Tessian is running at full speed to provide you with smarter, faster email security. Our team has been busy building and enhancing the products you know and love — making it even easier to use for security professionals. Here are the latest updates from our product team.
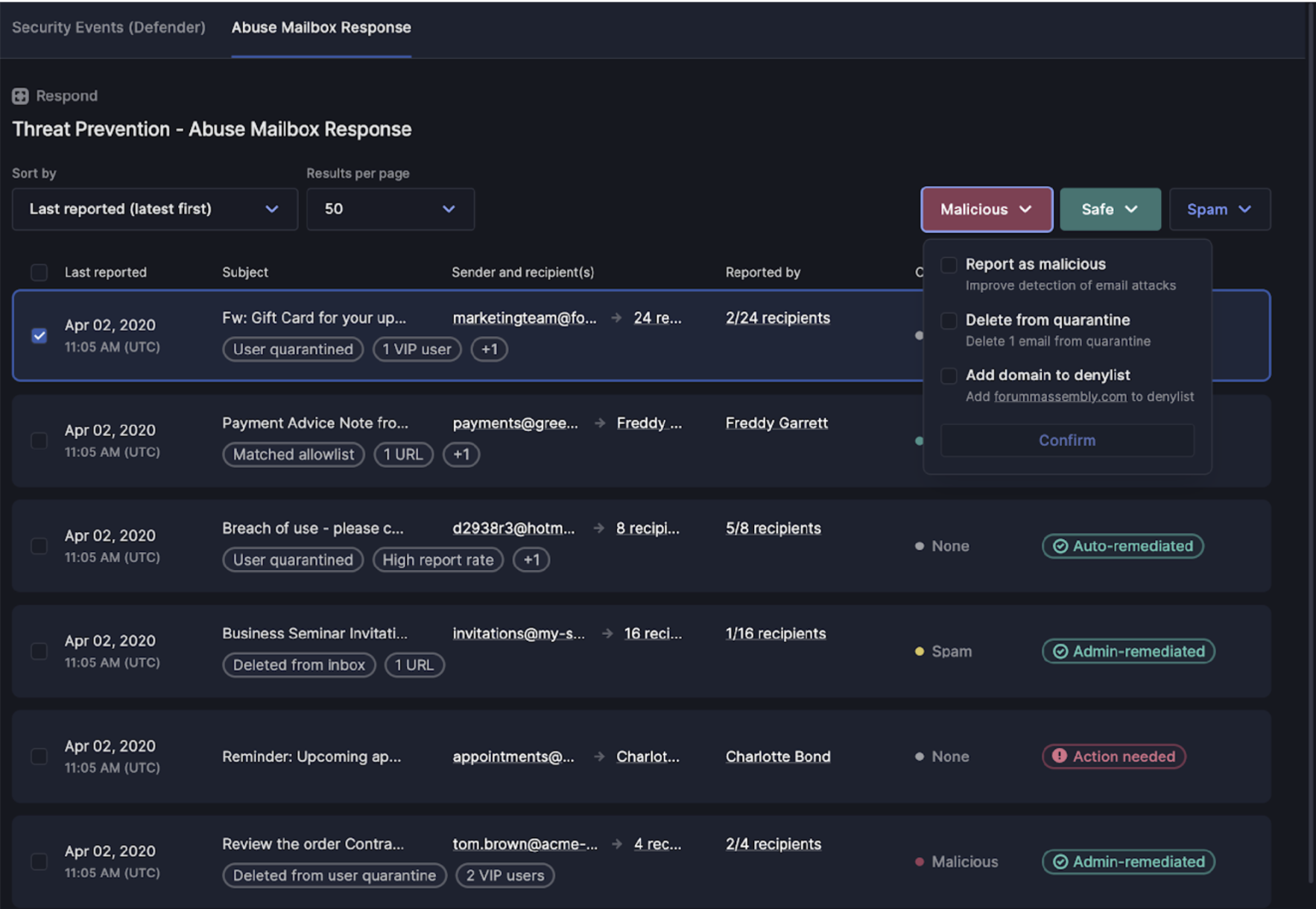
Abuse Mailbox Response
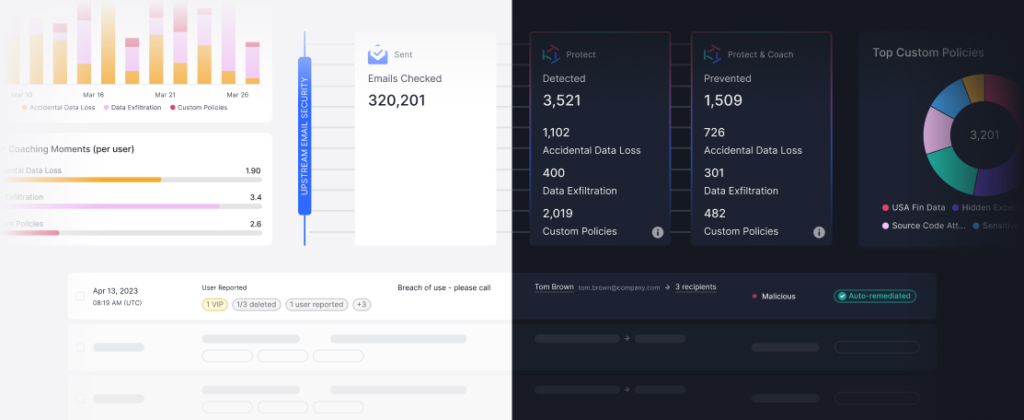
When something looks phishy, you want your end-users to hit that “report phish” button. But what happens when your security team is inundated with reported threats? 90% of user-reported emails aren’t malicious. And while it’s better safe than sorry, Tessian is releasing a product that saves security analysts precious time by automatically identifying the handful of true threats that require human attention.
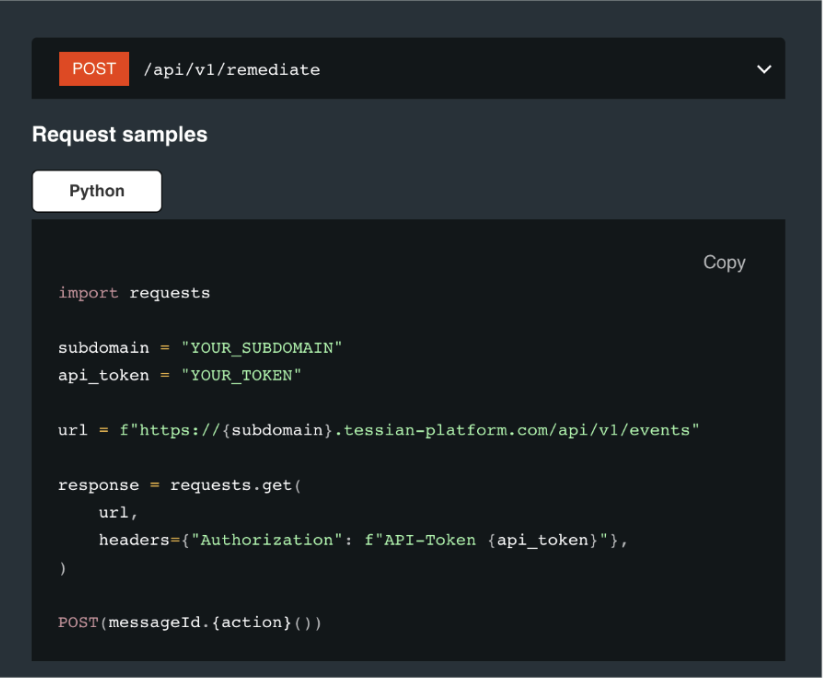
Abuse Mailbox Reponse uses machine learning to automatically classify, triage, and remediate user-reported emails so that security teams can focus on the threats that matter. It offers crowd-sourced detection, enabling automatic quarantines when multiple users report the same email threat. And it also provides custom communications options for end-users who report, making feedback loops between security and end users even stronger.
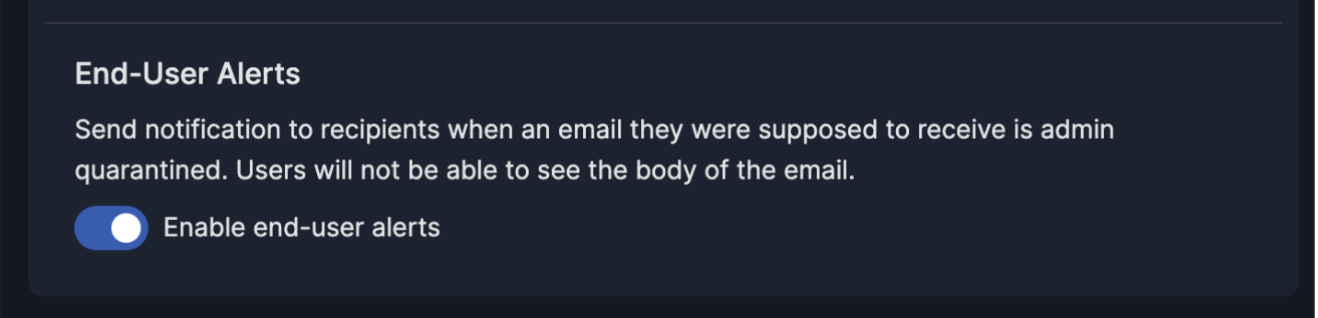
For example, a reported email will be classified as malicious, safe, or spam based on a number of factors that extend beyond the machine learning model. How good is the user at reporting? What percentage of users have reported it? After the email is remediated, the reporter will receive a customizable, automatic response. This message encourages users to keep reporting and educates when the email was found to be safe.
Even better, there is no change to the end-user experience during roll-out. Any existing report-phish buttons will work with the Abuse Mailbox product.
With this product, security teams save hours a day on manual classification. It’s significantly faster than legacy systems that rely on rule-based protection and manual inspection:
- A 5,000- user organization sees about 1,400 reported emails each month, on which they spend about 700 hours on manual investigation and remediation.
- Tessian reduces manual review by 90%
- Tessian accelerates investigation time by 80%
Abuse Mailbox Response is the second product release in the Respond product line, following Investigate and Respond from April 2023.