Contributors : Catalin Giana & Razvan Olteanu
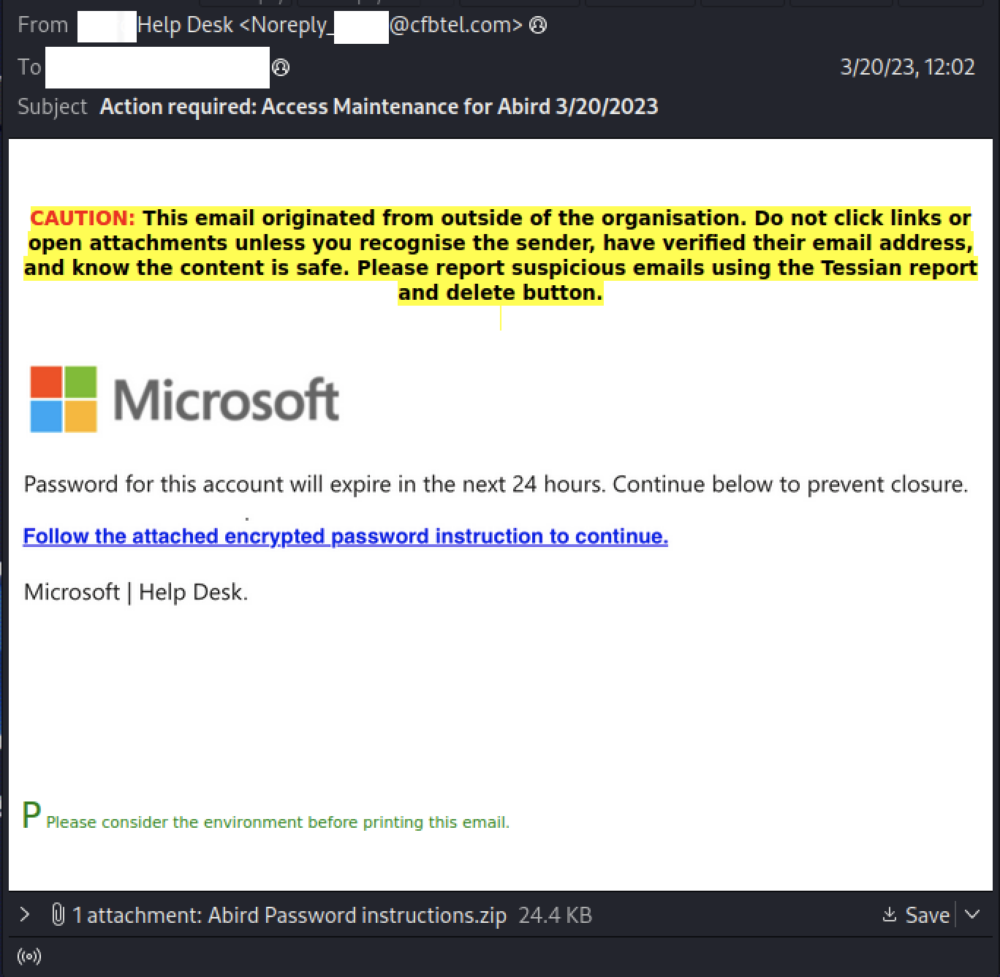
In this example of Tessian in Action members of our Threat Intel Team saw this Microsoft credential attack target several of Tessian’s customers. There are four interesting things to note in this attack.
- There was a zipped set of password instructions attached
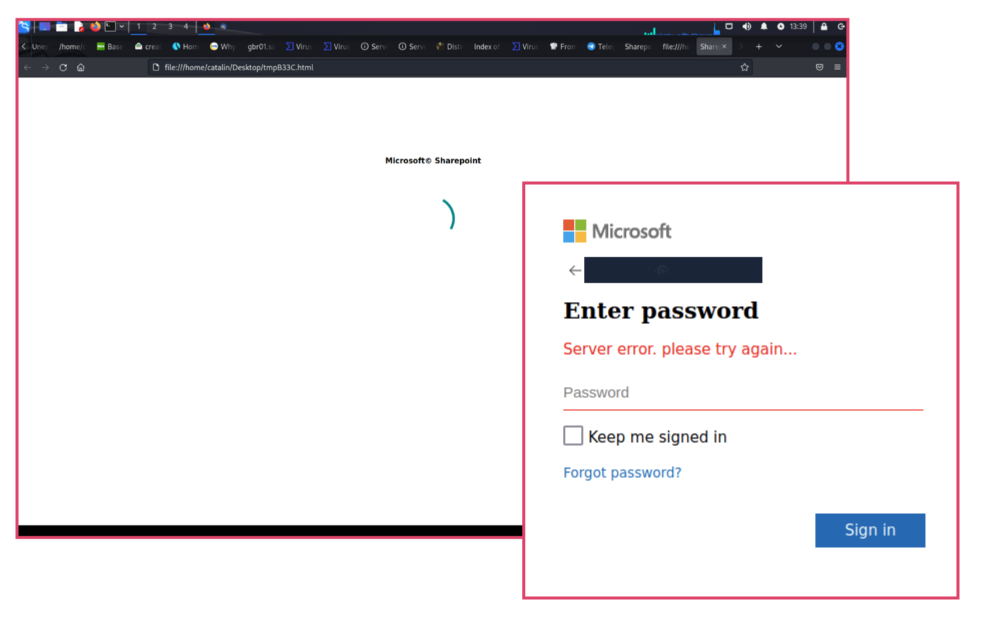
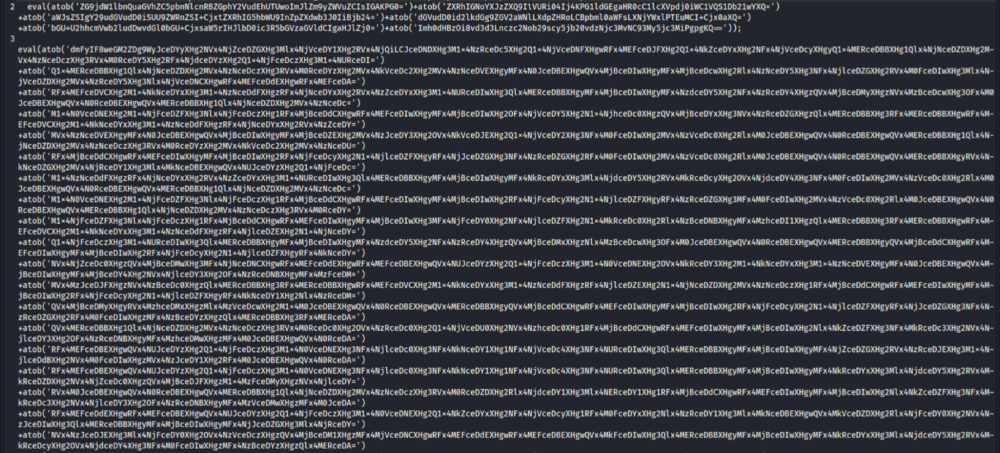
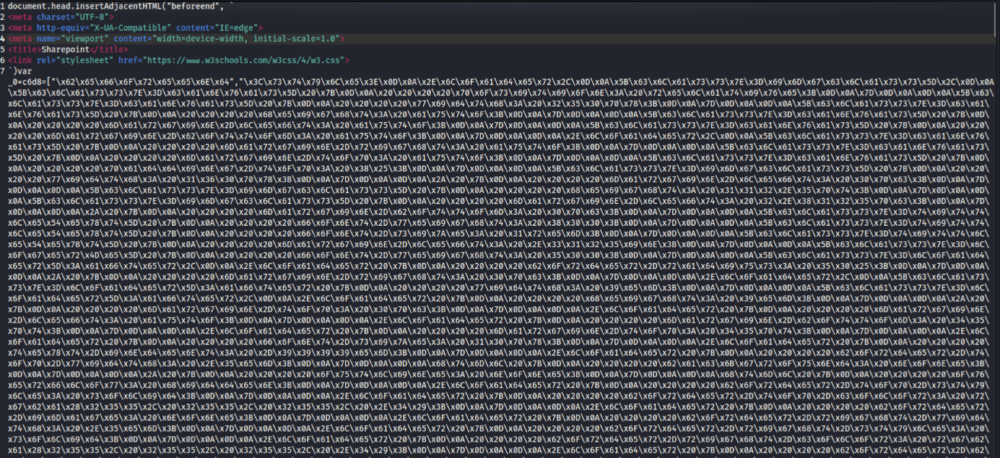
- Within that was HTML that hid obfuscated Javascript which forwarded to a credential harvesting site
- The attack had a custom sender name for each individual attack
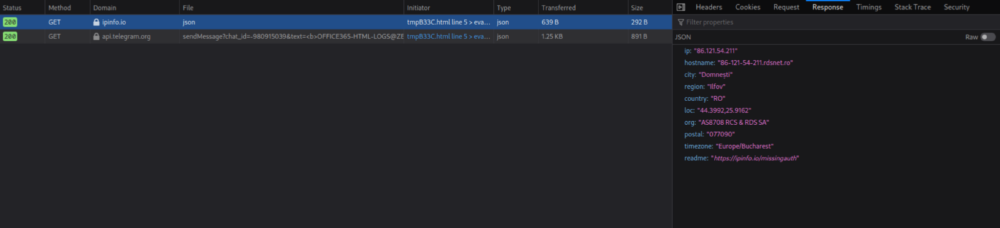
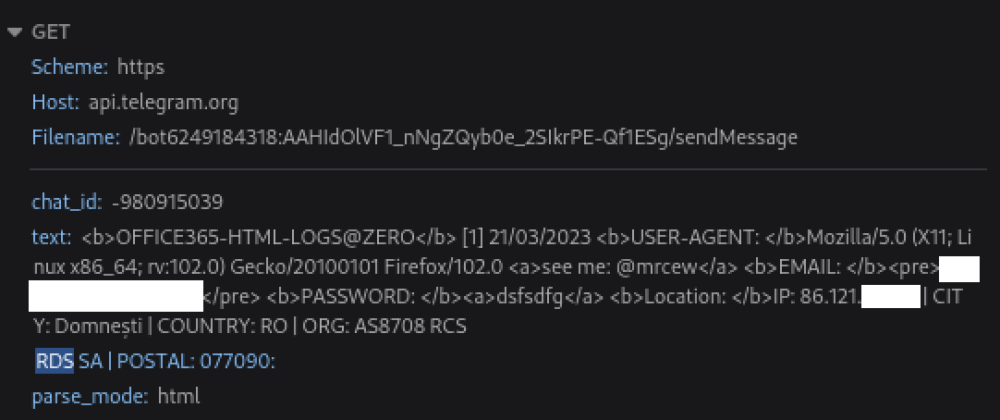
- Any successfully captured credentials were forwarded to Telegram.
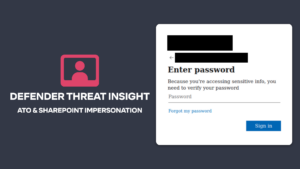
Here’s how the attack sequence worked. The email came as a Microsoft impersonating campaign with a zip file attached containing password instructions. Much like a sealed present, the hope was that the user would unpack the zip file to see what was in it, believing it to be legitimate.