According to new research into the future of hybrid working, 85% of IT leaders believe their security teams will be under higher pressure, feel more stretched, and need extra resources in 2021.
Could automation shoulder some of the burden?
In case you missed it, Tessian hosted Karl Knowles, Head of Cyber at HFW, and Timor Ahmad, Head of Data Governance & Privacy at Lloyd’s, for a session that took a deep dive into how organizations can utilize automation to reduce risk on email.
You can watch the full video on-demand, but we’ve summarized the highlights from the session along with some actionable advice you can use to give your security posture a boost.
1. Use this shift to remote working to create a more positive security culture
Can employees work remotely? Can they maintain the same quality of work?
These are both questions security and business leaders have asked for years but have been too hesitant to actually test.
But now – as we’ve all been forced to make the transition from office to home – we’ve seen how people have adapted and we now have new ways of working. These changes naturally affect your organization’s culture.
“It’s the ‘new norm’ now - but, soon it will be the ‘norm’.”
Timor Ahmad
Head of Data Governance & Privacy at Lloyd’s
So what does this mean for security leaders? It means you have the ability to mold and shape a more positive security culture. Take time to understand how your employees are working, what their new behaviors are, and how you can support them in a safe and compliant way.
Now is the time to integrate security awareness into the foundation of your organization and prioritize privacy for employees, clients, and customers wherever and however they work.
2. Be human-first in your approach to security
Working remotely, people may feel isolated, unmotivated, and unsupported. That’s why you have to prioritize employee wellbeing and help everyone adapt.
So, to help make security more human (and yes, fun) Karl and Timor suggested using cartoons, magazines, or digital games to help get employees involved and bring them along on your journey to security maturity.
But it’s not all about fun. It’s also about meaningful connections.
Security is a team sport and employees need to feel comfortable asking questions about security, sharing feedback about new solutions or policies, and reporting incidents and near-misses. You have to foster that environment. How? Drop into team meetings on occasion, encourage people to open up to you, and always ask questions and provide ways for employees to give feedback.
Building this connective tissue with employees across the organization will help people feel more supported in their new way of working.
3. Share your security wins
According to Karl and Timor, it can be a challenge to help employees feel like they’re actually contributing to the success of the security program. But, they had a tip.
Use data.
They explained how they use Tessian’s dashboard to display key charts and statistics around the organization’s security posture both at the board and employee level. The numbers include:
- How many phishing attacks are reaching employees
- How many of those were flagged to their security team
- What the outcome would have been if the attack was successful.
Everyone contributes to a safe working environment, and these dashboards can help security leaders communicate that message with both technical and non-technical audiences.
“It may be a new approach - which is always difficult, but it’s a challenge. You still have the company to support you.”
Timor Ahmad
Head of Data Governance & Privacy at Lloyd’s
4. Make your solutions work for you
Are you spending a lot of time configuring solutions and updating rules? Most security leaders are.
That’s because rules are static, meaning they don’t change over time. But – as we all know – over the last year, organizations have undergone a lot of change. People are working on different devices, in different locations, and are using different methods to share information. Hackers have changed their attack methods accordingly.
It’s unrealistic to expect security teams to be able to update rules at pace with all of the above. At Tessian, we think solutions should work for you.
How? Automation. Across three solutions, Tessian uses machine learning to understand employee behavior and communication patterns. And, it gets smarter over time. That means it can detect and prevent threats in real-time – without any manual investigation or rules – and keeps pace with the evolving threat landscape.
“Deployment and moderation are easy - the tool learns on the go. So we don’t have to set up rules or iterate rules as the attacks change and develop. This has massively cut down the manual burden on our team.”
Karl Knowles
Head of Cyber at HFW
5. Understand why your employees circumvent policies
According to Tessian research, over half of employees say they’ll find a workaround for security software or policies that make their job difficult or impossible to do.
It’s essential, then, that security leaders understand why. The key is visibility into employee behavior. Both customers explained how they use Tessian to get a more granular look at how employees handle data.
In one example, Karl looked at the data provided by Tessian Enforcer to understand why employees send emails to personal devices. In this case, Karl realized a key tool used by HFW was slowing employees down and making it hard to do their jobs on their work devices. That’s why people were sending work documents to their personal accounts — so that they could work faster on their personal devices.
With this understanding, HFW was able to create new policies that empowered people to work safely without security getting in the way.
6. Leverage in-the-moment warnings to reinforce existing policies
Whether it’s data exfiltration, misdirected emails, or spear phishing attacks, humans make mistakes. But, as Karl and Timor detailed, contextual, in-the-moment notifications can help raise awareness and train employees in real-time.
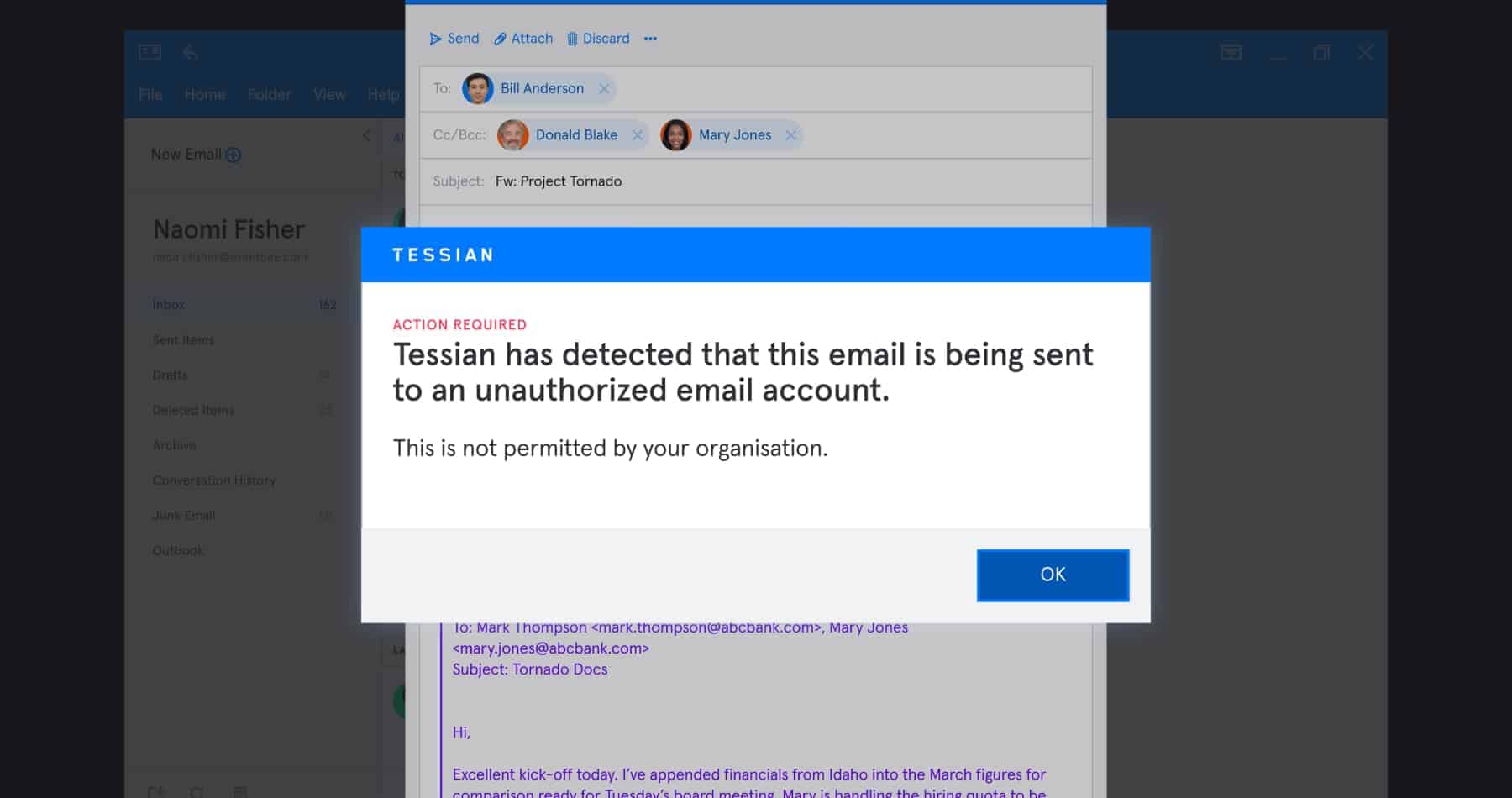
According to Karl, data exfiltration has always been a problem in the Legal Industry. But HFW has revolutionized the way they tackle it by implementing real-time alerts that remind employees that sending data externally is a major security risk. Tessian Enforcer warnings look something like this:
Tessian Enforcer in-the-moment, contexual warning
Over time, these warnings have nudged employees towards safer behavior to help HFW downtrend risk and reduce the number of emails being sent externally.
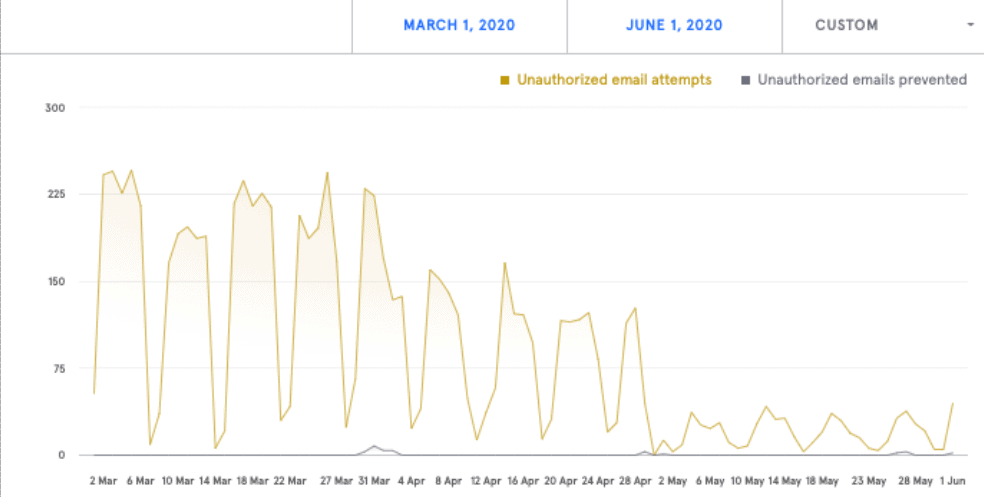
Karl explained this in more detail by showing his Tessian dashboard. “In the graph, you can see exactly where we implemented the warning and our employees’ response to that new system. So we can see data exfiltration has decreased massively,” he said.
One insight from the Tessian dashboard shows how data exfiltration attempts have decreased since Tessian Enforcer was deployed.
Now that they’ve tackled this problem, their next focus is around bad leavers and how to reduce the risk of data exfiltration after someone exits the company.
Here’s their plan: Once someone has handed in their notice, HR and compliance teams will monitor the employee’s behavior and see if it deviates from the norm. Are they sending more emails to personal accounts than usual? Do those emails contain sensitive information? Are they emailing new contacts?
Tessian will instantly flag any anomalous behavior to help HFW stop the exfiltration attempts.
Want to learn more about how Tessian has helped HFW and Lloyds level-up their security without burdening security teams? Watch the full interview now.