Email remains the number one tool of business communication. The email network is open to practically anyone—and its flexibility, reliability, and convenience mean it’s not going away any time soon.
But for all its benefits, email can also be a vector for serious cyberattacks. Social engineering attacks like phishing can lead to data breaches, malware attacks, and billions of dollars in losses for businesses worldwide.
This article will explain the major types of email attacks, provide some data on how common they are, and consider the devastating impact that email attacks can have on your business.
Types of email attacks
First, we’ll walk you through some of the most common types of email attacks.
Phishing
Phishing can mean one of two things:
- An “umbrella term” meaning any social engineering attack that takes place via email.
- A type of email attack where the attacker sends a lot of malicious emails in an untargeted way.
When we use “phishing” as an umbrella term, it refers to the most common type of email attack. Any malicious email that tries to trick you into clicking a link, opening a file, or taking any other action that causes harm, can be part of a phishing attack.
All of the other types of email attacks we’ll look at below are forms of phishing, if we use the term in this broad way.
When we use “phishing” as a specific term, it means a “bulk” or “spray and pray” email attack, where the malicious email is sent to many unnamed recipients.
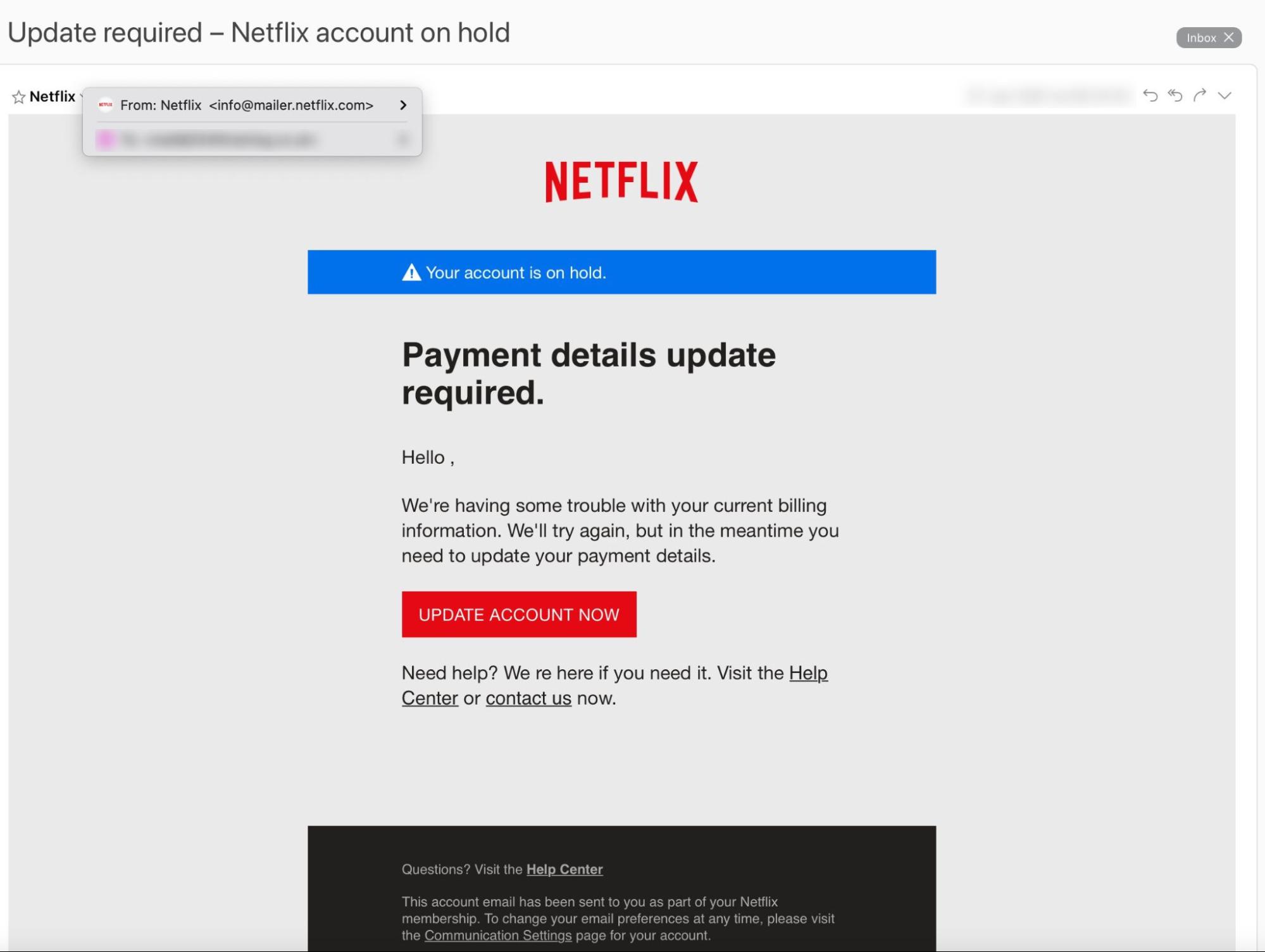
Here’s an example:
What makes this a phishing email?
- There’s no addressee: It says “Hello,” not “Hello Rob.”
- The “update account now” button leads to a credential phishing page.
- Most importantly — Netflix didn’t send it!
Spear phishing
Spear phishing is an email attack targeting a specific individual. So, whereas bulk phishing uses a net — sending emails to as many potential victims as possible — spear phishing uses a spear to target one specific victim.
Again, spear phishing is can also be an umbrella term, in that there are lots of different types of phishing attacks. Some of the examples below, including Business Email Compromise (BEC) and CEO fraud, are almost always spear phishing attacks.
Why? Because whenever a phishing attack targets a specific individual, it’s a spear phishing attack.
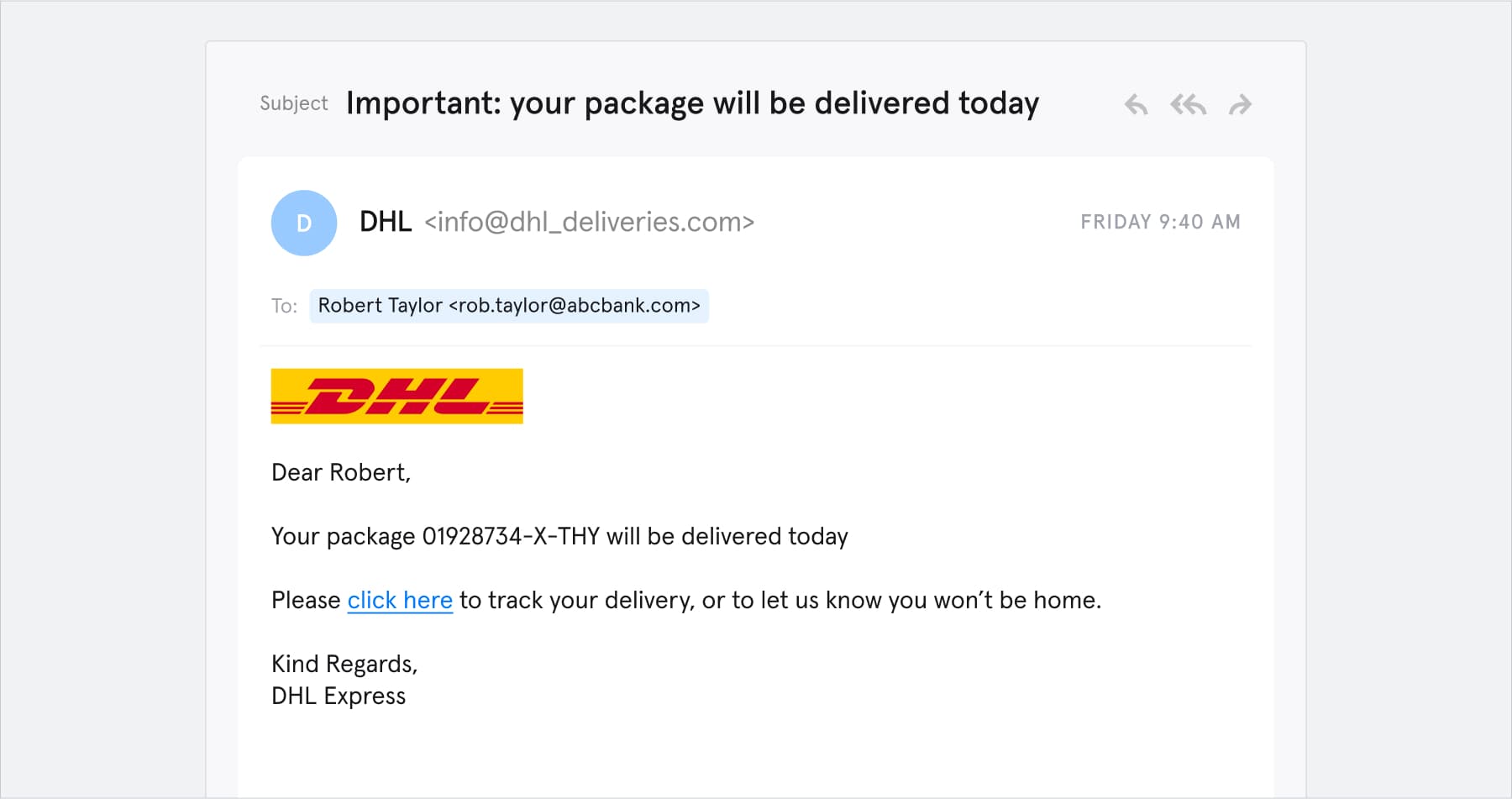
Here’s an example:
What makes this a spear phishing email?
- It targets a specific person.
- The “click here” link leads to a credential phishing website.
- Most importantly — you guessed it — DHL didn’t send it!
Business Email Compromise (BEC)
Business Email Compromise (BEC) is any phishing attack where the attacker uses a hacked, spoofed, or impersonated corporate email address.
In the sense that the attacker is impersonating a business, the Netflix and DHL examples above are both BEC attacks. But we normally use “BEC” to refer to a more sophisticated form of email attack.
For example, one of the biggest cyberattacks of all time is an example of BEC. Between 2013 and 2015, a Latvian cybercrime gang headed by Evaldas Rimasauskas scammed Facebook and Google out of around $121 million by impersonating their suppliers and sending fake invoices via email.
CEO fraud
In a CEO fraud attack, the attacker impersonates a company executive and targets a less senior employee.
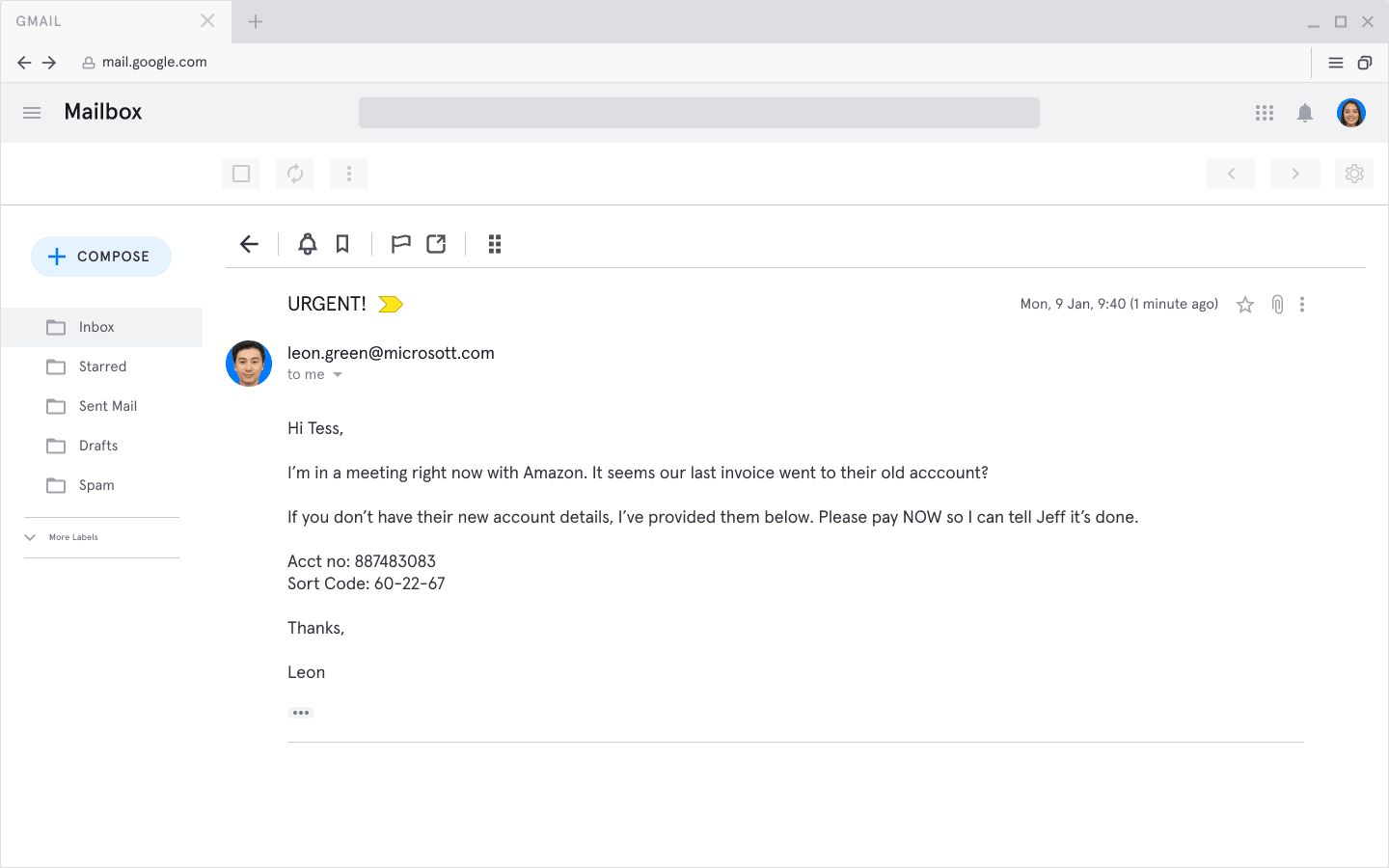
Here’s an example:
What makes this a CEO fraud attack?
- The sender’s email address impersonates a real company executive (note the method here is email impersonation — ”microsott.com” — but other methods such as email spoofing are also common).
- The sender (“Leon”) puts a lot of pressure on the recipient (Tess). Stressed people make poor decisions.
- The attack involves wire transfer fraud. While not all CEO fraud attacks involve wire transfer fraud, this is a very common tactic.
How common are email attacks?
Email attacks are on the rise, and are now extremely common.
- According to the FBI’s Internet Crime Complaint Center (IC3), phishing incidents more than doubled from 2019 to 2020, costing victims over $54 million in direct losses.
- Verizon says 22% of breaches in 2019 involved phishing.
- Around 75% of organizations around the world experienced some kind of phishing attack in 2020.
Consequences of email attacks
What are the main consequences of email attacks on businesses and their customers?
- Data breaches: Attackers use techniques such as credential phishing to exfiltrate your customers’ personal information. Data breaches can attract investigations, regulatory fines, and class-action lawsuits. IBM estimates that the average data breach costs a business $3.86 million
- Malware: Some email attacks aim to deposit a malicious payload on the recipient’s device. This payload is normally some form of malware, for example:
- A virus, which can infect other devices on your network
- Spyware, which can log your keystrokes and online activity
- Ransomware, which encrypts your valuable data and demands you pay a ransom to get it back.
- Wire transfer fraud: Spear phishing attacks—particularly if they involve BEC or CEO fraud—often attempt to persuade the target into transferring funds into a bank account controlled by the attacker. And it really works—that’s why the FBI calls BEC “the $26 billion scam”