Data loss prevention (DLP) and insider threat management are both top priorities for security leaders to protect data and meet compliance requirements.
And, while there are literally thousands of threat vectors – from devices to file sharing applications to physical security – email is the threat vector security leaders are most concerned about protecting.
It makes sense, especially with remote or hybrid working environments. According to Tessian platform data, employees send nearly 400 emails a month. When you think about the total for an organization with 1,000+ employees, that’s 400,000 emails, many of which contain sensitive data. That’s 400,000 opportunities for a data breach.
The solution? Email data loss prevention.
This article will explain how email DLP works, consider the different types of email DLP, and help you decide whether you need to consider it as a part of your overall data protection strategy.
What is email data loss prevention?
Essentially, email DLP tools monitor a company’s email communications to determine whether data is at risk of loss or theft. There are several methods of email DLP, which we’ll look at below. But they all attempt to:
- Monitor data sent and received via email
- Detect suspicious email activity
- Flag or block email activity that leads to data loss
Do I need email data loss prevention?
Unless you’re working with a limitless security budget (lucky you!), it’s important to prioritize your company’s resources and target areas that represent key security vulnerabilities.
Implementing security controls is mandatory under data protection laws and cybersecurity frameworks, like the General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), and Health Insurance Portability and Accountability Act (HIPAA).
And there’s a good reason to prioritize preventing data loss on email. As we’ve said, email is the threat vector security leaders are most concerned about. We’ll explain why.
Inbound email security threats
How can malicious external actors use email to steal data? There are many methods.
- Phishing—social engineering attacks designed to trick your employees into handing over sensitive data. According to the FBI, phishing is the leading cause of internet crime, and the number of phishing incidents doubled in 2020.
- Spear phishing—like phishing, but targeted at a specific individual. Spear phishing attacks are more sophisticated than the “bulk” phishing attacks many employees are used to.
- Malware—phishing emails can contain a “malicious payload”, such as a trojan, that installs itself on a user’s device and exfiltrates or corrupts data.
Email DLP can help prevent criminals from exfiltrating your company’s data.
Internal email security threats
While it’s crucial to guard against external security threats, security teams are increasingly concerned with protecting company data from internal actors. There are two types of internal security threats: accidental and malicious.
Accidental data loss
Accidents happen. Don’t believe us? Human error is the leading cause of data breaches. Tessian platform data shows that in organizations with 1,000 or more employees, people send an average of 800 misdirected emails (emails sent to the wrong recipient) every year. That’s two every day.
How can a misdirected email cause data loss? Misspelling the recipient’s address, attaching the wrong file, accidental “reply-all”—any of these common issues can lead to sensitive company data being emailed to the wrong person.
And remember—if the email contains information about an individual (personal data), this might be a data breach. Misdirected emails are the top cause of information security incidents according to the UK’s data regulator.
We can’t forget that misattached files are also a big problem. In fact, nearly half (48%) of employees say they’ve attached the wrong file to an email. Worse will, according to survey data:
- 42% of documents sent in error contained company research and data
- 39% contained security information like passwords and passcodes
- 38% contained financial information and client information
- 36% contained employee data
But, not all data loss incidents are an accident.
Insider threats
Employees or contractors can steal company data from the inside. While less common than accidental data loss, employees that steal data—or simply overstep the mark—are more common than you might think.
Some employees steal company data to gain a competitive advantage in a new venture—or for the benefit of a third party. We covered some of these incidents in our article, 11 Real Insider Threats.
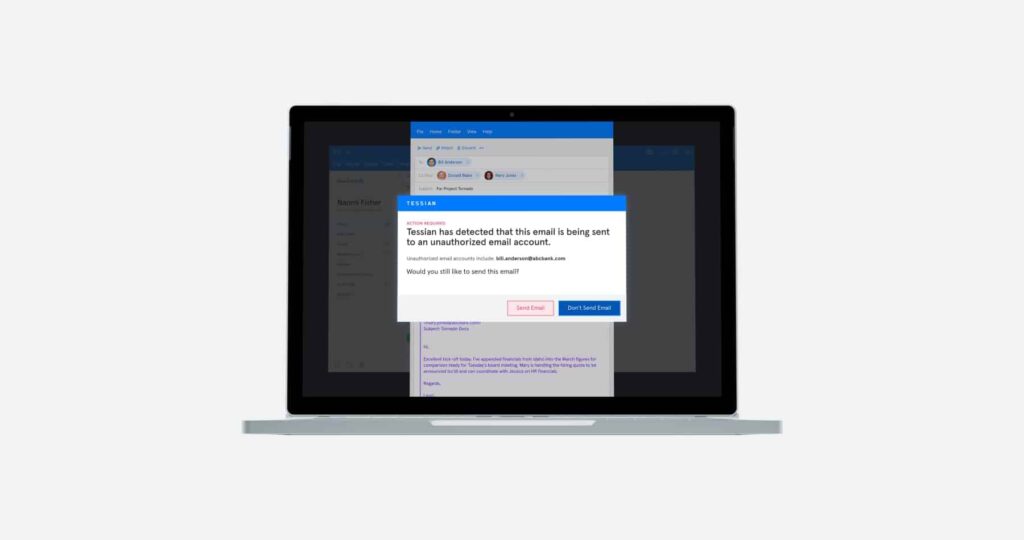
But more commonly, employees are breaking the rules for less nefarious reasons. For example, employees send company data to a personal email address for convenience. For example, to work on a project at home or on another device.
Sending unauthorized emails is a security risk, though. Tessian platform data shows that it occurs over 27,500 times per year in companies with 1,000 employees or more. And, while – yes – it’s often not done maliciously, the consequences are no less dire, especially in highly regulated industries. So, how do you prevent these things from happening?
Email DLP solutions to consider
Research shows that the majority of security leaders say that security awareness training and the implementation of policies and procedures are the best ways to prevent data loss. And both are very important.
[infogram id=”dlp-reportmicrosite-module-10-1hzj4ozjprpo2pw?live”]
But – as well-intentioned as most employees are – mistakes still happen despite frequent training and despite stringent policies. That means a more holistic approach to email DLP – including technology – is your best bet. Broadly, there are two “types” of DLP technology: ruled-based DLP and machine learning DLP.
Rule-based email DLP
Using rule-based DLP, IT administrators can tag sensitive domains, activities, or types of data. When the DLP software detects blacklisted data or behavior, it can flag it or block it.
Like training and policies, rule-based DLP certainly has its place in security strategies. But there are limitations of ruled-based DLP. This “data-centric” model does not fully account for the range of behavior that is appropriate in different situations.
For example, say an IT administrator asks email DLP software to block all correspondence arriving from “freemail” domains (such as gmail.com), which are often used to launch cyberattacks. What happens when you need to communicate with a contractor or customer using a freemail address?
What’s more, rule-based DLP is very admin-intensive. Creating and managing rules and analyzing events takes a lot of time, which isn’t ideal for thinly-stretched security teams.
🤖 Machine learning email DLP
Machine learning email DLP is a “human-centric” approach. By learning how every member of your company communicates, machine learning DLP understands the context behind every human interaction with data.
How does machine learning email DLP work? This DLP model processes large amounts of data and learns your employees’ communications patterns.
The software understands when a communication is anomalous or suspicious by constantly reclassifying data according to the relationship between a business and customers, suppliers, and other third parties. No rules required.
This type of DLP solution enables employees to work unimpeded until something goes wrong, and makes preventing data loss effortless for security teams.
“Traditional DLP has a low return on investment, and it’s expensive to run. It does stop some malicious emails, but it’s very low volume. On the other end of the spectrum, you have Tessian. If you look at Guardian, for example, it’s stopping data loss every day. Now, misdirected emails aren’t malicious activity, but the consequences are no less severe and the ROI is clear and easy to calculate. All we have to do is look at the number of employees who were going to do something - like send an email to the wrong person, move sensitive data outside of the company - but didn’t because of the solution.”
Rob Hyde
CISO at Schroders
Learn more about how Tessian’s email DLP solutions
Tessian uses contextual machine learning to address the problem of accidental or deliberate data loss by applying human understanding to email behavior.
Our contextual machine learning models have been trained on more than two billion emails – rich in information on the kind of data people send and receive every day. And they continue to adapt and learn as human relationships evolve over time.
This enables Tessian Guardian to look at email communications and determine in real-time if particular emails look like they’re about to be sent to the wrong person or if an employee has attached the wrong file. Tessian Enforcer, meanwhile, can identify when sensitive data is about to be sent to an unsafe place outside an organization’s email network. And, finally, Tessiden Defender prevents inbound threats, like spear phishing, business email compromise, and CEO fraud.
To learn more about data exfiltration and how Tessian uses machine learning to keep data safe, check out our customer stories or talk to one of our experts today. You can also subscribe to our monthly newsletter below to get more updates about DLP, compliance, spear phishing, industry trends, and more.