonable degree of email security that effectively makes the legacy SEG redundant.
M365 on E5 licensing provides the following capabilities:
- Anti-malware protection
- Anti-phishing protection
- Anti-spam protection
- Data Loss Prevention for email, files and for collaboration platforms such as Sharepoint, OneDrive
- Insider risk protection
- URL rewriting and time-click protection (Safe Links)
- Attachment sandboxing (Safe Attachments)
- Message encryption via issued PKI
- Audit logging
- Investigate and Respond
- Quarantine
- Exchange archiving
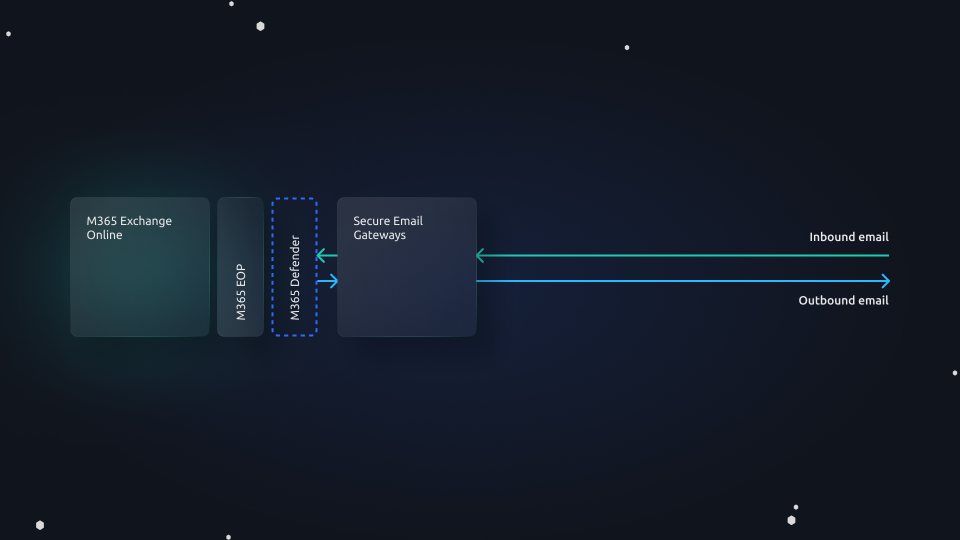
Microsoft alone, however, does not guarantee against advanced email threats. Significant gaps remain in Microsoft’s ability to protect against advanced social engineering campaigns that can result in business email compromise (BEC), ATO, or zero day exploitation. And this is why these shortcomings are also reflected in Microsoft’s Service Level Agreement (SLA) exclusions, for example excluding guarantees against zero day exploits and phishing in non-English languages. Its insider risk capabilities and ability to prevent data loss on email too are limited
Microsoft + Tessian = Comprehensive security
This is where an intelligent cybersecurity solution like Tessian Cloud Email Security Platform comes into play, providing advanced email threat protection and insider risk protection on email.
With Tessian, no mail exchange (MX) records need to be changed. Tessian is able to construct a historical user email pattern map of all email behavior in the organization. The algorithm is then able to detect and prevent threats that Microsoft or SEGs have failed to detect.
This dynamic protection improves with each threat that is prevented, and unlike the in-line static nature of SEGs, it ensures 24/7 real time protection against all attack vectors, including insider threats. That is why the leading enterprises are opting for displacing their legacy SEG and augmenting Microsoft’s native security capabilities with Tessian
Tessian capabilities include:
- Advanced Spear Phishing Protection
- Advanced Attachment and URL Protection
- Internal Impersonation & CEO Fraud
- Advanced Spoof Detection
- Counterparty & Vendor Impersonation
- Brand Impersonation
- Account Takeover
- Invoice Fraud
- Bulk Remediation
- Automated Quarantine
- Threat Intelligence
- Advanced Insider Risk and Data Loss Prevention
“We were having trouble with rule-based solutions and identifying email threats. You could spend hours trying to configure them to their optimal level and still have an issue with false positives. We needed an intelligent solution that could identify and pinpoint these threats without bombarding the users with false positive alerts.
”
Richard Mullins
IT Security Engineer at Pennington Manches Cooper
Improved SOC efficiency with intelligent risk mitigation
Tessian clients also see significant efficiency gains in the SOC due to the high degree of automating triage and the enablement of a distilled view on the threats that matter – finding that needle in the haystack, in real time and in context.
For example, with one-click, SOC analysts can bulk remediate high volume phishing campaigns (aka burst attacks) that are targeting the organization as they happen. Suspicious emails are also automatically quarantined, with threat remediation context provided.
The platform provides a single pane of glass, giving security and risk leaders visibility of how cybersecurity risk is trending in their organization and the types of threats thwarted, down to individual employee-level risk scoring.
Context aware security awareness training
The context-aware security capability of Tessian extends to providing in-the-moment security awareness coaching to employees. The real-time security notifications flag suspicious and malicious emails received, offer a clear explanation, and coach employees towards safer behavior.
Stopping threats, reducing cost and complexity
Tessian’s advanced protection and insider risk capability frees security teams to focus on mission critical tasks. Legacy email security approaches relying on SEGs simply no longer have a place in an increasingly crowded cybersecurity stack. By leveraging Microsoft 365’s native capability together with Tessian, presents an opportunity for security leaders to improve security while reducing cost and complexity.
“After so many years using Mimecast, we knew its strengths and weaknesses and we had identified a clear gap. We wanted to fill that gap in the least intrusive way possible. After evaluating various tools, Tessian was a no-brainer.
”
Associate Director of Information Security at a Biopharmaceutical company
Don’t just hear it from us: The value of Tessian’s Cloud Email Security Platform was independently verified by a Forrester study, revealing that a composite enterprise of 10,000 protected inboxes saw 268% Return On Investment (ROI) over three years after deploying Tessian. In addition to the advanced threat prevention and insider risk capabilities delivered by Tessian, this amounted to over 29,600 labor hours saved from having to triage threats and false positives from inboxes.