When our three founders, Tim, Ed, and Tom conceived of a company initially called “CheckRecipient” in their London apartment, the path to working with the largest and most prestigious companies on the planet would have felt a long way away.
Yet here we are, 9.5 years later, already growing our base of Fortune 500 customers while plotting our journey to 50k+ employee companies and beyond.
Of course, regardless of the size of our customers, our mission is the same. We continue to empower people to do their best work, without security getting in the way. But working relationships between customers and vendors change when you go upmarket.
Based on my experience of working with our largest customers, here are five challenges enterprise customers face with security vendors, and tips to help CISOs and Heads of Infosec carefully navigate the often rewarding (and always noisy) world of vendor partnerships.
Vendors, vendors everywhere…
So you’re a CISO at a prestigious bank, law firm, or healthcare company.
Every security vendor under the sun wants a piece of your time. This is exhausting. And frequently counterproductive. Don’t they know you also have a job to do?
So, what do you do about it? Go to every meeting your vendors book in and try to work around it? Go completely quiet on all your vendors and hope that you’re getting value from the partnerships anyhow?
We’ve learned with our customers that it’s worth taking control of this situation early on.
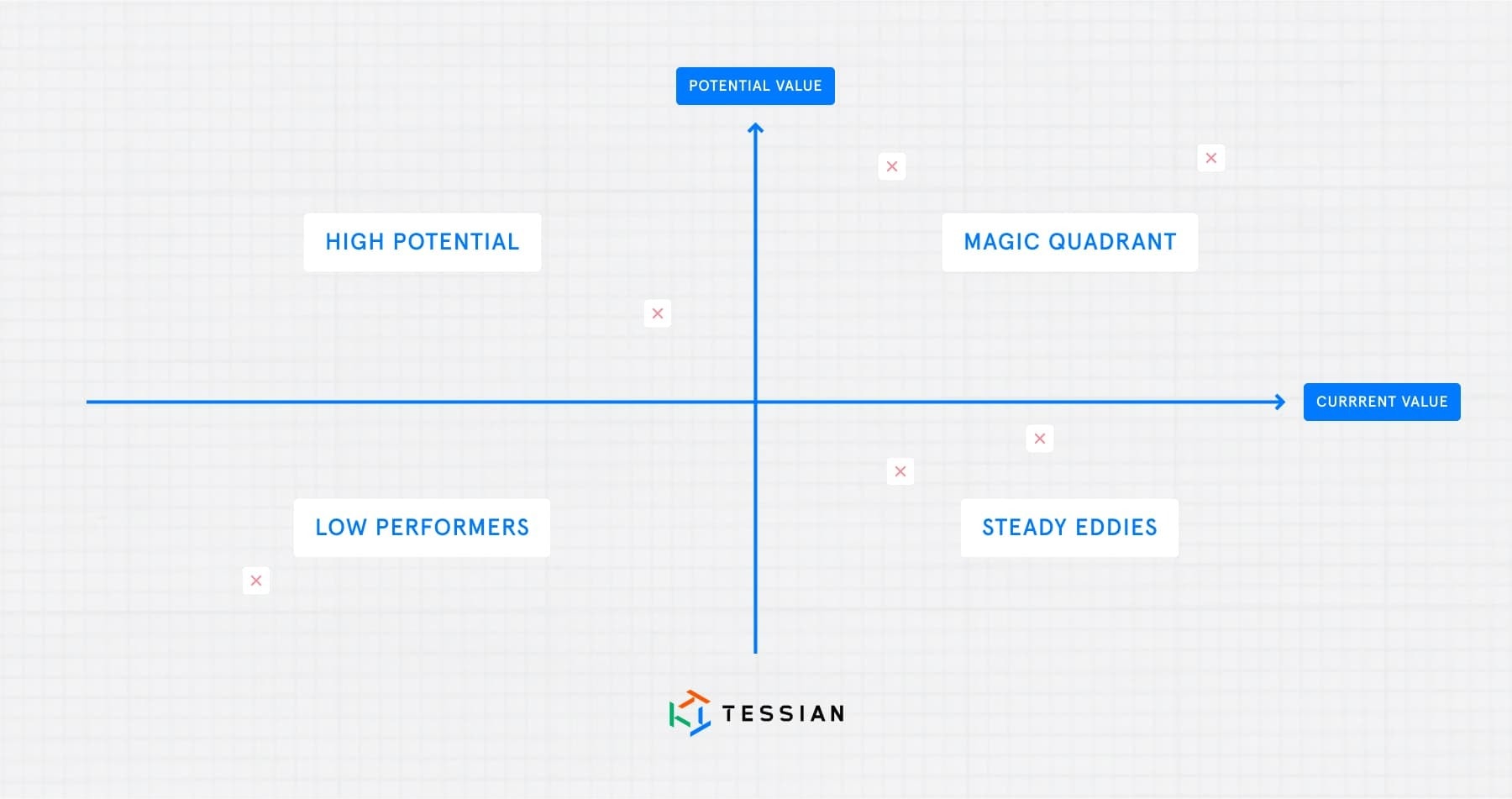
1. Categorize your vendors into a quadrant based on the current value you’re seeing and their potential value. Work with your team to sketch out a framework for current value, and then challenge your vendors to supply you with the telemetry to feed that framework. Potential value is more of a judgement call, but here are a list of questions you may want to consider.
- How fast is the vendor growing?
- How innovative is their roadmap?
- How many of their products/services are we currently not using that we could be?
By the way, this quadrant will also be really useful when it comes to budgeting season and renewal conversations with your vendors…
Think very critically about whether you should be continuing to partner with your “Low Performers”.
2. Based on the quadrant, communicate with your vendors how often you need to connect with them. (If you want to go a step further, you can even take the lead on scheduling so meetings go in at convenient times for you.). For example, you may want to meet with your magic quadrant and high potential vendors quarterly, but the “Steady Eddies” may only require your attention once a year.
Longer time to value
They say that time heals all. But in SaaS, time is the biggest killer for momentum, engagement, and ultimately ROI.
That’s why the onboarding process is critical to the long-term success of a partnership.
There’s two determining steps for onboarding:
- Internal Processes: For the enterprise, there is plenty of red tape and change management when it comes to deploying new tech. The most successful deployments I’ve seen involved a proactive CISO or Head of Infosec pulling as much process management forward as possible.
- Technical Deployment Considerations. Rome wasn’t built in a day. Likewise, enterprise tech teams will often adopt a 1-9-90 approach to deployment (e.g. a pilot 1% group of friendly users getting the tech initially, then 9%, then the rest). Those security leaders who agree on and stick to a deployment plan, encourage deployment project leads to connect regularly with the vendor, and ensure roadblocks are identified and escalated early are the most successful.
Support tickets and feature request prioritization
I’ve seen support processes and feature requests work really well and in all such cases, the key is communication.
Encourage your technical leads to agree up front with your vendors how best to flag high priority tickets. It’s worth keeping oversight on this to ensure it aligns with what’s strategically important to you. This is the hymn sheet that both parties can sing from when it comes to escalation and helps everyone involved avoid the old fashioned (and slightly anarchical) “who shouts the loudest” method of prioritization.
The same goes for feature requests. Agree a process for tracking these and allocating a scale all the way from “deal breaker” to “nice to have” (and what’s needed now vs in the future).
Strength in numbers
As 1997 UK trip-hop band Olive (niche reference?) once sang: “You’re not alone”. No enterprise CISO Head of Infosec is an island.
There’s often a temptation to hoard ownership of the partnership with a vendor to prevent those pesky folks running wild throughout your business. In practice, this probably achieves the opposite effect.
Our most successful Tessian customers involve a broad set of stakeholders in the ownership of the vendor partnership and outsource some of the heavy lifting of demonstrating the product ROI to the vendor’s CSM. For example, at Tessian, stakeholders from the security function, IT, HR, compliance, and legal will all have a say in the successful implementation of the product.
The exact same process is going on internally at Tessian, with exec sponsors, product managers, CSMs, and account executives all aligned to each enterprise account.
Integration is king (and consolidation is… prince?)
Finally, the enterprise space is becoming increasingly cluttered with more and more vendors seemingly popping up every day.
You may find yourself looking at the 10s or even 100s of vendors they partner with and asking, “Do I actually feel more secure?”. It’s a fine balancing act between the skyscraper of layered defenses and the modest bungalow of a lean stack.
And the wire that connects these two buildings is – you guessed it – integration.
Now, I dislike the cliche of “Make 1+1=3” (it doesn’t). But pushing your key vendors to integrate will not only improve the value you get out of them individually, it will also bring clarity to any overlap or redundancies in functionality between them. Any opportunity to trim down bulky incumbent contracts where another vendor can pick up the slack has to be considered a win.
I’d emphasize that this refers to integration not just in terms of functionality, but also reporting. Over half of our enterprise clients have already enabled the SIEM API to create a “single pane of glass” view of insights that becomes tool agnostic.
For example, Investec joined us for a webinar to explain how they’re using Splunk to centralize and correlate their Tessian reporting with other tools. You can check out a summary of their tips here].
Conclusion
If you’ve made it this far I commend your ability to put up with my penchant for a metaphor…
Increasingly, we’re moving away from the classic, client-vendor relationships and towards a more symbiotic model of shared goals. This is vastly more conducive to getting holistic value for what you pay for.
The bottom line: the foundation for any halfway decent partnership is good communication. That’s not “communication” in the sense of spending hours on calls with a vendor every day. What it does mean is early alignment with them on what it is you hope to achieve through working together – that way we all really are singing from the same hymn sheet 🎼
Will Patterson
Enterprise Customer Success Lead