Over a 12-month period, Tessian Defender detected nearly 2 million malicious emails, all of which slipped past Secure Email Gateways (SEGs) and native tools to land in employees’ inboxes.
This represents a lot of risk.
So, to help you understand what you’re up against and – more importantly – how to protect your organization, we analyzed them to identify the what, how, who, why, and when of today’s threat landscape. Here’s what we found out….
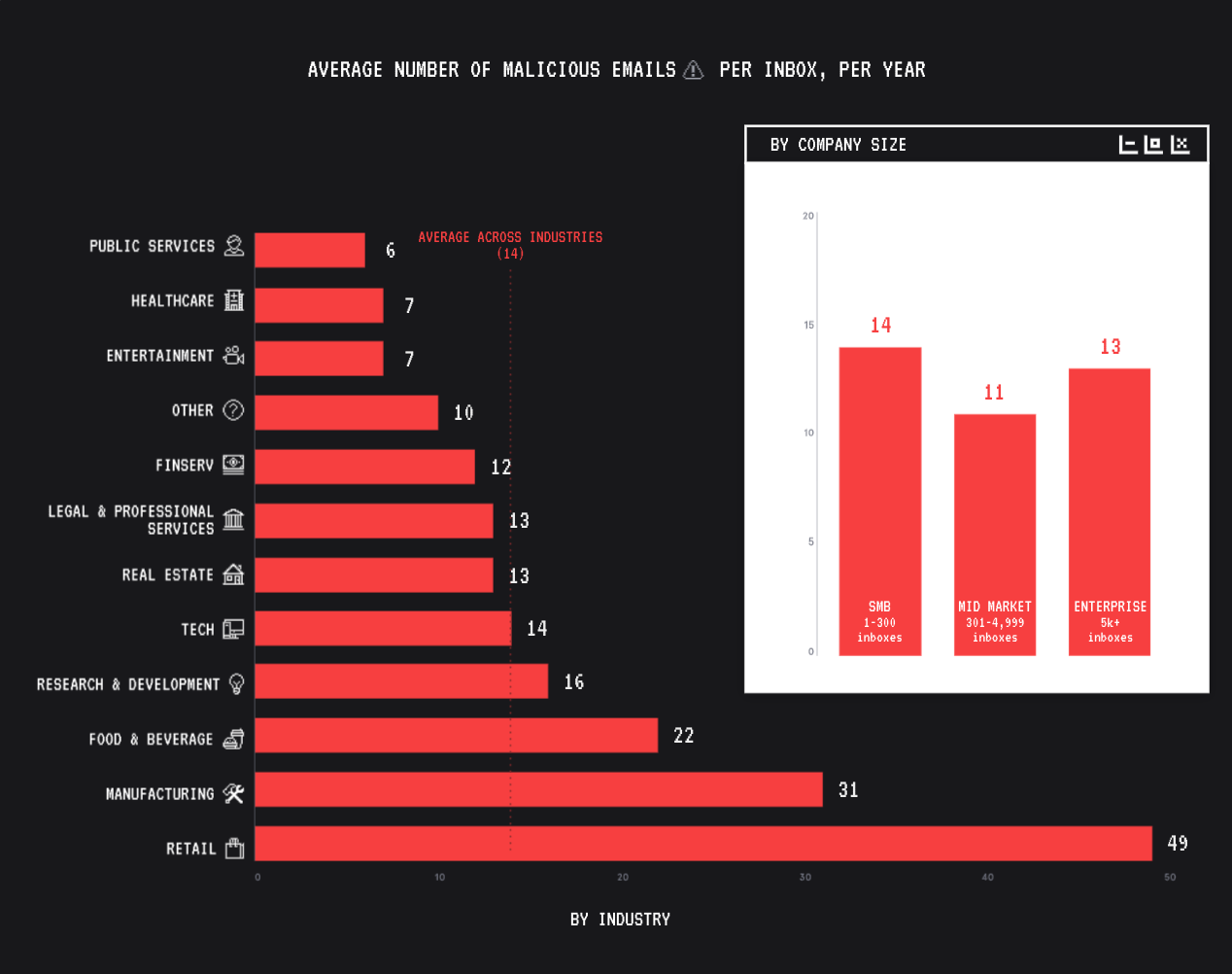
When it comes to who they target, bad actors cast a wide net, but do seem to have an affinity for Retail, Manufacturing, F&B, R&D, and Tech. But still, across all industries, Tessian flagged 14 malicious emails a year, per employee.
That means that, without Tessian, each employee would have to successfully identify 14 carefully crafted emails a year in order to avoid a breach. That’s just too much risk.
In terms of company size, bad actors will take whatever they can get.
Wondering why they don’t focus exclusively on the “big fish” (i.e. enterprise)? Because smaller companies – who generally have less money to spend on cybersecurity – are often easier to infiltrate. This can be a foothold for lateral movement, especially for companies with large supply chains.
Interestingly though, regardless of industry or company size, attacks look just about the same.
Across the board, display name spoofs are the most commonly used impersonation tactic.
Payloads are more often delivered via URLs than attachments. And keywords related to wire transfers are more frequently seen than keywords related to credentials.
This reinforces just how effective these tactics are, regardless of how much budget an organization has allocated to cybersecurity.
2. Most malicious emails don’t contain attachments 📎
While attachments are listed first in frameworks like MITRE, most bad emails don’t actually contain attachments. That’s why it’s important to train employees to spot a variety of different malicious payloads, including zero payload attacks.
Zero payload attacks don’t rely on a malicious payloads like attachments or links. The attacker simply persuades the victim to action a request.
Zero payload attacks can be just as devastating as malicious payload attacks, and traditional antivirus and anti-phishing software – which often rely solely on keyword detection and deny/allow lists – struggle to detect them.
But what about when bad actors do leverage attachments?
Download the full report to see which file extension type is most common, and to download an infographic to share with your employees.
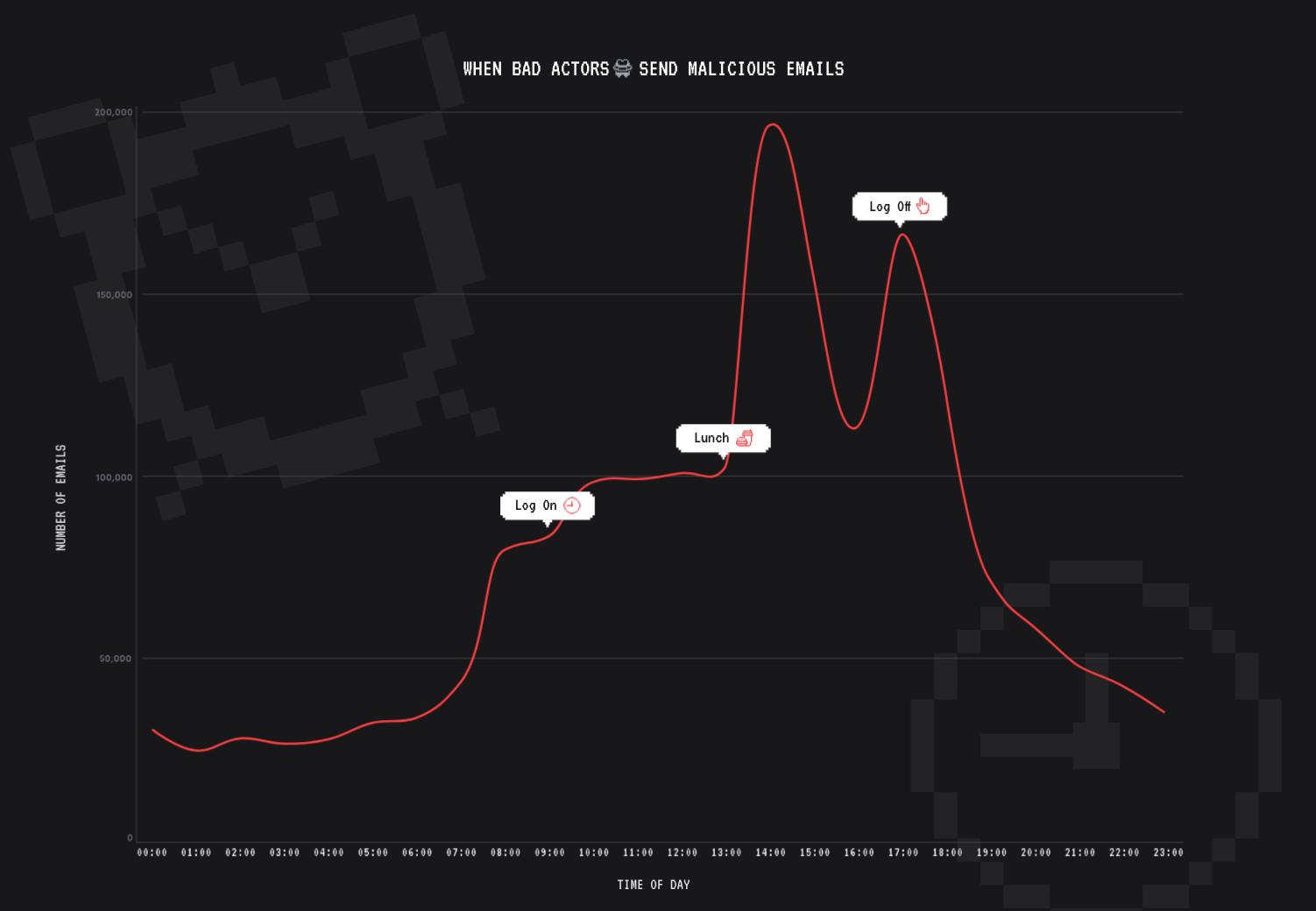
3. You’re most likely to be phished between 2PM and 6PM 🐟
We’re often told that bad actors borrow best practice from marketers. If that’s the case, most phishing attacks would land in employees’ inboxes around 10 AM on Wednesdays.
Our analysis tells a different story.
The most malicious emails are delivered between 2PM and 6PM, with very little fluctuation day-to-day (except over the weekend). This isn’t an accident.
Since employees are more likely to make mistakes when they’re stressed, tired, and distracted, the second half of the work day is a bad actor’s best bet. (Hello afternoon slump!)
Help your employees stay alert by letting them know when they’re most likely to receive a phishing email, what they look like, and what to do if and when they do spot something suspicious.
There are dozens more insights in the report, including:
- Which brands are the most frequently impersonated in attacks
- What keywords appear most frequently in subject lines and body copy
- Which industry is most frequently compromised in ATO attacks
Download it now while it’s ungated!