Think about all of your different online accounts. Email, social media, banking, eCommerce platforms, news sites….And that’s just in your personal life. What about at work?
For all of these different accounts, you’ll have a username, a password, a pin, or some combination of the three. We call these credentials and they’re the type of data that’s most frequently compromised in phishing attacks. In fact, businesses (and individuals!) lose millions every year to the direct and indirect costs of credential phishing attacks.
-
So, what exactly is credential phishing?
Credential phishing uses increasingly advanced forms of digital manipulation to extract people’s login details. But at its core, this brutally effective cyberattack works because it plays on people’s trust.
Keep reading to find out what credential phishing is, what a credential phishing email looks like, and how to avoid falling victim to a credential phishing attack.
What is phishing?
First things first. Before we can dive into credential phishing specifically, we have to explain what phishing is broadly. Phishing is a type of social engineering attack where the attacker uses “impersonation” to trick the target into giving up information, transferring money, or downloading malware.
Phishing attacks can take many different forms, including:
- Spear phishing: A targeted phishing attack against a known individual.
- Whaling: A phishing attack targeting a c-level executive. Senior employees make good targets, as they have easier access to a larger amount of money.
- Smishing: A phishing attack conducted via text message.
- Vishing: A phishing attack conducted via voice (phone or VoIP).
Any of these types of phishing could be used to gain access to credentials. Attackers also use these methods to target other types of information, like credit card details or social security numbers, and to steal money from the target (“wire transfer phishing”).
If you want to learn more about phishing and other social engineering attacks, check out these articles:
- How to Identify and Prevent Phishing Attacks
- Phishing vs. Spear Phishing: Differences and Defense Strategies
- 6 Real-World Examples of Social Engineering Attacks
How does credential phishing work?
Credential phishing almost always starts with an email. In fact, 96% of phishing attacks do. So how can you spot one? Let’s take a look at the elements of a credential phishing email.
Subject line
The cybercriminal’s first challenge is to get their target to open the phishing email. This requires an intriguing and attention-grabbing subject line. Research reveals some of the most commonly-used words and phrases in the subject lines of phishing emails, including:
- Request
- Follow up
- Urgent/Important
- Are you available?/Are you at your desk?
- Payment Status
- Hello
- Purchase
- Invoice Due
You’ll notice that some of these subject lines elicit feelings of urgency, while others aim for familiarity. According to another report, 25% of phishing emails get read. Ask any marketer, this is a high “open rate”. So, while these tactics might seem crude…they work.
Main body of email
The main content of a credential phishing email is designed to do two jobs: evade spam filters and persuade the target to click a malicious link. With that in mind, there are some hallmarks of a persuasive phishing email:
- It is addressed to you by name.
- It appears to be from a trusted sender with whom you regularly communicate.
- It uses the supposed sender’s proper branding, email signature, and communication style.
The goal – of course – is to make the target believe it’s real.
That’s why successful phishing operations are highly targeted and backed by meticulous research about the target. The days of “spray and pray” bulk phishing emails are long gone. Cybercriminals are using increasingly advanced tactics, such as open source intelligence (OSINT) and hijacking an ongoing email conversation.
Malicious link
Unlike other types of phishing attacks, a credential phishing attack will always contain a link to a fake login page. But, like the main body of the email, the URL should look legitimate. Again, the goal is to trick the target, not raise their suspicions. How? Piggyback off another brand’s reputation.
Research suggests that 52% of malicious links contain a brand name. This is known as a “spoof” domain. For example, a spoof of the URL “https://www.tessian.com” might be “http://www.tessian.nh”
Other techniques used for disguising URLs include using a link-shortening service like Bitly or using a hyperlinked image (for example, a “log in” button). Clickthrough rates on credential phishing links are estimated to fall anywhere from 3.4% (Verizon) to 10% (Proofpoint). This represents a very high success rate: remember that just one person clicking that link can cost a company millions of dollars.
Phishing website
Once you’ve clicked on the link, you’re directed to the phishing website designed to steal your credentials. We call these malicious websites. The landing page must be just as convincing as the email itself. That means a good phishing login page will be meticulously crafted, using authentic images and fonts to perfectly recreate a brand’s genuine site.
Did you know: Cybercriminals are increasingly securing their sites using HTTPS or SSL certification. Research from APWG suggests that 78% of phishing sites use SSL certificates. This security makes the user feel more secure, but it doesn’t mean the site owner can’t steal their data.
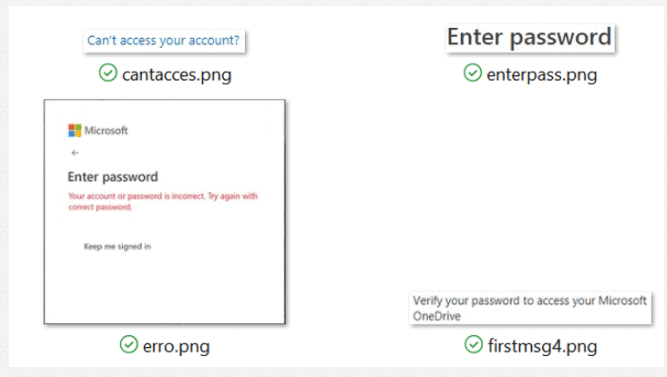
As well as looking convincing, the phishing site must also evade security controls that filter out non-whitelisted sites based on keywords such as “enter password.” But hackers have found a shortcut. Instead of using text on their login pages, they use images. That way, rule-based security controls and spam filters can’t spot the fakes.
Notice how each of the elements that appear as text are actually images (.png). This is a tactic used by hackers to evade security controls that use keywords to detect malicious emails
What happens to phished credentials?
Cybercriminals steal credentials for a variety of reasons. Once your username and password have been phished, they might be:
Credential phishing can be especially damaging for anyone who reuses passwords. Why? If one password is compromised, several accounts could be exposed. Researchers at Virginia Tech observed attackers using phished PayPal, LinkedIn, and Microsoft credentials to log into email accounts — even though the email accounts were not the attackers’ primary targets.
What you need to know about credential phishing
Now you know how credential phishing works, let’s clear up some myths and misconceptions about this particularly dangerous form of cyberattack.
Credential phishing is effective
Because phishing is such a common and well-established type of cyberattack, you might think people have become wise to these scams. Surely phishing for people’s credentials is an outdated tactic? Unfortunately not. Phishing attacks are becoming more sophisticated — and because many people naturally tend to trust others — we’re still clicking those phishing links.
According to Verizon, phishing was the most common cause of data breaches in 2019, with 22% of 2019 data breaches involving phishing. Phishing was also the leading issue in complaints to the FBI’s Internet Crime Complaint Centre (IC3) in 2020. Phishing incidents more than doubled compared to the previous year, and cost victims over $54 million in direct losses.
Not all of these phishing attacks targeted credentials. Other types of phishing involve fake invoices or target credit card details. But credentials are the most common target, with over 60% of phishing attacks aiming to steal usernames and/or passwords.
“According to Verizon, phishing was the most common cause of data breaches in 2019, with 22% of 2019 data breaches involving phishing. Phishing was also the leading issue in complaints to the FBI’s Internet Crime Complaint Centre (IC3) in 2020. Phishing incidents more than doubled compared to the previous year, and cost victims over $54 million in direct losses.”
Multifactor authentication won’t prevent credential phishing
Multifactor authentication (MFA) is an essential extra layer of login security. But MFA isn’t a solution to credential phishing. This is a misconception that can leave people and organizations vulnerable. Here’s why.
Logging into an account protected by MFA requires you to enter your login credentials and take one or more additional steps to verify your identity — such as clicking on a link in an email, entering a verification code sent via SMS, or using an authenticator app.
Yes, this makes things a lot harder for hackers, who must steal a user’s account credentials and access the additional authenticator. But cracking MFA is far from impossible. Authentication tokens can be phished or hacked, just like usernames and passwords.
That means MFA is an essential layer of protection that you should apply across all user accounts, but it’s not a failsafe against credential phishing.
Credential phishing attacks increasingly target corporate email accounts
Some organizations might focus their cybersecurity efforts on preventing attacks involving ransomware or wire transfer phishing, believing that consumers are more likely to be the target of credential phishing.
Credential phishing attacks against consumers are very common, but research shows that credential phishing scammers now have their sights set on corporate targets.
What makes corporate email accounts a particularly good target for credential phishing? Hackers can use one account as a foothold to conduct further phishing operations both within the organization and across their supply chain.
How to prevent credential phishing attacks
Investment in cybersecurity is increasing year on year (up 44% in the UK since GDPR was rolled out) and preventing inbound attacks like credential phishing is a high priority for many companies. Here are some solutions to consider.
Email security software
You’ve seen the sophisticated techniques that cybercriminals use to fool their targets. Even the most tech-savvy of your team members can’t be expected to detect advanced credential phishing emails.
Instead of leaving people as the first and last line of defense against these targeted attacks, consider email security software like Tessian Defender that automatically protects your employees’ email accounts against credential phishing and other inbound threats.
Here’s how:
- Tessian scans your employees’ inboxes to learn their regular email style and map their trusted relationships. This way, it automatically knows when an employee receives correspondence from an unexpected sender.
- Tessian inspects inbound emails for signs that they might be phishing emails. Signs might include barely noticeable irregularities in the sender’s email address, potentially malicious links, or suspicious changes to the sender’s communication patterns.
- Tessian warns employees before they fall victim to a phishing attack and alerts security teams, who can quickly and easily investigate the attack and – to prevent future attacks – can add the sender’s domain to a denylist in a single click.
Security training
Staff training in data protection and phishing awareness are both essential (and can even be a requirement under some privacy laws and regulatory standards).
Why? Your staff should know what phishing emails and other cyberattacks look like and know what to do if they fall victim to one. But the average person isn’t a security expert. Like we said, even the most tech-savvy person can fall for sophisticated attacks. It’s no wonder, then, that most data breaches start with human error. To learn more about the pros and cons of phishing awareness training, click here.
Password management
In a world where passwords protect our most valuable and sensitive data, it’s incredible how many people still use the same password across multiple accounts.
Re-using passwords increases your vulnerability across multiple accounts. Your organization should insist that employees use unique, complex passwords for each of their accounts. Employees should also be changing their passwords regularly.
One way to ensure better password management is to use a password manager, ideally designed for enterprise, with centralized user account controls. You should also be implementing multi-factor authentication wherever possible.
If you want to learn more about email security best practices, we recommend these articles:
- Email Security Best Practice 2020
- Email Mistakes at Work and How to Fix Them
- The Psychology of Human Error
- How to Catch a Phish: a Closer Look at Email Impersonation
Or, if you want to learn more about how Tessian helps enterprises around the world prevent credential phishing and other inbound and outbound threats, read our customer stories.