Overview
- Industry: Construction
- Size: 500 employees
- Platform: O365
In March 2021 Tessian Defender flagged an email received by one of our customers from one of their trusted vendors. The vendor had suffered from an account takeover when an attacker used compromised credentials to login to the mailbox of one of their employees and send out malicious emails.
Targets Identified
With access to the vendor mailbox, the attacker was able to identify all organizations or individuals they had regular correspondence with. The attacker identified a list of 6 high-ranking employees – including the CEO and their PA – who were part of an organization the employee had regular correspondence with. This organization – a construction firm – happened to be a Tessian customer running Defender across their mailboxes.
Attack Deployed
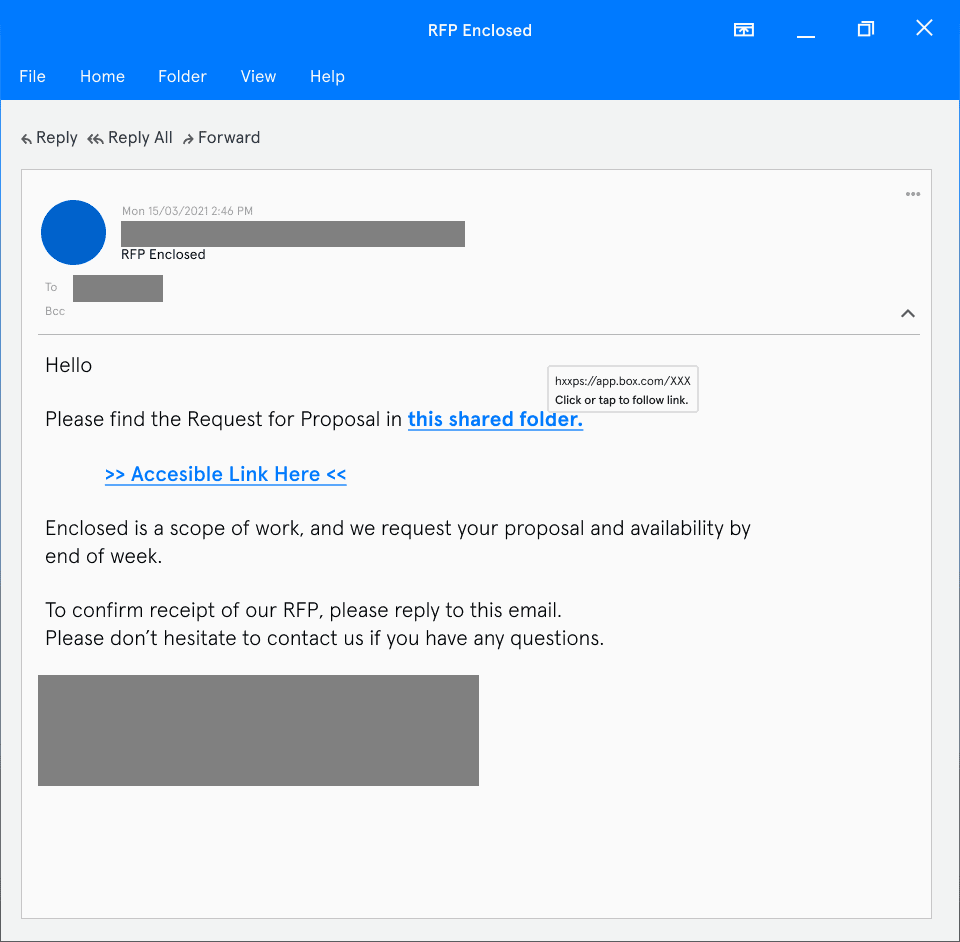
The attacker sent an email to their targeted list of recipients from the compromised account. This email contained a message outlining a request for proposal for a piece of work. The email also contained embedded links to a file sharing location hosted by box.com, which the recipients were encouraged to click on to see full details of the request.
Figure 1: Email requesting recipient to click malicious links
Threat Detected
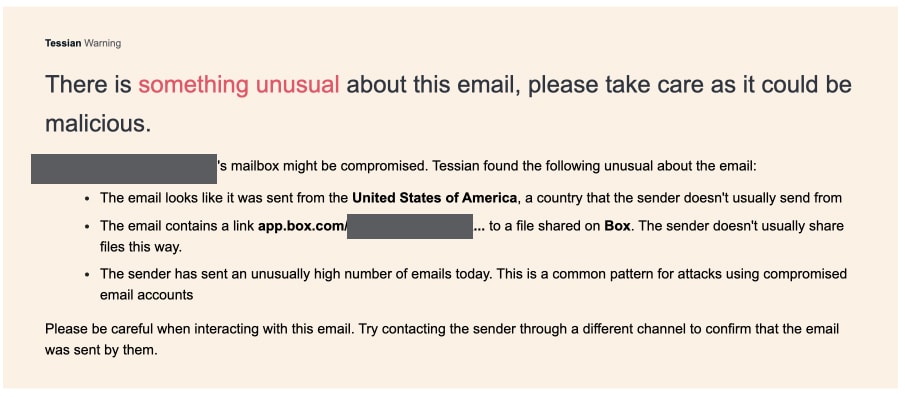
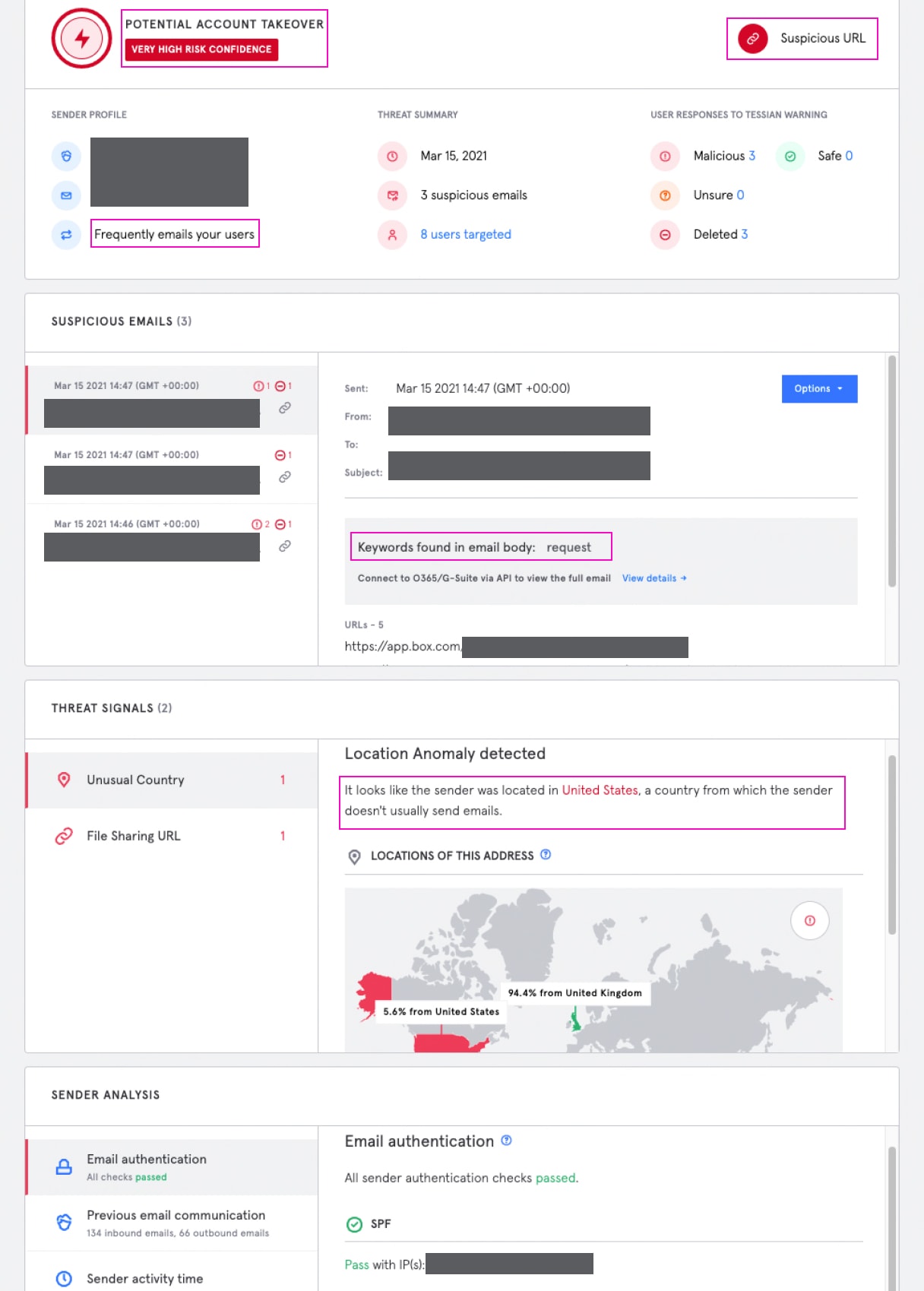
In addition to Tessian Defender, the targeted firm has in place another major phishing detection and response platform, as part of their email security stack. The account takeover attack was only flagged by Defender. Defender flagged this email as a possible account takeover attack by identifying 2 significant abnormalities. While the email did come from a trusted sender, what appeared to be out of place was that the email had been sent from a client IP address located in Miami, Florida, which is not a location the sender was known to have previously operated from. (The vendor is based outside the US.) Additionally the file sharing site – box.com – was not a tool the sender was known to use.
Figure 2: Tessian Defender notification, as seen by Recipient in their inbox
Figure 3: Tessian Defender threat analysis, as seen by Security Team in the Tessian Portal
The recipients of this email saw the warnings generated by Defender and, fortunately, marked them as malicious, which alerted their security team. The security team was then able to act on the attack. They contacted the real owner of the sending email address by phone to verify the legitimacy of the email and inform them their account may have been compromised.
Minimizing fallout
This attack could have been much worse had it not been for Defender flagging the malicious email, which could have otherwise gone unnoticed as it was sent from a trusted email address. The warning message displayed to the recipients successfully nudged them into treating the email with caution and raising it to the security team.
Most significant is that the security team on the recipient side went the extra mile to notify the owner of the compromised account. This enabled the security team on the sender’s side to quickly take the following remediation actions:
- Identify and notify any other organizations that were targeted by the attacker
- Secure the compromised mailbox and reset the credentials
As a result, the attacker was prevented from sending malicious emails to any other target organizations.
Charles Brook
Threat Intelligence Specialist