Data Loss Prevention is a vital part of security frameworks across industries, from Healthcare and Legal to Real Estate and Financial Services. There are dozens of different DLP solutions on the market, each of which secures data differently depending on the perimeter it is protecting.
There are three main types of DLP, including:
- Network DLP
- Endpoint DLP
- Email DLP
While we’ve covered the topic of email DLP broadly in this Complete Overview of DLP on Email, we think it’s important for individuals and larger organizations to fully understand what the proper application of email DLP can offer and, with that, why it’s so important to know which email DLP system to implement.
How can DLP for email protect an organization?
Importantly, there are two types of threats DLP must account for:
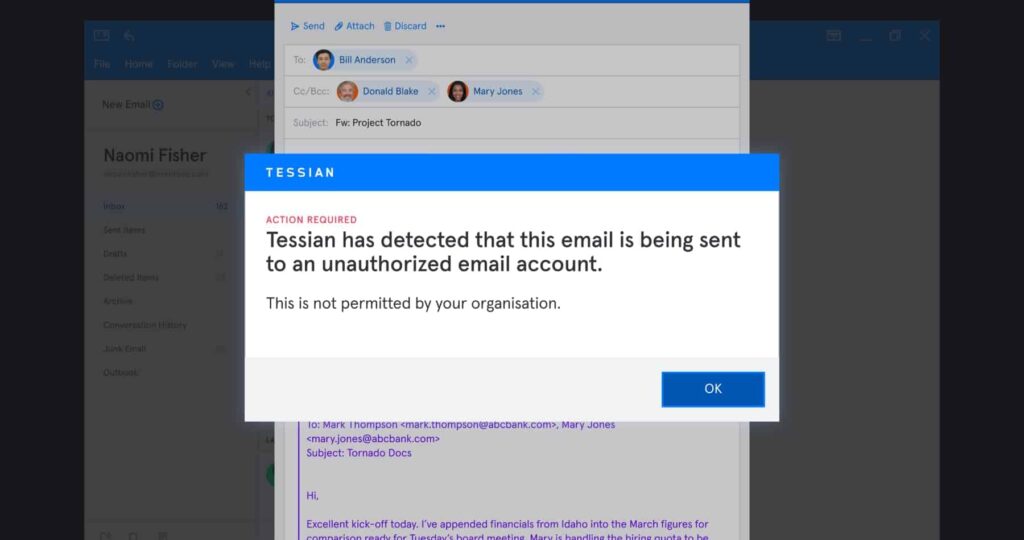
- Accidental Data Loss: To err is human. For example, an employee might fat finger an email and send it to the wrong person. While unintentional, this mistake could and has led to a costly data breach. DLP solutions need to be able to flag the email as misdirected before it’s sent, either by warning the individual or automatically quarantining or blocking it.
- Malicious Exfiltration: Whether it’s a bad leaver or someone hoping to sell trade secrets, some employees do, unfortunately, have malicious intent. DLP solutions need to be able to identify data exfiltration attempts over email before they happen in order to prevent breaches.
An introduction to rule-based DLP
On a basic level, the bulk of DLP solutions operate via rule-based policies, using if-then statements to lock down data after it’s been classified.
For example, if you want to ensure your HR department doesn’t share personally identifiable information (PII) like employees’ social security numbers, you could create a rule on email: “If an outbound email to a party outside of the organization contains the word ‘social security number’, then block. it.”
You could also create a more broad rule. For example, if you wanted to prevent accidental data loss of company information, you might forbid employees to send emails to their personal email accounts. To enforce this, you might block all emails from an official company account to freemail accounts like @gmail.com, @yahoo.com, or @hotmail.com.
Of course, these rules need to be set up separately for each organization where a DLP system is implemented. Various factors can influence these rules, including the type of data being protected, workflows, and existing policies, procedures, and tools. This will help you recognize potential “borders” that sensitive data shouldn’t cross.
The limitations of rule-based DLP
Unfortunately, DLP – especially rule-based DLP – can be a blunt instrument.