If you’re aiming to achieve compliance with the MITRE ATT&CK Framework, email security will be among your top priorities. Why? Because securing your organization’s email is critical to detect, mitigate, and defend against some of the most widespread and harmful online threats.
In this article, we’ll offer a brief overview of the MITRE ATT&CK framework, then consider which attack techniques you can mitigate by improving your organization’s email security.
MITRE ATT&CK Framework 101
Here’s a brief introduction to the MITRE ATT&CK framework. Outlining the framework is important as it’ll help you see how its components tie in with your email security program. But feel free to skip ahead f you already know the basics.
ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge. The ATT&CK framework has three iterations—ATT&CK for Enterprise, ATT&CK for Mobile, and Pre-ATT&CK.
We’re focusing on ATT&CK for Enterprise, covering threats to Windows, macOS, Linux, AWS, GCP, Azure, Azure AD, Office 365, SaaS, and Network environments. You can check out the Mobile Matrices here, and the PRE Matric here.
MITRE ATT&CK tactics, techniques, sub-techniques, and mitigations
At the core of the framework is the ATT&CK matrix—a set of “Tactics” and corresponding “Techniques” used by “Adversaries” (threat actors).
The ATT&ACK for Enterprise matrix includes 14 Tactics:
- TA0043: Reconnaissance
- TA0042: Resource Development
- TA0001: Initial Access
- TA0002: Execution
- TA0003: Persistence
- TA0004: Privilege Escalation
- TA0005: Defense Evasion
- TA0006: Credential Access
- TA0007: Discovery
- TA0008: Lateral Movement
- TA0009: Collection
- TA0011: Command and Control
- TA0010: Exfiltration
- TA0040: Impact
Think of these Tactics as the Adversary’s main objectives. For example, under the “Collection” Tactic (TA0009), the adversary is “trying to gather data of interest to their goal.” If you want to learn more about these tactics, or see a full list of the Techniques, Sub-Techniques, and Mitigations we mention below, click here.
A set of Techniques and sometimes “Sub-Techniques” is associated with each Tactic. Techniques are the methods an Adversary uses to achieve their tactical objectives. Sub-Techniques are variations on certain Techniques. We won’t list all the MITRE ATT&CK Techniques here, but we’ll identify some relevant to email security in just a second.
But first (and finally) there are “Mitigations”—methods of preventing or defending against adversaries. Examples of Mitigations include M1041: “Encrypt Sensitive Information,” and M1027: “Password Policies.” Back to email security…
MITRE and Email Security
Now we’ll identify the MITRE ATT&CK framework Tactics and Techniques that are relevant to email security specifically. We’ll consider MITRE’s recommended Mitigations and look at how you can align your email security program to meet the framework’s requirements.
Technique T1566: Phishing
“Phishing” is a MITRE ATT&CK Technique associated with the “Initial Access” Tactic (TA0001). As you’ll probably know, phishing is a type of social engineering attack—usually conducted via email—where an adversary impersonates a trusted person and brand and attempts to trick their target into divulging information, downloading malware, or transferring money.
The MITRE ATT&CK framework identifies both targeted phishing attacks (a technique known as “spear phishing”) and more general phishing attacks (conducted in bulk via spam emails). Now let’s look at the three Sub-Techniques associated with the Phishing Technique.
📎 T1566.001: Spearphishing Attachment
Sub-Technique T1566.001 involves sending a spear phishing email with a malicious attachment. The attachment is malware, such as a virus, spyware, or ransomware file that enables the adversary to harm or gain control of the target device or system.
A spear phishing attachment is usually disguised as a harmless Office, PDF, or ZIP file, and legacy email security software and spam filters can struggle to determine whether an attachment is malicious.
The spear phishing email itself will usually try to persuade the target to open the file. The Adversary may impersonate a trusted person and can even provide the target with instructions on opening the file that will bypass system protections. For more information about malicious email attachments, read What is a Malicious Payload?
🔗 T1566.002: Spearphishing Link
Alternatively to using a malicious attachment, a spear phishing email can include a link that leads to a malicious site such as a fraudulent account login page or a webpage that hosts a malicious download.
Like with the “Spearphishing Attachment” Sub-Technique, the “Spearphishing Link” Sub-Technique will normally employ social engineering methods—this time as a way to persuade the target to click the malicious link.
For example, the spear phishing email may be disguised as a “security alert” email from Microsoft, urging the target to log into their account. Upon following the link and “logging in,” the target’s login credentials will be sent to the adversary.
We’ve written in detail about this type of attack in our article What is Credential Phishing?
📱T1566.003: Spearphishing via Service
The “Spearphishing via Service” Sub-Technique uses platforms other than email to initiate a spearphishing attack—for example, a LinkedIn job post or WhatsApp message.
This Sub-Technique is not directly related to email security—but email security is still relevant here. For example, if an Adversary is able to establish rapport with their target via social media, then they might follow up with a spear phishing email.
❌ Phishing Detection and Mitigation
Now let’s look at which Mitigations MITRE recommends for dealing with the Phishing Technique and its three associated Sub-Techniques:
- M1049: Antivirus/Antimalware — Quarantine suspicious files arriving via email.
- M1031: Network Intrusion Prevention — Monitor inbound email traffic for malicious attachments and links.
- M1021: Restrict Web-Based Content — Block access to web-based content and file types that are not necessary for business activity.
- M1054: Software Configuration — Use anti-spoofing methods to detect invalid Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) signatures.
- M1017: User Training — Educate employees to help them detect signs of a phishing attack.
Note: None of MITRE’s recommended Phishing Mitigations is sufficient on its own.
Antivirus Software, for example, can quarantine malicious files but is less likely to detect suspicious links. User Training helps embed a security-focused workplace culture—but you can’t expect employees to recognize sophisticated social engineering scenarios.
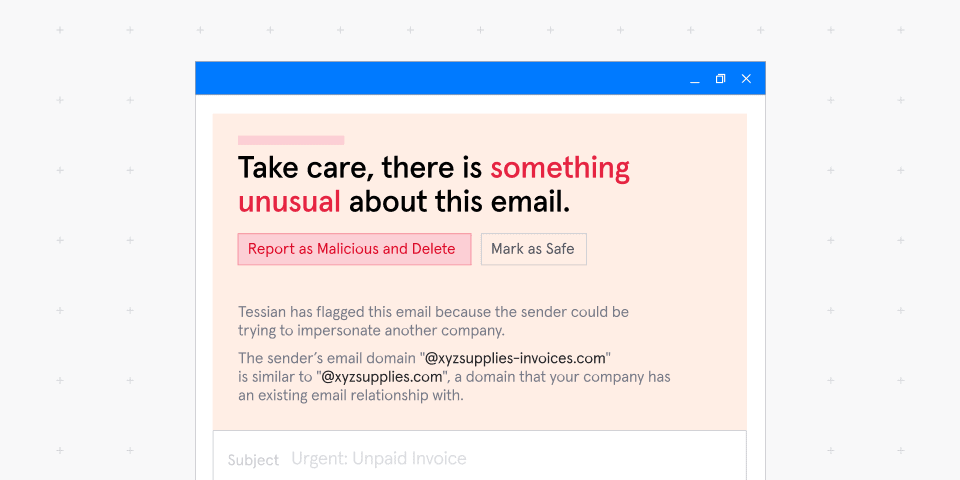
To prevent phishing attacks, it’s vital security leaders take a layered approach, including training, policies, and technology. Your best bet when it comes to technology? A next-gen email security solution that can automatically scan internal and external email communication for signs of malicious activity based on historical analysis.
Email security software can use several methods of detecting phishing attacks. Older solutions rely on techniques such as labeling and filtering—an administrator manually inputs the domain names, file types, and subject lines that the software should block.
Tessian is a modern email security solution driven by machine learning. As well as monitoring inbound emails for signs of phishing, the software scans your employees’ email activity to learn how they “normally” act, and flags suspicious behavior.
This intelligent, context-driven approach means Tessian will allow your employees to work uninterrupted, access the legitimate files and links they need— while being alerted to anomalous and suspicious email content.